Mathematical RSA Algorithm in Network Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
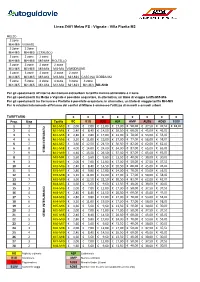
Polimetriche Per Linea STIBM Area Nord.Xlsx
Linea Z401 Melzo FS - Vignate - Villa Fiorita M2 MELZO 2 zone Mi4-Mi5 VIGNATE 2 zone 2 zone Mi4-Mi5 Mi4-Mi5 CERNUSCO 2 zone 2 zone 2 zone Mi4-Mi5 Mi4-Mi5 Mi3-Mi4 PIOLTELLO 3 zone 3 zone 2 zone 2 zone Mi3-Mi5 Mi3-Mi5 Mi3-Mi4 Mi3-Mi4 VIMODRONE 3 zone 3 zone 2 zone 2 zone 2 zone Mi3-Mi5 Mi3-Mi5 Mi3-Mi4 Mi3-Mi4 Mi3-Mi4 CASCINA GOBBA M2 5 zone 5 zone 4 zone 4 zone 3 zone 3 zone Mi1-Mi5 Mi1-Mi5 Mi1-Mi4 Mi1-Mi4 Mi1-Mi3 Mi1-Mi3 MILANO Per gli spostamenti all'interno dei Comuni extraurbani la tariffa minima utilizzabile è 2 zone Per gli spostamenti tra Melzo e Vignate è possibile acquistare, in alternativa, un titolo di viaggio tariffa Mi5-Mi6 Per gli spostamenti tra Cernusco e Pioltello è possibile acquistare, in alternativa, un titolo di viaggio tariffa Mi4-Mi5 Per le relazioni interamente all'interno dei confini di Milano è ammesso l'utilizzo di mensili e annuali urbani TARIFFARIO €€€€€€€€ Prog. Ring Tariffa BO B1G B3G ASP AMP AU26 AO65 B10V 1 3 Mi1-Mi3 € 2,00 € 7,00 € 12,00 € 17,00 € 50,00 € 37,50 € 37,50 € 18,00 2 4 Mi1-Mi4 € 2,40 € 8,40 € 14,50 € 20,50 € 60,00 € 45,00 € 45,00 3 5 Mi1-Mi5 € 2,80 € 9,80 € 17,00 € 24,00 € 70,00 € 53,00 € 53,00 4 6 Mi1-Mi6 € 3,20 € 11,00 € 19,00 € 27,00 € 77,00 € 58,00 € 58,00 5 7 Mi1-Mi7 € 3,60 € 12,50 € 21,50 € 30,50 € 82,00 € 62,00 € 62,00 6 8 Mi1-Mi8 € 4,00 € 14,00 € 24,00 € 34,00 € 87,00 € 65,00 € 65,00 7 9STIBM INTEGRATO Mi1-Mi9€ 4,40 € 15,50 € 26,50 € 37,50 € 87,00 € 65,00 € 65,00 8 2 MI3-MI4 € 1,60 € 5,60 € 9,60 € 13,50 € 40,00 € 30,00 € 30,00 9 3 MI3-MI5 € 2,00 € 7,00 € 12,00 € 17,00 € 50,00 € 37,50 -

Cambia Il Modo Di Viaggiare
Cambia il modo di viaggiare Nuovo sistema tariffario integrato dei mezzi pubblici www.trenord.it | App Trenord Indice 11 Il sistema tariffario integrato del bacino di mobilità (STIBM) 6 1.1 La suddivisione del territorio del bacino di mobilità in zone tariffarie 6 Tabella 1 Elenco in ordine alfabetico dei comuni ubicati nella zona tariffaria denominata Mi3 7 Tabella 2 Elenco in ordine alfabetico dei comuni ubicati nelle zone tariffarie Mi4, Mi5, Mi6, Mi7, Mi8, Mi9 8 Mappa del sistema tariffario integrato del bacino di mobilità (stibm) Milano - Monza Brianza 12 1.2 Il calcolo della tariffa 14 1.3 Le principali novità del nuovo sistema tariffario 15 22 Tipologie di spostamento e titoli di viaggio 16 2.1 Per spostarsi a Milano 16 2.2 Per spostarsi tra Milano e le località extraurbane 16 2.3 Per spostarsi tra località extraurbane senza attraversare i confini di Milano 17 2.4 Per spostarsi tra località extraurbane attraversando i confini di Milano 17 33 I nuovi titoli di viaggio 18 3.1 Titoli di viaggio ordinari 18 3.2 Titoli di viaggio agevolati e gratuità per ragazzi 19 3.3 Le informazioni presenti sul titolo di viaggio 20 3.4 Regole generali di utilizzo del titolo di viaggio 21 3.5 Il Biglietto Chip On Paper 22 44 Tariffe dei titoli di viaggio ordinari e dei titoli di viaggio agevolati 24 Tabella 3 Biglietti ordinari e altri titoli di viaggio occasionali 25 Tabella 4 Abbonamenti ordinari 26 Tabella 5 Abbonamenti agevolati 27 2 | IL NUOVO SISTEMA TARIFFARIO INTEGRATO - MILANO - MONZA BRIANZA 3 IL NUOVO SISTEMA Mi9 TARIFFARIO INTEGRATO MILANO -

Monday/Tuesday Playoff Schedule
