Table of Contents
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

DRM Specification Approved Version 2.1 – 06 Nov 2008
DRM Specification Approved Version 2.1 – 06 Nov 2008 Open Mobile Alliance OMA-TS-DRM-DRM-V2_1-20081106-A 2008 Open Mobile Alliance Ltd. All Rights Reserved. Used with the permission of the Open Mobile Alliance Ltd. under the terms as stated in this document. [OMA-Template-DRM-20080101-I] OMA-TS-DRM-DRM-V2_1-20081106-A Page 2 (214) Use of this document is subject to all of the terms and conditions of the Use Agreement located at http://www.openmobilealliance.org/UseAgreement.html. Unless this document is clearly designated as an approved specification, this document is a work in process, is not an approved Open Mobile Alliance™ specification, and is subject to revision or removal without notice. You may use this document or any part of the document for internal or educational purposes only, provided you do not modify, edit or take out of context the information in this document in any manner. Information contained in this document may be used, at your sole risk, for any purposes. You may not use this document in any other manner without the prior written permission of the Open Mobile Alliance. The Open Mobile Alliance authorizes you to copy this document, provided that you retain all copyright and other proprietary notices contained in the original materials on any copies of the materials and that you comply strictly with these terms. This copyright permission does not constitute an endorsement of the products or services. The Open Mobile Alliance assumes no responsibility for errors or omissions in this document. Each Open Mobile Alliance member has agreed to use reasonable endeavors to inform the Open Mobile Alliance in a timely manner of Essential IPR as it becomes aware that the Essential IPR is related to the prepared or published specification. -

Open Ongtang-Phd-Dissertation.Pdf
The Pennsylvania State University The Graduate School SECURING MOBILE PHONES IN THE EVOLVING MOBILE ECOSYSTEM A Dissertation in Computer Science and Engineering by Machigar Ongtang © 2010 Machigar Ongtang Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy August 2010 The dissertation of Machigar Ongtang was reviewed and approved∗ by the following: Patrick D. McDaniel Associate Professor of Computer Science and Engineering Dissertation Advisor, Chair of Committee Thomas F. La Porta Distinguished Professor of Computer Science and Engineering Trent Jaeger Associate Professor of Computer Science and Engineering Ling Rothrock Associate Professor of Industrial and Manufacturing Engineering Raj Acharya Professor of Computer Science and Engineering Department Head ∗Signatures are on file in the Graduate School. Abstract The revolution of mobile phone industry has been altering our life and business practices over the past few decades. Driven by user demands and technological advancement, we now experience rich mobile phone applications and sophisticated cellular services ranging from mobile payment, stock trading, to social networking, vehicle tracking to in-car control. As more players joining the community, this mobile phone environment has transformed into a complex network of interacting companies, known as mobile ecosystem. Unfortunately, this opening and converging mobile ecosystem has brought in more opportunities for more attacks on mobile phones, a key element of the system. This dissertation aims to achieve mobile phone security. We reveal two main chal- lenges that we need to overcome, namely developing a clear definition of secure phones, and building security infrastructure that imposes such definition on the phones. We also identify three key elements that contribute to the fidelity of mobile phones, namely, mobile phone platforms, mobile phone applications, and mobile content. -

