SONY BMG Music Entertainment. Respondent. This Assurance Of
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Information Disclosure Mechanism for Technological Protection Measures in China
Journal of Intellectual Property Rights Vol 17, November 2012, pp 532-538 Information Disclosure Mechanism for Technological Protection Measures in China Lili Zhao† Center for China Information Security Law, Xi’an Jiao tong University, Shaanxi Xi’an, P R China 710 049 Received 12 February 2012, revised 21 May 2012 With increasing cases of digital works being copied and pirated, technological protection measures have been greatly favoured by copyright owners for protecting the intellectual property in their digital works, while ensuring that these works can be used and disseminated. However, when any copyright owner or supplier fails to disclose the information of technological protection measures appropriately or effectively, damages such as privacy violations, security breaches and unfair competition may be caused to the public. Therefore, it is necessary to establish an information disclosure mechanism for technological protection measures, make the labeling obligation with regard to technological protection measures by copyright owners apparent and warning to security risks obligatory by legislation; effectively guarding against information security threats from the technological protection measures. Keywords: Technological protection measures, TPM, information disclosure, label and warning The advance of digital technologies make many information security, it is necessary to integrate such acts things become possible, including the copy and in a standardized, normalized and legal manner. dissemination of commercially valuable digital works Therefore, to further prevent copyright owners from through global digital network. Particularly, among using insecure or untested software, protect information the copyright owners of entertainment industry, security and prohibit the abuse of TPMs; disclosure technological protection measures (TPMs) have been obligations should be established for the right holders of regarded as a necessary creation to help digital works TPMs in the form of legislation. -
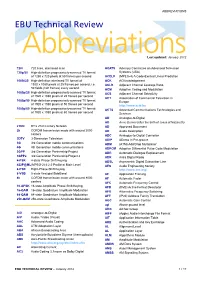
ABBREVIATIONS EBU Technical Review
ABBREVIATIONS EBU Technical Review AbbreviationsLast updated: January 2012 720i 720 lines, interlaced scan ACATS Advisory Committee on Advanced Television 720p/50 High-definition progressively-scanned TV format Systems (USA) of 1280 x 720 pixels at 50 frames per second ACELP (MPEG-4) A Code-Excited Linear Prediction 1080i/25 High-definition interlaced TV format of ACK ACKnowledgement 1920 x 1080 pixels at 25 frames per second, i.e. ACLR Adjacent Channel Leakage Ratio 50 fields (half frames) every second ACM Adaptive Coding and Modulation 1080p/25 High-definition progressively-scanned TV format ACS Adjacent Channel Selectivity of 1920 x 1080 pixels at 25 frames per second ACT Association of Commercial Television in 1080p/50 High-definition progressively-scanned TV format Europe of 1920 x 1080 pixels at 50 frames per second http://www.acte.be 1080p/60 High-definition progressively-scanned TV format ACTS Advanced Communications Technologies and of 1920 x 1080 pixels at 60 frames per second Services AD Analogue-to-Digital AD Anno Domini (after the birth of Jesus of Nazareth) 21CN BT’s 21st Century Network AD Approved Document 2k COFDM transmission mode with around 2000 AD Audio Description carriers ADC Analogue-to-Digital Converter 3DTV 3-Dimension Television ADIP ADress In Pre-groove 3G 3rd Generation mobile communications ADM (ATM) Add/Drop Multiplexer 4G 4th Generation mobile communications ADPCM Adaptive Differential Pulse Code Modulation 3GPP 3rd Generation Partnership Project ADR Automatic Dialogue Replacement 3GPP2 3rd Generation Partnership -

