The Petri Dish Attack - Guessing Secrets Based on Bacterial Growth
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Microbiology Laboratory Exercises Third Edition 2020
MICROBIOLOGY Laboratory Exercises Third Edition Keddis & Rauschenbach 2020 Photo Credits (in order of contribution): Diane Davis, Ines Rauschenbach & Ramaydalis Keddis Acknowledgements: Many thanks to those in the Department of Biochemistry and Microbiology, Rutgers University, who have through the years inspired our enthusiasm for the science and teaching of microbiology, with special thanks to Diane Davis, Douglas Eveleigh and Max Häggblom. Safety: The experiments included in this manual have been deemed safe by the authors when all necessary safety precautions are met. The authors recommend maintaining biosafety level 2 in the laboratory setting and using risk level 1 organisms for all exercises. License: This work is licensed under a Creative Commons Attribution- NonCommercial-NoDerivatives 4.0 International License Microbiology Laboratory Exercises Third Edition 2020 Ramaydalis Keddis, Ph.D. Ines Rauschenbach, Ph.D. Department of Biochemistry and Microbiology Rutgers, The State University of New Jersey CONTENTS PAGE Introduction Schedule ii Best Laboratory Practices Iii Working in a Microbiology Laboratory iv Exercises Preparation of a Culture Medium 1 Culturing and Handling Microorganisms 3 Isolation of a Pure Culture 5 Counting Bacterial Populations 8 Controlling Microorganisms 10 Disinfectants 10 Antimicrobial Agents: Susceptibility Testing 12 Hand Washing 14 The Lethal Effects of Ultraviolet Light 15 Selection of Fungi from Air 17 Microscopy 21 Morphology and Staining of Bacteria 26 Microbial Metabolism 30 Enzyme Assay 32 Metabolic -
Page 1 of 27 the Diagram Shows Two Thermometers. the Bulb of Each
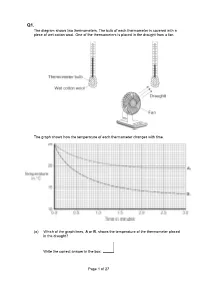
Q1. The diagram shows two thermometers. The bulb of each thermometer is covered with a piece of wet cotton wool. One of the thermometers is placed in the draught from a fan. The graph shows how the temperature of each thermometer changes with time. (a) Which of the graph lines, A or B, shows the temperature of the thermometer placed in the draught? Write the correct answer in the box. Page 1 of 27 Explain, in terms of evaporation, the reason for your answer. ___________________________________________________________________ ___________________________________________________________________ ___________________________________________________________________ ___________________________________________________________________ ___________________________________________________________________ ___________________________________________________________________ (3) (b) A wet towel spread out and hung outside on a day without wind dries faster than an identical wet towel left rolled up in a plastic bag. Explain why. ___________________________________________________________________ ___________________________________________________________________ ___________________________________________________________________ ___________________________________________________________________ (2) (Total 5 marks) Q2. The picture shows a person taking a hot shower. (a) When a person uses the shower the mirror gets misty. Why? ___________________________________________________________________ ___________________________________________________________________ -

Pouring Plates from Prepared Bottled Media
Pouring Plates from Prepared Bottled Media Primary Hazard Warning Never purchase living specimens without having a disposition strategy in place. When pouring bottles, agar is HOT! Burning can occur. Always handle hot agar bottles with heat-protective gloves. For added protection wear latex or nitrile gloves when working with bacteria, and always wash hands before and after with hot water and soap. Availability Agar is available for purchase year round. Information • Storage: Bottled agar can be stored at room temperature for about six months unless otherwise specified. Never put agar in the freezer. It will cause the agar to breakdown and become unusable. To prevent contamination keep all bottles and Petri dishes sealed until ready to use. • Pouring Plates • Materials Needed: • Draft-free enclosure or Laminar flow hood • 70% isopropyl alcohol • Petri dishes • Microwave or hot water bath or autoclave 1. Melt the agar using one of the following methods: a) Autoclave: Loosen the cap on the agar bottle and autoclave the bottle at 15 psi for five minutes. While wearing heat-protective gloves, carefully remove the hot bottle and let it cool to between 75–55°C before pouring. This takes approximately 15 minutes. b)Water Bath: Loosen the cap on the agar bottle and place it into a water bath. Water temperature should remain at around 100°C. Leave it in the water bath until the agar is completely melted. While wearing heat- protective gloves, carefully remove the hot bottle and let it cool to between 75–55°C before pouring. c) Microwave: Loosen the cap on the agar bottle before microwaving. -