Symbian Phone Security
Symbian phone Security Job de Haas ITSX Symbian phone Job de Haas BlackHat Security ITSX BV Amsterdam 2005 Overview • Symbian OS. • Security Risks and Features. • Taking it apart. • Conclusions. Symbian phone Job de Haas BlackHat Security ITSX BV Amsterdam 2005 Symbian History • Psion owner of EPOC OS, originally from 1989, released EPOC32 in 1996 • EPOC32 was designed with OO in C++ • 1998: Symbian Ltd. formed by Ericsson, Nokia, Motorola and Psion. • EPOC renamed to Symbian OS • Currently ~30 phones with Symbian and 15 licensees. Symbian phone Job de Haas BlackHat Security ITSX BV Amsterdam 2005 Symbian Organization • Symbian licenses the main OS • Two GUI’s on top of Symbian: – Series 60, led by Nokia – UIQ, subsidiary of Symbian • Ownership: – Nokia 47.5% Panasonic 10.5% – Ericsson 15.6% Siemens 8.4% – SonyEricsson 13.1% Samsung 4.5% Symbian phone Job de Haas BlackHat Security ITSX BV Amsterdam 2005 Symbian Versions • EPOC32 • EPOC R5 • Symbian v6.0 • Symbian v7.0 • Symbian v8.0 • Symbian v9.0 announced for Q3 ‘05 Symbian phone Job de Haas BlackHat Security ITSX BV Amsterdam 2005 Series60 versions • 1st edition • 2nd edition • 3rd edition, announced feb. 2005 Symbian phone Job de Haas BlackHat Security ITSX BV Amsterdam 2005 UIQ versions • UIQ 1.0 • UIQ 2.1 • UIQ 3.0 released feb 2005 Symbian phone Job de Haas BlackHat Security ITSX BV Amsterdam 2005 Symbian OS Symbian phone Job de Haas BlackHat Security ITSX BV Amsterdam 2005 Symbian OS • Multitasking, preemptive kernel. • MMU protection of kernel and process spaces. • Strong Client – Server architecture • Plug-in patterns • Filesystem in ROM, Flash, RAM and on SD-card Symbian phone Job de Haas BlackHat Security ITSX BV Amsterdam 2005 Symbian development • Symbian v6 and v7 are compiled with a modified GCC. -
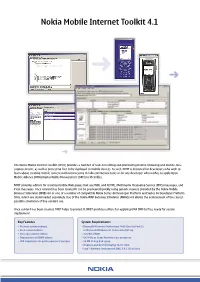
Nokia Mobile Internet Toolkit 4.1
Nokia Mobile Internet Toolkit 4.1 The Nokia Mobile Internet Toolkit (NMIT) provides a number of tools for editing and previewing mobile-browsing and mobile-mes- saging content, as well as protecting fi les to be deployed to mobile devices. As such, NMIT is designed for developers who wish to learn about creating mobile content without investing in fully commercial tools or for any developer who wishes to apply Open Mobile Alliance (OMA) Digital Rights Management (DRM) to their fi les. NMIT provides editors for creating mobile Web pages that use WML and XHTML, Multimedia Messaging Service (MMS) messages, and Push messages. Once content has been created it can be previewed quickly using generic viewers provided by the Nokia Mobile Browser Simulator (NMB) 4.0 or one of a number of compatible Nokia Series 40 Developer Platform and Series 60 Developer Platform SDKs, which are downloaded separately. Use of the Nokia WAP Gateway Simulator (NWGS) 4.0 allows the achievement of the closest possible emulation of live-content use. Once content has been created, NMIT helps to protect it. NMIT provides editors for applying OMA DRM to fi les, ready for secure deployment. Key Features System Requirements • Browser-content editors. • Microsoft Windows Professional 2000 (Service Pack 3) • Push-content editors. or Microsoft Windows XP Professional (SP1a). • Message-content editors. • 256 MB of RAM. • Deployment and DRM editors. • 667-MHz or faster Pentium-class processor. • SDK integration for quick preview of content. • 50 MB of free disk space. • Display capable of displaying 16-bit color. • Java™ Runtime Environment (JRE) 1.4.1_02 or later. -

Internal Use Only
White paper August 2012 Internal use only LT30p T White paper | Xperia™ T Purpose of this document Sony Mobile Communications product White papers are intended to give an overview of a product and provide details in relevant areas of technology. Document history Version August 2012 First released version Version 1 Sony Mobile Developer World For the latest Sony Moible Communications technical documentation and development tools, go to www.sonymobile.com/developer. This document is published by Sony Mobile This White paper is published by: Communications AB, without any warranty*. Improvements and changes to this text Sony Mobile Communications AB, necessitated by typographical errors, SE-221 88 Lund, Sweden inaccuracies of current information or improvements to programs and/or equipment may be made by Sony Mobile Communications www.sonymobile.com AB at any time and without notice. Such changes will, however, be incorporated into new editions © Sony Mobile Communications AB, 2009-2012. of this document. Printed versions are to be regarded as temporary reference copies only. All rights reserved. You are hereby granted a license to download and/or print a copy of this *All implied warranties, including without document. limitation the implied warranties of Any rights not expressly granted herein are merchantability or fitness for a particular reserved. purpose, are excluded. In no event shall Sony Mobile Communications or its licensors be liable for incidental or consequential damages of any First released version (June 2012) nature, including but not limited to lost profits or Publication number: 1252-1327.1 commercial loss, arising out of the use of the information in this document. -

Snap, Show, Share White Paper K300i Preface
February 2005 K300i Snap, show, share White Paper K300i Preface Purpose of this document This White Paper will be published in several revisions as the phone is developed. Therefore, some of the headings and tables below contain limited information. Additional information and facts will be forthcoming in later revisions. The aim of this White Paper is to give the reader an understanding of technology and its main applications, as well as the main functions and features of the phone. Note: This document contains general descriptions for this specific Sony Ericsson mobile phone. People who can benefit from this document include: • Operators • Service providers • Software developers • Support engineers • Application developers More information, useful for product, service and application developers, is published at www.SonyEricsson.com/developer/, which contains up-to-date information about technologies, products and tools. This White Paper is published by: This document is published by Sony Ericsson Mobile Communications AB, without any warranty*. Improvements and changes to this text Sony Ericsson Mobile Communications AB, necessitated by typographical errors, inaccuracies SE-221 88 Lund, Sweden of current information or improvements to programs and/or equipment, may be made by Phone: +46 46 19 40 00 Sony Ericsson Mobile Communications AB at any Fax: +46 46 19 41 00 time and without notice. Such changes will, however, be incorporated into new editions of this www.SonyEricsson.com/ document. Printed versions are to be regarded as temporary reference copies only. © Sony Ericsson Mobile Communications AB, 2005. All rights reserved. You are hereby granted *All implied warranties, including without limitation the implied warranties of merchantability or fitness a license to download and/or print a copy of this for a particular purpose, are excluded. -

