Humeceptor® – Technical Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Polimetriche Per Linea STIBM Area Nord.Xlsx
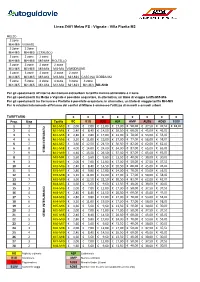
Linea Z401 Melzo FS - Vignate - Villa Fiorita M2 MELZO 2 zone Mi4-Mi5 VIGNATE 2 zone 2 zone Mi4-Mi5 Mi4-Mi5 CERNUSCO 2 zone 2 zone 2 zone Mi4-Mi5 Mi4-Mi5 Mi3-Mi4 PIOLTELLO 3 zone 3 zone 2 zone 2 zone Mi3-Mi5 Mi3-Mi5 Mi3-Mi4 Mi3-Mi4 VIMODRONE 3 zone 3 zone 2 zone 2 zone 2 zone Mi3-Mi5 Mi3-Mi5 Mi3-Mi4 Mi3-Mi4 Mi3-Mi4 CASCINA GOBBA M2 5 zone 5 zone 4 zone 4 zone 3 zone 3 zone Mi1-Mi5 Mi1-Mi5 Mi1-Mi4 Mi1-Mi4 Mi1-Mi3 Mi1-Mi3 MILANO Per gli spostamenti all'interno dei Comuni extraurbani la tariffa minima utilizzabile è 2 zone Per gli spostamenti tra Melzo e Vignate è possibile acquistare, in alternativa, un titolo di viaggio tariffa Mi5-Mi6 Per gli spostamenti tra Cernusco e Pioltello è possibile acquistare, in alternativa, un titolo di viaggio tariffa Mi4-Mi5 Per le relazioni interamente all'interno dei confini di Milano è ammesso l'utilizzo di mensili e annuali urbani TARIFFARIO €€€€€€€€ Prog. Ring Tariffa BO B1G B3G ASP AMP AU26 AO65 B10V 1 3 Mi1-Mi3 € 2,00 € 7,00 € 12,00 € 17,00 € 50,00 € 37,50 € 37,50 € 18,00 2 4 Mi1-Mi4 € 2,40 € 8,40 € 14,50 € 20,50 € 60,00 € 45,00 € 45,00 3 5 Mi1-Mi5 € 2,80 € 9,80 € 17,00 € 24,00 € 70,00 € 53,00 € 53,00 4 6 Mi1-Mi6 € 3,20 € 11,00 € 19,00 € 27,00 € 77,00 € 58,00 € 58,00 5 7 Mi1-Mi7 € 3,60 € 12,50 € 21,50 € 30,50 € 82,00 € 62,00 € 62,00 6 8 Mi1-Mi8 € 4,00 € 14,00 € 24,00 € 34,00 € 87,00 € 65,00 € 65,00 7 9STIBM INTEGRATO Mi1-Mi9€ 4,40 € 15,50 € 26,50 € 37,50 € 87,00 € 65,00 € 65,00 8 2 MI3-MI4 € 1,60 € 5,60 € 9,60 € 13,50 € 40,00 € 30,00 € 30,00 9 3 MI3-MI5 € 2,00 € 7,00 € 12,00 € 17,00 € 50,00 € 37,50 -

SPYCATCHER by PETER WRIGHT with Paul Greengrass WILLIAM
SPYCATCHER by PETER WRIGHT with Paul Greengrass WILLIAM HEINEMANN: AUSTRALIA First published in 1987 by HEINEMANN PUBLISHERS AUSTRALIA (A division of Octopus Publishing Group/Australia Pty Ltd) 85 Abinger Street, Richmond, Victoria, 3121. Copyright (c) 1987 by Peter Wright ISBN 0-85561-166-9 All Rights Reserved. No part of this publication may be reproduced, stored in or introduced into a retrieval system, or transmitted, in any form or by any means (electronic, mechanical, photocopying, recording or otherwise) without the prior written permission of the publisher. TO MY WIFE LOIS Prologue For years I had wondered what the last day would be like. In January 1976 after two decades in the top echelons of the British Security Service, MI5, it was time to rejoin the real world. I emerged for the final time from Euston Road tube station. The winter sun shone brightly as I made my way down Gower Street toward Trafalgar Square. Fifty yards on I turned into the unmarked entrance to an anonymous office block. Tucked between an art college and a hospital stood the unlikely headquarters of British Counterespionage. I showed my pass to the policeman standing discreetly in the reception alcove and took one of the specially programmed lifts which carry senior officers to the sixth-floor inner sanctum. I walked silently down the corridor to my room next to the Director-General's suite. The offices were quiet. Far below I could hear the rumble of tube trains carrying commuters to the West End. I unlocked my door. In front of me stood the essential tools of the intelligence officer’s trade - a desk, two telephones, one scrambled for outside calls, and to one side a large green metal safe with an oversized combination lock on the front. -