Microlab® STAR™
Microlab ® STAR™ Microlab ® STAR ™ AUTOMATED WORKFLOW SOLUTIONS CENTERED AROUND YOUR ASSAY The STAR combines Hamilton's patented pipetting technology including precise lock-and-key tip attachment, unrivaled liquid level detection, and comprehensive volume ranges to create flexible liquid handling workstations. Available in three base platform sizes, the STAR portfolio incorporates countless options to automate your workflows. Hamilton Robotics has also partnered with top leaders in the biotechnology industry to provide Standard Solutions based on commonly automated applications. Offering ready-to-start protocols for a variety of applications such as NGS, ELISA, and forensic assays, our Standard Solutions provide a faster way to automate your processes. 2 1 PATENTED TECHNOLOGY The STAR utilizes Hamilton’s proprietary Compressed O-Ring Expansion (CO-RE®) technology. CO-RE minimizes the production of aerosols and allows disposable tips or washable, steel needles to be used on channels in the same run. 2 MULTI-FUNCTIONAL ARM Our technology offers high pipetting accuracy and precision, from sub-microliter to large volumes, using Independent Channels and/or the Multi-Probe Head (MPH). Labware transportation is possible with the iSWAP® or CO-RE Grippers. The STAR can incorporate a camera, tube transportation, and other channel tools on a single arm. Comprehensive pipetting range: ■■■0.5 μL to 1 mL using the 1 mL Independent Channel ■■■50 μL to 5 mL using the 5 mL Independent Channel ■■■1 μL to 1 mL using the CO-RE 96 MPH ■■■0.1 μL to 50 μL using the CO-RE 384 MPH 3 FLEXIBLE SETUP The high-capacity deck is customized specific to your workflow, accommodating a wide range of labware and automated devices that can easily be exchanged to support multiple assays on one platform. -

Evobot: an Open-Source, Modular, Liquid Handling Robot for Scientific Experiments
applied sciences Article EvoBot: An Open-Source, Modular, Liquid Handling Robot for Scientific Experiments Andres Faiña 1,* , Brian Nejati 2 and Kasper Stoy 1 1 Robots, Evolution and Art Lab (REAL), Department of Computer Science, IT University of Copenhagen, 2300 Copenhagen, Denmark; [email protected] 2 Department of Mechanical and Industrial Engineering, University of Toronto, Toronto, ON M5S 1A1, Canada; His work was carried out while he was employed at ITU; [email protected] * Correspondence: [email protected]; Tel.: +45-7218-5258 Received: 13 October 2019; Accepted: 17 January 2020; Published: 23 January 2020 Featured Application: Our modular liquid handling robot can be applied to automate scientific experiments in research labs, where tasks change often, and to carry out new kinds of experiments that cannot be done manually. Abstract: Commercial liquid handling robots are rarely appropriate when tasks change often, which is the case in the early stages of biochemical research. In order to address it, we have developed EvoBot, a liquid handling robot, which is open-source and employs a modular design. The combination of an open-source and a modular design is particularly powerful because functionality is divided into modules with simple, well-defined interfaces, hence customisation of modules is possible without detailed knowledge of the entire system. Furthermore, the modular design allows end-users to only produce and assemble the modules that are relevant for their specific application. Hence, time and money are not wasted on functionality that is not needed. Finally, modules can easily be reused. In this paper, we describe the EvoBot modular design and through scientific experiments such as basic liquid handling, nurturing of microbial fuel cells, and droplet chemotaxis experiments document how functionality is increased one module at a time with a significant amount of reuse. -

Process Skills Review Warm-Up C
Process Skills Review Warm-Up C. • Define function • Match the following 1. Puts out fire 2. Curved line of liquid in a graduated cylinder 3. Used to observe insects A. B. Which of the following describes the correct way to handle chemicals in a laboratory? A. It is safe to combine unknown chemicals as long as only small amounts are used. B. Return all chemicals to their original containers. C. Always pour extra amounts of the chemicals called for the experiment. D. To test for odors, always use a wafting motion. Which of the following describes the correct way to handle chemicals in a laboratory? A. It is safe to combine unknown chemicals as long as only small amounts are used. B. Return all chemicals to their original containers. C. Always pour extra amounts of the chemicals called for the experiment. D. To test for odors, always use a wafting motion. What task is being performed in the picture? A. measuring mass with a graduated cylinder B. measuring length with a triple beam balance C. measuring mass with a triple beam balance D. measuring length with a metric ruler What task is being performed in the picture? A. measuring mass with a graduated cylinder B. measuring length with a triple beam balance C. measuring mass with a triple beam balance D. measuring length with a metric ruler John and Lisa are conducting an experiment in their 7th grade science class in which they are handling potentially dangerous chemicals. As John is pouring a chemical from a beaker to a graduated cylinder, he splashes some of the chemical into his eyes. -