W380 April 2008
W380 April 2008 Feel music, see music, hear music White paper W380 Preface Purpose of this document This White paper will be published in several revisions as the phone is developed. Therefore, some of the headings and tables below contain limited information. Additional information and facts will be forthcoming in later revisions. The aim of this White paper is to give the reader an understanding of technology used in the phone and its main applications, as well as the main functions and features of the phone. Note: This document contains general descriptions for this specific Sony Ericsson mobile phone. People who can benefit from this document include: • Operators • Service providers • Software developers • Support engineers • Application developers • Market units and sales people This White paper is published by: This document is published by Sony Ericsson Mobile Communications AB, without any warranty*. Improvements and changes to this text Sony Ericsson Mobile Communications AB, necessitated by typographical errors, inaccuracies SE-221 88 Lund, Sweden of current information or improvements to programs and/or equipment, may be made by Phone: +46 46 19 40 00 Sony Ericsson Mobile Communications AB at any Fax: +46 46 19 41 00 time and without notice. Such changes will, however, be incorporated into new editions of this www.sonyericsson.com/ document. Printed versions are to be regarded as temporary reference copies only. © Sony Ericsson Mobile Communications AB, 2008. All rights reserved. You are hereby granted *All implied warranties, including without limitation the implied warranties of merchantability or fitness a license to download and/or print a copy of this for a particular purpose, are excluded. -

OMA DRM Requirements Candidate Version 2.2 – 29 June 2010
OMA DRM Requirements Candidate Version 2.2 – 29 June 2010 Open Mobile Alliance OMA-RD-DRM-V2_2-20100629-C 2010 Open Mobile Alliance Ltd. All Rights Reserved. Used with the permission of the Open Mobile Alliance Ltd. under the terms as stated in this document. [OMA-Template-Spec-20100101-I] OMA-RD-DRM-V2_2-20100629-C.doc Page 2 (36) Use of this document is subject to all of the terms and conditions of the Use Agreement located at http://www.openmobilealliance.org/UseAgreement.html. Unless this document is clearly designated as an approved specification, this document is a work in process, is not an approved Open Mobile Alliance™ specification, and is subject to revision or removal without notice. You may use this document or any part of the document for internal or educational purposes only, provided you do not modify, edit or take out of context the information in this document in any manner. Information contained in this document may be used, at your sole risk, for any purposes. You may not use this document in any other manner without the prior written permission of the Open Mobile Alliance. The Open Mobile Alliance authorizes you to copy this document, provided that you retain all copyright and other proprietary notices contained in the original materials on any copies of the materials and that you comply strictly with these terms. This copyright permission does not constitute an endorsement of the products or services. The Open Mobile Alliance assumes no responsibility for errors or omissions in this document. Each Open Mobile Alliance member has agreed to use reasonable endeavours to inform the Open Mobile Alliance in a timely manner of Essential IPR as it becomes aware that the Essential IPR is related to the prepared or published specification. -

DRM — “Digital Rights” Or “Digital Restrictions” Management?
DIGITAL RIGHTS MANAGEMENT DRM — “digital rights” or “digital restrictions” management? Richard Leeming Red Bee Media If correctly applied, DRM can be likened to a motorway, providing a seamless high- speed route to content, enabling people to get the content they want, where they want it, quickly and easily. However, if badly applied, heavy handed and overly restrictive, DRM is more like a traffic jam – denying people access to the content they want and crucially denying rights-holders the revenue they want. This article looks at some of the proprietary DRM systems currently available and argues that we need to start thinking hard about when and how we apply DRM to our precious content. In 2006, music lovers worldwide have been celebrating the 250th anniversary of Mozart’s birth. Although he only lived for 35 years, Mozart composed more than 600 pieces of classical music – most of which are still hugely popular today. But it’s perhaps something of a surprise to discover that one of the key moments of Mozart’s early career would today count as piracy and be prevented by digital-rights technology. As a 14-year-old, Mozart travelled to the Vatican and heard Gregorio Allegri’s Miserere. This piece of music had long been closely guarded by the Vatican and it was forbidden to transcribe it: if you did, you would be excommunicated. Whether Mozart knew this is unknown but, having heard it once, he transcribed it from memory and it became published in London, thus breaking the Vatican’s ban. This is perhaps one of the earliest-known examples of content rights management being overturned. -

