Psikologi-Dan-Internet.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Eszter Babarczy: Community Based Trust on the Internet
PTE BTK Nyelvtudományi Doktori Iskola Kommunikáció Doktori Program Babarczy Eszter: Community Based Trust on the Internet Doktori értekezés Témavezető: Horányi Özséb egyetemi tanár 2011. 1 Community-based trust on the internet Tartalom Introduction .................................................................................................................................................. 3 II. A very brief history of the internet ........................................................................................................... 9 Early Days ............................................................................................................................................... 11 Mainstream internet .............................................................................................................................. 12 The internet of social software .............................................................................................................. 15 III Early trust related problems and solutions ............................................................................................ 20 Trading .................................................................................................................................................... 20 Risks of and trust in content ....................................................................................................................... 22 UGC and its discontents: Wikipedia ...................................................................................................... -

The Internet Is a Semicommons
GRIMMELMANN_10_04_29_APPROVED_PAGINATED 4/29/2010 11:26 PM THE INTERNET IS A SEMICOMMONS James Grimmelmann* I. INTRODUCTION As my contribution to this Symposium on David Post’s In Search of Jefferson’s Moose1 and Jonathan Zittrain’s The Future of the Internet,2 I’d like to take up a question with which both books are obsessed: what makes the Internet work? Post’s answer is that the Internet is uniquely Jeffersonian; it embodies a civic ideal of bottom-up democracy3 and an intellectual ideal of generous curiosity.4 Zittrain’s answer is that the Internet is uniquely generative; it enables its users to experiment with new uses and then share their innovations with each other.5 Both books tell a story about how the combination of individual freedom and a cooperative ethos have driven the Internet’s astonishing growth. In that spirit, I’d like to suggest a third reason that the Internet works: it gets the property boundaries right. Specifically, I see the Internet as a particularly striking example of what property theorist Henry Smith has named a semicommons.6 It mixes private property in individual computers and network links with a commons in the communications that flow * Associate Professor, New York Law School. My thanks for their comments to Jack Balkin, Shyam Balganesh, Aislinn Black, Anne Chen, Matt Haughey, Amy Kapczynski, David Krinsky, Jonathon Penney, Chris Riley, Henry Smith, Jessamyn West, and Steven Wu. I presented earlier versions of this essay at the Commons Theory Workshop for Young Scholars (Max Planck Institute for the Study of Collective Goods), the 2007 IP Scholars conference, the 2007 Telecommunications Policy Research Conference, and the December 2009 Symposium at Fordham Law School on David Post’s and Jonathan Zittrain’s books. -

Internet... the Final Frontier. Eine Ethnographie. Schlußbericht Des Projekts 'Interaktionsraum Internet. Netzkultur Und Ne
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Research Papers in Economics econstor www.econstor.eu Der Open-Access-Publikationsserver der ZBW – Leibniz-Informationszentrum Wirtschaft The Open Access Publication Server of the ZBW – Leibniz Information Centre for Economics Helmers, Sabine; Hoffmann, Ute; Hofmann, Jeanette Working Paper Internet... the final frontier: Eine Ethnographie. Schlußbericht des Projekts Interaktionsraum Internet. Netzkultur und Netzwerkorganisation Schriftenreihe der Abteilung Organisation und Technikgenese des Forschungsschwerpunktes Technik-Arbeit-Umwelt am Wissenschaftszentrum Berlin für Sozialforschung, No. FS II 98-112 Provided in cooperation with: Wissenschaftszentrum Berlin für Sozialforschung (WZB) Suggested citation: Helmers, Sabine; Hoffmann, Ute; Hofmann, Jeanette (1998) : Internet... the final frontier: Eine Ethnographie. Schlußbericht des Projekts Interaktionsraum Internet. Netzkultur und Netzwerkorganisation, Schriftenreihe der Abteilung Organisation und Technikgenese des Forschungsschwerpunktes Technik-Arbeit- Umwelt am Wissenschaftszentrum Berlin für Sozialforschung, No. FS II 98-112, http:// hdl.handle.net/10419/49813 Nutzungsbedingungen: Terms of use: Die ZBW räumt Ihnen als Nutzerin/Nutzer das unentgeltliche, The ZBW grants you, the user, the non-exclusive right to use räumlich unbeschränkte und zeitlich auf die Dauer des Schutzrechts the selected work free of charge, territorially unrestricted and beschränkte einfache Recht ein, das ausgewählte Werk im Rahmen within the time limit of the term of the property rights according der unter to the terms specified at → http://www.econstor.eu/dspace/Nutzungsbedingungen → http://www.econstor.eu/dspace/Nutzungsbedingungen nachzulesenden vollständigen Nutzungsbedingungen zu By the first use of the selected work the user agrees and vervielfältigen, mit denen die Nutzerin/der Nutzer sich durch die declares to comply with these terms of use. -

