DRM — “Digital Rights” Or “Digital Restrictions” Management?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tuesday 13 November 2007
Tuesday 13 November 2007 RE: Response to the proposed BSkyB digital terrestrial television services consultation I wish to start by personally thanking you for allowing me to respond to the plans that British Sky Broadcastings plans to launch their Picnic platform on Digital Terrestrial Television, including the launch of the following services: z Sky Sports One; z A children's channel/Sky Movies SD One; z A factual channel/Sky News/Sky One; z Sky News (if BSkyB is given permission to launch a fourth service on DTT using MPEG-4 encoding); z Broadband up to 16Mbps and a telephony service. I wish to begin by giving an idea of my thoughts on the proposal by BSkyB before I answer the questions in the consultation document. Introduction 1. Regarding the use of by BSkyB and NDS Group, the VideoGuard conditional access technology for its pay television services. According to the press release that was released by BSkyB on the 8th of February 2007,1 the service will use a highly secure conditional access system similar to the one BSkyB uses for its digital satellite services, Sky Digital and FreesatFromSky. I also understand that Sky has also stated that viewers will require a new set-top-box to access the new service. In the past, since the launch of the Sky satellite television service in February 1989 via the Astra satellite, BSkyB have always used NDS Group technology to encrypt and protect their own branded services, with both the VideoCrypt and VideoGuard conditional access systems for their Sky analogue and digital satellite services respectively. -

Information Disclosure Mechanism for Technological Protection Measures in China
Journal of Intellectual Property Rights Vol 17, November 2012, pp 532-538 Information Disclosure Mechanism for Technological Protection Measures in China Lili Zhao† Center for China Information Security Law, Xi’an Jiao tong University, Shaanxi Xi’an, P R China 710 049 Received 12 February 2012, revised 21 May 2012 With increasing cases of digital works being copied and pirated, technological protection measures have been greatly favoured by copyright owners for protecting the intellectual property in their digital works, while ensuring that these works can be used and disseminated. However, when any copyright owner or supplier fails to disclose the information of technological protection measures appropriately or effectively, damages such as privacy violations, security breaches and unfair competition may be caused to the public. Therefore, it is necessary to establish an information disclosure mechanism for technological protection measures, make the labeling obligation with regard to technological protection measures by copyright owners apparent and warning to security risks obligatory by legislation; effectively guarding against information security threats from the technological protection measures. Keywords: Technological protection measures, TPM, information disclosure, label and warning The advance of digital technologies make many information security, it is necessary to integrate such acts things become possible, including the copy and in a standardized, normalized and legal manner. dissemination of commercially valuable digital works Therefore, to further prevent copyright owners from through global digital network. Particularly, among using insecure or untested software, protect information the copyright owners of entertainment industry, security and prohibit the abuse of TPMs; disclosure technological protection measures (TPMs) have been obligations should be established for the right holders of regarded as a necessary creation to help digital works TPMs in the form of legislation. -

Study on the Use of Conditional Access Systems for Reasons Other Than The
Study on the use of conditional access systems for reasons other than the protection of remuneration, to examine the legal and the economic implications within the Internal Market and the need of introducing specific legal protection Report presented to the European Commission by N. Helberger N. A. N. M. van Eijk P. B. Hugenholtz Institute for Information Law (IViR) University of Amsterdam Preface The study, commissioned by the Directorate-General for Internal Market and Financial Services (DG XV) of the Commission of the European Community, offers an analysis of the use of conditional access systems for other reasons than the protection of remuneration interests. The report also examines the need to provide for additional legal protection by means of a Community initiative, such as a possible extension of the Conditional Access Directive. The report will give a legal and economic analysis of the most important non- remuneration reasons to use conditional access (CA), examine whether services based on conditional access for these reasons are endangered by piracy activities, to what extent existing legislation in the Member States provides for sufficient protection, and what the possible impact of the use of conditional access is on the Internal Market. Furthermore, the study analysis the specific legislation outside the European Union, notably in Australia, Canada, Japan and the US, as well as the relevant international rules at the level of the EC, WIPO and the Council of Europe. This study was written by Natali Helberger and Dr Nico A. N. M. van Eijk at the Institute for Information Law (IViR), University of Amsterdam under the supervision of Professor P. -

