³5Hjxodwlqj´
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Zahlensysteme
A Zahlensysteme Außer dem Dezimalsystem sind das Dual-,dasOktal- und das Hexadezimalsystem gebräuchlich. Ferner spielt das Binär codierte Dezimalsystem (BCD) bei manchen Anwendungen eine Rolle. Bei diesem sind die einzelnen Dezimalstellen für sich dual dargestellt. Die folgende Tabelle enthält die Werte von 0 bis dezimal 255. Be- quemlichkeitshalber sind auch die zugeordneten ASCII-Zeichen aufgeführt. dezimal dual oktal hex BCD ASCII 0 0 0 0 0 nul 11111soh 2102210stx 3113311etx 4 100 4 4 100 eot 5 101 5 5 101 enq 6 110 6 6 110 ack 7 111 7 7 111 bel 8 1000 10 8 1000 bs 9 1001 11 9 1001 ht 10 1010 12 a 1.0 lf 11 101 13 b 1.1 vt 12 1100 14 c 1.10 ff 13 1101 15 d 1.11 cr 14 1110 16 e 1.100 so 15 1111 17 f 1.101 si 16 10000 20 10 1.110 dle 17 10001 21 11 1.111 dc1 18 10010 22 12 1.1000 dc2 19 10011 23 13 1.1001 dc3 20 10100 24 14 10.0 dc4 21 10101 25 15 10.1 nak 22 10110 26 16 10.10 syn 430 A Zahlensysteme 23 10111 27 17 10.11 etb 24 11000 30 18 10.100 can 25 11001 31 19 10.101 em 26 11010 32 1a 10.110 sub 27 11011 33 1b 10.111 esc 28 11100 34 1c 10.1000 fs 29 11101 35 1d 10.1001 gs 30 11110 36 1e 11.0 rs 31 11111 37 1f 11.1 us 32 100000 40 20 11.10 space 33 100001 41 21 11.11 ! 34 100010 42 22 11.100 ” 35 100011 43 23 11.101 # 36 100100 44 24 11.110 $ 37 100101 45 25 11.111 % 38 100110 46 26 11.1000 & 39 100111 47 27 11.1001 ’ 40 101000 50 28 100.0 ( 41 101001 51 29 100.1 ) 42 101010 52 2a 100.10 * 43 101011 53 2b 100.11 + 44 101100 54 2c 100.100 , 45 101101 55 2d 100.101 - 46 101110 56 2e 100.110 . -

Eszter Babarczy: Community Based Trust on the Internet
PTE BTK Nyelvtudományi Doktori Iskola Kommunikáció Doktori Program Babarczy Eszter: Community Based Trust on the Internet Doktori értekezés Témavezető: Horányi Özséb egyetemi tanár 2011. 1 Community-based trust on the internet Tartalom Introduction .................................................................................................................................................. 3 II. A very brief history of the internet ........................................................................................................... 9 Early Days ............................................................................................................................................... 11 Mainstream internet .............................................................................................................................. 12 The internet of social software .............................................................................................................. 15 III Early trust related problems and solutions ............................................................................................ 20 Trading .................................................................................................................................................... 20 Risks of and trust in content ....................................................................................................................... 22 UGC and its discontents: Wikipedia ...................................................................................................... -