Jargon File, Version 4.0.0, 24 Jul 1996
JARGON FILE, VERSION 4.0.0, 24 JUL 1996 This is the Jargon File, a comprehensive compendium of hacker slang illuminating many aspects of hackish tradition, folklore, and humor. This document (the Jargon File) is in the public domain, to be freely used, shared, and modified. There are (by intention) no legal restraints on what you can do with it, but there are traditions about its proper use to which many hackers are quite strongly attached. Please extend the courtesy of proper citation when you quote the File, ideally with a version number, as it will change and grow over time. (Examples of appropriate citation form: "Jargon File 4.0.0" or "The on-line hacker Jargon File, version 4.0.0, 24 JUL 1996".) The Jargon File is a common heritage of the hacker culture. Over the years a number of individuals have volunteered considerable time to maintaining the File and been recognized by the net at large as editors of it. Editorial responsibilities include: to collate contributions and suggestions from others; to seek out corroborating information; to cross-reference related entries; to keep the file in a consistent format; and to announce and distribute updated versions periodically. Current volunteer editors include: Eric Raymond [email protected] Although there is no requirement that you do so, it is considered good form to check with an editor before quoting the File in a published work or commercial product. We may have additional information that would be helpful to you and can assist you in framing your quote to reflect not only the letter of the File but its spirit as well. -

Handling Information Overload on Usenet
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by NORA - Norwegian Open Research Archives UNIVERSITY OF OSLO Department of Informatics Handling Information Overload on Usenet Advanced Caching Methods for News Jan Ingvoldstad Cand Scient Thesis 4th August 2001 Abstract Usenet is the name of a world wide network of servers for group communica- tion between people. From 1979 and onwards, it has seen a near exponential growth in the amount of data transported, which has been a strain on band- width and storage. There has been a wide range of academic research with focus on the WWW, but Usenet has been neglected. Instead, Usenet’s evolu- tion has been dominated by practical solutions. This thesis describes the history of Usenet in a growth perspective, and introduces methods for collection and analysis of statistical data for testing the usefulness of various caching strategies. A set of different caching strategies are proposed and examined in light of bandwidth and storage demands as well as user perceived performance. I have shown that advanced caching methods for news offers relief for reading servers’ storage and bandwidth capacity by exploiting usage patterns for fetching or prefetching articles the users may want to read, but it will not solve the problem of near exponential growth nor the problems of Usenet’s backbone peers. Preface When I first started my studies at the University in Oslo in the autumn of 1991, I thought I was going to be a mathematician, and followed my first class in university level mathematics with vigor. -