Nokia Nseries | Tech Specs
Nokia Nseries | Tech Specs Nokia N91 Print Technical Specifications Operating frequency ● EGSM/GPRS 900/1800/1900MHz + WCDMA, EDGE ● Data transfer: WCDMA up to speed 384 kbps, EGPRS/GPRS (class B/multislot 10) up to 236.8 kbps ● Note: Actual achieved speeds may vary depending on network support Return to top Dimensions ● Weight: 164 g ● Length: 113.1 mm ● Width (max): 55.2 mm ● Thickness (max): 22 mm Return to top Display and User Interface ● Color display (176 x 208, 262k color) ● S60 software on Symbian OS ● Automatic brightness control for display and keypad ● Music keys: Play/Pause, Forward, Back, Stop. Switch easily between music player and last used application with dedicated key. ● Keys: Two configurable soft keys, Send & End, 5-way configurable navigation key, keys for S60 (Menu, Edit, Clear), ITU-T (number/text) keypad, Volume (up & down), Power, Device lock switch http://www.nseries.com/nseries/v2/media/product/tech_specs/en-GB/tech_specs_n91_en_GB.html?lang=en&country=GB (1 of 6)3/2/2006 12:50:40 μμ Nokia Nseries | Tech Specs Return to top Audio formats (decoding) ● MP3, AAC, AAC+, eAAC+, Real, WAV, WMA, M4A, AMR-WB, True Tones, AMR-NB Return to top Music Player ● Intelligently designed music player • optimized for music listening ● Dedicated playback keys and volume control ● Enhanced on the go playlist management • edit playlists, add new music ● Get meta data ● Enhanced music features: mixer, 5-band equalizer, loudness, music DRC (Dynamic Range Compression) ● See what is playing when in the Nokia N91 is in the idle state ● Answer calls while listening to music and music pauses and then resumes again when the call is ended ● Smart integration with music services (easy access to music shop) ● Music user profile or sim-less operation allows for uninterrupted listening ● Synch with PC ● Download new music over the air to your Nokia N91 Return to top Visual Radio ● Flick on Visual Radio mode. -
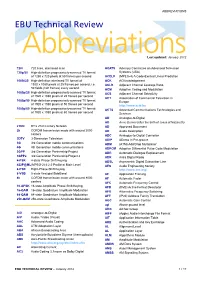
ABBREVIATIONS EBU Technical Review
ABBREVIATIONS EBU Technical Review AbbreviationsLast updated: January 2012 720i 720 lines, interlaced scan ACATS Advisory Committee on Advanced Television 720p/50 High-definition progressively-scanned TV format Systems (USA) of 1280 x 720 pixels at 50 frames per second ACELP (MPEG-4) A Code-Excited Linear Prediction 1080i/25 High-definition interlaced TV format of ACK ACKnowledgement 1920 x 1080 pixels at 25 frames per second, i.e. ACLR Adjacent Channel Leakage Ratio 50 fields (half frames) every second ACM Adaptive Coding and Modulation 1080p/25 High-definition progressively-scanned TV format ACS Adjacent Channel Selectivity of 1920 x 1080 pixels at 25 frames per second ACT Association of Commercial Television in 1080p/50 High-definition progressively-scanned TV format Europe of 1920 x 1080 pixels at 50 frames per second http://www.acte.be 1080p/60 High-definition progressively-scanned TV format ACTS Advanced Communications Technologies and of 1920 x 1080 pixels at 60 frames per second Services AD Analogue-to-Digital AD Anno Domini (after the birth of Jesus of Nazareth) 21CN BT’s 21st Century Network AD Approved Document 2k COFDM transmission mode with around 2000 AD Audio Description carriers ADC Analogue-to-Digital Converter 3DTV 3-Dimension Television ADIP ADress In Pre-groove 3G 3rd Generation mobile communications ADM (ATM) Add/Drop Multiplexer 4G 4th Generation mobile communications ADPCM Adaptive Differential Pulse Code Modulation 3GPP 3rd Generation Partnership Project ADR Automatic Dialogue Replacement 3GPP2 3rd Generation Partnership -

