Contents in This Issue
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

A the Hacker
A The Hacker Madame Curie once said “En science, nous devons nous int´eresser aux choses, non aux personnes [In science, we should be interested in things, not in people].” Things, however, have since changed, and today we have to be interested not just in the facts of computer security and crime, but in the people who perpetrate these acts. Hence this discussion of hackers. Over the centuries, the term “hacker” has referred to various activities. We are familiar with usages such as “a carpenter hacking wood with an ax” and “a butcher hacking meat with a cleaver,” but it seems that the modern, computer-related form of this term originated in the many pranks and practi- cal jokes perpetrated by students at MIT in the 1960s. As an example of the many meanings assigned to this term, see [Schneier 04] which, among much other information, explains why Galileo was a hacker but Aristotle wasn’t. A hack is a person lacking talent or ability, as in a “hack writer.” Hack as a verb is used in contexts such as “hack the media,” “hack your brain,” and “hack your reputation.” Recently, it has also come to mean either a kludge, or the opposite of a kludge, as in a clever or elegant solution to a difficult problem. A hack also means a simple but often inelegant solution or technique. The following tentative definitions are quoted from the jargon file ([jargon 04], edited by Eric S. Raymond): 1. A person who enjoys exploring the details of programmable systems and how to stretch their capabilities, as opposed to most users, who prefer to learn only the minimum necessary. -

Undergraduate Report
UNDERGRADUATE REPORT Attack Evolution: Identifying Attack Evolution Characteristics to Predict Future Attacks by MaryTheresa Monahan-Pendergast Advisor: UG 2006-6 IINSTITUTE FOR SYSTEMSR RESEARCH ISR develops, applies and teaches advanced methodologies of design and analysis to solve complex, hierarchical, heterogeneous and dynamic problems of engineering technology and systems for industry and government. ISR is a permanent institute of the University of Maryland, within the Glenn L. Martin Institute of Technol- ogy/A. James Clark School of Engineering. It is a National Science Foundation Engineering Research Center. Web site http://www.isr.umd.edu Attack Evolution 1 Attack Evolution: Identifying Attack Evolution Characteristics To Predict Future Attacks MaryTheresa Monahan-Pendergast Dr. Michel Cukier Dr. Linda C. Schmidt Dr. Paige Smith Institute of Systems Research University of Maryland Attack Evolution 2 ABSTRACT Several approaches can be considered to predict the evolution of computer security attacks, such as statistical approaches and “Red Teams.” This research proposes a third and completely novel approach for predicting the evolution of an attack threat. Our goal is to move from the destructive nature and malicious intent associated with an attack to the root of what an attack creation is: having successfully solved a complex problem. By approaching attacks from the perspective of the creator, we will chart the way in which attacks are developed over time and attempt to extract evolutionary patterns. These patterns will eventually -

Information Disclosure Mechanism for Technological Protection Measures in China
Journal of Intellectual Property Rights Vol 17, November 2012, pp 532-538 Information Disclosure Mechanism for Technological Protection Measures in China Lili Zhao† Center for China Information Security Law, Xi’an Jiao tong University, Shaanxi Xi’an, P R China 710 049 Received 12 February 2012, revised 21 May 2012 With increasing cases of digital works being copied and pirated, technological protection measures have been greatly favoured by copyright owners for protecting the intellectual property in their digital works, while ensuring that these works can be used and disseminated. However, when any copyright owner or supplier fails to disclose the information of technological protection measures appropriately or effectively, damages such as privacy violations, security breaches and unfair competition may be caused to the public. Therefore, it is necessary to establish an information disclosure mechanism for technological protection measures, make the labeling obligation with regard to technological protection measures by copyright owners apparent and warning to security risks obligatory by legislation; effectively guarding against information security threats from the technological protection measures. Keywords: Technological protection measures, TPM, information disclosure, label and warning The advance of digital technologies make many information security, it is necessary to integrate such acts things become possible, including the copy and in a standardized, normalized and legal manner. dissemination of commercially valuable digital works Therefore, to further prevent copyright owners from through global digital network. Particularly, among using insecure or untested software, protect information the copyright owners of entertainment industry, security and prohibit the abuse of TPMs; disclosure technological protection measures (TPMs) have been obligations should be established for the right holders of regarded as a necessary creation to help digital works TPMs in the form of legislation. -