STERILE TECHNIQUE PRACTICE Module 3 Supplement
STUDENT STERILE TECHNIQUE PRACTICE Module 3 Supplement ONLY FOR PRACTICE you should Re-use the loop and pipette and re-use their "sterile" wrappings Do not dispose of a culture dish even if you accidentally contaminate it. If you were really doing a lab with bacteria you would • Never reuse any loop or pipette. • Always dispose of used loops and pipettes in the "biological trash beaker." • Throw away any culture dish or other item that is accidentally contaminated, and ask for a replacement. • Wash hands immediately if they contact any liquids containing bacteria. Each member of the team should practice each of the following: 1. Open, hold, and close a sterile 15 ml culture tube. 2. Open and close a sterile 1.5 ml test tube. 3. Open a culture dish, observe it without breathing on it, and close it. After each team member has practiced 1-3, use (practice) sterile technique as you 4. Transfer 250 l of liquid from the 1.5 ml test tube to the culture tube. 5. Pretend to transfer a colony from the surface of the culture dish to the liquid in the culture tube. 6. Use the pipette to suspend the imaginary bacteria in the culture tube liquid. After each team member has practiced 4-6, use (practice) sterile technique as you 7. Transfer 100 l of culture tube contents to culture dish and spread it. POSSIBLE SEQUENCE OF STEPS FOR STERILE TECHNIQUE DEMONSTRATION/PRACTICE Delete parts as time requires 1. a. Teacher demonstrates opening/holding/closing of sterile 1.5 ml test tube, sterile 15 ml culture tube, sterile pipettes, measuring with pipettes. -

Laboratory Equipment Used in Filtration
KNOW YOUR LAB EQUIPMENTS Test tube A test tube, also known as a sample tube, is a common piece of laboratory glassware consisting of a finger-like length of glass or clear plastic tubing, open at the top and closed at the bottom. Beakers Beakers are used as containers. They are available in a variety of sizes. Although they often possess volume markings, these are only rough estimates of the liquid volume. The markings are not necessarily accurate. Erlenmeyer flask Erlenmeyer flasks are often used as reaction vessels, particularly in titrations. As with beakers, the volume markings should not be considered accurate. Volumetric flask Volumetric flasks are used to measure and store solutions with a high degree of accuracy. These flasks generally possess a marking near the top that indicates the level at which the volume of the liquid is equal to the volume written on the outside of the flask. These devices are often used when solutions containing dissolved solids of known concentration are needed. Graduated cylinder Graduated cylinders are used to transfer liquids with a moderate degree of accuracy. Pipette Pipettes are used for transferring liquids with a fixed volume and quantity of liquid must be known to a high degree of accuracy. Graduated pipette These Pipettes are calibrated in the factory to release the desired quantity of liquid. Disposable pipette Disposable transfer. These Pipettes are made of plastic and are useful for transferring liquids dropwise. Burette Burettes are devices used typically in analytical, quantitative chemistry applications for measuring liquid solution. Differing from a pipette since the sample quantity delivered is changeable, graduated Burettes are used heavily in titration experiments. -

Quantitative Method for Evaluating Bactericidal and Mycobactericidal Activity of Microbicides Used on Hard, Non-Porous Surfaces
US Environmental Protection Agency Office of Pesticide Programs Office of Pesticide Programs Microbiology Laboratory Environmental Science Center, Ft. Meade, MD Standard Operating Procedure for OECD Quantitative Method for Evaluating Bactericidal and Mycobactericidal Activity of Microbicides Used on Hard, Non-Porous Surfaces SOP Number: MB-25-04 Date Revised: 12-04-17 SOP No. MB-25-04 Date Revised 12-04-17 Page 1 of 26 SOP Number MB-25-04 Title OECD Quantitative Method for Evaluating Bactericidal and Mycobactericidal Activity of Microbicides Used on Hard, Non- Porous Surfaces Scope The method provides a quantitative assessment of the performance of liquid antimicrobial substances against Pseudomonas aeruginosa, Salmonella enterica, Staphylococcus aureus, and Mycobacterium terrae designed for use on hard, non-porous surfaces. This method is based on an Organization for Economic Co-operation and Development (OECD) Guidance Document, dated June 21, 2013 (see ref. 15.1); however, the SOP contains revisions based on information and data collected by the EPA since 2013. Application This method provides log reduction (LR) as the quantitative measure of efficacy for liquid disinfectants against the test microbes on a hard non-porous surface. Approval Date SOP Developer: _____________________________________________ Print Name: ___________________________________ SOP Reviewer _____________________________________________ Print Name: ___________________________________ Quality Assurance Unit _____________________________________________ Print Name: ___________________________________ Branch Chief _____________________________________________ Print Name: ___________________________________ Data SOP issued: Controlled copy number: Date SOP withdrawn: SOP No. MB-25-04 Date Revised 12-04-17 Page 2 of 26 TABLE OF CONTENTS Contents Page Number 1. DEFINITIONS 3 2. HEALTH AND SAFETY 3 3. PERSONNEL QUALIFICATIONS AND TRAINING 3 4. INSTRUMENT CALIBRATION 3 5. -