Intellectual Property Part 2 Pornography
Intellectual Property Part 2 Pornography By Jeremy Parmenter What is pornography Pornography is the explicit portrayal of sexual subject matter Can be found as books, magazines, videos The web has images, tube sites, and pay sites scattered with porn Statistics 12% of total websites are pornography websites 25% of total daily search engine requests are pornographic requests 42.7% of internet users who view pornography 34% internet users receive unwanted exposure to sexual material $4.9 billion in internet pornography sales 11 years old is the average age of first internet exposure to pornography Innovations ● Richard Gordon created an e-commerce start up in mid- 90s that was used on many sites, most notably selling Pamela Anderson/Tommey Lee sex tape ● Danni Ashe founded Danni's Hard Drive with one of the first streaming video without requiring a plug-in ● Adult content sites were one of the first to use traffic optimization by linking to similar sites ● Live chat during the early days of the web ● Pornographic companies were known to give away broadband devices to promote faster connections Negative Impacts ● Between 2001-2002 adult-oriented spam rose 450% ● Malware such as Trojans and video codecs occur most often on porn sites ● Domain hijacking, using fake documents and information to steal a site ● Pop-ups preventing users from leaving the site or infecting their computer ● Browser hijacking adware or spyware manipulating the browser to change home page or search engine to a bogus site, including pay-per-click adult site ● Accessibility -

DISTRIBUTING PRODUCTIVE PLAY: a MATERIALIST ANALYSIS of STEAM Daniel Joseph Doctor of Philosophy Ryerson University, 2017
DISTRIBUTING PRODUCTIVE PLAY: A MATERIALIST ANALYSIS OF STEAM by Daniel Joseph Master of Arts, Ryerson University and York University, Toronto, Ontario 2011 Bachelor of Arts, Wilfrid Laurier University, Waterloo, Ontario, 2009 A dissertation presented to Ryerson University and York University in partial fulfillment for the degree of Doctor of Philosophy in the program of Communication and Culture Toronto, Ontario, Canada, 2017 © Daniel Joseph, 2017 AUTHOR'S DECLARATION FOR ELECTRONIC SUBMISSION OF A DISSERTATION I hereby declare that I am the sole author of this dissertation. This is a true copy of the dissertation, including any required final revisions, as accepted by my examiners. I authorize Ryerson University to lend this dissertation to other institutions or individuals for the purpose of scholarly research. I further authorize Ryerson University to reproduce this dissertation by photocopying or by other means, in total or in part, at the request of other institutions or individuals for the purpose of scholarly research. I understand that my dissertation may be made electronically available to the public. ii Abstract DISTRIBUTING PRODUCTIVE PLAY: A MATERIALIST ANALYSIS OF STEAM Daniel Joseph Doctor of Philosophy Ryerson University, 2017 Valve Corporation’s digital game distribution platform, Steam, is the largest distributor of games on personal computers, analyzed here as a site where control over the production, design and use of digital games is established. Steam creates and exercises processes and techniques such as monopolization and enclosure over creative products, online labour, and exchange among game designers. Stuart Hall’s encoding/decoding framework places communication at the centre of the political economy, here of digital commodities distributed and produced by online platforms like Steam. -

Compilation of Manuals, Guidelines, and Directories in the Area of Intellectual Property (Ip) Portfolio Management
DRAFT FOR DISCUSSION COMPILATION OF MANUALS, GUIDELINES, AND DIRECTORIES IN THE AREA OF INTELLECTUAL PROPERTY (IP) PORTFOLIO MANAGEMENT CUSTOMIZED FOR THE ASSOCIATION OF SOUTHEAST ASIAN NATIONS (ASEAN) MEMBER COUNTRIES TABLE OF CONTENTS page 1. Preface…………………………………………………………………. 4 2. Mission Report of Mr. Lee Yuke Chin, Regional Consultant………… 5 3. Overview of ASEAN Companies interviewed in the Study……...…… 22 4. ASEAN COUNTRIES 4. 1. Brunei Darussalam Part I: Listing of Manuals, Guidelines and Directories in the Area of Intellectual Property (IP) Portfolio Management………………………. 39 Part II: Success Stories…………………………………………………. 53 4. 2. Cambodia Part I: Listing of Manuals, Guidelines and Directories in the Area of Intellectual Property (IP) Portfolio Management………………………. 66 Part II: Success Stories…………………………………………………. 85 4. 3. Indonesia Part I: Listing of Manuals, Guidelines and Directories in the Area of Intellectual Property (IP) Portfolio Management………………………. 96 Part II: Success Stories…………………………………………………. 113 4. 4. Lao PDR Part I: Listing of Manuals, Guidelines and Directories in the Area of Intellectual Property (IP) Portfolio Management………………………. 127 Part II: Success Stories…………………………………………………. 144 4. 5. Malaysia Part I: Listing of Manuals, Guidelines and Directories in the Area of Intellectual Property (IP) Portfolio Management………………………. 156 Part II: Success Stories…………………………………………………. 191 4. 6. Myanmar Part I: Listing of Manuals, Guidelines and Directories in the Area of Intellectual Property (IP) Portfolio Management………………………. 213 Part II: Success Stories…………………………………………………. 232 4. 7. Philippines Part I: Listing of Manuals, Guidelines and Directories in the Area of Intellectual Property (IP) Portfolio Management………………………. 248 Part II: Success Stories…………………………………………………. 267 4. 8. Singapore Part I: Listing of Manuals, Guidelines and Directories in the Area of Intellectual Property (IP) Portfolio Management………………………. -

