Evobot: an Open-Source, Modular, Liquid Handling Robot for Scientific Experiments
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Exploring Small-Scale Chemostats to Scale up Microbial Processes: 3-Hydroxypropionic Acid Production in S
Lawrence Berkeley National Laboratory Recent Work Title Exploring small-scale chemostats to scale up microbial processes: 3-hydroxypropionic acid production in S. cerevisiae. Permalink https://escholarship.org/uc/item/43h8866j Journal Microbial cell factories, 18(1) ISSN 1475-2859 Authors Lis, Alicia V Schneider, Konstantin Weber, Jost et al. Publication Date 2019-03-11 DOI 10.1186/s12934-019-1101-5 Peer reviewed eScholarship.org Powered by the California Digital Library University of California Lis et al. Microb Cell Fact (2019) 18:50 https://doi.org/10.1186/s12934-019-1101-5 Microbial Cell Factories RESEARCH Open Access Exploring small-scale chemostats to scale up microbial processes: 3-hydroxypropionic acid production in S. cerevisiae Alicia V. Lis1, Konstantin Schneider1,2, Jost Weber1,3, Jay D. Keasling1,4,5,6,7, Michael Krogh Jensen1 and Tobias Klein1,2* Abstract Background: The physiological characterization of microorganisms provides valuable information for bioprocess development. Chemostat cultivations are a powerful tool for this purpose, as they allow defned changes to one single parameter at a time, which is most commonly the growth rate. The subsequent establishment of a steady state then permits constant variables enabling the acquisition of reproducible data sets for comparing microbial perfor- mance under diferent conditions. We performed physiological characterizations of a 3-hydroxypropionic acid (3-HP) producing Saccharomyces cerevisiae strain in a miniaturized and parallelized chemostat cultivation system. The physi- ological conditions under investigation were various growth rates controlled by diferent nutrient limitations (C, N, P). Based on the cultivation parameters obtained subsequent fed-batch cultivations were designed. Results: We report technical advancements of a small-scale chemostat cultivation system and its applicability for reliable strain screening under diferent physiological conditions, i.e. -

Chemostat Culture for Yeast Experimental Evolution
Downloaded from http://cshprotocols.cshlp.org/ at Cold Spring Harbor Laboratory Library on August 9, 2017 - Published by Cold Spring Harbor Laboratory Press Protocol Chemostat Culture for Yeast Experimental Evolution Celia Payen and Maitreya J. Dunham1 Department of Genome Sciences, University of Washington, Seattle, Washington 98195 Experimental evolution is one approach used to address a broad range of questions related to evolution and adaptation to strong selection pressures. Experimental evolution of diverse microbial and viral systems has routinely been used to study new traits and behaviors and also to dissect mechanisms of rapid evolution. This protocol describes the practical aspects of experimental evolution with yeast grown in chemostats, including the setup of the experiment and sampling methods as well as best laboratory and record-keeping practices. MATERIALS It is essential that you consult the appropriate Material Safety Data Sheets and your institution’s Environmental Health and Safety Office for proper handling of equipment and hazardous material used in this protocol. Reagents Defined minimal medium appropriate for the experiment For examples, see Protocol: Assembly of a Mini-Chemostat Array (Miller et al. 2015). Ethanol (95%) Glycerol (20% and 50%; sterile) Yeast strain of interest Equipment Agar plates (appropriate for chosen strain) Chemostat array Assemble the apparatus as described in Miller et al. (2013) and Protocol: Assembly of a Mini-Chemostat Array (Miller et al. 2015). Cryo deep-freeze labels Cryogenic vials Culture tubes Cytometer (BD Accuri C6) Glass beads, 4 mm (sterile; for plating yeast cells) Glass cylinder Kimwipes 1Correspondence: [email protected] © 2017 Cold Spring Harbor Laboratory Press Cite this protocol as Cold Spring Harb Protoc; doi:10.1101/pdb.prot089011 559 Downloaded from http://cshprotocols.cshlp.org/ at Cold Spring Harbor Laboratory Library on August 9, 2017 - Published by Cold Spring Harbor Laboratory Press C. -

