Monday/Tuesday Playoff Schedule
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Polimetriche Per Linea STIBM Area Nord.Xlsx
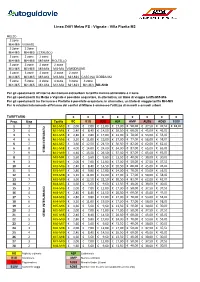
Linea Z401 Melzo FS - Vignate - Villa Fiorita M2 MELZO 2 zone Mi4-Mi5 VIGNATE 2 zone 2 zone Mi4-Mi5 Mi4-Mi5 CERNUSCO 2 zone 2 zone 2 zone Mi4-Mi5 Mi4-Mi5 Mi3-Mi4 PIOLTELLO 3 zone 3 zone 2 zone 2 zone Mi3-Mi5 Mi3-Mi5 Mi3-Mi4 Mi3-Mi4 VIMODRONE 3 zone 3 zone 2 zone 2 zone 2 zone Mi3-Mi5 Mi3-Mi5 Mi3-Mi4 Mi3-Mi4 Mi3-Mi4 CASCINA GOBBA M2 5 zone 5 zone 4 zone 4 zone 3 zone 3 zone Mi1-Mi5 Mi1-Mi5 Mi1-Mi4 Mi1-Mi4 Mi1-Mi3 Mi1-Mi3 MILANO Per gli spostamenti all'interno dei Comuni extraurbani la tariffa minima utilizzabile è 2 zone Per gli spostamenti tra Melzo e Vignate è possibile acquistare, in alternativa, un titolo di viaggio tariffa Mi5-Mi6 Per gli spostamenti tra Cernusco e Pioltello è possibile acquistare, in alternativa, un titolo di viaggio tariffa Mi4-Mi5 Per le relazioni interamente all'interno dei confini di Milano è ammesso l'utilizzo di mensili e annuali urbani TARIFFARIO €€€€€€€€ Prog. Ring Tariffa BO B1G B3G ASP AMP AU26 AO65 B10V 1 3 Mi1-Mi3 € 2,00 € 7,00 € 12,00 € 17,00 € 50,00 € 37,50 € 37,50 € 18,00 2 4 Mi1-Mi4 € 2,40 € 8,40 € 14,50 € 20,50 € 60,00 € 45,00 € 45,00 3 5 Mi1-Mi5 € 2,80 € 9,80 € 17,00 € 24,00 € 70,00 € 53,00 € 53,00 4 6 Mi1-Mi6 € 3,20 € 11,00 € 19,00 € 27,00 € 77,00 € 58,00 € 58,00 5 7 Mi1-Mi7 € 3,60 € 12,50 € 21,50 € 30,50 € 82,00 € 62,00 € 62,00 6 8 Mi1-Mi8 € 4,00 € 14,00 € 24,00 € 34,00 € 87,00 € 65,00 € 65,00 7 9STIBM INTEGRATO Mi1-Mi9€ 4,40 € 15,50 € 26,50 € 37,50 € 87,00 € 65,00 € 65,00 8 2 MI3-MI4 € 1,60 € 5,60 € 9,60 € 13,50 € 40,00 € 30,00 € 30,00 9 3 MI3-MI5 € 2,00 € 7,00 € 12,00 € 17,00 € 50,00 € 37,50 -

SPYCATCHER by PETER WRIGHT with Paul Greengrass WILLIAM
SPYCATCHER by PETER WRIGHT with Paul Greengrass WILLIAM HEINEMANN: AUSTRALIA First published in 1987 by HEINEMANN PUBLISHERS AUSTRALIA (A division of Octopus Publishing Group/Australia Pty Ltd) 85 Abinger Street, Richmond, Victoria, 3121. Copyright (c) 1987 by Peter Wright ISBN 0-85561-166-9 All Rights Reserved. No part of this publication may be reproduced, stored in or introduced into a retrieval system, or transmitted, in any form or by any means (electronic, mechanical, photocopying, recording or otherwise) without the prior written permission of the publisher. TO MY WIFE LOIS Prologue For years I had wondered what the last day would be like. In January 1976 after two decades in the top echelons of the British Security Service, MI5, it was time to rejoin the real world. I emerged for the final time from Euston Road tube station. The winter sun shone brightly as I made my way down Gower Street toward Trafalgar Square. Fifty yards on I turned into the unmarked entrance to an anonymous office block. Tucked between an art college and a hospital stood the unlikely headquarters of British Counterespionage. I showed my pass to the policeman standing discreetly in the reception alcove and took one of the specially programmed lifts which carry senior officers to the sixth-floor inner sanctum. I walked silently down the corridor to my room next to the Director-General's suite. The offices were quiet. Far below I could hear the rumble of tube trains carrying commuters to the West End. I unlocked my door. In front of me stood the essential tools of the intelligence officer’s trade - a desk, two telephones, one scrambled for outside calls, and to one side a large green metal safe with an oversized combination lock on the front. -