Piatkus Non-Fiction Backlist Translation Rights
PIATKUS NON-FICTION BACKLIST TRANSLATION RIGHTS Contents: Non-fiction p.2 Mind, Body & Spirit p.11 Health p.30 Patrick Holford p.42 Self-help/Popular Psychology p.54 Sex p.76 Memoir p.78 Humour p.87 Business p.89 ANDY HINE Rights Director (for Brazil, Germany, Italy, Poland, Scandinavia, Latin America) [email protected] KATE HIBBERT Rights Director (for the USA, Spain, Portugal, Far East and the Netherlands) [email protected] HELENA DOREE Senior Rights Manager (for France, Turkey, Arab States, Israel, Greece, Bulgaria, Czech Republic, Slovak Republic, Hungary, Romania, Russia, Serbia, Macedonia and the Baltic States) [email protected] JONATHAN HAINES Rights Assistant [email protected] Carmelite House 50 Victoria Embankment London EC4Y 0DZ Tel: +44 (0) 20 3122 6209 1 NON-FICTION CONNED by James Morton A racy, highly entertaining history of cons and conmen. To the many people who've been the subject of a con, this book will be of personal interest: even if you haven't, there's still a fascination in how it has happened to other. The great, the god and the bad, from Oscar Wilde to Al Capone, have fallen victim to the wiles of the trickster. In Capone's case, he purchased a machine from 'Count' Victor Lustig, guaranteed to produce dollar bills. Other great cons described in this alarming yet funny book are: Royal Cons, Psychic Swindlers, Fairground Cons, Sexual Swindles, and Gambling Swindles. James Morton’s previous books include the bestselling GANGLAND and EAST END GANGLAND. THE BEASTLY BATTLES OF OLD ENGLAND by Nigel Cawthorne Throughout history the English have been a warlike lot. -

Artículo (376.0Kb)
Páez, Daniela La conformación de un campo editorial global : el nuevo escenario para la circulación de las ideas y su impacto en el mercado local Esta obra está bajo una Licencia Creative Commons Argentina. Atribución - No Comercial - Sin Obra Derivada 2.5 https://creativecommons.org/licenses/by-nc-nd/2.5/ar/ Documento descargado de RIDAA-UNQ Repositorio Institucional Digital de Acceso Abierto de la Universidad Nacional de Quilmes de la Universidad Nacional de Quilmes Cita recomendada: Páez, D. (2017) La conformación de un campo editorial global: el nuevo escenario para la circulación de las ideas y su impacto en el mercado argentino. Divulgatio. Perfiles académicos de posgrado, 2(4), 104-119. Disponible en RIDAA-UNQ Repositorio Institucional Digital de Acceso Abierto de la Universidad Nacional de Quilmes http://ridaa.unq.edu.ar/handle/20.500.11807/2768 Puede encontrar éste y otros documentos en: https://ridaa.unq.edu.ar Divulgatio. Perfiles académicos de posgrado, Vol. 2, Número 4, 2017, 104-119. La conformación de un campo editorial global: el nuevo escenario para la circulación de las ideas y su impacto en el mercado argentino The conformation of a global publishing field: the new scenario for the circulation of ideas and its impact in the Argentinian market ARTÍCULO Daniela Páez Universidad Nacional de Quilmes, Argentina. Contacto: [email protected] Recibido: septiembre de 2017 Aceptado: octubre de 2017 Resumen El presente artículo se enfoca en analizar las condiciones de circulación de libros e ideas del campo editorial global, un espacio que está integrado por múltiples actores con desiguales capacidades de acción e influencia en el sistema, que comenzó a consolidarse a partir de la década de 1980. -