Microbiology Laboratory Exercises Third Edition 2020
MICROBIOLOGY Laboratory Exercises Third Edition Keddis & Rauschenbach 2020 Photo Credits (in order of contribution): Diane Davis, Ines Rauschenbach & Ramaydalis Keddis Acknowledgements: Many thanks to those in the Department of Biochemistry and Microbiology, Rutgers University, who have through the years inspired our enthusiasm for the science and teaching of microbiology, with special thanks to Diane Davis, Douglas Eveleigh and Max Häggblom. Safety: The experiments included in this manual have been deemed safe by the authors when all necessary safety precautions are met. The authors recommend maintaining biosafety level 2 in the laboratory setting and using risk level 1 organisms for all exercises. License: This work is licensed under a Creative Commons Attribution- NonCommercial-NoDerivatives 4.0 International License Microbiology Laboratory Exercises Third Edition 2020 Ramaydalis Keddis, Ph.D. Ines Rauschenbach, Ph.D. Department of Biochemistry and Microbiology Rutgers, The State University of New Jersey CONTENTS PAGE Introduction Schedule ii Best Laboratory Practices Iii Working in a Microbiology Laboratory iv Exercises Preparation of a Culture Medium 1 Culturing and Handling Microorganisms 3 Isolation of a Pure Culture 5 Counting Bacterial Populations 8 Controlling Microorganisms 10 Disinfectants 10 Antimicrobial Agents: Susceptibility Testing 12 Hand Washing 14 The Lethal Effects of Ultraviolet Light 15 Selection of Fungi from Air 17 Microscopy 21 Morphology and Staining of Bacteria 26 Microbial Metabolism 30 Enzyme Assay 32 Metabolic -
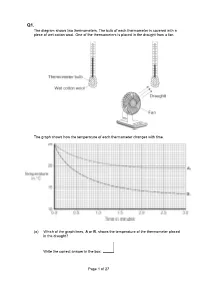
Page 1 of 27 the Diagram Shows Two Thermometers. the Bulb of Each
Q1. The diagram shows two thermometers. The bulb of each thermometer is covered with a piece of wet cotton wool. One of the thermometers is placed in the draught from a fan. The graph shows how the temperature of each thermometer changes with time. (a) Which of the graph lines, A or B, shows the temperature of the thermometer placed in the draught? Write the correct answer in the box. Page 1 of 27 Explain, in terms of evaporation, the reason for your answer. ___________________________________________________________________ ___________________________________________________________________ ___________________________________________________________________ ___________________________________________________________________ ___________________________________________________________________ ___________________________________________________________________ (3) (b) A wet towel spread out and hung outside on a day without wind dries faster than an identical wet towel left rolled up in a plastic bag. Explain why. ___________________________________________________________________ ___________________________________________________________________ ___________________________________________________________________ ___________________________________________________________________ (2) (Total 5 marks) Q2. The picture shows a person taking a hot shower. (a) When a person uses the shower the mirror gets misty. Why? ___________________________________________________________________ ___________________________________________________________________ -

Pouring Plates from Prepared Bottled Media
Pouring Plates from Prepared Bottled Media Primary Hazard Warning Never purchase living specimens without having a disposition strategy in place. When pouring bottles, agar is HOT! Burning can occur. Always handle hot agar bottles with heat-protective gloves. For added protection wear latex or nitrile gloves when working with bacteria, and always wash hands before and after with hot water and soap. Availability Agar is available for purchase year round. Information • Storage: Bottled agar can be stored at room temperature for about six months unless otherwise specified. Never put agar in the freezer. It will cause the agar to breakdown and become unusable. To prevent contamination keep all bottles and Petri dishes sealed until ready to use. • Pouring Plates • Materials Needed: • Draft-free enclosure or Laminar flow hood • 70% isopropyl alcohol • Petri dishes • Microwave or hot water bath or autoclave 1. Melt the agar using one of the following methods: a) Autoclave: Loosen the cap on the agar bottle and autoclave the bottle at 15 psi for five minutes. While wearing heat-protective gloves, carefully remove the hot bottle and let it cool to between 75–55°C before pouring. This takes approximately 15 minutes. b)Water Bath: Loosen the cap on the agar bottle and place it into a water bath. Water temperature should remain at around 100°C. Leave it in the water bath until the agar is completely melted. While wearing heat- protective gloves, carefully remove the hot bottle and let it cool to between 75–55°C before pouring. c) Microwave: Loosen the cap on the agar bottle before microwaving. -

