Intel 8086 MICROPROCESSOR ARCHITECTURE
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Over View of Microprocessor 8085 and Its Application
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE) e-ISSN: 2278-2834,p- ISSN: 2278-8735.Volume 10, Issue 6, Ver. II (Nov - Dec .2015), PP 09-14 www.iosrjournals.org Over view of Microprocessor 8085 and its application Kimasha Borah Assistant Professor, Centre for Computer Studies Centre for Computer Studies, Dibrugarh University, Dibrugarh, Assam, India Abstract: Microprocessor is a program controlled semiconductor device (IC), which fetches, decode and executes instructions. It is versatile in application and is flexible to some extent. Nowadays, modern microprocessors can perform extremely sophisticated operations in areas such as meteorology, aviation, nuclear physics and engineering, and take up much less space as well as delivering superior performance Here is a brief review of microprocessor and its various application Key words: Semi Conductor, Integrated Circuits, CPU, NMOS ,PMOS, VLSI I. Introduction: Microprocessor is derived from two words micro and processor. Micro means small, tiny and processor means which processes something. It is a single Very Large Scale of Integration (VLSI) chip that incorporates all functions of central processing unit (CPU) fabricated on a single Integrated Circuits (ICs) (1).Some other units like caches, pipelining, floating point processing arithmetic and superscaling units are additionally present in the microprocessor and that results in increasing speed of operation.8085,8086,8088 are some examples of microprocessors(2). The technology used for microprocessor is N type metal oxide semiconductor(NMOS)(3). Basic operations of microprocessor are fetching instructions from memory ,decoding and executing them ie it takes data or operand from input device, perform arithmetic and logical operations and store results in required location or send result to output devices(1).Word size identifies the microprocessor.E.g. -

Appendix D an Alternative to RISC: the Intel 80X86
D.1 Introduction D-2 D.2 80x86 Registers and Data Addressing Modes D-3 D.3 80x86 Integer Operations D-6 D.4 80x86 Floating-Point Operations D-10 D.5 80x86 Instruction Encoding D-12 D.6 Putting It All Together: Measurements of Instruction Set Usage D-14 D.7 Concluding Remarks D-20 D.8 Historical Perspective and References D-21 D An Alternative to RISC: The Intel 80x86 The x86 isn’t all that complex—it just doesn’t make a lot of sense. Mike Johnson Leader of 80x86 Design at AMD, Microprocessor Report (1994) © 2003 Elsevier Science (USA). All rights reserved. D-2 I Appendix D An Alternative to RISC: The Intel 80x86 D.1 Introduction MIPS was the vision of a single architect. The pieces of this architecture fit nicely together and the whole architecture can be described succinctly. Such is not the case of the 80x86: It is the product of several independent groups who evolved the architecture over 20 years, adding new features to the original instruction set as you might add clothing to a packed bag. Here are important 80x86 milestones: I 1978—The Intel 8086 architecture was announced as an assembly language– compatible extension of the then-successful Intel 8080, an 8-bit microproces- sor. The 8086 is a 16-bit architecture, with all internal registers 16 bits wide. Whereas the 8080 was a straightforward accumulator machine, the 8086 extended the architecture with additional registers. Because nearly every reg- ister has a dedicated use, the 8086 falls somewhere between an accumulator machine and a general-purpose register machine, and can fairly be called an extended accumulator machine. -

Class-Action Lawsuit
Case 3:20-cv-00863-SI Document 1 Filed 05/29/20 Page 1 of 279 Steve D. Larson, OSB No. 863540 Email: [email protected] Jennifer S. Wagner, OSB No. 024470 Email: [email protected] STOLL STOLL BERNE LOKTING & SHLACHTER P.C. 209 SW Oak Street, Suite 500 Portland, Oregon 97204 Telephone: (503) 227-1600 Attorneys for Plaintiffs [Additional Counsel Listed on Signature Page.] UNITED STATES DISTRICT COURT DISTRICT OF OREGON PORTLAND DIVISION BLUE PEAK HOSTING, LLC, PAMELA Case No. GREEN, TITI RICAFORT, MARGARITE SIMPSON, and MICHAEL NELSON, on behalf of CLASS ACTION ALLEGATION themselves and all others similarly situated, COMPLAINT Plaintiffs, DEMAND FOR JURY TRIAL v. INTEL CORPORATION, a Delaware corporation, Defendant. CLASS ACTION ALLEGATION COMPLAINT Case 3:20-cv-00863-SI Document 1 Filed 05/29/20 Page 2 of 279 Plaintiffs Blue Peak Hosting, LLC, Pamela Green, Titi Ricafort, Margarite Sampson, and Michael Nelson, individually and on behalf of the members of the Class defined below, allege the following against Defendant Intel Corporation (“Intel” or “the Company”), based upon personal knowledge with respect to themselves and on information and belief derived from, among other things, the investigation of counsel and review of public documents as to all other matters. INTRODUCTION 1. Despite Intel’s intentional concealment of specific design choices that it long knew rendered its central processing units (“CPUs” or “processors”) unsecure, it was only in January 2018 that it was first revealed to the public that Intel’s CPUs have significant security vulnerabilities that gave unauthorized program instructions access to protected data. 2. A CPU is the “brain” in every computer and mobile device and processes all of the essential applications, including the handling of confidential information such as passwords and encryption keys. -