The Evolution of British Intelligence Assessment, 1940-41
University of Calgary PRISM: University of Calgary's Digital Repository Graduate Studies Legacy Theses 1999 The evolution of British intelligence assessment, 1940-41 Tang, Godfrey K. Tang, G. K. (1999). The evolution of British intelligence assessment, 1940-41 (Unpublished master's thesis). University of Calgary, Calgary, AB. doi:10.11575/PRISM/18755 http://hdl.handle.net/1880/25336 master thesis University of Calgary graduate students retain copyright ownership and moral rights for their thesis. You may use this material in any way that is permitted by the Copyright Act or through licensing that has been assigned to the document. For uses that are not allowable under copyright legislation or licensing, you are required to seek permission. Downloaded from PRISM: https://prism.ucalgary.ca THE UNIVERSITY OF CALGARY The Evolution of British Intelligence Assessment, 1940-41 by Godfiey K. Tang A THESIS SUBMITTED TO THE FACULTY OF GRADUATE STUDIES IN PARTIAL FLTLFILMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF ARTS DEPARTMENT OF HISTORY CALGARY, ALBERTA JANUARY, 1999 O Godfiey K Tang 1999 National Library Biblioth4que nationale #*lof Canada du Canada Acquisitions and Acquisitions et Bibliographic Services services bibliographiques 395 Wellington Street 395, rue Wellington OnawaON K1AON4 Ottawa ON KIA ON4 Canada Canada The author has granted a non- L'auteur a accorde une licence non exclusive licence allowing the exclusive pernettant Pla National Library of Canada to Blbliotheque nationale du Canada de reproduce, loan, distribute or sell reproduire, preter, distciiuer ou copies of this thesis in microform, vendre des copies de cette these sous paper or electronic formats. la forme de microfiche/f&n, de reproduction sur papier ou sur format Bectronique. -

A Visual Motion Detection Circuit Suggested by Drosophila Connectomics
ARTICLE doi:10.1038/nature12450 A visual motion detection circuit suggested by Drosophila connectomics Shin-ya Takemura1, Arjun Bharioke1, Zhiyuan Lu1,2, Aljoscha Nern1, Shiv Vitaladevuni1, Patricia K. Rivlin1, William T. Katz1, Donald J. Olbris1, Stephen M. Plaza1, Philip Winston1, Ting Zhao1, Jane Anne Horne2, Richard D. Fetter1, Satoko Takemura1, Katerina Blazek1, Lei-Ann Chang1, Omotara Ogundeyi1, Mathew A. Saunders1, Victor Shapiro1, Christopher Sigmund1, Gerald M. Rubin1, Louis K. Scheffer1, Ian A. Meinertzhagen1,2 & Dmitri B. Chklovskii1 Animal behaviour arises from computations in neuronal circuits, but our understanding of these computations has been frustrated by the lack of detailed synaptic connection maps, or connectomes. For example, despite intensive investigations over half a century, the neuronal implementation of local motion detection in the insect visual system remains elusive. Here we develop a semi-automated pipeline using electron microscopy to reconstruct a connectome, containing 379 neurons and 8,637 chemical synaptic contacts, within the Drosophila optic medulla. By matching reconstructed neurons to examples from light microscopy, we assigned neurons to cell types and assembled a connectome of the repeating module of the medulla. Within this module, we identified cell types constituting a motion detection circuit, and showed that the connections onto individual motion-sensitive neurons in this circuit were consistent with their direction selectivity. Our results identify cellular targets for future functional investigations, and demonstrate that connectomes can provide key insights into neuronal computations. Vision in insects has been subject to intense behavioural1,physiological2 neuroanatomy14. Given the time-consuming nature of such recon- and anatomical3 investigations, yet our understanding of its underlying structions, we wanted to determine the smallest medulla volume, neural computations is still far from complete. -