2013 TUC MONDAY/TUESDAY PLAYOFF MASTER FIELD SCHEDULE Start End Hockey1 Hockey2 Hockey3 Hockey4 Hockey5 Ulti A Soccer 3A Soccer 3B Cricket E1 Cricket E2 Cricket N1 Cricket N2 Field X 8:00 9:15 MI13 MI14 TI13 TI14 TI15 TI16 MI1 MI2 MI3 MI4 MI15 MI16 9:20 10:35 MI17 MI18 TI17 TI18 TI19 TI20 MI5 MI6 10:40 11:55 MI19 MI20 MC1 MC2 MC3 MI21 MI7 MI8 12:00 1:15 MI9* TI21* TI22 TI23 TI24 MI10 MI11 MI12 1:20 2:35 MI22 MC4 MC6 MC5 MI23 TC1 MI24 MI25 2:40 3:55 TI1 TI2 MC7 TI3 MI26 TC2 TR1 TR2 MI27 4:00 5:15 MC8* TC3 MC10 MC9 TI4 TC4 TR3 TR4 5:20 6:35 TC5* TI5 TI6 TI7 TI8 TC6 TR5 TR6 6:40 7:55 TI9* TC7 TI10 TI11 TI12 TC8 TR8 TR7 Games are to 15 points Half time at 8 points Games are 1 hour and 15 minutes long Soft cap is 10 minutes before the end of game, +1 to highest score 2 Timeouts per team, per game NO TIMEOUTS AFTER SOFT CAP Footblocks not allowed, unless captains agree otherwise 2013 TUC Monday Competitive Playoffs - 1st to 7th Place 3rd Place Bracket Loser of MC4 Competitive Teams Winner of MC9 MC9 Allth Darth (1) Allth Darth (1) 3rd Place Slam Dunks (2) Loser of MC5 The Ligers (3) Winner of MC4 MC4 Krash Kart (4) Krash Kart (4) The El Guapo Sausage Party (5) MC1 Wonky Pooh (6) Winner of MC1 Disc Horde (7) The El Guapo Sausage Winner of MC8 Party (5) MC8 Slam Dunks (2) Champions Winner of MC2 MC2 Disc Horde (7) MC5 The Ligers (3) Winner of MC5 MC3 Winner of MC3 Wonky Pooh (6) Time Hockey3 Score Spirit Hockey4 Score Spirit Hockey5 Score Spirit Score Spirit 10:40 Krash Kart (4) Slam Dunks (2) The Ligers (3) to vs. -

Michigan-Specific Reporting Update Memorandum
DEPARTMENT OF HEALTH & HUMAN SERVICES Centers for Medicare & Medicaid Services 7500 Security Boulevard Baltimore, Maryland 21244-1850 MEDICARE-MEDICAID COORDINATION OFFICE DATE: February 28, 2020 TO: Medicare-Medicaid Plans in Michigan FROM: Lindsay P. Barnette Director, Models, Demonstrations and Analysis Group SUBJECT: Revised Michigan-Specific Reporting Requirements and Value Sets Workbook The purpose of this memorandum is to announce the release of the revised Medicare-Medicaid Capitated Financial Alignment Model Reporting Requirements: Michigan-Specific Reporting Requirements and corresponding Michigan-Specific Value Sets Workbook. These documents provide updated guidance, technical specifications, and applicable codes for the state-specific measures that Michigan Medicare-Medicaid Plans (MMPs) are required to collect and report under the demonstration. As with prior annual update cycles, revisions were made in an effort to streamline and clarify reporting expectations for Michigan MMPs. Please see below for a summary of the substantive changes to the Michigan-Specific Reporting Requirements. Note that the Michigan-Specific Value Sets Workbook also includes changes; Michigan MMPs should carefully review and incorporate the updated value sets, particularly for measures MI2.5, MI5.6, MI7.1, and MI7.3. Michigan MMPs must use the updated specifications and value sets for measures due on or after June 1, 2020. Michigan MMPs must also reference the latest Prevention Quality Indicators (PQI) technical specifications when reporting measure MI5.1 on April 30, 2020. Should you have any questions, please contact the Medicare-Medicaid Coordination Office at [email protected]. SUMMARY OF CHANGES Introduction • In the “Variations from the Core Reporting Requirements Document” section, updated the Michigan-specific guidance regarding data sources for reporting Core Measure 9.2. -

DEFENCE STRATEGIC COMMUNICATIONS the Official Journal of the NATO Strategic Communications Centre of Excellence