Table of Contents
Journal of Mobile, Embedded and Distributed Systems, vol. I, no. 1, 2009 ISSN 2067 – 4074 Survey of Mobile Digital Rights Management Platforms Cristian TOMA, Catalin BOJA Faculty of Cybernetics, Statistics and Economic Informatics Department of IT&C Technologies Academy of Economic Studies Bucharest, Romania [email protected], [email protected] Abstract: Based on the development of new communication and data transfer technologies, the mobile solutions for the e-activities have been able to provide new ways to provide multimedia content. This environment describes methods and tools available here, which will bring information, speed and efficiency to any stage and component of the mobile business process. The paper takes into discussion the Digital Rights Management technology in mobile world. The paper presents the main aspects regarding the business and technological models used in mobile digital rights management technology. Key-Words: M-applications, digital rights management, mobile DRM models. 1. Mobile Projects Taking into consideration the advantages that the communication technologies bring into the mobile business process, the subscribers will have more information at their disposal. This will conduct to a reliable and secure communication, better results and in the end to high quality output. Despite the necessary high costs required to implement and to maintain a communication system at this level, in the end, the benefits and the lower levels of costs penalties due to a non efficient information and data transfer will highlight the importance of this resource. For instance, file sharing and file control software systems allow a much better data maintenance and permanent access to information than the printed or paper format. -

Intellectual Property Part 2 Pornography
Intellectual Property Part 2 Pornography By Jeremy Parmenter What is pornography Pornography is the explicit portrayal of sexual subject matter Can be found as books, magazines, videos The web has images, tube sites, and pay sites scattered with porn Statistics 12% of total websites are pornography websites 25% of total daily search engine requests are pornographic requests 42.7% of internet users who view pornography 34% internet users receive unwanted exposure to sexual material $4.9 billion in internet pornography sales 11 years old is the average age of first internet exposure to pornography Innovations ● Richard Gordon created an e-commerce start up in mid- 90s that was used on many sites, most notably selling Pamela Anderson/Tommey Lee sex tape ● Danni Ashe founded Danni's Hard Drive with one of the first streaming video without requiring a plug-in ● Adult content sites were one of the first to use traffic optimization by linking to similar sites ● Live chat during the early days of the web ● Pornographic companies were known to give away broadband devices to promote faster connections Negative Impacts ● Between 2001-2002 adult-oriented spam rose 450% ● Malware such as Trojans and video codecs occur most often on porn sites ● Domain hijacking, using fake documents and information to steal a site ● Pop-ups preventing users from leaving the site or infecting their computer ● Browser hijacking adware or spyware manipulating the browser to change home page or search engine to a bogus site, including pay-per-click adult site ● Accessibility -