CONTENTS in THIS ISSUE Fighting Malware and Spam
MARCH 2008 Fighting malware and spam CONTENTS IN THIS ISSUE 2 COMMENT EVASIVE ACTION Home (page) renovations Pandex has attracted very little attention from the media and generated little 3 NEWS discussion between malware Botherders herded researchers and among the 29A folds general populace. Chandra Prakash and Adam Thomas provide an overview of the Pandex operation and take an in-depth look at VIRUS PREVALENCE TABLE 3 the underlying code that has allowed this malware to evade detection for so long. 4 MALWARE ANALYSIS page 4 Pandex: the botnet that could PACKING A PUNCH In the fi nal part of the series on exepacker 9 FEATURE blacklisting, Robert Neumann takes a look at how all the processing and analysis techniques are put Exepacker blacklisting part 3 into practice in a real-life situation. page 9 15 CONFERENCE REPORT AVG TURNS 8 Black Hat DC and CCC 24C3 John Hawes gets his hands on a preview version of the latest offering from AVG. 18 PRODUCT REVIEW page 18 AVG Internet Security 8 22 END NOTES & NEWS This month: anti-spam news and events, and Ken Simpson considers the implications of rising spam volume despite increasing accuracy of content fi lters. ISSN 1749-7027 COMMENT ‘It is hoped that within all sizes of business. It is hoped that the comment facility will promote discussion among visitors and that the comment facility in some cases the more knowledgeable of VB’s readers will promote will be able to guide and assist those less well versed in discussion among the complexities of anti-malware technologies. -
ABBREVIATIONS EBU Technical Review
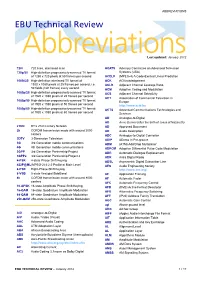
ABBREVIATIONS EBU Technical Review AbbreviationsLast updated: January 2012 720i 720 lines, interlaced scan ACATS Advisory Committee on Advanced Television 720p/50 High-definition progressively-scanned TV format Systems (USA) of 1280 x 720 pixels at 50 frames per second ACELP (MPEG-4) A Code-Excited Linear Prediction 1080i/25 High-definition interlaced TV format of ACK ACKnowledgement 1920 x 1080 pixels at 25 frames per second, i.e. ACLR Adjacent Channel Leakage Ratio 50 fields (half frames) every second ACM Adaptive Coding and Modulation 1080p/25 High-definition progressively-scanned TV format ACS Adjacent Channel Selectivity of 1920 x 1080 pixels at 25 frames per second ACT Association of Commercial Television in 1080p/50 High-definition progressively-scanned TV format Europe of 1920 x 1080 pixels at 50 frames per second http://www.acte.be 1080p/60 High-definition progressively-scanned TV format ACTS Advanced Communications Technologies and of 1920 x 1080 pixels at 60 frames per second Services AD Analogue-to-Digital AD Anno Domini (after the birth of Jesus of Nazareth) 21CN BT’s 21st Century Network AD Approved Document 2k COFDM transmission mode with around 2000 AD Audio Description carriers ADC Analogue-to-Digital Converter 3DTV 3-Dimension Television ADIP ADress In Pre-groove 3G 3rd Generation mobile communications ADM (ATM) Add/Drop Multiplexer 4G 4th Generation mobile communications ADPCM Adaptive Differential Pulse Code Modulation 3GPP 3rd Generation Partnership Project ADR Automatic Dialogue Replacement 3GPP2 3rd Generation Partnership -

Intellectual Property Part 2 Pornography
Intellectual Property Part 2 Pornography By Jeremy Parmenter What is pornography Pornography is the explicit portrayal of sexual subject matter Can be found as books, magazines, videos The web has images, tube sites, and pay sites scattered with porn Statistics 12% of total websites are pornography websites 25% of total daily search engine requests are pornographic requests 42.7% of internet users who view pornography 34% internet users receive unwanted exposure to sexual material $4.9 billion in internet pornography sales 11 years old is the average age of first internet exposure to pornography Innovations ● Richard Gordon created an e-commerce start up in mid- 90s that was used on many sites, most notably selling Pamela Anderson/Tommey Lee sex tape ● Danni Ashe founded Danni's Hard Drive with one of the first streaming video without requiring a plug-in ● Adult content sites were one of the first to use traffic optimization by linking to similar sites ● Live chat during the early days of the web ● Pornographic companies were known to give away broadband devices to promote faster connections Negative Impacts ● Between 2001-2002 adult-oriented spam rose 450% ● Malware such as Trojans and video codecs occur most often on porn sites ● Domain hijacking, using fake documents and information to steal a site ● Pop-ups preventing users from leaving the site or infecting their computer ● Browser hijacking adware or spyware manipulating the browser to change home page or search engine to a bogus site, including pay-per-click adult site ● Accessibility -