Microlab® STAR™
Microlab ® STAR™ Microlab ® STAR ™ AUTOMATED WORKFLOW SOLUTIONS CENTERED AROUND YOUR ASSAY The STAR combines Hamilton's patented pipetting technology including precise lock-and-key tip attachment, unrivaled liquid level detection, and comprehensive volume ranges to create flexible liquid handling workstations. Available in three base platform sizes, the STAR portfolio incorporates countless options to automate your workflows. Hamilton Robotics has also partnered with top leaders in the biotechnology industry to provide Standard Solutions based on commonly automated applications. Offering ready-to-start protocols for a variety of applications such as NGS, ELISA, and forensic assays, our Standard Solutions provide a faster way to automate your processes. 2 1 PATENTED TECHNOLOGY The STAR utilizes Hamilton’s proprietary Compressed O-Ring Expansion (CO-RE®) technology. CO-RE minimizes the production of aerosols and allows disposable tips or washable, steel needles to be used on channels in the same run. 2 MULTI-FUNCTIONAL ARM Our technology offers high pipetting accuracy and precision, from sub-microliter to large volumes, using Independent Channels and/or the Multi-Probe Head (MPH). Labware transportation is possible with the iSWAP® or CO-RE Grippers. The STAR can incorporate a camera, tube transportation, and other channel tools on a single arm. Comprehensive pipetting range: ■■■0.5 μL to 1 mL using the 1 mL Independent Channel ■■■50 μL to 5 mL using the 5 mL Independent Channel ■■■1 μL to 1 mL using the CO-RE 96 MPH ■■■0.1 μL to 50 μL using the CO-RE 384 MPH 3 FLEXIBLE SETUP The high-capacity deck is customized specific to your workflow, accommodating a wide range of labware and automated devices that can easily be exchanged to support multiple assays on one platform. -

Yeast Metabolic and Signaling Genes Are Required for Heat-Shock Survival
Yeast metabolic and signaling genes are required for PNAS PLUS heat-shock survival and have little overlap with the heat-induced genes Patrick A. Gibneya,b,1, Charles Lub,1, Amy A. Caudya,2,3, David C. Hessc,3, and David Botsteina,b,4 aLewis-Sigler Institute for Integrative Genomics and bDepartment of Molecular Biology, Princeton University, Princeton, NJ 08544; and cDepartment of Biology, Santa Clara University, Santa Clara, CA 95053 Contributed by David Botstein, September 30, 2013 (sent for review August 25, 2013) Genome-wide gene-expression studies have shown that hundreds or proteins that increase in abundance as part of the heat-shock of yeast genes are induced or repressed transiently by changes in response (1, 11–14). Classically, this set of genes/proteins includes temperature; many are annotated to stress response on this basis. the molecular chaperones, which often are induced in response to To obtain a genome-scale assessment of which genes are function- stress (14). However, by using the deletion collection to assay ally important for innate and/or acquired thermotolerance, we thermotolerance, we also can identify genes important for stress combined the use of a barcoded pool of ∼4,800 nonessential, pro- resistance that are either constitutively present or posttransla- totrophic Saccharomyces cerevisiae deletion strains with Illumina- tionally modified. We therefore carried out two kinds of exper- based deep-sequencing technology. As reported in other recent iment to examine heat-stress resistance. First we studied the 50 °C studies that have used deletion mutants to study stress responses, survival time-course of samples from a steady-state chemostat cul- we observed that gene deletions resulting in the highest thermo- ture of the entire prototrophic barcoded deletion collection. -