ISSN 2500-9478 Volume 1 | Number 1 | Winter 2015 DEFENCE STRATEGIC COMMUNICATIONS The official journal of the NATO Strategic Communications Centre of Excellence Russia’s 21st century information war. Moving past the ‘Funnel’ Model of Counterterrorism Communication. Assessing a century of British military Information Operations. Memetic warfare. The constitutive narratives of Daesh. Method for minimizing the negative consequences of nth order effects in StratCom. The Narrative and Social Media. Public Diplomacy and NATO. 2 ISSN 2500-9478 Defence Strategic Communications Editor-in-Chief Dr. Steve Tatham Editor Anna Reynolds Production and Copy Editor Linda Curika Editorial Board Matt Armstrong, MA Dr. Emma Louise Briant Dr. Nerijus Maliukevicius Thomas Elkjer Nissen, MA Dr. Žaneta Ozolina Dr. Agu Uudelepp Dr. J. Michael Waller Dr. Natascha Zowislo-Grünewald “Defence Strategic Communications” is an international peer-reviewed journal. The journal is a project of the NATO Strategic Communications Centre of Excellence (NATO StratCom COE). It is produced for NATO, NATO member countries, NATO partners, related private and public institutions, and related individuals. It does not represent the opinions or policies of NATO or NATO StratCom COE. The views presented in the following articles are those of the authors alone. © All rights reserved by the NATO StratCom COE. Articles may not be copied, reproduced, distributed or publicly displayed without reference to the NATO StratCom COE and the academic journal. NATO Strategic Communications Centre of Excellence Riga, Kalnciema iela 11b, Latvia LV1048 www.stratcomcoe.org Ph.: 0037167335463 [email protected] 3 INTRODUCTION I am delighted to welcome you to the first edition of ‘Defence Strategic Communications’ Journal. -
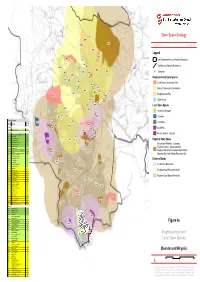
7929 GIS 104 Fig 4A Neighbourhood and Local Open Space
ML1 Open Space Strategy MR1 MF1 MR10 January 2014 7929 GIS 104 MR1 Legend MP2 MS3 MI6 East Dunbartonshire Local Authority Boundary MI7 MI5 Scottish Local Authority Boundaries MS4 MI9 BLF1 MR5 MI15 ! MP3 MI2 MR1 Allotments MR4 MI12 Neighbourhood Open Spaces MS7 MI4 MI1 Local Nature Conservation Site MI10 MI13 MI11 MI3 Natural / Semi-natural Greenspace MR6 MS6 Neighbourhood Park MS2 MR8 MI14 Sports Areas ML2 MR9 MR3 Local Open Spaces BI18 MI8 BI8 Amenity Greenspace BI1 BI2 BI15 MR7 Cemetery BI16 Fitness for Purpose BR6 Quality BF2 Civic Space Site Ref. Site Name MR2 Score BR5 BI14 Baldernock BI4 Local Park BLF1 Baldernock Cemetery 69 BR12 Bearsden BI6 BR2 Kilmardinny Loch Local Nature Reserve 85 Private Gardens / Grounds BR12 Mosshead Park 81 BI11 BP2 Glasgow Uni. Woods 79 BR3 BI10 Regional Open Space BR3 Langfaulds Field 78 BR2 BI17 Bearsden War Memorial 76 BR4 King George V Park 76 Recreational Walkway / Cycleway; BS2 Cairnhill Woods 76 Regional Historic / Natural Attraction; BR1 Colquhoun Park 74 BI4 Grampian Way and Cruchan Road O.S. 73 BI13 Regional Site of Nature Conservation Interest; BR7 Thorn Park 70 BR11 BR6 Heather Ave Open Space 68 Regional Sport and Outdoor Recreation Site BF1 New Kilpatrick Cemetery 67 BI15 Paterson Place O.S. 66 BR8 BS1 Templehill Woods 65 BF1 Distance Bands BR11 Antonine Park 65 BI12 BI18 Stockie Muir Road OS 2 65 Local Parks 400m buffer BI5 Braemar Cres. O.S. 65 BR8 Roman Park 64 BS3 Cairnhill Woods 64 BI17 Neighbourhood Parks 840m buffer BF2 Langfaulds Cemetery 63 BR7 BI2 Stockie Muir Road 1 63 BI16 Abercrombie Dr. -

Lee Richards the West Is Again Facing Multiple Threats Spearheaded by Hostile Information Activity