Attractive Outside. Intelligent Inside White Paper T700 Preface
T700 November 2008 Attractive outside. Intelligent inside White paper T700 Preface Purpose of this document This White paper will be published in several revisions as the phone is developed. Therefore, some of the headings and tables in this document contain limited information. Additional information and facts will be forthcoming in later revisions. The aim of this White paper is to give the reader an understanding of the main functions and features of the phone. People who can benefit from this document include: • Operators • Service providers • Software developers • Support engineers • Application developers This White paper is published by: This document is published by Sony Ericsson Mobile Communications AB or its local affiliated Sony Ericsson Mobile Communications AB, company, without any warranty*. Improvements SE-221 88 Lund, Sweden and changes to this text necessitated by typographical errors, inaccuracies of current information or improvements to programs and/or www.sonyericsson.com/ equipment, may be made by Sony Ericsson Mobile Communications AB at any time and © Sony Ericsson Mobile Communications AB, without notice. Such changes will, however, be 2008. All rights reserved. You are hereby granted incorporated into new editions of this document. Printed versions are to be regarded as temporary a license to download and/or print a copy of this reference copies only. document. Any rights not expressly granted herein are *All implied warranties, including without limitation reserved. the implied warranties of merchantability or fitness for a particular purpose, are excluded. In no event shall Sony Ericsson or its licensors be liable for Second edition (November 2008) incidental or consequential damages of any Publication number: 1214-1270.2 nature, including but not limited to lost profits or commercial loss, arising out of the use of the information in this document. -

Implementing Mobile DRM with MPEG-21 and OMA
Implementing Mobile DRM with MPEG-21 and OMA Silvia Llorente, Jaime Delgado and Xavier Maroñas Departament d’Arquitectura de Computadors, Universitat Politècnica de Catalunya C/ Jordi Girona 1-3, E-08034, Barcelona, Spain Abstract. Digital Rights Management (DRM) is an important issue when try- ing to provide advanced multimedia content distribution services. DRM is mostly thought for personal computers, but now, with the emerging mobile de- vices which include multimedia support and higher bandwidth capabilities, us- ers demand more valuable content for their mobile devices. The most relevant initiatives in the area, MPEG 21 and OMA DRM have been used for imple- menting a DRM system for mobiles. A lot of work has still to be done in this area and what we present here is a combination of techniques coming from MPEG 21 and OMA for providing a more complex system with combined ca- pabilities. 1 Introduction The provision of multimedia content for mobile devices is increasing day by day. This implies that content providers want their contents to be protected in a more com- plex way, too. On the other hand, devices have more resources in terms of screen size, processing capabilities and formats supported and users want to take profit. In this paper we present a way of providing digital rights management (DRM) for mobiles based on two of the most important initiatives in this area: MPEG-21 and OMA. The structure of this paper is as follows. First, we introduce MPEG-21 and OMA, and their most relevant parts for the work presented here. Then, in section 4, we de- scribe the DRM system for mobiles implemented. -

Wireless Application Environment Specification Candidate Version 2.3 – 22 Dec 2004
Wireless Application Environment Specification Candidate Version 2.3 – 22 Dec 2004 Open Mobile Alliance OMA-WAP-TS-WAESpec-V2_3-20050118-C Continues the Technical Activities Originated in the WAP Forum 2005 Open Mobile Alliance Ltd. All Rights Reserved. Used with the permission of the Open Mobile Alliance Ltd. under the terms as stated in this document. [OMA-Template-SpecWAP-20040205] OMA-WAP-TS-WAESpec-V2_3-20050118-C Page 2 (59) Use of this document is subject to all of the terms and conditions of the Use Agreement located at http://www.openmobilealliance.org/UseAgreement.html. Unless this document is clearly designated as an approved specification, this document is a work in process, is not an approved Open Mobile Alliance™ specification, and is subject to revision or removal without notice. You may use this document or any part of the document for internal or educational purposes only, provided you do not modify, edit or take out of context the information in this document in any manner. Information contained in this document may be used, at your sole risk, for any purposes. You may not use this document in any other manner without the prior written permission of the Open Mobile Alliance. The Open Mobile Alliance authorizes you to copy this document, provided that you retain all copyright and other proprietary notices contained in the original materials on any copies of the materials and that you comply strictly with these terms. This copyright permission does not constitute an endorsement of the products or services. The Open Mobile Alliance assumes no responsibility for errors or omissions in this document.