What's in Your Petri
Ages: 10-14 Topic: Bacteria, Scientific Method, Classifying, Sampling Time: 2 class days Standards Mission X: Train Like an Astronaut Next Generation Science Standards: 5-LS2-1 Develop a model to describe the movement of matter among plants, animals, decomposers, and the What's in your Petri environment Common Core State Standards: MP.4 Model with BUGS IN SPACE PART 2 mathematics EDUCATOR SECTION (PAGES 1-12) STUDENT SECTION (PAGES 13-21) Background Microbes live everywhere! While many microbes on Earth are harmless, and can even be helpful to humans, some microbes can be unsafe. Microbes belong to a group all by themselves because they are neither plants nor animals. Because they can multiply extremely quickly, it is normal to find millions of them in the same location. Some microbes or “germs”, such as bacteria and mold, can grow on food, dirty clothes, and garbage that people produce. Microbes live on your skin, in your Astronaut Chris Hadfield taking microbe samples on the ISS. mouth, nose, hair, and inside your body. Microbes can also be found aboard the International Space Station (ISS). NASA scientists have reported that some germs on the ISS have different characteristics when grown in space compared to when they grow on Earth. The safety of the crew is of utmost importance. Therefore, cleanliness and proper disposal of garbage is an important part of living on the ISS. Scientists who study microbes are called microbiologists and microbiology is the study of microorganisms or microbes. The root word “micro” comes from Greek and means “small”. These microbes are so small that powerful microscopes are needed to be able to see them. -

Pure Culture Techniques
Microbiology BIOL 275 PURE CULTURE TECHNIQUES I. OBJECTIVES • To demonstrate good aseptic technique in culture transfer or inoculation and in handling sterile materials. • To demonstrate skill in isolation of organisms from a mixed culture using selective and differential media. • To isolate microorganisms from a wide variety of sources and describe their colonial morphology. II. INTRODUCTION Most environments carry a mixed microbial population. To fully appreciate the contribution of each group of organisms to the ecology of the mass, one must first dissect this mixed culture to obtain single colonies. The single colony is transferred (picked) to a fresh medium to obtain a larger, homogeneous culture that may be studied and characterized by a variety of techniques. One such technique is called aseptic technique. Microbiologists and health workers use this technique to prevent contamination of cultures from outside sources and to prevent the introduction of potential disease agents into the human body (infection can occur through contamination of your hands and clothing with material from your bacterial cultures). Aseptic Techniques Aseptic techniques (also called sterile techniques) are defined as the processes required for transferring a culture from one vessel to another without introducing any additional organisms to the culture or contaminating the environment with the culture. The following conditions must exist for aseptic technique to be successful: 1. The work area must be wiped with an antiseptic to reduce the number of potential contaminants. 2. The transfer instruments must be sterile. 3. The work must be accomplished quickly and efficiently to minimize the time of exposure during which contamination of the culture or laboratory worker can occur. -

Using a Microwave to Prepare Bacterial Media for Inquiry-Based Experiments Judith A
Illinois Math and Science Academy DigitalCommons@IMSA Staff ubP lications & Research Student Inquiry and Research (SIR) Fall 2014 Watts Cooking: Using a Microwave to Prepare Bacterial Media for Inquiry-Based Experiments Judith A. Scheppler Illinois Mathematics and Science Academy, [email protected] Follow this and additional works at: http://digitalcommons.imsa.edu/sir_staffpr Part of the Education Commons, and the Microbiology Commons Recommended Citation Scheppler, Judith A., "Watts ooC king: Using a Microwave to Prepare Bacterial Media for Inquiry-Based Experiments" (2014). Staff Publications & Research. 2. http://digitalcommons.imsa.edu/sir_staffpr/2 This Article is brought to you for free and open access by the Student Inquiry and Research (SIR) at DigitalCommons@IMSA. It has been accepted for inclusion in Staff ubP lications & Research by an authorized administrator of DigitalCommons@IMSA. For more information, please contact [email protected], [email protected]. Articles Watts Cooking: Using a Microwave to Prepare Bacterial Media for Inquiry-Based Experiments Judith A. Scheppler Illinois Mathematics and Science Academy Abstract depend on the knowledge base students bring to Microbiology provides an excellent opportunity this experience. to capture student interest, encourage explora- tion, and to begin the development of research Preparation and Sterilization of Luria-Ber- skills. With a low power microwave, similar to tani Agar for Bacterial Growth the type found in homes, and a short list of ma- Bacteria media plates will need to be prepared terials easily obtainable and/or found in many at least one day in advance of carrying out any biology laboratories, you can begin to open this experiment. The following procedure should be exciting world to your life science and biology used to prepare sterile Luria-Bertani (LB) agar classes.