The Evolution of British Intelligence Assessment, 1940-41
University of Calgary PRISM: University of Calgary's Digital Repository Graduate Studies Legacy Theses 1999 The evolution of British intelligence assessment, 1940-41 Tang, Godfrey K. Tang, G. K. (1999). The evolution of British intelligence assessment, 1940-41 (Unpublished master's thesis). University of Calgary, Calgary, AB. doi:10.11575/PRISM/18755 http://hdl.handle.net/1880/25336 master thesis University of Calgary graduate students retain copyright ownership and moral rights for their thesis. You may use this material in any way that is permitted by the Copyright Act or through licensing that has been assigned to the document. For uses that are not allowable under copyright legislation or licensing, you are required to seek permission. Downloaded from PRISM: https://prism.ucalgary.ca THE UNIVERSITY OF CALGARY The Evolution of British Intelligence Assessment, 1940-41 by Godfiey K. Tang A THESIS SUBMITTED TO THE FACULTY OF GRADUATE STUDIES IN PARTIAL FLTLFILMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF ARTS DEPARTMENT OF HISTORY CALGARY, ALBERTA JANUARY, 1999 O Godfiey K Tang 1999 National Library Biblioth4que nationale #*lof Canada du Canada Acquisitions and Acquisitions et Bibliographic Services services bibliographiques 395 Wellington Street 395, rue Wellington OnawaON K1AON4 Ottawa ON KIA ON4 Canada Canada The author has granted a non- L'auteur a accorde une licence non exclusive licence allowing the exclusive pernettant Pla National Library of Canada to Blbliotheque nationale du Canada de reproduce, loan, distribute or sell reproduire, preter, distciiuer ou copies of this thesis in microform, vendre des copies de cette these sous paper or electronic formats. la forme de microfiche/f&n, de reproduction sur papier ou sur format Bectronique. -

Notes and References Documents Held at the Public Record Office, London, Are Crown Copyright and Are Reproduced by Permission of the Controller Ofhm Stationery Office
Notes and References Documents held at the Public Record Office, London, are crown copyright and are reproduced by permission of the Controller ofHM Stationery Office. I NTRODUCTION Christopher Andrew and David Dilks I. David Dilks (ed.), The Diaries rifSir Alexander Cadogan O.M. 1938-1945 (Lon don , (971) , p. 21. 2. Interview with Professor Hinsley in Part 3 of the BBC Radio 4 documentary series 'T he Profession of Intelligence', written and presented by Christopher Andrew (producer Peter Everett); first broadcast 16 Aug 1981. 3. F. H. Hinsleyet al., British Intelligencein the Second World War (London, 1979-). The first two chapters of volume I contain a useful retrospect on the pre-war development of the intelligence community. Curiously, despite the publication of Professor Hinsley's volumes, the government has decided not to release the official histories commissioned by it on wartime counter-espionage and deception. The forthcoming (non-official) collection of essays edited by Ernest R. May, Knowing One's Enemies: IntelligenceAssessment before the Two World Wars (Princeton) promises to add significantly to our knowledge of the role of intelligence on the eve of the world wars. 4. House of Commons Education, Science and Arts Committee (Session 1982-83) , Public Records: Minutes ofEvidence, pp . 76-7. 5. Chapman Pincher, Their Trade is Treachery (London, 1981). Nigel West, A Matter of Trust: MI51945-72 (London, 1982). Both volumes contain ample evidence of extensive 'inside information'. 6. Nigel West , MI5: British Security Operations /90/-/945 (London, 1981), pp . 41, 49, 58. One of the most interesting studies of British peacetime intelligence which depends on a substantial amount of inside information is Antony Verrier's history of post-war British foreign policy , Through the Looking Glass (London, 1983) . -