Process Skills Review Warm-Up C
Process Skills Review Warm-Up C. • Define function • Match the following 1. Puts out fire 2. Curved line of liquid in a graduated cylinder 3. Used to observe insects A. B. Which of the following describes the correct way to handle chemicals in a laboratory? A. It is safe to combine unknown chemicals as long as only small amounts are used. B. Return all chemicals to their original containers. C. Always pour extra amounts of the chemicals called for the experiment. D. To test for odors, always use a wafting motion. Which of the following describes the correct way to handle chemicals in a laboratory? A. It is safe to combine unknown chemicals as long as only small amounts are used. B. Return all chemicals to their original containers. C. Always pour extra amounts of the chemicals called for the experiment. D. To test for odors, always use a wafting motion. What task is being performed in the picture? A. measuring mass with a graduated cylinder B. measuring length with a triple beam balance C. measuring mass with a triple beam balance D. measuring length with a metric ruler What task is being performed in the picture? A. measuring mass with a graduated cylinder B. measuring length with a triple beam balance C. measuring mass with a triple beam balance D. measuring length with a metric ruler John and Lisa are conducting an experiment in their 7th grade science class in which they are handling potentially dangerous chemicals. As John is pouring a chemical from a beaker to a graduated cylinder, he splashes some of the chemical into his eyes. -

Raman Spectroscopy for the Microbiological Characterization and Identification of Medically Relevant Bacteria Khozima Mahmoud Hamasha Wayne State University
Wayne State University Wayne State University Dissertations 1-1-2011 Raman spectroscopy for the microbiological characterization and identification of medically relevant bacteria Khozima Mahmoud Hamasha Wayne State University, Follow this and additional works at: http://digitalcommons.wayne.edu/oa_dissertations Part of the Physics Commons Recommended Citation Hamasha, Khozima Mahmoud, "Raman spectroscopy for the microbiological characterization and identification of medically relevant bacteria" (2011). Wayne State University Dissertations. Paper 311. This Open Access Dissertation is brought to you for free and open access by DigitalCommons@WayneState. It has been accepted for inclusion in Wayne State University Dissertations by an authorized administrator of DigitalCommons@WayneState. RAMAN SPECTROSCOPY FOR THE MICROBIOLOGICAL CHARACTERIZATION AND IDENTIFICATION OF MEDICALLY RELEVANT BACTERIA by KHOZIMA MAHMOUD HAMASHA DISSERTATION Submitted to the Graduate School of Wayne State University, Detroit, Michigan in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY 2011 MAJOR: PHYSICS Approved by: Advisor Date DEDICATION I would like to dedicate my dissertation to the memory of my brother “Saleh”. ii ACKNOWLEDGMENTS First of all, I would like to express my great thanks to my advisor Dr. Steven Rehse for his guidance and great help and support throughout my research work. I am always appreciative of this precious opportunity to learn from him about all research aspects, starting from thinking about the problems, sharing the ideas, performing the experiments, collecting the data, analyzing the results, and preparing the manuscripts for publication. Also, special thanks to the committee members, Dr. Ratna Naik for her continued support and encouragement through my graduate study, Dr. Choong-Min Kang for his great assistance and generosity through providing his facility to improve my skills and to getting trained in every microbiological aspect related to my research, and Dr. -