The Internet Is a Semicommons
GRIMMELMANN_10_04_29_APPROVED_PAGINATED 4/29/2010 11:26 PM THE INTERNET IS A SEMICOMMONS James Grimmelmann* I. INTRODUCTION As my contribution to this Symposium on David Post’s In Search of Jefferson’s Moose1 and Jonathan Zittrain’s The Future of the Internet,2 I’d like to take up a question with which both books are obsessed: what makes the Internet work? Post’s answer is that the Internet is uniquely Jeffersonian; it embodies a civic ideal of bottom-up democracy3 and an intellectual ideal of generous curiosity.4 Zittrain’s answer is that the Internet is uniquely generative; it enables its users to experiment with new uses and then share their innovations with each other.5 Both books tell a story about how the combination of individual freedom and a cooperative ethos have driven the Internet’s astonishing growth. In that spirit, I’d like to suggest a third reason that the Internet works: it gets the property boundaries right. Specifically, I see the Internet as a particularly striking example of what property theorist Henry Smith has named a semicommons.6 It mixes private property in individual computers and network links with a commons in the communications that flow * Associate Professor, New York Law School. My thanks for their comments to Jack Balkin, Shyam Balganesh, Aislinn Black, Anne Chen, Matt Haughey, Amy Kapczynski, David Krinsky, Jonathon Penney, Chris Riley, Henry Smith, Jessamyn West, and Steven Wu. I presented earlier versions of this essay at the Commons Theory Workshop for Young Scholars (Max Planck Institute for the Study of Collective Goods), the 2007 IP Scholars conference, the 2007 Telecommunications Policy Research Conference, and the December 2009 Symposium at Fordham Law School on David Post’s and Jonathan Zittrain’s books. -

Internet... the Final Frontier. an Ethnographic Account. Exploring the Cultural Space of the Net from the Inside. Mit CD-Rom
Schriftenreihe der Abteilung "Organisation und Technikgenese" des Forschungsschwerpunktes Technik-Arbeit-Umwelt am Wissenschaftszentrum Berlin für Sozialforschung FS II 2000- Internet… The Final Frontier: An Ethnographic Account Exploring the cultural space of the Net from the inside Sabine Helmers, Ute Hoffmann & Jeanette Hofmann Projektgruppe Kulturraum Internet http://duplox.wz-berlin.de Institute for Social Sciences Technical University Berlin and Social Science Research Center Berlin (WZB) Reichpietschufer 50, D-10785 Berlin Telefon (030) 25491-0, Fax (030) 25491-684 Abstract The research project "The Internet as a space for interaction", which completed its mission in Autumn 1998, studied the constitutive features of network culture and network organisation. Special emphasis was given to the dynamic interplay of technical and social conventions regarding both the Net's organisation as well as its change. The ethnographic perspective chosen studied the Internet from the inside. Research concentrated upon three fields of study: the hegemonial operating technology of net nodes (UNIX) the network's basic transmission technology (the Internet Protocol IP) and a popular communication service (Usenet). The project's final report includes the results of the three branches explored. Drawing upon the development in the three fields it is shown that changes that come about on the Net are neither anarchic nor arbitrary. Instead, the decentrally organised Internet is based upon technically and organisationally distributed forms of coordination -

Internet... the Final Frontier. Eine Ethnographie. Schlußbericht Des Projekts 'Interaktionsraum Internet. Netzkultur Und Ne
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Research Papers in Economics econstor www.econstor.eu Der Open-Access-Publikationsserver der ZBW – Leibniz-Informationszentrum Wirtschaft The Open Access Publication Server of the ZBW – Leibniz Information Centre for Economics Helmers, Sabine; Hoffmann, Ute; Hofmann, Jeanette Working Paper Internet... the final frontier: Eine Ethnographie. Schlußbericht des Projekts Interaktionsraum Internet. Netzkultur und Netzwerkorganisation Schriftenreihe der Abteilung Organisation und Technikgenese des Forschungsschwerpunktes Technik-Arbeit-Umwelt am Wissenschaftszentrum Berlin für Sozialforschung, No. FS II 98-112 Provided in cooperation with: Wissenschaftszentrum Berlin für Sozialforschung (WZB) Suggested citation: Helmers, Sabine; Hoffmann, Ute; Hofmann, Jeanette (1998) : Internet... the final frontier: Eine Ethnographie. Schlußbericht des Projekts Interaktionsraum Internet. Netzkultur und Netzwerkorganisation, Schriftenreihe der Abteilung Organisation und Technikgenese des Forschungsschwerpunktes Technik-Arbeit- Umwelt am Wissenschaftszentrum Berlin für Sozialforschung, No. FS II 98-112, http:// hdl.handle.net/10419/49813 Nutzungsbedingungen: Terms of use: Die ZBW räumt Ihnen als Nutzerin/Nutzer das unentgeltliche, The ZBW grants you, the user, the non-exclusive right to use räumlich unbeschränkte und zeitlich auf die Dauer des Schutzrechts the selected work free of charge, territorially unrestricted and beschränkte einfache Recht ein, das ausgewählte Werk im Rahmen within the time limit of the term of the property rights according der unter to the terms specified at → http://www.econstor.eu/dspace/Nutzungsbedingungen → http://www.econstor.eu/dspace/Nutzungsbedingungen nachzulesenden vollständigen Nutzungsbedingungen zu By the first use of the selected work the user agrees and vervielfältigen, mit denen die Nutzerin/der Nutzer sich durch die declares to comply with these terms of use. -