A Pilot Trap Survey of Artificial Reefs in New Jersey for Monitoring of Black Sea Bass, Tautog, and Lobster
Final Report Submitted to the New Jersey Department of Environmental Protection, Division of Fish and Wildlife for the following project: Project Title: A Pilot Trap Survey of Artificial Reefs in New Jersey for Monitoring of Black Sea Bass, Tautog, and Lobster Organization Name: Rutgers, the State University of New Jersey Principal Investigator: Dr. Olaf P. Jensen, Associate Professor, Rutgers University ([email protected], 410-812-4842) Project Co-Investigator: Dr. Douglas Zemeckis, Postdoctoral Researcher, Rutgers University ([email protected], 848-932-3450) NJDEP Project Manager: Peter Clarke, Fisheries Biologist, NJDEP Division of Fish and Wildlife ([email protected]) Performance Period: January 1, 2016 through April 1, 2019 Total Budget: $201,905.00 Table of Contents Introduction……………………………………………………………………………………...1 Project Objectives……………………………………………………………………………….6 Methods………………………………………………………………………………………......8 Study Design: Locations and Times……………………………………………………....8 Protocol: Field and Laboratory Methods…………………………………………………10 2016 Spring Seasonal Monitoring of Artificial Reefs…………………………………….11 2016 Summer Seasonal Monitoring of Artificial Reefs…………………………………..12 2016 Fall Seasonal Monitoring of Artificial Reefs………………………………………13 2017 Spring Seasonal Monitoring of Artificial Reefs…………………………………….14 2017 Summer Seasonal Monitoring of Artificial Reefs……………………………..……15 2017 Fall Seasonal Monitoring of Artificial Reefs………………………………………17 2018 Spring Seasonal Monitoring of Artificial Reefs……………………………………18 2018 Summer Seasonal -

Notes and References Documents Held at the Public Record Office, London, Are Crown Copyright and Are Reproduced by Permission of the Controller Ofhm Stationery Office
Notes and References Documents held at the Public Record Office, London, are crown copyright and are reproduced by permission of the Controller ofHM Stationery Office. I NTRODUCTION Christopher Andrew and David Dilks I. David Dilks (ed.), The Diaries rifSir Alexander Cadogan O.M. 1938-1945 (Lon don , (971) , p. 21. 2. Interview with Professor Hinsley in Part 3 of the BBC Radio 4 documentary series 'T he Profession of Intelligence', written and presented by Christopher Andrew (producer Peter Everett); first broadcast 16 Aug 1981. 3. F. H. Hinsleyet al., British Intelligencein the Second World War (London, 1979-). The first two chapters of volume I contain a useful retrospect on the pre-war development of the intelligence community. Curiously, despite the publication of Professor Hinsley's volumes, the government has decided not to release the official histories commissioned by it on wartime counter-espionage and deception. The forthcoming (non-official) collection of essays edited by Ernest R. May, Knowing One's Enemies: IntelligenceAssessment before the Two World Wars (Princeton) promises to add significantly to our knowledge of the role of intelligence on the eve of the world wars. 4. House of Commons Education, Science and Arts Committee (Session 1982-83) , Public Records: Minutes ofEvidence, pp . 76-7. 5. Chapman Pincher, Their Trade is Treachery (London, 1981). Nigel West, A Matter of Trust: MI51945-72 (London, 1982). Both volumes contain ample evidence of extensive 'inside information'. 6. Nigel West , MI5: British Security Operations /90/-/945 (London, 1981), pp . 41, 49, 58. One of the most interesting studies of British peacetime intelligence which depends on a substantial amount of inside information is Antony Verrier's history of post-war British foreign policy , Through the Looking Glass (London, 1983) . -

Michigan-Specific Reporting Requirements
Version: February 28, 2020 MEDICARE-MEDICAID CAPITATED FINANCIAL ALIGNMENT MODEL REPORTING REQUIREMENTS: MICHIGAN-SPECIFIC REPORTING REQUIREMENTS Issued February 28, 2020 MI-1 Version: February 28, 2020 Table of Contents Michigan-Specific Reporting Requirements Appendix ......................................... MI-3 Introduction ....................................................................................................... MI-3 Definitions .......................................................................................................... MI-3 Variations from the Core Reporting Requirements Document ..................... MI-4 Quality Withhold Measures .............................................................................. MI-5 Reporting on Assessments and IICSPs Completed Prior to First Effective Enrollment Date ................................................................................. MI-6 Guidance on Assessments and IICSPs for Members with a Break in Coverage ............................................................................................................ MI-6 Reporting on Passively Enrolled and Opt-In Enrolled Members .................. MI-8 Reporting on Disenrolled and Retro-disenrolled Members ........................... MI-9 Hybrid Sampling ................................................................................................ MI-9 Value Sets ........................................................................................................ MI-10 Michigan’s Implementation, Ongoing, -