Michigan-Specific Reporting Requirements
Version: February 28, 2020 MEDICARE-MEDICAID CAPITATED FINANCIAL ALIGNMENT MODEL REPORTING REQUIREMENTS: MICHIGAN-SPECIFIC REPORTING REQUIREMENTS Issued February 28, 2020 MI-1 Version: February 28, 2020 Table of Contents Michigan-Specific Reporting Requirements Appendix ......................................... MI-3 Introduction ....................................................................................................... MI-3 Definitions .......................................................................................................... MI-3 Variations from the Core Reporting Requirements Document ..................... MI-4 Quality Withhold Measures .............................................................................. MI-5 Reporting on Assessments and IICSPs Completed Prior to First Effective Enrollment Date ................................................................................. MI-6 Guidance on Assessments and IICSPs for Members with a Break in Coverage ............................................................................................................ MI-6 Reporting on Passively Enrolled and Opt-In Enrolled Members .................. MI-8 Reporting on Disenrolled and Retro-disenrolled Members ........................... MI-9 Hybrid Sampling ................................................................................................ MI-9 Value Sets ........................................................................................................ MI-10 Michigan’s Implementation, Ongoing, -

Cambia Il Modo Di Viaggiare
Cambia il modo di viaggiare Nuovo sistema tariffario integrato dei mezzi pubblici www.trenord.it | App Trenord Indice 11 Il sistema tariffario integrato del bacino di mobilità (STIBM) 6 1.1 La suddivisione del territorio del bacino di mobilità in zone tariffarie 6 Tabella 1 Elenco in ordine alfabetico dei comuni ubicati nella zona tariffaria denominata Mi3 7 Tabella 2 Elenco in ordine alfabetico dei comuni ubicati nelle zone tariffarie Mi4, Mi5, Mi6, Mi7, Mi8, Mi9 8 Mappa del sistema tariffario integrato del bacino di mobilità (stibm) Milano - Monza Brianza 12 1.2 Il calcolo della tariffa 14 1.3 Le principali novità del nuovo sistema tariffario 15 22 Tipologie di spostamento e titoli di viaggio 16 2.1 Per spostarsi a Milano 16 2.2 Per spostarsi tra Milano e le località extraurbane 16 2.3 Per spostarsi tra località extraurbane senza attraversare i confini di Milano 17 2.4 Per spostarsi tra località extraurbane attraversando i confini di Milano 17 33 I nuovi titoli di viaggio 18 3.1 Titoli di viaggio ordinari 18 3.2 Titoli di viaggio agevolati e gratuità per ragazzi 19 3.3 Le informazioni presenti sul titolo di viaggio 20 3.4 Regole generali di utilizzo del titolo di viaggio 21 3.5 Il Biglietto Chip On Paper 22 44 Tariffe dei titoli di viaggio ordinari e dei titoli di viaggio agevolati 24 Tabella 3 Biglietti ordinari e altri titoli di viaggio occasionali 25 Tabella 4 Abbonamenti ordinari 26 Tabella 5 Abbonamenti agevolati 27 2 | IL NUOVO SISTEMA TARIFFARIO INTEGRATO - MILANO - MONZA BRIANZA 3 IL NUOVO SISTEMA Mi9 TARIFFARIO INTEGRATO MILANO -

Mathematical RSA Algorithm in Network Security
ISSN(Online): 2319-8753 ISSN (Print): 2347-6710 International Journal of Innovative Research in Science, Engineering and Technology (A High Impact Factor & UGC Approved Journal) Website: www.ijirset.com Vol. 6, Issue 8, August 2017 Mathematical RSA Algorithm in Network Security Sujata Bala1, Dr. Sahdeo Mahto2 Research scholar, Department of Mathematics, Ranchi University, Ranchi, Jharkhand, India1 Associate Professor, Department of Mathematics, Ranchi University, Ranchi, Jharkhand, India2 ABSTRACT: In day to day growing of larger and complex networks are needs to be a system to protect and secure the information on net. Aim of my paper is to describe a mathematical model for network security. This paper presents a design of data encryption and decryption in a network environment using RSA algorithm with specific coding of message. KEYWORDS: encryption, decryption, RSA, algorithm, I. INTRODUCTION Network security controls and prevents the un-authorized access of data, misuse, refutation, of computer network and other network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. It covers a variety of computer networks, both public and private, that are used in everyday jobs; conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security starts with authentication, commonly with a username and a password. Since this requires just one detail authenticating the user name i.e., the password—OTP NO. -