DRM Specification Approved Version 2.1 – 06 Nov 2008
DRM Specification Approved Version 2.1 – 06 Nov 2008 Open Mobile Alliance OMA-TS-DRM-DRM-V2_1-20081106-A 2008 Open Mobile Alliance Ltd. All Rights Reserved. Used with the permission of the Open Mobile Alliance Ltd. under the terms as stated in this document. [OMA-Template-DRM-20080101-I] OMA-TS-DRM-DRM-V2_1-20081106-A Page 2 (214) Use of this document is subject to all of the terms and conditions of the Use Agreement located at http://www.openmobilealliance.org/UseAgreement.html. Unless this document is clearly designated as an approved specification, this document is a work in process, is not an approved Open Mobile Alliance™ specification, and is subject to revision or removal without notice. You may use this document or any part of the document for internal or educational purposes only, provided you do not modify, edit or take out of context the information in this document in any manner. Information contained in this document may be used, at your sole risk, for any purposes. You may not use this document in any other manner without the prior written permission of the Open Mobile Alliance. The Open Mobile Alliance authorizes you to copy this document, provided that you retain all copyright and other proprietary notices contained in the original materials on any copies of the materials and that you comply strictly with these terms. This copyright permission does not constitute an endorsement of the products or services. The Open Mobile Alliance assumes no responsibility for errors or omissions in this document. Each Open Mobile Alliance member has agreed to use reasonable endeavors to inform the Open Mobile Alliance in a timely manner of Essential IPR as it becomes aware that the Essential IPR is related to the prepared or published specification. -

Open Ongtang-Phd-Dissertation.Pdf
The Pennsylvania State University The Graduate School SECURING MOBILE PHONES IN THE EVOLVING MOBILE ECOSYSTEM A Dissertation in Computer Science and Engineering by Machigar Ongtang © 2010 Machigar Ongtang Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy August 2010 The dissertation of Machigar Ongtang was reviewed and approved∗ by the following: Patrick D. McDaniel Associate Professor of Computer Science and Engineering Dissertation Advisor, Chair of Committee Thomas F. La Porta Distinguished Professor of Computer Science and Engineering Trent Jaeger Associate Professor of Computer Science and Engineering Ling Rothrock Associate Professor of Industrial and Manufacturing Engineering Raj Acharya Professor of Computer Science and Engineering Department Head ∗Signatures are on file in the Graduate School. Abstract The revolution of mobile phone industry has been altering our life and business practices over the past few decades. Driven by user demands and technological advancement, we now experience rich mobile phone applications and sophisticated cellular services ranging from mobile payment, stock trading, to social networking, vehicle tracking to in-car control. As more players joining the community, this mobile phone environment has transformed into a complex network of interacting companies, known as mobile ecosystem. Unfortunately, this opening and converging mobile ecosystem has brought in more opportunities for more attacks on mobile phones, a key element of the system. This dissertation aims to achieve mobile phone security. We reveal two main chal- lenges that we need to overcome, namely developing a clear definition of secure phones, and building security infrastructure that imposes such definition on the phones. We also identify three key elements that contribute to the fidelity of mobile phones, namely, mobile phone platforms, mobile phone applications, and mobile content. -

Nokia N91: Smartphone That Features 4 Gb Hard Drive 28 April 2005
Nokia N91: Smartphone that features 4 Gb hard drive 28 April 2005 Nokia Nseries range, bringing you the latest multimedia technologies and smartphone functionalities. "The Nokia N91 delivers both a fantastic music experience and cutting-edge phone features," said Jonas Geust, Vice President, Music at Nokia. "What sets the Nokia N91 apart is the fact that it is always connected - you can download new music while on the move, add it to your favorite playlist and then share your playlist with friends. It's truly the world's best mobile connected jukebox." The Nokia N91 serves up to 12.5 hours of great sound via the included stereo headset with remote control. Enjoying your music collection has never been easier, as the Nokia N91 supports a wide range of digital music formats including MP3, M4A, AAC and WMA. Nokia N91 is compatible with a number of accessories from industry leading brands Bose, Harman Kardon, JBL, and Sennheiser. In addition to using their favorite audio accessories with the Nokia N91 through its standard 3.5mm jack, Nokia introduced the Nokia N91 mobile phone that consumers can maximize their audio experience by has room for up to 3,000 of your favorite stereo choosing products from a line-up of Nokia tested tracks on the integrated 4 Gb hard disk. It's a and recommended audio accessories. premium music device in an ultra-portable package that snaps 2 megapixel photos and has Packed with multiple connectivity options, such as smartphone features. Your smartphone already WCDMA, WLAN and Bluetooth wireless goes everywhere you do and now your music will, technology, the Nokia N91 makes it easy for you to too. -