WRAP Theses Shah 2016.Pdf
A Thesis Submitted for the Degree of PhD at the University of Warwick Permanent WRAP URL: http://wrap.warwick.ac.uk/81565 Copyright and reuse: This thesis is made available online and is protected by original copyright. Please scroll down to view the document itself. Please refer to the repository record for this item for information to help you to cite it. Our policy information is available from the repository home page. For more information, please contact the WRAP Team at: [email protected] warwick.ac.uk/lib-publications 1 2 ‘Secret Towns’: British Intelligence in Asia during the Cold War Nikita Shah A thesis submitted in partial fulfilment of the requirements for the degree of Doctor of Philosophy in Politics and International Studies Submitted March 2016 Department of Politics and International Studies University of Warwick 3 Table of Contents List of Abbreviations 1. Introduction 1 1.1 Chapter Outline 21 2. Methodology 25 2.1 Reading the Archive 25 2.2 A Lesson in Empire 31 2.3 Overcoming Archival Obstacles 38 3. Literature Review 49 3.1 Introduction 49 3.2 Definitional Debate – What is Intelligence? 51 3.3 The Special Relationship 63 3.4 The Special Intelligence Relationship in Asia 71 4. Historical Overview 80 4.1 The Special Intelligence Relationship in Asia 80 4.2 The Remnants of Empire 81 4.3 China, Hong Kong, and Taiwan 84 4.4 Burma 87 4.5 India 88 4.6 Indonesia 91 5. The Watchtower: British Intelligence in Hong Kong 95 5.1 Intelligence and Chaos in Hong Kong 101 5.2 Failed Networks and Blind Spots 106 5.3 British Intelligence and the Residue of Empire 112 4 5.4 Sino-Soviet Tensions and Espionage 128 5.5 The Special Intelligence Relationship in Hong Kong 132 6. -

Cambia Il Modo Di Viaggiare
Cambia il modo di viaggiare Nuovo sistema tariffario integrato dei mezzi pubblici www.trenord.it | App Trenord Indice 11 Il sistema tariffario integrato del bacino di mobilità (STIBM) 6 1.1 La suddivisione del territorio del bacino di mobilità in zone tariffarie 6 Tabella 1 Elenco in ordine alfabetico dei comuni ubicati nella zona tariffaria denominata Mi3 7 Tabella 2 Elenco in ordine alfabetico dei comuni ubicati nelle zone tariffarie Mi4, Mi5, Mi6, Mi7, Mi8, Mi9 8 Mappa del sistema tariffario integrato del bacino di mobilità (stibm) Milano - Monza Brianza 12 1.2 Il calcolo della tariffa 14 1.3 Le principali novità del nuovo sistema tariffario 15 22 Tipologie di spostamento e titoli di viaggio 16 2.1 Per spostarsi a Milano 16 2.2 Per spostarsi tra Milano e le località extraurbane 16 2.3 Per spostarsi tra località extraurbane senza attraversare i confini di Milano 17 2.4 Per spostarsi tra località extraurbane attraversando i confini di Milano 17 33 I nuovi titoli di viaggio 18 3.1 Titoli di viaggio ordinari 18 3.2 Titoli di viaggio agevolati e gratuità per ragazzi 19 3.3 Le informazioni presenti sul titolo di viaggio 20 3.4 Regole generali di utilizzo del titolo di viaggio 21 3.5 Il Biglietto Chip On Paper 22 44 Tariffe dei titoli di viaggio ordinari e dei titoli di viaggio agevolati 24 Tabella 3 Biglietti ordinari e altri titoli di viaggio occasionali 25 Tabella 4 Abbonamenti ordinari 26 Tabella 5 Abbonamenti agevolati 27 2 | IL NUOVO SISTEMA TARIFFARIO INTEGRATO - MILANO - MONZA BRIANZA 3 IL NUOVO SISTEMA Mi9 TARIFFARIO INTEGRATO MILANO -

