Information Disclosure Mechanism for Technological Protection Measures in China
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
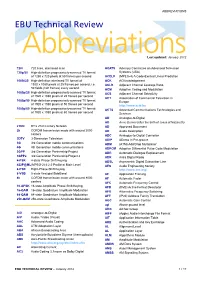
ABBREVIATIONS EBU Technical Review
ABBREVIATIONS EBU Technical Review AbbreviationsLast updated: January 2012 720i 720 lines, interlaced scan ACATS Advisory Committee on Advanced Television 720p/50 High-definition progressively-scanned TV format Systems (USA) of 1280 x 720 pixels at 50 frames per second ACELP (MPEG-4) A Code-Excited Linear Prediction 1080i/25 High-definition interlaced TV format of ACK ACKnowledgement 1920 x 1080 pixels at 25 frames per second, i.e. ACLR Adjacent Channel Leakage Ratio 50 fields (half frames) every second ACM Adaptive Coding and Modulation 1080p/25 High-definition progressively-scanned TV format ACS Adjacent Channel Selectivity of 1920 x 1080 pixels at 25 frames per second ACT Association of Commercial Television in 1080p/50 High-definition progressively-scanned TV format Europe of 1920 x 1080 pixels at 50 frames per second http://www.acte.be 1080p/60 High-definition progressively-scanned TV format ACTS Advanced Communications Technologies and of 1920 x 1080 pixels at 60 frames per second Services AD Analogue-to-Digital AD Anno Domini (after the birth of Jesus of Nazareth) 21CN BT’s 21st Century Network AD Approved Document 2k COFDM transmission mode with around 2000 AD Audio Description carriers ADC Analogue-to-Digital Converter 3DTV 3-Dimension Television ADIP ADress In Pre-groove 3G 3rd Generation mobile communications ADM (ATM) Add/Drop Multiplexer 4G 4th Generation mobile communications ADPCM Adaptive Differential Pulse Code Modulation 3GPP 3rd Generation Partnership Project ADR Automatic Dialogue Replacement 3GPP2 3rd Generation Partnership -

Intellectual Property Part 2 Pornography
Intellectual Property Part 2 Pornography By Jeremy Parmenter What is pornography Pornography is the explicit portrayal of sexual subject matter Can be found as books, magazines, videos The web has images, tube sites, and pay sites scattered with porn Statistics 12% of total websites are pornography websites 25% of total daily search engine requests are pornographic requests 42.7% of internet users who view pornography 34% internet users receive unwanted exposure to sexual material $4.9 billion in internet pornography sales 11 years old is the average age of first internet exposure to pornography Innovations ● Richard Gordon created an e-commerce start up in mid- 90s that was used on many sites, most notably selling Pamela Anderson/Tommey Lee sex tape ● Danni Ashe founded Danni's Hard Drive with one of the first streaming video without requiring a plug-in ● Adult content sites were one of the first to use traffic optimization by linking to similar sites ● Live chat during the early days of the web ● Pornographic companies were known to give away broadband devices to promote faster connections Negative Impacts ● Between 2001-2002 adult-oriented spam rose 450% ● Malware such as Trojans and video codecs occur most often on porn sites ● Domain hijacking, using fake documents and information to steal a site ● Pop-ups preventing users from leaving the site or infecting their computer ● Browser hijacking adware or spyware manipulating the browser to change home page or search engine to a bogus site, including pay-per-click adult site ● Accessibility -

Of Price Discriminiation, Rootkits and Flatrates
Of Price Discriminiation, Rootkits and Flatrates Volker Grassmuck Helmholtz-Zentrum für Kulturtechnik, Humboldt-University Berlin 19 February 2006 DRAFT VERSION – final version is slated for print publication Licensed under Creative Commons Share-Alike Germany 2.0 „Copyright owners continue to be ambivalent about the Internet. On the one hand, it represents a fantastic new medium for distribution; on the other, many in the publishing industry see it as one ‚giant, out of control copying machine.‘ ... The very technological advances that make rights management more difficult – the dramatic reduction in costs of copying and distribution – also offer a fantastic opportunity for owners of intellectual content.“1 Without scarcity there is no market. Information by its nature is a public good.2 Copyright law artificially creates scarcity by granting exclusive rights to it for a limited time. Media technology so far helped enforcability of those rights because the means of production and the means of distribution of informational goods were expensive and therefore scarce. The digital revolution does away with this scarcity. PC and Internet bring to virtually everyone the power of the printing press and the recording studio. Only now, information‘s defining qualities of non-rivalrousness and non-excludability come to full bearing. Zero cost for reproduction and distribution is indeed a fantastic value proposition for information vendors. Alas, it is undermined by the fact that for consumers the cost of copying and distribution is zero as well. Peer-to-peer networks show that transporting bits from A to B is now such a low-cost service that users can effortlessly provide it to each other. -