Feminist Counter-Publicity in the Digital Age
Strange Spaces & Stranger Sensibilities: Feminist Counter-Publicity in the Digital Age by Bonnie Marilyn Washick A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (Political Science) in the University of Michigan 2016 Doctoral Committee: Professor Elizabeth R. Wingrove (Chair) Assistant Professor André L. Brock Professor Lisa J. Disch Professor Don Herzog Associate Professor Mika LaVaque-Manty © Bonnie Marilyn Washick 2016 ACKNOWLEDGEMENTS In undertaking this project, it often seemed that writing was a brutal thing. There’s always more that could be said and, one suspects, more that is worth exploring before committing words to the page. What a pleasure, then, to write with such blistering certainty: I could not have done this without the guidance, advocacy, and support of many people. A thousand thanks are owed; I am grateful for the space to pay some small portion of that debt. I must begin by thanking my committee: Lisa Disch, André Brock, Don Herzog, Mika LaVaque-Manty, and my Dissertation Chair, Elizabeth Wingrove. I am so appreciative of Lisa Disch’s incisive reading and productively challenging feedback. André’s in-depth knowledge and experience with the study of digital media was invaluable, and I’m certain will continue to be so. Many thanks to Don Herzog for his willingness to go over my work with a fine-tooth comb, or simply riff on a theme over coffee. I probably should have taken you up more on the former, but it was the latter that made me excited about work. Thanks to Mika LaVaque-Manty for serving as my teaching mentor in addition to serving on my committee, and modeling an enthusiastic, inquisitive, and student-like (in the best of ways) approach to innovation in the classroom. -

Online Identifiers in Everyday Life
© 2010 by Benjamin M. Gross. All rights reserved. ONLINE IDENTIFIERS IN EVERYDAY LIFE BY BENJAMIN M. GROSS DISSERTATION Submied in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Library and Information Science in the Graduate College of the University of Illinois at Urbana-Champaign, 2010 Urbana, Illinois Doctoral Commiee: Associate Professor Michael Twidale, Chair Professor Geof Bowker, University of Pisburgh Professor Chip Bruce Associate Professor Ann Bishop Abstract Identifiers are an essential component of online communication. Email addresses and instant messenger usernames are two of the most common online identi- fiers. is dissertation focuses on the ways that social, technical and policy fac- tors affect individual’s behavior with online identifiers. Research for this dissertation was completed in two parts, an interview-based study drawn from two populations and an examination of the infrastructure for managing identifiers in two large consumer services. e exploratory study ex- amines how individuals use online identifiers to segment and integrate aspects of their lives. e first population is drawn from employees of a financial ser- vice firm with substantial constraints on communication in the workplace. e second population is drawn from a design firm with minimal constraints on com- munication. e two populations provide the opportunity to explore the social, technical, and policy issues that arise from diverse communication needs, uses, strategies, and technologies. e examination of systems focuses on the infras- tructure that Google and Yahoo! provide for individuals to manage their iden- tifiers across multiple services, and the risks and benefits of employing single sign-on systems. -

³5Hjxodwlqj´
29th November 2002 ,,,³5HJXODWLQJ´ $EXVH%XONHPDLO&U\SWRJUDSK\ 'HIDPDWLRQDQG(YHU\WKLQJHOVH WK-DQXDU\ 5LFKDUG&OD\WRQ These lecture notes were specially prepared for the Cambridge University Computer Science “Additional Topics” course, Michaelmas Term 2002. © Richard Clayton 2002 [email protected] Regulating rnc1 1 29th November 2002 2XWOLQH 7KHFODVVLFVHOIUHJXODWLRQDSSURDFK &KLOGSRUQRJUDSK\DQGRWKHUQDVW\WKLQJV 8QVROLFLWHGEXONHPDLO 6SDPRQ8VHQHW 5HJXODWLQJFU\SWRJUDSK\ 'DWDSUHVHUYDWLRQ :KDWDERXWQDWLRQDOERUGHUV" 'HIDPDWLRQ 7KH(&RPPHUFH'LUHFWLYH 29th November 2002 Regulating The slides give the broad outline of the lectures and the notes ensure that the details are properly recorded, lest they be skipped over on the day. However, it is at least arguable that it will be far more interesting to take notice of what I say off-the-cuff rather than relying on this document as an accurate rendition of what the lecture was really about! Also, please note that “IANAL” (I am not a lawyer). Consult a professional if you wish to receive accurate advice about the law! Regulating rnc1 2 29th November 2002 )XUWKHU5HDGLQJ (3ROLF\ ± 6HFXULW\(QJLQHHULQJ$QGHUVRQ ± &U\SWR6WHYHQ/HY\ ± KWWSZZZHIIRUJ ± KWWSZZZILSURUJ 1DVW\WKLQJV ± KWWSZZZLZIRUJXN ± KWWSZZZF\EHUULJKWVRUJ ± KWWSZZZILDZROGHPRQFRXN)$&EDFNKWP ³6SDP´ ± KWWSZZZFDXFHRUJ 29th November 2002 Regulating Since almost everything covered in this lecture has happened in the past six years it probably isn’t surprising to find very few books on the topic. However, almost all the original documents are still available online along with detailed records of the many discussions through which people came to understand the meaning of what was happening. Ross Anderson’s book covers slightly different areas than this lecture, reflecting in each case where we each had first hand experience. -