The Baghdad Set
The Baghdad Set Also by Adrian O’Sullivan: Nazi Secret Warfare in Occupied Persia (Iran): The Failure of the German Intelligence Services, 1939–45 (Palgrave, 2014) Espionage and Counterintelligence in Occupied Persia (Iran): The Success of the Allied Secret Services, 1941–45 (Palgrave, 2015) Adrian O’Sullivan The Baghdad Set Iraq through the Eyes of British Intelligence, 1941–45 Adrian O’Sullivan West Vancouver, BC, Canada ISBN 978-3-030-15182-9 ISBN 978-3-030-15183-6 (eBook) https://doi.org/10.1007/978-3-030-15183-6 Library of Congress Control Number: 2019934733 © The Editor(s) (if applicable) and The Author(s), under exclusive licence to Springer Nature Switzerland AG 2019 This work is subject to copyright. All rights are solely and exclusively licensed by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. The use of general descriptive names, registered names, trademarks, service marks, etc. in this publication does not imply, even in the absence of a specific statement, that such names are exempt from the relevant protective laws and regulations and therefore free for general use. The publisher, the authors and the editors are safe to assume that the advice and information in this book are believed to be true and accurate at the date of publication. Neither the pub- lisher nor the authors or the editors give a warranty, express or implied, with respect to the material contained herein or for any errors or omissions that may have been made. -

Churchill's Diplomatic Eavesdropping and Secret Signals Intelligence As
CHURCHILL’S DIPLOMATIC EAVESDROPPING AND SECRET SIGNALS INTELLIGENCE AS AN INSTRUMENT OF BRITISH FOREIGN POLICY, 1941-1944: THE CASE OF TURKEY Submitted for the Degree of Ph.D. Department of History University College London by ROBIN DENNISTON M.A. (Oxon) M.Sc. (Edin) ProQuest Number: 10106668 All rights reserved INFORMATION TO ALL USERS The quality of this reproduction is dependent upon the quality of the copy submitted. In the unlikely event that the author did not send a complete manuscript and there are missing pages, these will be noted. Also, if material had to be removed, a note will indicate the deletion. uest. ProQuest 10106668 Published by ProQuest LLC(2016). Copyright of the Dissertation is held by the Author. All rights reserved. This work is protected against unauthorized copying under Title 17, United States Code. Microform Edition © ProQuest LLC. ProQuest LLC 789 East Eisenhower Parkway P.O. Box 1346 Ann Arbor, Ml 48106-1346 2 ABSTRACT Churchill's interest in secret signals intelligence (sigint) is now common knowledge, but his use of intercepted diplomatic telegrams (bjs) in World War Two has only become apparent with the release in 1994 of his regular supply of Ultra, the DIR/C Archive. Churchill proves to have been a voracious reader of diplomatic intercepts from 1941-44, and used them as part of his communication with the Foreign Office. This thesis establishes the value of these intercepts (particularly those Turkey- sourced) in supplying Churchill and the Foreign Office with authentic information on neutrals' response to the war in Europe, and analyses the way Churchill used them. -

Mathematical RSA Algorithm in Network Security
ISSN(Online): 2319-8753 ISSN (Print): 2347-6710 International Journal of Innovative Research in Science, Engineering and Technology (A High Impact Factor & UGC Approved Journal) Website: www.ijirset.com Vol. 6, Issue 8, August 2017 Mathematical RSA Algorithm in Network Security Sujata Bala1, Dr. Sahdeo Mahto2 Research scholar, Department of Mathematics, Ranchi University, Ranchi, Jharkhand, India1 Associate Professor, Department of Mathematics, Ranchi University, Ranchi, Jharkhand, India2 ABSTRACT: In day to day growing of larger and complex networks are needs to be a system to protect and secure the information on net. Aim of my paper is to describe a mathematical model for network security. This paper presents a design of data encryption and decryption in a network environment using RSA algorithm with specific coding of message. KEYWORDS: encryption, decryption, RSA, algorithm, I. INTRODUCTION Network security controls and prevents the un-authorized access of data, misuse, refutation, of computer network and other network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. It covers a variety of computer networks, both public and private, that are used in everyday jobs; conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security starts with authentication, commonly with a username and a password. Since this requires just one detail authenticating the user name i.e., the password—OTP NO.