Abkürzungs-Liste ABKLEX
Abkürzungs-Liste ABKLEX (Informatik, Telekommunikation) W. Alex 1. Juli 2021 Karlsruhe Copyright W. Alex, Karlsruhe, 1994 – 2018. Die Liste darf unentgeltlich benutzt und weitergegeben werden. The list may be used or copied free of any charge. Original Point of Distribution: http://www.abklex.de/abklex/ An authorized Czechian version is published on: http://www.sochorek.cz/archiv/slovniky/abklex.htm Author’s Email address: [email protected] 2 Kapitel 1 Abkürzungen Gehen wir von 30 Zeichen aus, aus denen Abkürzungen gebildet werden, und nehmen wir eine größte Länge von 5 Zeichen an, so lassen sich 25.137.930 verschiedene Abkür- zungen bilden (Kombinationen mit Wiederholung und Berücksichtigung der Reihenfol- ge). Es folgt eine Auswahl von rund 16000 Abkürzungen aus den Bereichen Informatik und Telekommunikation. Die Abkürzungen werden hier durchgehend groß geschrieben, Akzente, Bindestriche und dergleichen wurden weggelassen. Einige Abkürzungen sind geschützte Namen; diese sind nicht gekennzeichnet. Die Liste beschreibt nur den Ge- brauch, sie legt nicht eine Definition fest. 100GE 100 GBit/s Ethernet 16CIF 16 times Common Intermediate Format (Picture Format) 16QAM 16-state Quadrature Amplitude Modulation 1GFC 1 Gigabaud Fiber Channel (2, 4, 8, 10, 20GFC) 1GL 1st Generation Language (Maschinencode) 1TBS One True Brace Style (C) 1TR6 (ISDN-Protokoll D-Kanal, national) 247 24/7: 24 hours per day, 7 days per week 2D 2-dimensional 2FA Zwei-Faktor-Authentifizierung 2GL 2nd Generation Language (Assembler) 2L8 Too Late (Slang) 2MS Strukturierte -

SONY BMG Music Entertainment. Respondent. This Assurance Of
In the Matter of: SONY BMG Music Entertainment. Respondent. This Assuranceof Voluntary Complianceor Discontinuance('oAssurance") is enteredinto by the AttorneysGeneral of the Statesof Alabama,Alaska, Arizona, Arkansas,Connecticut, Delawareo Florida,Idatro,Illinois, Indiana,Iow4 Kentucky,Louisian4 Maine, Maryland, Massachusetts, Michigan,Mississippi, Montana" Nebraska, Nevada, New Jersey,New Mexico,New york, North Carolina,North Dakota,Ohio, Oklahoma,Oregon, Pennsylvania, Rhode Island, South Dakota,Tennessee, Vermont, Virginia, Washington,West Virginia, Wisconsin,and Wyoming, and by the Attorney Generalfor the District of Columbia("the States"),acting pursuantto their respectiveconsumet protection statutes,r and SONY BMG Music Entertainment(.SONy I ALABAMA: AlabamaDeceptive Trade Practices Act, Ala. Codeg 8-19-1,et seq.;ALASKA: Unfair TradePractices and Consumer Protection Act, AS 45.50.471,-etseq.;ARIZbNA: Arizonaconsumer lrf{191, A.R.s. $ 44-1521et seq.;ARKANSAS: Ark. stat.Ann., g 4-gg- l0l et seq.;COIYNECTICUT: Conn.Gen. Stat. $ 42-110a,et seq.; DELAWARE: Consumer FraudAct,6 Del.C.$251l, et seq.;DISTRICT OF COLUMBI* Districrof Columbia ConsumerProtection Procedures Act, D.C. Code$ 28-3901et seq.; FLORIDA: Deceptiveand Unfair TradePractices Act, Fla. Stat.Ch. 501.201et seq.;IDAHO: IdahoConsumer protection Act, IdahoCode $ 48-601,et seq.;ILLINOIS: ConsumerFraud and Deceptive Business PracticesAct, 815ILcs 505/l et seq.;INDIANA: Ind.code Ann. $24-5-b-5-l;IowA: Iowa ConsumerFraud Act, Iowa Codesection714.16; KENTUCKY: ConsumerProtection Act, Ky. Rev. Stat.$$ 367.1l0 to 367.990;LOUISIANA: Unfair Tradepractices and Consumer ProtectionLaw,La. Rev. Stat.Ann. $$51:1401to 5|:1420;MAINE: MaineUnfair Trade PracticesAct, 5 M.R.S.A.sections 207 and209;MARYLANDI MarylandConsumer protection Act, Md. -