Abkürzungs-Liste ABKLEX
Abkürzungs-Liste ABKLEX (Informatik, Telekommunikation) W. Alex 1. Juli 2021 Karlsruhe Copyright W. Alex, Karlsruhe, 1994 – 2018. Die Liste darf unentgeltlich benutzt und weitergegeben werden. The list may be used or copied free of any charge. Original Point of Distribution: http://www.abklex.de/abklex/ An authorized Czechian version is published on: http://www.sochorek.cz/archiv/slovniky/abklex.htm Author’s Email address: [email protected] 2 Kapitel 1 Abkürzungen Gehen wir von 30 Zeichen aus, aus denen Abkürzungen gebildet werden, und nehmen wir eine größte Länge von 5 Zeichen an, so lassen sich 25.137.930 verschiedene Abkür- zungen bilden (Kombinationen mit Wiederholung und Berücksichtigung der Reihenfol- ge). Es folgt eine Auswahl von rund 16000 Abkürzungen aus den Bereichen Informatik und Telekommunikation. Die Abkürzungen werden hier durchgehend groß geschrieben, Akzente, Bindestriche und dergleichen wurden weggelassen. Einige Abkürzungen sind geschützte Namen; diese sind nicht gekennzeichnet. Die Liste beschreibt nur den Ge- brauch, sie legt nicht eine Definition fest. 100GE 100 GBit/s Ethernet 16CIF 16 times Common Intermediate Format (Picture Format) 16QAM 16-state Quadrature Amplitude Modulation 1GFC 1 Gigabaud Fiber Channel (2, 4, 8, 10, 20GFC) 1GL 1st Generation Language (Maschinencode) 1TBS One True Brace Style (C) 1TR6 (ISDN-Protokoll D-Kanal, national) 247 24/7: 24 hours per day, 7 days per week 2D 2-dimensional 2FA Zwei-Faktor-Authentifizierung 2GL 2nd Generation Language (Assembler) 2L8 Too Late (Slang) 2MS Strukturierte -

Jargon File, Version 4.0.0, 24 Jul 1996
JARGON FILE, VERSION 4.0.0, 24 JUL 1996 This is the Jargon File, a comprehensive compendium of hacker slang illuminating many aspects of hackish tradition, folklore, and humor. This document (the Jargon File) is in the public domain, to be freely used, shared, and modified. There are (by intention) no legal restraints on what you can do with it, but there are traditions about its proper use to which many hackers are quite strongly attached. Please extend the courtesy of proper citation when you quote the File, ideally with a version number, as it will change and grow over time. (Examples of appropriate citation form: "Jargon File 4.0.0" or "The on-line hacker Jargon File, version 4.0.0, 24 JUL 1996".) The Jargon File is a common heritage of the hacker culture. Over the years a number of individuals have volunteered considerable time to maintaining the File and been recognized by the net at large as editors of it. Editorial responsibilities include: to collate contributions and suggestions from others; to seek out corroborating information; to cross-reference related entries; to keep the file in a consistent format; and to announce and distribute updated versions periodically. Current volunteer editors include: Eric Raymond [email protected] Although there is no requirement that you do so, it is considered good form to check with an editor before quoting the File in a published work or commercial product. We may have additional information that would be helpful to you and can assist you in framing your quote to reflect not only the letter of the File but its spirit as well. -