Tangled Web : Tales of Digital Crime from the Shadows of Cyberspace
TANGLED WEB Tales of Digital Crime from the Shadows of Cyberspace RICHARD POWER A Division of Macmillan USA 201 West 103rd Street, Indianapolis, Indiana 46290 Tangled Web: Tales of Digital Crime Associate Publisher from the Shadows of Cyberspace Tracy Dunkelberger Copyright 2000 by Que Corporation Acquisitions Editor All rights reserved. No part of this book shall be reproduced, stored in a Kathryn Purdum retrieval system, or transmitted by any means, electronic, mechanical, pho- Development Editor tocopying, recording, or otherwise, without written permission from the Hugh Vandivier publisher. No patent liability is assumed with respect to the use of the infor- mation contained herein. Although every precaution has been taken in the Managing Editor preparation of this book, the publisher and author assume no responsibility Thomas Hayes for errors or omissions. Nor is any liability assumed for damages resulting from the use of the information contained herein. Project Editor International Standard Book Number: 0-7897-2443-x Tonya Simpson Library of Congress Catalog Card Number: 00-106209 Copy Editor Printed in the United States of America Michael Dietsch First Printing: September 2000 Indexer 02 01 00 4 3 2 Erika Millen Trademarks Proofreader Benjamin Berg All terms mentioned in this book that are known to be trademarks or ser- vice marks have been appropriately capitalized. Que Corporation cannot Team Coordinator attest to the accuracy of this information. Use of a term in this book should Vicki Harding not be regarded as affecting the validity of any trademark or service mark. Design Manager Warning and Disclaimer Sandra Schroeder Every effort has been made to make this book as complete and as accurate Cover Designer as possible, but no warranty or fitness is implied. -

The Norman Book on Computer Viruses Ii Z the Norman Book on Computer Viruses
The Norman Book on Computer Viruses ii z The Norman Book on Computer Viruses Norman ASA is not liable for any other form of loss or damage arising from use of the documentation or from errors or deficiencies therein, including but not limited to loss of earnings. In particular, and without the limitations imposed by the licensing agreement with regard to any special use or purpose, Norman ASA will in no event be liable for loss of profits or other commercial damage including but not limited to incidental or consequential damages. The information in this document as well as the functionality of the software is subject to change without notice. No part of this documentation may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording or information storage and retrieval systems, for any purpose other than the purchaser's personal use, without the explicit written permission of Norman ASA. Contributors to The Norman Book on Viruses: Snorre Fagerland, Sylvia Moon, Kenneth Walls, Carl Bretteville Edited by Camilla Jaquet and Yngve Ness The Norman logo is a registered trademark of Norman ASA. Names of products mentioned in this documentation are either trademarks or registered trademarks of their respective owners. They are mentioned for identification purposes only. Norman documentation is Copyright © 1990-2002 Norman ASA. All rights reserved. October 2001 Copyright © 1990-2002 Norman z iii Norman Offices Norman Data Defense Systems Pty Ltd 6 Sarton Road, Clayton, Victoria, 3168 Australia. Tel: +61 3 9562 7655 Fax: +61 3 9562 9663 E-mail: [email protected] Web: http://www.norman.com.au Norman Data Defense Systems A/S Dronningensgade 23, DK-5000 Odense C, Denmark Tel. -

UTTARAKHAND OPEN UNIVERSITY Teen Pani Bypass Road, Near Transport Nagar, Haldwani -263139 Phone No- 05946 - 261122, 261123 Toll Free No
CYBER CRIMES AND CONSUMER PROTECTION IN CYBERSPACE CYL-104 [1] CYL- 104 Cyber Crimes And Consumer Protection in Cyber Space School of Law UTTARAKHAND OPEN UNIVERSITY Teen Pani Bypass Road, Near Transport Nagar, Haldwani -263139 Phone No- 05946 - 261122, 261123 Toll Free No. 18001804025 Fax No.- 05946-264232, Email- [email protected], http://uou.ac.in Uttarakhand Open University CYBER CRIMES AND CONSUMER PROTECTION IN CYBERSPACE CYL-104 [2] BOARD OF STUDIES Professor Girija Prasad Pande, Director, School of Law, Uttarakhand Open University, Haldwani, Nainital. Professor J.S.Bisht, Faculty of Law,S.S. Jeena Campus, Almora,Kumaun University, Nainital, Uttarakhand. Professor B.P. Maithani, Former RTI Advisor, Government of Uttarakhand Mr. Deepankur Joshi, Coordinator School of Law, Uttarakhand Open University, Haldwani, (Nainital). UNIT WRITING UNIT WRITERS UNIT [1] Dr. Razit Sharma, Assistant Professor, Unit- 1,2,3,4 Law College, Uttaranchal University, Dehradun Uttarakhand [2] Ms. Sapna Agarwal, Advocate High Court of Uttarakhand, Unit- 5,6,7 Nainital [3 Mr. Rajeev Bhatt, Advocate High Court of Uttarakhand, Ex. RTI Advisor Kumaun University Nainital, Ex. Assistant Professor Unity Unit- 8 ,9,10 Law College Rudrapur [4] Dr. Sushim Shukla, Assistant Professor, Unit- 11, 12, 13 Law College, Uttaranchal University, Dehradun Uttarakhand EDITOR Mr. Deepankur Joshi, Coordinator, School of Law, Uttarakhand Open University, Haldwani, (Nainital) Copyright © Uttarakhand Open University, Haldwani, Nainital Edition- 2018, Pre Publication copy for Limited Circulation ISBN- Publication- Directorate of Studies and Publication, Uttarakhand Open University, Haldwani, Nainital. E- Mail: [email protected] . Uttarakhand Open University CYBER CRIMES AND CONSUMER PROTECTION IN CYBERSPACE CYL-104 [3] POST GRADUATE DIPLOMA IN CYBER LAW CYL- 104 CYBERCRIMES AND CONSUMER PROTECTION IN CYBER SPACE INDEX S. -