The European IP Bulletin
The European IP Bulletin The Intellectual Property, Media & Technology Department Issue 28, January 2006 McDermott Will & Emery UK LLP 7 Bishopsgate London EC2N 3AR Tel: +44 20 7577 6900 Fax: +44 20 7577 6950 www.mwe.com www.mwe.com/london Boston Brussels Chicago Düsseldorf London Los Angeles Miami Munich New York Orange County Rome San Diego Silicon Valley Washington, D.C. SUMMARY OF PAGE CONTENTS NO. HOT TOPICS 1. WORLD TRADE ORGANISATION MEMBERS AGREE TO AMEND THE 1 TRIPS AGREEMENT ON PATENTS AND PUBLIC HEALTH The decision of the General Council of 6 December 2005 on the amendment of the TRIPS Agreement makes the flexibilities contained in the 2003 decision on patents and public health permanent. This in effect will lead to the first amendment of a core WTO Agreement. 2. UK CHANCELLOR ANNOUNCES INTELLECTUAL PROPERTY REVIEW 2 As part of his Pre-Budget Report Package, the Chancellor of the Exchequer, Gordon Brown, has announced the launch of an independent review of intellectual property in the UK, to be headed by the former editor of the Financial Times. COPYRIGHT 3. SONY BMG’S ANTI-PIRACY SOFTWARE IN BIG TROUBLE 3 Sony BMG’s trouble started immediately following Windows programming expert Mark Russinovich's discovery that Sony’s anti- piracy software used virus-like techniques to stop illegal copies being made. There have been several class action lawsuits launched against both Sony BMG and First4Internet. Widespread pressure has made Sony BMG take actions to settle the dispute. 4. EVALUATION OF EU RULES ON DATABASES 4 The European Commission has published an evaluation of the protection EU law gives to databases. -

DRM — “Digital Rights” Or “Digital Restrictions” Management?
DIGITAL RIGHTS MANAGEMENT DRM — “digital rights” or “digital restrictions” management? Richard Leeming Red Bee Media If correctly applied, DRM can be likened to a motorway, providing a seamless high- speed route to content, enabling people to get the content they want, where they want it, quickly and easily. However, if badly applied, heavy handed and overly restrictive, DRM is more like a traffic jam – denying people access to the content they want and crucially denying rights-holders the revenue they want. This article looks at some of the proprietary DRM systems currently available and argues that we need to start thinking hard about when and how we apply DRM to our precious content. In 2006, music lovers worldwide have been celebrating the 250th anniversary of Mozart’s birth. Although he only lived for 35 years, Mozart composed more than 600 pieces of classical music – most of which are still hugely popular today. But it’s perhaps something of a surprise to discover that one of the key moments of Mozart’s early career would today count as piracy and be prevented by digital-rights technology. As a 14-year-old, Mozart travelled to the Vatican and heard Gregorio Allegri’s Miserere. This piece of music had long been closely guarded by the Vatican and it was forbidden to transcribe it: if you did, you would be excommunicated. Whether Mozart knew this is unknown but, having heard it once, he transcribed it from memory and it became published in London, thus breaking the Vatican’s ban. This is perhaps one of the earliest-known examples of content rights management being overturned. -