Handling Information Overload on Usenet
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by NORA - Norwegian Open Research Archives UNIVERSITY OF OSLO Department of Informatics Handling Information Overload on Usenet Advanced Caching Methods for News Jan Ingvoldstad Cand Scient Thesis 4th August 2001 Abstract Usenet is the name of a world wide network of servers for group communica- tion between people. From 1979 and onwards, it has seen a near exponential growth in the amount of data transported, which has been a strain on band- width and storage. There has been a wide range of academic research with focus on the WWW, but Usenet has been neglected. Instead, Usenet’s evolu- tion has been dominated by practical solutions. This thesis describes the history of Usenet in a growth perspective, and introduces methods for collection and analysis of statistical data for testing the usefulness of various caching strategies. A set of different caching strategies are proposed and examined in light of bandwidth and storage demands as well as user perceived performance. I have shown that advanced caching methods for news offers relief for reading servers’ storage and bandwidth capacity by exploiting usage patterns for fetching or prefetching articles the users may want to read, but it will not solve the problem of near exponential growth nor the problems of Usenet’s backbone peers. Preface When I first started my studies at the University in Oslo in the autumn of 1991, I thought I was going to be a mathematician, and followed my first class in university level mathematics with vigor. -

Feminist Counter-Publicity in the Digital Age
Strange Spaces & Stranger Sensibilities: Feminist Counter-Publicity in the Digital Age by Bonnie Marilyn Washick A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (Political Science) in the University of Michigan 2016 Doctoral Committee: Professor Elizabeth R. Wingrove (Chair) Assistant Professor André L. Brock Professor Lisa J. Disch Professor Don Herzog Associate Professor Mika LaVaque-Manty © Bonnie Marilyn Washick 2016 ACKNOWLEDGEMENTS In undertaking this project, it often seemed that writing was a brutal thing. There’s always more that could be said and, one suspects, more that is worth exploring before committing words to the page. What a pleasure, then, to write with such blistering certainty: I could not have done this without the guidance, advocacy, and support of many people. A thousand thanks are owed; I am grateful for the space to pay some small portion of that debt. I must begin by thanking my committee: Lisa Disch, André Brock, Don Herzog, Mika LaVaque-Manty, and my Dissertation Chair, Elizabeth Wingrove. I am so appreciative of Lisa Disch’s incisive reading and productively challenging feedback. André’s in-depth knowledge and experience with the study of digital media was invaluable, and I’m certain will continue to be so. Many thanks to Don Herzog for his willingness to go over my work with a fine-tooth comb, or simply riff on a theme over coffee. I probably should have taken you up more on the former, but it was the latter that made me excited about work. Thanks to Mika LaVaque-Manty for serving as my teaching mentor in addition to serving on my committee, and modeling an enthusiastic, inquisitive, and student-like (in the best of ways) approach to innovation in the classroom. -

Online Identifiers in Everyday Life
© 2010 by Benjamin M. Gross. All rights reserved. ONLINE IDENTIFIERS IN EVERYDAY LIFE BY BENJAMIN M. GROSS DISSERTATION Submied in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Library and Information Science in the Graduate College of the University of Illinois at Urbana-Champaign, 2010 Urbana, Illinois Doctoral Commiee: Associate Professor Michael Twidale, Chair Professor Geof Bowker, University of Pisburgh Professor Chip Bruce Associate Professor Ann Bishop Abstract Identifiers are an essential component of online communication. Email addresses and instant messenger usernames are two of the most common online identi- fiers. is dissertation focuses on the ways that social, technical and policy fac- tors affect individual’s behavior with online identifiers. Research for this dissertation was completed in two parts, an interview-based study drawn from two populations and an examination of the infrastructure for managing identifiers in two large consumer services. e exploratory study ex- amines how individuals use online identifiers to segment and integrate aspects of their lives. e first population is drawn from employees of a financial ser- vice firm with substantial constraints on communication in the workplace. e second population is drawn from a design firm with minimal constraints on com- munication. e two populations provide the opportunity to explore the social, technical, and policy issues that arise from diverse communication needs, uses, strategies, and technologies. e examination of systems focuses on the infras- tructure that Google and Yahoo! provide for individuals to manage their iden- tifiers across multiple services, and the risks and benefits of employing single sign-on systems. -