Eg Phd, Mphil, Dclinpsychol
This thesis has been submitted in fulfilment of the requirements for a postgraduate degree (e.g. PhD, MPhil, DClinPsychol) at the University of Edinburgh. Please note the following terms and conditions of use: This work is protected by copyright and other intellectual property rights, which are retained by the thesis author, unless otherwise stated. A copy can be downloaded for personal non-commercial research or study, without prior permission or charge. This thesis cannot be reproduced or quoted extensively from without first obtaining permission in writing from the author. The content must not be changed in any way or sold commercially in any format or medium without the formal permission of the author. When referring to this work, full bibliographic details including the author, title, awarding institution and date of the thesis must be given. TEST FOR ECHO: COMPETITION LAW AND THE MUSIC INDUSTRIES FROM A BUSINESS MODEL PERSPECTIVE Evgenia Kanellopoulou Thesis submitted for the degree of Doctor of Philosophy University of Edinburgh, School of Law Academic year 2016/2017 DECLARATION I declare that this thesis was composed by myself and that the work contained herein is my own except where explicitly stated otherwise in the text. This thesis contains parts of work submitted to the University of Glasgow for the award of the LLM in International Commercial Law (academic year 2010/2011). Signed 1 Table of Contents DECLARATION .............................................................................................................. -

A SONY PICTURES CLASSICS RELEASE Www
A SONY PICTURES CLASSICS RELEASE www.itmightgetloudmovie.com Running time: 97 minutes *Official Selection: 2008 Toronto International Film Festival *Official Selection: 2009 Sundance Film Festival Publicity Distributor PMK/HBH Sony Pictures Classics Allen Eichhorn Carmelo Pirrone 622 Third Avenue Lindsay Macik 8th Floor 550 Madison Ave New York, NY 10017 New York, NY 10022 212-373-6115 Tel: 212-833-8833 [email protected] Short Synopsis Rarely can a film penetrate the glamorous surface of rock legends. It Might Get Loud tells the personal stories, in their own words, of three generations of electric guitar virtuosos – The Edge (U2), Jimmy Page (Led Zeppelin), and Jack White (The White Stripes). It reveals how each developed his unique sound and style of playing favorite instruments, guitars both found and invented. Concentrating on the artist’s musical rebellion, traveling with him to influential locations, provoking rare discussion as to how and why he writes and plays, this film lets you witness intimate moments and hear new music from each artist. The movie revolves around a day when Jimmy Page, Jack White, and The Edge first met and sat down together to share their stories, teach and play. Long Synopsis Who hasn't wanted to be a rock star, join a band or play electric guitar? Music resonates, moves and inspires us. Strummed through the fingers of The Edge, Jimmy Page and Jack White, somehow it does more. Such is the premise of It Might Get Loud, a new documentary conceived by producer Thomas Tull. It Might Get Loud isn't like any other rock'n roll documentary. -