" Who Controls the Vocabulary, Controls the Knowledge"
Acronyms from Future-Based Consultancy & Solutions "Translation" of some Business, Finance, ICDT acronyms (including several SAP ones), initialims, tech term oddities and techronyms, loaded words and buzzwords to ease the reading of courses, books, magazines and papers: see "anacronym", "ASS" and many others ... (third main version since 1997) ( www.fbc-e.com , updated & corrected twice a month. Release 02-10-2009) " Who controls the vocabulary , 6170+ controls the knowledge " George ORWELL in "1984" Instruction To ease your researches , we are inviting you to use the " search " function within the Menu " edit " Pour faciliter vos recherches, utilisez la fonction " rechercher " disponible dans le menu " Edition " Information Underligned names are identifying authors, editors and / or copyrighted applications ©, ®, ™ FBWPA Free Business White Page Available (www.fbc-e.com ) Acronym Rose salmon is related to acronyms and assimilated terms and concepts. IL / InLin Internet Lingo also called " PC talk" Intelligence Light green color is related to intelligence, business intelligence ( BI , CI ) FBC>s Yellow color is related to FBC>s concepts and methodologies (more on www.fbc-e.com ) Finance Deep blue color is related to Finance and Accounting ( FI ) Note: BOLD acronyms KM Deep green color is related to Knowledge Management ( KM ) and texts are "translated" HR & R Lemon green color is related to HR and recruitment in the list. Mobility Light blue color is related to mobile communication ( MoMo ) Security Red color is related to security and risks management ( RM ) Note : US spelling Virtual Pink color is related to virtual / virtuality ( VR ) & ampersand $$$ temporary files Feel free to copy and distribute this "computer-babble *.001 Hayes JT Fax translator" provided that it is distributed only in its 0 Day FTP server supposed to be moved within original and unmodified state with our name, address, the next 24 hours to another IP . -

UNITED STATES DISTRICT COURT SOUTHERN DISTRICT of NEW YORK in Re: SONY BMG CD TECHNOLOGIES LITIGATION Case No. 1:05-Cv-09575-NR
UNITED STATES DISTRICT COURT SOUTHERN DISTRICT OF NEW YORK In re: SONY BMG CD Case No. 1:05-cv-09575-NRB TECHNOLOGIES LITIGATION MOTION AND MEMORANDUM OF LAW IN SUPPORT OF PLAINTIFFS’ APPLICATION FOR PRELIMINARY APPROVAL OF CLASS ACTION SETTLEMENT GIRARD GIBBS KAMBER & ASSOCIATES LLC & De BARTOLOMEO LLP Scott A. Kamber (SK-5794) Daniel C. Girard (Pro Hac Vice) 19 Fulton Street, Suite 400 Jonathan K. Levine (JL-8390) New York, NY 10038 Elizabeth C. Pritzker (Pro Hac Vice) Telephone: (212) 571-2000 Aaron M. Sheanin (Pro Hac Vice) 601 California Street, Suite 1400 San Francisco, California 94108 Telephone: (415) 981-4800 Plaintiffs’ Co-Lead Counsel www.girardgibbs.com TABLE OF CONTENTS I. INTRODUCTION ............................................................................................................. 1 II. BACKGROUND OF THE LITIGATION.......................................................................... 3 A. The Nature Of SONY BMG’s Content Protection Software.............................................. 3 B. XCP CDs And Software Expose Computers To Security Vulnerabilities ......................... 4 C. MediaMax CD Software Installs Without Consent And Exposes Computers To Security Vulnerabilities .............................................................................. 6 D. The Class Action Litigation................................................................................................ 6 III. THE PROPOSED SETTLEMENT..................................................................................... 8 A. The -