The Internet Is a Semicommons
Fordham Law Review Volume 78 Issue 6 Article 5 2010 The Internet is a Semicommons James Grimmelmann Follow this and additional works at: https://ir.lawnet.fordham.edu/flr Part of the Law Commons Recommended Citation James Grimmelmann, The Internet is a Semicommons, 78 Fordham L. Rev. 2799 (2010). Available at: https://ir.lawnet.fordham.edu/flr/vol78/iss6/5 This Article is brought to you for free and open access by FLASH: The Fordham Law Archive of Scholarship and History. It has been accepted for inclusion in Fordham Law Review by an authorized editor of FLASH: The Fordham Law Archive of Scholarship and History. For more information, please contact [email protected]. The Internet is a Semicommons Cover Page Footnote Associate Professor, New York Law School. My thanks for their comments to Jack Balkin, Shyam Balganesh, Aislinn Black, Anne Chen, Matt Haughey, Amy Kapczynski, David Krinsky, Jonathon Penney, Chris Riley, Henry Smith, Jessamyn West, and Steven Wu. I presented earlier versions of this essay at the Commons Theory Workshop for Young Scholars (Max Planck Institute for the Study of Collective Goods), the 2007 IP Scholars conference, the 2007 Telecommunications Policy Research Conference, and the December 2009 Symposium at Fordham Law School on David Post’s and Jonathan Zittrain’s books. This essay may be freely reused under the terms of the Creative Commons Attribution 3.0 United States license, http://creativecommons.org/licenses/by/3.0/us/. This article is available in Fordham Law Review: https://ir.lawnet.fordham.edu/flr/vol78/iss6/5 THE INTERNET IS A SEMICOMMONS James Grimmelmann* I. -
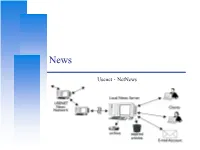
Usenet、Netnews
News Usenet、NetNews Computer Center, CS, NCTU Computer Center, News outline Introduction • History of netnews • History of newsgroups • News operations Transfer protocol • NNTP – Network News Transfer Protocol News softwares • Reader: tin • Server: INN – InterNet News 2 Introduction to News Computer Center, CS, NCTU Computer Center, Introduction to news (1) Usenet is a worldwide distributed Internet discussion system. • The initial Internet community • Like bulletin board systems (BBS) • Hybrid between e-mail and web forums • Absence of a central server and dedicated administrator The format and transmission of Usenet articles is similar to that of Internet e-mail messages. Usenet has significant cultural importance in the networked world • FAQ, spam. 4 Computer Center, CS, NCTU Computer Center, Introduction to news (2) Spamming: In 1994, advertisers began broadcasting messags to all newsgroups at once. Usenet has diminished in importance with respect to Internet forums, blogs, and mailing lists. Google made efforts to buy archive of Usenet newsgroups to attempt to create a complete one. Google has a web search interface and also allows newsgroup posting. • http://groups.google.com Usenet is a “must-have” resource? Year 1996 1997 1998 1999 2000 2001 2002 2003 Daily Vol. (GB) 4.5 9 12 26 82 181 257 492 Year 2004 2005 2006 2007 2008 2009 2010 2011 Daily Vol. (TB) 1 1.52 2.27 2.95 3.07 4.65 5.42 7.52 5 Computer Center, CS, NCTU Computer Center, Introduction to news (3) 6 Computer Center, CS, NCTU Computer Center, History (1) Origins