Computer Viruses, in Order to Detect Them
Behaviour-based Virus Analysis and Detection PhD Thesis Sulaiman Amro Al amro This thesis is submitted in partial fulfilment of the requirements for the degree of Doctor of Philosophy Software Technology Research Laboratory Faculty of Technology De Montfort University May 2013 DEDICATION To my beloved parents This thesis is dedicated to my Father who has been my supportive, motivated, inspired guide throughout my life, and who has spent every minute of his life teaching and guiding me and my brothers and sisters how to live and be successful. To my Mother for her support and endless love, daily prayers, and for her encouragement and everything she has sacrificed for us. To my Sisters and Brothers for their support, prayers and encouragements throughout my entire life. To my beloved Family, My Wife for her support and patience throughout my PhD, and my little boy Amro who has changed my life and relieves my tiredness and stress every single day. I | P a g e ABSTRACT Every day, the growing number of viruses causes major damage to computer systems, which many antivirus products have been developed to protect. Regrettably, existing antivirus products do not provide a full solution to the problems associated with viruses. One of the main reasons for this is that these products typically use signature-based detection, so that the rapid growth in the number of viruses means that many signatures have to be added to their signature databases each day. These signatures then have to be stored in the computer system, where they consume increasing memory space. Moreover, the large database will also affect the speed of searching for signatures, and, hence, affect the performance of the system. -

"Year 2000 Y2K" December 28, 1999
NIPC ADVISORY 99-031 "Year 2000 Y2K" December 28, 1999 Introduction Large-scale U.S. infrastructure disruptions are not expected from "Y2K failures" during the Y2K transition period. However we are prepared for a possible increase in real or reported criminal cyber activity (such as hacking and spreading computer viruses), considering the heightened awareness of and media focus on malicious activity during the Y2K period. Any increased criminal activity during the Y2K period could raise the level of problems in infrastructure systems, adding to genuine Y2K-generated issues and the normal level of infrastructure concerns. We anticipate encountering both known and new viruses and hacking exploits. We could see the dissemination of several new and possibly destructive viruses, and the successful exploitation of both corporate and government information systems. But even these possibilities reflect only a larger assembly of the same kinds of malicious activity seen and addressed every day. Finally, known and possible extremist or apocalyptic terrorist activity in the United States by individuals or groups suggests the possibility of threats to domestic infrastructures. For example, the media have reported arrests of certain individuals allegedly planning violent actions against electric power and oil and gas facilities. These indications of possible threats to our infrastructures warrant an increased vigilance to protect against both cyber and physical threats to our nation's critical infrastructures. Summary The Y2K Transition might be seen by potential malefactors as an unprecedented opportunity for malicious code release and associated publicity, where a new and significant exploit can achieve a widespread notoriety in the information security and hacker world. -

Chapter 3: Viruses, Worms, and Blended Threats
Chapter 3 Chapter 3: Viruses, Worms, and Blended Threats.........................................................................46 Evolution of Viruses and Countermeasures...................................................................................46 The Early Days of Viruses.................................................................................................47 Beyond Annoyance: The Proliferation of Destructive Viruses .........................................48 Wiping Out Hard Drives—CIH Virus ...................................................................48 Virus Programming for the Masses 1: Macro Viruses...........................................48 Virus Programming for the Masses 2: Virus Generators.......................................50 Evolving Threats, Evolving Countermeasures ..................................................................51 Detecting Viruses...................................................................................................51 Radical Evolution—Polymorphic and Metamorphic Viruses ...............................53 Detecting Complex Viruses ...................................................................................55 State of Virus Detection.........................................................................................55 Trends in Virus Evolution..................................................................................................56 Worms and Vulnerabilities ............................................................................................................57