Contemplating a Digital First-Sale Doctrine Damien A
William Mitchell Law Review Volume 40 | Issue 2 Article 10 2014 Is Buying Digital Content Just Renting for Life: Contemplating a Digital First-sale Doctrine Damien A. Riehl Jumi Kassim Follow this and additional works at: http://open.mitchellhamline.edu/wmlr Recommended Citation Riehl, Damien A. and Kassim, Jumi (2014) "Is Buying Digital Content Just Renting for Life: Contemplating a Digital First-sale Doctrine," William Mitchell Law Review: Vol. 40: Iss. 2, Article 10. Available at: http://open.mitchellhamline.edu/wmlr/vol40/iss2/10 This Article is brought to you for free and open access by the Law Reviews and Journals at Mitchell Hamline Open Access. It has been accepted for inclusion in William Mitchell Law Review by an authorized administrator of Mitchell Hamline Open Access. For more information, please contact [email protected]. © Mitchell Hamline School of Law Riehl and Kassim: Is Buying Digital Content Just Renting for Life: Contemplating a IS “BUYING” DIGITAL CONTENT JUST “RENTING” FOR LIFE? CONTEMPLATING A DIGITAL FIRST-SALE DOCTRINE Damien Riehl† and Jumi Kassim†† I. INTRODUCTION ...................................................................... 784 II. HISTORY OF THE FIRST-SALE DOCTRINE ................................ 784 A. The First-Sale Doctrine’s Establishment ............................... 784 B. The First-Sale Doctrine’s Expansion.................................... 786 C. The First-Sale Doctrine’s Contraction .................................. 787 III. PURE DIGITAL CONTENT MAY BE DIFFERENT ....................... -

Unclassified DSTI/CP(2005)15/FINAL
Unclassified DSTI/CP(2005)15/FINAL Organisation de Coopération et de Développement Economiques Organisation for Economic Co-operation and Development 18-Apr-2006 ___________________________________________________________________________________________ English - Or. English DIRECTORATE FOR SCIENCE, TECHNOLOGY AND INDUSTRY COMMITTEE ON CONSUMER POLICY Unclassified DSTI/CP(2005)15/FINAL REPORT ON DISCLOSURE ISSUES RELATED TO THE USE OF COPY CONTROL AND DIGITAL RIGHTS MANAGEMENT TECHNOLOGIES English - Or. English JT03207632 Document complet disponible sur OLIS dans son format d'origine Complete document available on OLIS in its original format DSTI/CP(2005)15/FINAL FOREWORD This report was prepared by the Secretariat with comments by the Committee on Consumer Policy (CCP). The report was declassified by the CCP at its 71st Session on 29-30 March 2006. It is published on the responsibility of the Secretary-General of the OECD. © OECD / OCDE 2006 2 DSTI/CP(2005)15/FINAL TABLE OF CONTENTS FOREWORD 2 REPORT ON DISCLOSURE ISSUES RELATED TO THE USE OF COPY CONTROL AND DIGITAL RIGHTS MANAGEMENT TECHNOLOGIES 4 I. Introduction 4 II. Practical applications of digital rights management and copy control technologies 5 A. Copy-protected CDs 6 B. Music downloads 8 C. DVD regional coding 9 III. Issues for consideration 11 IV. Conclusion 13 3 DSTI/CP(2005)15/FINAL REPORT ON DISCLOSURE ISSUES RELATED TO THE USE OF COPY CONTROL AND DIGITAL RIGHTS MANAGEMENT TECHNOLOGIES I. Introduction Prepared by the OECD Committee on Consumer Policy (CCP), this report analyses the disclosure issues raised by the use of digital rights management (DRM) and copy control technologies (CCTs) to protect intellectual property rights. More specifically, it examines the kinds of restrictions that are commonly placed on access or use of protected material (for example, restrictions on making back-ups or private copies) and the disclosures provided to inform consumers about these restrictions. -

Tesina Costante Luca
UNIVERSITÀ DEGLI STUDI DI SALERNO FACOLTÀ DI SCIENZE NATURALI FISICHE E MATEMATICHE Corso di laurea in Informatica Tesina di Sicurezza su Reti 2 Digital Rights Management Professore Studente Alfredo De Santis Costante Luca Matr. 0521000838 Anno Accademico 2008/2009 INDICE INTRODUZIONE ............................................................................................................ 1 1.1. Storia .................................................................................................................. 2 1.2. Dominio di applicazione .................................................................................... 3 1.2.1. Attivazione del software ............................................................................. 3 1.2.2. Audio e Film ............................................................................................... 4 1.2.3. Internet music shop ..................................................................................... 5 1.2.4. Videogiochi ................................................................................................. 6 1.2.5. EBook ......................................................................................................... 6 1.3. Opinioni contrarie .............................................................................................. 7 CAPITOLO 2: CD & DVD .............................................................................................. 8 2.1. CD .....................................................................................................................