The Internet Is a Semicommons
Fordham Law Review Volume 78 Issue 6 Article 5 2010 The Internet is a Semicommons James Grimmelmann Follow this and additional works at: https://ir.lawnet.fordham.edu/flr Part of the Law Commons Recommended Citation James Grimmelmann, The Internet is a Semicommons, 78 Fordham L. Rev. 2799 (2010). Available at: https://ir.lawnet.fordham.edu/flr/vol78/iss6/5 This Article is brought to you for free and open access by FLASH: The Fordham Law Archive of Scholarship and History. It has been accepted for inclusion in Fordham Law Review by an authorized editor of FLASH: The Fordham Law Archive of Scholarship and History. For more information, please contact [email protected]. The Internet is a Semicommons Cover Page Footnote Associate Professor, New York Law School. My thanks for their comments to Jack Balkin, Shyam Balganesh, Aislinn Black, Anne Chen, Matt Haughey, Amy Kapczynski, David Krinsky, Jonathon Penney, Chris Riley, Henry Smith, Jessamyn West, and Steven Wu. I presented earlier versions of this essay at the Commons Theory Workshop for Young Scholars (Max Planck Institute for the Study of Collective Goods), the 2007 IP Scholars conference, the 2007 Telecommunications Policy Research Conference, and the December 2009 Symposium at Fordham Law School on David Post’s and Jonathan Zittrain’s books. This essay may be freely reused under the terms of the Creative Commons Attribution 3.0 United States license, http://creativecommons.org/licenses/by/3.0/us/. This article is available in Fordham Law Review: https://ir.lawnet.fordham.edu/flr/vol78/iss6/5 THE INTERNET IS A SEMICOMMONS James Grimmelmann* I. -
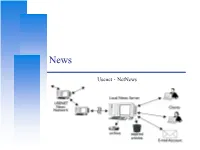
Usenet、Netnews
News Usenet、NetNews Computer Center, CS, NCTU Computer Center, News outline Introduction • History of netnews • History of newsgroups • News operations Transfer protocol • NNTP – Network News Transfer Protocol News softwares • Reader: tin • Server: INN – InterNet News 2 Introduction to News Computer Center, CS, NCTU Computer Center, Introduction to news (1) Usenet is a worldwide distributed Internet discussion system. • The initial Internet community • Like bulletin board systems (BBS) • Hybrid between e-mail and web forums • Absence of a central server and dedicated administrator The format and transmission of Usenet articles is similar to that of Internet e-mail messages. Usenet has significant cultural importance in the networked world • FAQ, spam. 4 Computer Center, CS, NCTU Computer Center, Introduction to news (2) Spamming: In 1994, advertisers began broadcasting messags to all newsgroups at once. Usenet has diminished in importance with respect to Internet forums, blogs, and mailing lists. Google made efforts to buy archive of Usenet newsgroups to attempt to create a complete one. Google has a web search interface and also allows newsgroup posting. • http://groups.google.com Usenet is a “must-have” resource? Year 1996 1997 1998 1999 2000 2001 2002 2003 Daily Vol. (GB) 4.5 9 12 26 82 181 257 492 Year 2004 2005 2006 2007 2008 2009 2010 2011 Daily Vol. (TB) 1 1.52 2.27 2.95 3.07 4.65 5.42 7.52 5 Computer Center, CS, NCTU Computer Center, Introduction to news (3) 6 Computer Center, CS, NCTU Computer Center, History (1) Origins -