Monday/Tuesday Playoff Schedule
2013 TUC MONDAY/TUESDAY PLAYOFF MASTER FIELD SCHEDULE Start End Hockey1 Hockey2 Hockey3 Hockey4 Hockey5 Ulti A Soccer 3A Soccer 3B Cricket E1 Cricket E2 Cricket N1 Cricket N2 Field X 8:00 9:15 MI13 MI14 TI13 TI14 TI15 TI16 MI1 MI2 MI3 MI4 MI15 MI16 9:20 10:35 MI17 MI18 TI17 TI18 TI19 TI20 MI5 MI6 10:40 11:55 MI19 MI20 MC1 MC2 MC3 MI21 MI7 MI8 12:00 1:15 MI9* TI21* TI22 TI23 TI24 MI10 MI11 MI12 1:20 2:35 MI22 MC4 MC6 MC5 MI23 TC1 MI24 MI25 2:40 3:55 TI1 TI2 MC7 TI3 MI26 TC2 TR1 TR2 MI27 4:00 5:15 MC8* TC3 MC10 MC9 TI4 TC4 TR3 TR4 5:20 6:35 TC5* TI5 TI6 TI7 TI8 TC6 TR5 TR6 6:40 7:55 TI9* TC7 TI10 TI11 TI12 TC8 TR8 TR7 Games are to 15 points Half time at 8 points Games are 1 hour and 15 minutes long Soft cap is 10 minutes before the end of game, +1 to highest score 2 Timeouts per team, per game NO TIMEOUTS AFTER SOFT CAP Footblocks not allowed, unless captains agree otherwise 2013 TUC Monday Competitive Playoffs - 1st to 7th Place 3rd Place Bracket Loser of MC4 Competitive Teams Winner of MC9 MC9 Allth Darth (1) Allth Darth (1) 3rd Place Slam Dunks (2) Loser of MC5 The Ligers (3) Winner of MC4 MC4 Krash Kart (4) Krash Kart (4) The El Guapo Sausage Party (5) MC1 Wonky Pooh (6) Winner of MC1 Disc Horde (7) The El Guapo Sausage Winner of MC8 Party (5) MC8 Slam Dunks (2) Champions Winner of MC2 MC2 Disc Horde (7) MC5 The Ligers (3) Winner of MC5 MC3 Winner of MC3 Wonky Pooh (6) Time Hockey3 Score Spirit Hockey4 Score Spirit Hockey5 Score Spirit Score Spirit 10:40 Krash Kart (4) Slam Dunks (2) The Ligers (3) to vs. -

Evolution of Stickleback in 50 Years on Earthquake-Uplifted Islands
Evolution of stickleback in 50 years on earthquake-uplifted islands Emily A. Lescaka,b, Susan L. Basshamc, Julian Catchenc,d, Ofer Gelmondb,1, Mary L. Sherbickb, Frank A. von Hippelb, and William A. Creskoc,2 aSchool of Fisheries and Ocean Sciences, University of Alaska Fairbanks, Fairbanks, AK 99775; bDepartment of Biological Sciences, University of Alaska Anchorage, Anchorage, AK 99508; cInstitute of Ecology and Evolution, University of Oregon, Eugene, OR 97403; and dDepartment of Animal Biology, University of Illinois at Urbana–Champaign, Urbana, IL 61801 Edited by John C. Avise, University of California, Irvine, CA, and approved November 9, 2015 (received for review June 19, 2015) How rapidly can animal populations in the wild evolve when faced occur immediately after a habitat shift or environmental distur- with sudden environmental shifts? Uplift during the 1964 Great bance (26, 27). However, because of previous technological lim- Alaska Earthquake abruptly created freshwater ponds on multiple itations, few studies of rapid differentiation in the wild have islands in Prince William Sound and the Gulf of Alaska. In the short included genetic data to fully disentangle evolution from induced time since the earthquake, the phenotypes of resident freshwater phenotypic plasticity. The small numbers of markers previously threespine stickleback fish on at least three of these islands have available for most population genetic studies have not provided changed dramatically from their oceanic ancestors. To test the the necessary precision with which to analyze very recently diverged hypothesis that these freshwater populations were derived from populations (but see refs. 28 and 29). As a consequence, the fre- oceanic ancestors only 50 y ago, we generated over 130,000 single- quency of contemporary evolution in the wild is still poorly defined, nucleotide polymorphism genotypes from more than 1,000 individ- and its genetic and genomic basis remains unclear (30). -