41 THE RAINBOW IN THE DARK: ASSESSING A CENTURY OF BRITISH MILITARY INFORMATION OPERATIONS Lee Richards The West is again facing multiple threats spearheaded by hostile information activity. ISIL’s exploitation of social media has lured new recruits reaching straight into the bedrooms of our teenagers. Seemingly inexplicably, young intelligent minds have been radicalised through a perversion of their faith. A resurgent Russia has reinvented its ‘hybrid war’ doctrine of the Soviet Cold War-era, believing that it can only be secure when we are weak. Putin’s incursions into Ukraine and now Syria have required a vanguard of blatant untruths filtered through its expansive international news agencies RT and Sputnik. All the while our own performance in Iraq and Afghanistan has been questionable with our strategic communications (stratcom) never becoming as pre-eminent as they were in the World Wars. As will be shown in the following review of British military information operations, a recurrent pattern of under-resourcing, ad-hoc responses, and Whitehall battles of control have been a constant hindrance to effective stratcom, particularly through the Cold War period and despite the best efforts of those involved. It seems, and one hopes, the UK Ministry of Defence through its ‘post-Afghan reset’ has recognised and is attempting to address these deficiencies, as it continues to wrestle at almost every level to understand and respond effectively to the emerging character of war in the information age. In 2012, Stephen Jolly was appointed the UK’s new Director of Defence Communications. It was a controversial appointment.1 An expert on information operations and psyops, Jolly is an unorthodox thinker drawn from an academic background (he is a Fellow of Clare College, Cambridge); he held a Fellowship in Psychological Warfare at the International Centre for Security Analysis at King’s College, London, in the early 2000s; and was a former instructor at the UK Defence Intelligence and Security Centre at Chicksands. -

Sub Rosa Newsletter of the Friends of the Intelligence Corps Museum E Newsletter 09 - Winter 2014 WELCOME to YOUR WINTER SUB ROSA!
11141_FOTICM_Newsletter_Newsletter 05/12/2014 11:12 Page 1 Sub Rosa Newsletter of the Friends of The Intelligence Corps Museum www.intelligencemuseum.org E Newsletter 09 - Winter 2014 WELCOME TO YOUR WINTER SUB ROSA! This edition of Sub Rosa includes fascinating articles ranging from the Congo to Kiel, plus a look at the legendary Legion of Frontiersmen. This reflects the span of activities across the globe in which the Corps has been, and in some cases continues to be involved. Our thanks are due to all our contributors who make the editor’s life so difficult in deciding what to put where opting, when appropriate, to place some items onto the website for members to browse at their leisure! The FICM open meeting and open day held at the museum on 11th September attracted a representative group of FICM members who were joined by a number of the volunteers who work in the museum and archive, together with a strong showing from Corps HQ, mostly in uniform (hence no photographs with this piece). Thus with Curator Sally Ann Reed and Archivist Joyce Hutton on hand to show off the recent museum display developments and a full complement of FICM trustees present, we decided to dispense with any formalities and circulate for more personal conversations with those present and especially our members. The event was doubtless enhanced by a generous supply of tea and cakes! Feedback received during the afternoon was very valuable and thankfully very positive. The reorganisation of many of the exhibits enhanced by a number of new display cabinets, received glowing approval, as did the entirely new interactive WWI display. -