United States Patent (19) 11 Patent Number: 5,845,265 Woolston (45) Date of Patent: Dec
USOO584,5265A United States Patent (19) 11 Patent Number: 5,845,265 Woolston (45) Date of Patent: Dec. 1, 1998 54 CONSIGNMENT NODES 5,206.803 4/1993 Vitagliano et al.. 5,235,680 8/1993 Bijnagte. 75 Inventor: Thomas G. Woolston, Arlington, Va. 5,237,500 8/1993 Perg et al. 5,239,462 8/1993 Jones et al.. 73 Assignee: MercFxchange, L.L.C., Alexandria, Va. 5,262,942 11/1993 Earle. 5,283,731 2/1994 Lalonde et al.. 5,285,383 2/1994 Lindsey et al.. 21 Appl. No.: 554,704 5,323,315 6/1994 Highbloom. 1-1. 5,451,998 9/1995 Hamrick. 22 Filed: Nov. 7, 1995 5,465.291 11/1995 Barrus et al.. Related U.S. Application Data OTHER PUBLICATIONS 63 Continuation-in-part of Ser. No. 427.820, Apr. 26, 1995. Whitmore, S. “Business on the Net: the New Gold Rush', 6 PC Week v12, n43, p. 106, Oct. 30, 1995. 51) Int. Cl. ...................................................... G06F 17/60 Gordon, M. “Auctions Become High Tech', Dealer Busi 52) U.S. Cl. ................................................. 705/37; 705/27 neSS, v29, n7, p. 21, Mar. 1995. 58 Field of Search ..................................... 395/226, 237, Goulde, M., “Sun Microsystems Bringing Interactive Tech 395/227, 235, 236, 239; 235/383,381; nology to the WWW,” Open Information Systems, 10:3 p. 705/26, 27, 35, 36, 37, 39 29, Mar. 1995. 56) References Cited Primary Examiner Robert A. Weinhardt U.S. PATENT DOCUMENTS Attorney, Agent, or Firm Thomas G. Woolston 57 ABSTRACT 4,270.042 5/1981 Case ........................................ 235/379 4,346,442 8/1982 Musmanno. -

The UNIX- HATERS Handbook
The UNIX- HATERS Handbook The UNIX- HATERS Handbook “Two of the most famous products of Berkeley are LSD and Unix. I don’t think that is a coincidence.” Edited by Simson Garfinkel, Daniel Weise, and Steven Strassmann ® PROGRAMMERS IDG Illustrations by John Klossner BOOKS PRESS iv IDG Books Worldwide, Inc. An International Data Group Company San Mateo, California • Indianapolis, Indiana • Boston, Massachusetts The UNIX-HATERS Handbook Published by IDG Books Worldwide, Inc. An International Data Group Company 155 Bovet Road, Suite 310 San Mateo, CA 94402 Copyright 1994 by IDG Books Worldwide. All rights reserved. No part of this book (including interior design, cover design, and illustrations) may be reproduced or transmitted in any form, by any means, (electronic, photocopying, recording, or otherwise) without the prior written permission of the publisher. ISBN 1-56884-203-1 Printed in the United States of America First Printing, May, 1994 10 9 8 7 6 5 4 3 2 1 Distributed in the United States by IDG Books Worldwide, Inc. Distributed in Canada by Macmillan of Canada, a Division of Canada Publishing Corporation; by Computer and Technical Books in Miami, Florida, for South America and the Caribbean; by Longman Singapore in Singapore, Malaysia, Thailand, and Korea; by Toppan Co. Ltd. in Japan; by Asia Computerworld in Hong Kong; by Woodslane Pty. Ltd. in Australia and New Zealand; and by Transword Publishers Ltd. in the U.K. and Europe. For information on where to purchase IDG’s books outside the U.S., contact Christina Turner at 415-312-0633. For information on translations, contact Marc Jeffrey Mikulich, Foreign Rights Manager, at IDG Books Worldwide; FAX number: 415-358-1260.