STERILE TECHNIQUE PRACTICE Module 3 Supplement
STUDENT STERILE TECHNIQUE PRACTICE Module 3 Supplement ONLY FOR PRACTICE you should Re-use the loop and pipette and re-use their "sterile" wrappings Do not dispose of a culture dish even if you accidentally contaminate it. If you were really doing a lab with bacteria you would • Never reuse any loop or pipette. • Always dispose of used loops and pipettes in the "biological trash beaker." • Throw away any culture dish or other item that is accidentally contaminated, and ask for a replacement. • Wash hands immediately if they contact any liquids containing bacteria. Each member of the team should practice each of the following: 1. Open, hold, and close a sterile 15 ml culture tube. 2. Open and close a sterile 1.5 ml test tube. 3. Open a culture dish, observe it without breathing on it, and close it. After each team member has practiced 1-3, use (practice) sterile technique as you 4. Transfer 250 l of liquid from the 1.5 ml test tube to the culture tube. 5. Pretend to transfer a colony from the surface of the culture dish to the liquid in the culture tube. 6. Use the pipette to suspend the imaginary bacteria in the culture tube liquid. After each team member has practiced 4-6, use (practice) sterile technique as you 7. Transfer 100 l of culture tube contents to culture dish and spread it. POSSIBLE SEQUENCE OF STEPS FOR STERILE TECHNIQUE DEMONSTRATION/PRACTICE Delete parts as time requires 1. a. Teacher demonstrates opening/holding/closing of sterile 1.5 ml test tube, sterile 15 ml culture tube, sterile pipettes, measuring with pipettes. -

The Petri Dish Attack - Guessing Secrets Based on Bacterial Growth
Poster: The Petri Dish Attack - Guessing Secrets Based on Bacterial Growth Katharina Krombholz Adrian Dabrowski Peter Purgathofer Edgar Weippl SBA Research SBA Research TU Wien SBA Research [email protected] [email protected] [email protected] [email protected] Abstract—PINs and unlock patterns remain by far the most common knowledge-based authentication methods on mobile devices. Biometric authentication methods such as fingerprints also rely on PINs and unlock patterns as fallback methods. In recent years, several attacks on knowledge-based mobile authentication have been presented, e.g., shoulder-surfing [1], smudge attacks [2] and thermal attacks [3]. In this poster, we present the Petri dish attack, a novel attack to guess secrets based on bacterial growth. We conducted a series of lab experiments with 20 Petri dishes to evaluate the feasibility of this new attack and unfortunately were not able to successfully conduct the attack on off-the-shelf smartphones. However, we still believe that our results are valuable to the scientific community and provide a baseline to explore future cross- domain attack vectors and interdisciplinary approaches on smartphone security. Figure 1. The study setup. 1. Concept and Threat Model 2. Lab Study To evaluate the feasibility of the Petri dish attack, we In recent years, several attack scenarios based on human conducted a series of experiments at the Max Perutz Labo- traces left on smartphone touchscreens have been presented, ratories in Vienna. We used 20 Petri dishes with a previously e.g., smudge attacks [2] and thermal attacks [3]. The com- prepared fertile soil optimized for E.coli bacteria which is mon threat model behind these attacks is that the user leaves one of the most commonly found type of bacteria on human their smartphone unattended after a successful authenti- hands and hence often left on surfaces that we frequently cation session. -

Laboratory Equipment Used in Filtration
KNOW YOUR LAB EQUIPMENTS Test tube A test tube, also known as a sample tube, is a common piece of laboratory glassware consisting of a finger-like length of glass or clear plastic tubing, open at the top and closed at the bottom. Beakers Beakers are used as containers. They are available in a variety of sizes. Although they often possess volume markings, these are only rough estimates of the liquid volume. The markings are not necessarily accurate. Erlenmeyer flask Erlenmeyer flasks are often used as reaction vessels, particularly in titrations. As with beakers, the volume markings should not be considered accurate. Volumetric flask Volumetric flasks are used to measure and store solutions with a high degree of accuracy. These flasks generally possess a marking near the top that indicates the level at which the volume of the liquid is equal to the volume written on the outside of the flask. These devices are often used when solutions containing dissolved solids of known concentration are needed. Graduated cylinder Graduated cylinders are used to transfer liquids with a moderate degree of accuracy. Pipette Pipettes are used for transferring liquids with a fixed volume and quantity of liquid must be known to a high degree of accuracy. Graduated pipette These Pipettes are calibrated in the factory to release the desired quantity of liquid. Disposable pipette Disposable transfer. These Pipettes are made of plastic and are useful for transferring liquids dropwise. Burette Burettes are devices used typically in analytical, quantitative chemistry applications for measuring liquid solution. Differing from a pipette since the sample quantity delivered is changeable, graduated Burettes are used heavily in titration experiments.