Michigan-Specific Reporting Update Memorandum
DEPARTMENT OF HEALTH & HUMAN SERVICES Centers for Medicare & Medicaid Services 7500 Security Boulevard Baltimore, Maryland 21244-1850 MEDICARE-MEDICAID COORDINATION OFFICE DATE: February 28, 2018 TO: Medicare-Medicaid Plans in Michigan FROM: Lindsay P. Barnette Director, Models, Demonstrations and Analysis Group SUBJECT: Revised Michigan-Specific Reporting Requirements and Value Sets Workbook The purpose of this memorandum is to announce the release of the revised Medicare-Medicaid Capitated Financial Alignment Model Reporting Requirements: Michigan-Specific Reporting Requirements and corresponding Michigan-Specific Value Sets Workbook. These documents provide updated guidance, technical specifications, and applicable codes for the state-specific measures that Michigan Medicare-Medicaid Plans (MMPs) are required to collect and report under the demonstration. Many of the updates were made in an effort to clarify and simplify reporting expectations for Michigan MMPs, consistent with the Administration’s commitment to reduce administrative burden and increase efficiency. Please see below for a summary of the substantive changes to the Michigan-Specific Reporting Requirements. Note that the Michigan-Specific Value Sets Workbook also includes changes; Michigan MMPs should carefully review and incorporate the updated value sets, particularly for measures MI2.5, MI2.6, MI5.3, MI5.6, and MI7.3. Michigan MMPs must use the updated specifications and value sets for measures due on or after May 31, 2018. Should you have any questions, please contact the Medicare-Medicaid Coordination Office at [email protected]. SUMMARY OF CHANGES Introduction • In the “Variations from the Core Document” section, added additional Michigan-specific guidance for reporting the new Core Measure 3.2 and updated the Michigan-specific guidance for reporting Core Measure 9.2. -

2021 Game Schedule
Mooresville Baseball League - 2021 Game Schedule Baseball MINOR ROOKIE PEEWEE INSTRUCTIONAL MAJOR Softball STB 7-8U (CP) 9-10U (KP) 11-12U (S) Opening Day - April 17 May 17 - May 22 Diamond Diamond Date Day Time Date Day Time 1 2 3 4 5 6 1 2 3 4 5 6 9:00 IN1-IN2 IN3-IN8 MA1-MA2 MA3-MA5 IN4-IN7 17-May Mon 6:00 S1-S2 IN2-IN7 MA5-MA1 MA2-MA4 MI2 - MI5 11:00 MI2 - MI1 MI3 - MI8 MI4 - MI7 MI5 - MI6 STB1-STB2 18-May Tue 6:00 MI2 - MI1 MI3 - MI8 MI4 - MI7 MI5 - MI6 17-Apr Sat 1:00 PW1-PW2 PW3-PW10 PW4-PW9 PW5-PW8 PW6-PW7 19-May Wed 6:00 S2-S3 IN3-IN6 MA2-MA5 MA4-MA3 PW2-PW9 3:00 R1-R4 R2-R3 CP1-CP2 CP3-CP4 KP1-KP2 20-May Thu 6:00 MI3 - MI4 MI1 - MI7 MI8 - MI6 MI2 - MI5 5:00 KP3-KP4 IN5-IN6 STB3-STB4 STB5-STB6 21-May Fri 6:00 CP2-CP3 CP4-CP1 KP1-KP2 KP3-KP4 9:00 IN4-IN5 IN8-IN1 STB3-STB6 STB4-STB1 April 19 - April 24 11:00 R3-R1 R4-R2 STB2-STB5 Diamond 22-May Sat 1:00 PW3-PW8 PW1-PW10 PW5-PW6 PW4-PW7 Date Day Time 1 2 3 4 5 6 3:00 19-Apr Mon 6:00 S1-S2 R1-R4 MA3-MA2 MA4-MA1 5:00 20-Apr Tue 6:00 Cancel Cancel Cancel Cancel 21-Apr Wed 6:00 Cancel Cancel Cancel Cancel May 24 - May 29 22-Apr Thu 6:00 S2-S3 R2-R3 MA1-MA3 MA5-MA4 IN8-IN6 Diamond Date Day Time 23-Apr Fri 6:00 PW2-PW3 PW1-PW7 PW8-PW6 PW9-PW5 PW10-PW4 1 2 3 4 5 6 9:00 IN3-IN4 IN2-IN5 STB1-STB6 STB2-STB4 IN1-IN7 24-May Mon 6:00 S3-S1 KP2-KP3 MA1-MA2 MA3-MA5 STB2-STB4 11:00 R1-R2 R3-R4 STB3-STB5 PW7-PW8 PW5-PW10 25-May Tue 6:00 MI6 - MI2 MI7 - MI8 MI4 - MI1 MI5 - MI3 STB1-STB6 24-Apr Sat 1:00 CP3-CP1 CP2-CP4 PW3-PW1 PW4-PW2 26-May Wed 6:00 S1-S2 KP4-KP1 MA3-MA2 MA4-MA1 3:00 27-May Thu 6:00 -