Lessons from the Sony CD DRM Episode
Lessons from the Sony CD DRM Episode J. Alex Halderman and Edward W. Felten Center for Information Technology Policy Department of Computer Science Princeton University Abstract system called XCP that had been installed when he in- In the fall of 2005, problems discovered in two Sony- serted a Sony-BMG music CD into his computer’s CD BMG compact disc copy protection systems, XCP and drive. MediaMax, triggered a public uproar that ultimately led News of Russinovich’s discovery circulated rapidly on to class-action litigation and the recall of millions of the Internet, and further revelations soon followed, from discs. We present an in-depth analysis of these technolo- us,1 from Russinovich, and from others. It was discov- gies, including their design, implementation, and deploy- ered that the XCP rootkit makes users’ systems more ment. The systems are surprisingly complex and suffer vulnerable to attacks, that both CD DRM schemes install from a diverse array of flaws that weaken their content risky software components without obtaining informed protection and expose users to serious security and pri- consent from users, that both systems covertly transmit vacy risks. Their complexity, and their failure, makes usage information back to the vendor or the music label, them an interesting case study of digital rights manage- and that none of the protected discs include tools for unin- ment that carries valuable lessons for content companies, stalling the software. (For these reasons, both XCP and DRM vendors, policymakers, end users, and the security MediaMax seem to meet the consensus definition of spy- community. ware.) These and other findings outraged many users. -

Copy Protection
Content Protection / DRM Content Protection / Digital Rights Management Douglas Dixon November 2006 Manifest Technology® LLC www.manifest-tech.com 11/2006 Copyright 2005-2006 Douglas Dixon, All Rights Reserved – www.manifest-tech.com Page 1 Content Protection / DRM Content Goes Digital Analog -> Digital for Content Owners • Digital Threat – No impediment to casual copying – Perfect digital copies – Instant copies – Worldwide distribution over Internet – And now High-Def content … • Digital Promise – Can protect – Encrypt content – Associate rights – Control usage 11/2006 Copyright 2005-2006 Douglas Dixon, All Rights Reserved – www.manifest-tech.com Page 2 1 Content Protection / DRM Conflict: Open vs. Controlled Managed Content • Avoid Morality: Applications & Technology – How DRM is impacting consumer use of media – Awareness, Implications • Consumers: “Bits want to be free” – Enjoy purchased content: Any time, anywhere, anyhow – Fair Use: Academic, educational, personal • Content owners: “Protect artist copyrights” – RIAA / MPAA : Rampant piracy (physical and electronic) – BSA: Software piracy, shareware – Inhibit indiscriminate casual copying: “Speed bump” • “Copy protection” -> “Content management” (DRM) 11/2006 Copyright 2005-2006 Douglas Dixon, All Rights Reserved – www.manifest-tech.com Page 3 Content Protection / DRM Content Protection / DRM How DRM is being applied • Consumer Scenarios: Impact of DRM – Music CD Playback on PC – Archive Digital Music – Play and Record DVDs – Record and Edit Personal Content • Industry Model: Content -

Digital Rights Management
Journal of Intellectual Property Rights Vol 9, July 2004, pp 313-331 Digital Rights Management: An Integrated Secure Digital Content Distribution Technology P Ghatak, R C Tripathi, A K Chakravarti Department of Information Technology, Electronics Niketan, 6, CGO Complex, New Delhi-110 003 Received 5 December 2003 The ability to distribute copyrighted works in digital form through high capacity prere- corded disks (CD ROMs, DVDs etc.) and Internet-enabled transmissions have brought new challenges to the protections of such content from unauthorized copying and use. Technological advancements in this regard are reviewed. Despite the ease with which digital content owners can now transfer data, images, music, video and multimedia documents across the Internet, cur- rent technology does not let them protect their rights to the works, which has resulted into wide- spread music and video piracy. In fact, although the Internet permits widespread dissemination of digital content, the easy-to-copy nature of digital data limits content owners’ willingness to distribute their documents electronically. Digital Rights Management (DRM) technology is a key enabler for the distribution of digital content. DRM refers to protecting ownership/copyright of electronic content by restricting the extent of usage an authorized recipient is allowed in re- gard to that content. DRM technology has historically been viewed as the methodology for the protection of digital media copyrights. But DRM technology products can be leveraged to ad- dress much larger issues, including the control of rights and usage permissions of content and digital information. DRM presents the opportunity to package, price, distribute and sell content in many new ways that have never been possible before.