Michigan-Specific Reporting Update Memorandum
DEPARTMENT OF HEALTH & HUMAN SERVICES Centers for Medicare & Medicaid Services 7500 Security Boulevard Baltimore, Maryland 21244-1850 MEDICARE-MEDICAID COORDINATION OFFICE DATE: February 28, 2020 TO: Medicare-Medicaid Plans in Michigan FROM: Lindsay P. Barnette Director, Models, Demonstrations and Analysis Group SUBJECT: Revised Michigan-Specific Reporting Requirements and Value Sets Workbook The purpose of this memorandum is to announce the release of the revised Medicare-Medicaid Capitated Financial Alignment Model Reporting Requirements: Michigan-Specific Reporting Requirements and corresponding Michigan-Specific Value Sets Workbook. These documents provide updated guidance, technical specifications, and applicable codes for the state-specific measures that Michigan Medicare-Medicaid Plans (MMPs) are required to collect and report under the demonstration. As with prior annual update cycles, revisions were made in an effort to streamline and clarify reporting expectations for Michigan MMPs. Please see below for a summary of the substantive changes to the Michigan-Specific Reporting Requirements. Note that the Michigan-Specific Value Sets Workbook also includes changes; Michigan MMPs should carefully review and incorporate the updated value sets, particularly for measures MI2.5, MI5.6, MI7.1, and MI7.3. Michigan MMPs must use the updated specifications and value sets for measures due on or after June 1, 2020. Michigan MMPs must also reference the latest Prevention Quality Indicators (PQI) technical specifications when reporting measure MI5.1 on April 30, 2020. Should you have any questions, please contact the Medicare-Medicaid Coordination Office at [email protected]. SUMMARY OF CHANGES Introduction • In the “Variations from the Core Reporting Requirements Document” section, updated the Michigan-specific guidance regarding data sources for reporting Core Measure 9.2. -

DEFENCE STRATEGIC COMMUNICATIONS the Official Journal of the NATO Strategic Communications Centre of Excellence
ISSN 2500-9478 Volume 1 | Number 1 | Winter 2015 DEFENCE STRATEGIC COMMUNICATIONS The official journal of the NATO Strategic Communications Centre of Excellence Russia’s 21st century information war. Moving past the ‘Funnel’ Model of Counterterrorism Communication. Assessing a century of British military Information Operations. Memetic warfare. The constitutive narratives of Daesh. Method for minimizing the negative consequences of nth order effects in StratCom. The Narrative and Social Media. Public Diplomacy and NATO. 2 ISSN 2500-9478 Defence Strategic Communications Editor-in-Chief Dr. Steve Tatham Editor Anna Reynolds Production and Copy Editor Linda Curika Editorial Board Matt Armstrong, MA Dr. Emma Louise Briant Dr. Nerijus Maliukevicius Thomas Elkjer Nissen, MA Dr. Žaneta Ozolina Dr. Agu Uudelepp Dr. J. Michael Waller Dr. Natascha Zowislo-Grünewald “Defence Strategic Communications” is an international peer-reviewed journal. The journal is a project of the NATO Strategic Communications Centre of Excellence (NATO StratCom COE). It is produced for NATO, NATO member countries, NATO partners, related private and public institutions, and related individuals. It does not represent the opinions or policies of NATO or NATO StratCom COE. The views presented in the following articles are those of the authors alone. © All rights reserved by the NATO StratCom COE. Articles may not be copied, reproduced, distributed or publicly displayed without reference to the NATO StratCom COE and the academic journal. NATO Strategic Communications Centre of Excellence Riga, Kalnciema iela 11b, Latvia LV1048 www.stratcomcoe.org Ph.: 0037167335463 [email protected] 3 INTRODUCTION I am delighted to welcome you to the first edition of ‘Defence Strategic Communications’ Journal. -

Confidence Men the Mediterranean Double-Cross System, 1941-45 By
Confidence Men The Mediterranean Double-Cross System, 1941-45 by Brett Edward Lintott A thesis submitted in conformity with the requirements for the Degree of Doctor of Philosophy, Graduate Department of History, in the University of Toronto © Copyright by Brett Edward Lintott, 2015 Abstract Confidence Men The Mediterranean Double-Cross System, 1941-45 Brett Edward Lintott Doctor of Philosophy Department of History University of Toronto, 2015 This dissertation provides an analysis of the Mediterranean double-cross system of the Second World War, which was composed of a number of double agents who were turned by the Allies and operated against their ostensible German spymasters. Utilizing many freshly released archival materials, this study assesses how the double-cross system was constructed, why it was an effective instrument, and how it contributed to Allied success in two areas: security and counter-intelligence, and military deception. The focus is thus on both organization and operations. The chapters cover three chronological periods. In the first — 1941-42 — the initial operational usage of a double agent is assessed, along with the development of early organizational structures to manage and operate individual cases as components of a team of spies. The second section, covering 1943, assesses three issues: major organizational innovations made early that year; the subsequent use of the double agent system to deceive the Germans regarding the planned invasion of Sicily in July; and the ongoing effort to utilize double agents to ensure a stable security and counter-intelligence environment in the Mediterranean theatre. The third and final section analyzes events in 1944, with a focus on double-cross deception in Italy and France, and on the emergence of more systematic security and counter-intelligence double-cross operations in Italy and the Middle East.