Testvinnaren Nokia N91 Nu I Butik - Telefonen För En Total Mobil Musikupplevelse
PRESSMEDDELANDE 1 (2) 3 maj, 2006 Testvinnaren Nokia N91 nu i butik - Telefonen för en total mobil musikupplevelse För dig som är musikälskare finns nu N91 till försäljning - en riktig mobil jukebox med plats för upp till 3 000 låtar och smartphone funktioner i ett bärbart format. N91 klassas som Sveriges bästa musiktelefon av magasinet Mobil efter ett omfattande test av alla musikmobiler på marknaden. Nokia N91 är optimerad för musik. Användare kan spara upp till 3 000 låtar på den interna hårddisken (4 GB) vilket gör terminalen till en riktig mobil jukebox. Att överföra musik från en kompatibel PC är enkelt och Nokia N91 stödjer dessutom standarden för hörlurar (3,5 mm) vilket innebär att användare kan använda sina vanliga hörlurar. Nokia N91 har en yta av rostfritt stål med ett antal dedikerade knappar för musik, och är del av nya Nokia Nseries som erbjuder det senaste inom mobil multimedia och smartphones. Testvinnare bland musikmobiler i tidningen Mobil Tidningen Mobil lät i aprilnumret genomföra ett omfattande test av åtta aktuella musikmobiler där Nokia N91 utsågs till marknadens vinnare. Enligt tidningen är det främst kombinationen 3G- och musikmobil som gör Nokia N91 till en vinnare. Två Nokia-telefoner, Nokia N91 och Nokia 3250, är med i testet som totalt omfattar åtta mobiltelefoner. Gemensamt för alla mobiltelefoner i testet är att de är musikmobiler som på allvar utmanar den vanliga mp3-spelaren. Av testets totalt sju kategorier utses 3G- musikmobilen Nokia N91 som vinnare i sex av dem. Minnesstorleken är viktig för många när det kommer till val av musikspelare. Med störst minne, 4 GB och plats för upp till 3 000 låtar, är Nokia N91 bättre än konkurrenterna och vinner kategorierna Minne och Filformat. -

Pointsec Mobile Symbian OS (S60) 3.3.1 Revision and Device Tracking
Pointsec Mobile Symbian OS (S60) 3.3.1 Revision and Device Tracking Revised: October 2, 2008 This Revision and Device Tracking document contains information on changes and corrections implemented in previous versions of Pointsec Mobile Symbian OS (S60). It also contains information on devices supported in different releases Note - There may be an updated version of this document and of the other documents you received with your copy of Pointsec Mobile Symbian OS (S60). You can access the latest version at: http://www.checkpoint.com/support/ In This Document Introduction page 2 Product Version Tracking page 2 Version 3.3.0 page 2 Version 3.2.1 page 5 Version 3.2.1 page 5 Version 3.1.4 page 7 Version 3.1.3 page 8 Version 3.1.2 (Limited Release) page 9 Version 3.1.1 page 11 Version 3.1.0 page 12 Version 3.0.1 page 13 Version 3.0.0 page 14 Device Tracking page 15 Documentation Feedback page 15 Copyright © 2008 Pointsec Mobile Technologies AB, a Check Point Software Technologies company. All rights reserved 1 Introduction Introduction This document contains information on previous releases of Pointsec Mobile Symbian OS (S60) in the 3.X series. The information included here is based on the Release Notes for each release. For information on releases in the 2.X series, please see the documentation accompanying that product. As you read this document, please note the following: • The first Pointsec for Symbian OS (S60 3rd Ed.) version recorded in this document is 3.0, because this is the version in which the Symbian OS platform changed from S80 to S60.