Investigating the Diversity of the Terrestrial Invertebrate Fauna of Antarctica: a Closer Look at the Stereotydeus (Acari: Prostigmata) Genus
Investigating the diversity of the terrestrial invertebrate fauna of Antarctica: a closer look at the Stereotydeus (Acari: Prostigmata) genus Claudia Brunetti 1,*, Henk Siepel 2, Pietro Paolo Fanciulli 1, Francesco Nardi 1 and Antonio Carapelli 1 1 Department of Life Sciences, University of Siena, Via Aldo Moro 2, 53100 SI Siena, Italy; 2 Department of Animal Ecology and Physiology, Institute for Water and Wetland Research, Radboud University, Heyendaalseweg 135, 6525 AJ Nijmegen, The Netherlands * Corresponding author: [email protected] 1 Abstract: In the extreme Antarctic ecosystems, plants and invertebrates are confine to sparse and isolated ice-free refugia where they survived for millions of years and where they undergo differentiation and population divergence, potentially resulting in speciation. In invertebrates' populations, the gene flow is strongly affected and reduce by their limited dispersal abilities, their specific habitat requirements and the substantial geographical barriers. And thus, results in high genetic differentiation between clusters of individuals. Mites are surely the predominant invertebrate group of Continental Antarctica and the free-living genus Stereotydeus Berlese, 1901 (Acari: Prostigmata) is one of the most abundant along the coastal zones of Victoria Land and the Transantarctic Mountains. To examine the biodiversity and the phylogeographic distribution ranges of Stereotydeus spp. across Victoria Land, we conducted an integrated analysis of the genus through morphological, phylogenetic and population genetics studies. The results suggest a possible common evolutionary history in several isolated glacial refugia, with scarce gene flow even within populations probably resulting from inter/intra-specific events influenced by several abiotic/biotic factors. Keywords: Victoria Land; molecular phylogeny; biogeography; Acari; Stereotydeus spp. -

MBT FAQ Index
MBT FAQ Index *Words surrounded by quotation marks are defined in the MBT statute* A Accounting Methods Actual or Annual A8, A11, A31, C33, U28, M55 Cash or Accrual C32, C40, M16, M33, U17, U21 Accounts Receivable Factoring Companies B30, M54 “Active Shareholder” C3, C20 “Actively Solicits” Ap4, B11, F1, N2, N4, N5, N6, N7, N8, N10, N11, U12 Actual Method, Computation of Tax for First Taxable Year Less Than 12 Months A8, A11 Amended Returns C9, C13 Annual Method, Computation of Tax for First Taxable Year Less Than 12 Months A8, A11, A31 Annual Returns A6, A7, A10, A11, A14, A17, A20, Fi6 Apportionment Ap1, Ap2, Ap3, Ap5, M2, M5, N1, N4, N5, U3, U5 Arts and Culture Credit C15, C26 Associations (Condominiums, Homeowners and Timeshares) Mi29 B “Base Investment” Fi8 Book Tax Difference B5, B6, Mi9 Bottle Deposit Administration Credit C34, Mi33, M55 Brother-Sister Corporations U7, U9, U24, U25, U33, U34 Brownfield Rehabilitation Credit C7, C8, C9, C13, C24, C26, U22 “Business Activity” Ap1, Ap2, Ap5, B4, B7, B20, B21, B29, B30, M2, M10, M11, M40, M42, M52, M54 “Business Income” A22, A25, Ap2, B2, B3, B4, B7, B12, B14, B16, B18, B20, B21, B22, B23, B29, B30, M10, M11, M12, M13, M27, M38, M40, M42, M43, M44, M52, M54 Business Income Tax Base Administrative A14 Calculation A22, A25, A27, B10, B12, B19, B22, B27, B29, C14, C33, Mi20, M15, M27, M36, M38, M42, M55, N9 Included Ap2, B4, B8, B20, B21, B28, M10, M11, M40, M49, M54 Deduction B2, B3, B5, B6, B18, B27, Mi9, Mi10 Unitary Business Group U5, U27, U32 Business Loss, MBT B10, M15, M36, U27