Micro-Circuits for High Energy Physics*
MICRO-CIRCUITS FOR HIGH ENERGY PHYSICS* Paul F. Kunz Stanford Linear Accelerator Center Stanford University, Stanford, California, U.S.A. ABSTRACT Microprogramming is an inherently elegant method for implementing many digital systems. It is a mixture of hardware and software techniques with the logic subsystems controlled by "instructions" stored Figure 1: Basic TTL Gate in a memory. In the past, designing microprogrammed systems was difficult, tedious, and expensive because the available components were capable of only limited number of functions. Today, however, large blocks of microprogrammed systems have been incorporated into a A input B input C output single I.e., thus microprogramming has become a simple, practical method. false false true false true true true false true true true false 1. INTRODUCTION 1.1 BRIEF HISTORY OF MICROCIRCUITS Figure 2: Truth Table for NAND Gate. The first question which arises when one talks about microcircuits is: What is a microcircuit? The answer is simple: a complete circuit within a single integrated-circuit (I.e.) package or chip. The next question one might ask is: What circuits are available? The answer to this question is also simple: it depends. It depends on the economics of the circuit for the semiconductor manufacturer, which depends on the technology he uses, which in turn changes as a function of time. Thus to understand Figure 3: Logical NOT Circuit. what microcircuits are available today and what makes them different from those of yesterday it is interesting to look into the economics of producing microcircuits. The basic element in a logic circuit is a gate, which is a circuit with a number of inputs and one output and it performs a basic logical function such as AND, OR, or NOT. -

A Simulator for the Intel 8086 Microprocessor
Rochester Institute of Technology RIT Scholar Works Theses 1988 A Simulator for the Intel 8086 microprocessor William A. Chapman Follow this and additional works at: https://scholarworks.rit.edu/theses Recommended Citation Chapman, William A., "A Simulator for the Intel 8086 microprocessor" (1988). Thesis. Rochester Institute of Technology. Accessed from This Thesis is brought to you for free and open access by RIT Scholar Works. It has been accepted for inclusion in Theses by an authorized administrator of RIT Scholar Works. For more information, please contact [email protected]. A SIMULATOR FOR THE INTEL 8086 MICROPROCESSOR by William A. Chapman A Thesis Submitted in Partial Fulfillment of the Requirements for the Degree of Master of Science in Electrical Engineering Approved by: Professor Ken Hsu ':"(':":T~h":"e~sJ.';":·S=--=-A-d'=""v-i:-s-o-r-)------- Professor James R. Schueckler Professor _~~ _ Professor __~__:--:~-=- _ (Department Head) DEPARTMENT OF ELECTRICAL ENGINEERING COLLEGE OF ENGINEERING ROCHESTER INSTITUTE OF TECHNOLOGY ROCHESTER, NEW YORK MAY, 1988 Abstract This project was originally suggested by J. Schueckler as an aid to teaching students the Intel 8086 Assembly Language. The need for such a tool becomes apparent when one considers the expense of providing students with dedicated hardware that rapidly becomes obsolete, but a Simulator which could be easily updated and runs on a general purpose or timesharing computer system would be accessible to many students for a fraction of the cost. The intended use of the Simulator therefore dictated that it precisely model the hardware, be available on a multiuser system and run as efficiently as possible. -

8086 16-Bit Hmos Microprocessor 8086/8086-2/8086-1
8086 16-BIT HMOS MICROPROCESSOR 8086/8086-2/8086-1 Y Direct Addressing Capability 1 MByte Y Range of Clock Rates: of Memory 5 MHz for 8086, 8 MHz for 8086-2, Y Architecture Designed for Powerful Assembly Language and Efficient High 10 MHz for 8086-1 Level Languages Y MULTIBUS System Compatible Interface Y 14 Word,by 16-Bit Register Set with Symmetrical Operations Y Available in EXPRESS –Standard Temperature Range Y 24 Operand Addressing Modes –Extended Temperature Range Y Bit,Byte,Word,and Block Operations Y Available in 40-Lead Cerdip and Plastic Y 8 and 16-Bit Signed and Unsigned Package Arithmetic in Binary or Decimal (See Packaging Spec.Order ›231369) Including Multiply and Divide The Intel 8086 high performance 16-bit CPU is available in three clock rates:5,8 and 10 MHz.The CPU is implemented in N-Channel,depletion load,silicon gate technology (HMOS-III),and packaged in a 40-pin CERDIP or plastic package.The 8086 operates in both single processor and multiple processor configurations to achieve high performance levels. 231455–2 40 Lead Figure 2.8086 Pin Configuration Figure 1.8086 CPU Block Diagram 231455–1 September 1990 Order Number:231455-005 8086 Table 1.Pin Description The following pin function descriptions are for 8086 systems in either minimum or maximum mode.The ‘‘Local Bus’’ in these descriptions is the direct multiplexed bus interface connection to the 8086 (without regard to additional bus buffers). Symbol Pin No.Type Name and Function AD15–AD0 2–16,39 I/O ADDRESS DATA BUS: These lines constitute the time multiplexed memory/IO address (T1),and data (T2,T3,TW,T4) bus.A0 is analogous to BHE for the lower byte of the data bus,pins D7–D0.It is LOW during T1 when a byte is to be transferred on the lower portion of the bus in memory or I/O operations.Eight-bit oriented devices tied to the lower half would normally use A0 to condition chip select functions.(See BHE.) These lines are active HIGH and float to 3-state OFF during interrupt acknowledge and local bus ‘‘hold acknowledge’’. -

Computer Architecture Out-Of-Order Execution
Computer Architecture Out-of-order Execution By Yoav Etsion With acknowledgement to Dan Tsafrir, Avi Mendelson, Lihu Rappoport, and Adi Yoaz 1 Computer Architecture 2013– Out-of-Order Execution The need for speed: Superscalar • Remember our goal: minimize CPU Time CPU Time = duration of clock cycle × CPI × IC • So far we have learned that in order to Minimize clock cycle ⇒ add more pipe stages Minimize CPI ⇒ utilize pipeline Minimize IC ⇒ change/improve the architecture • Why not make the pipeline deeper and deeper? Beyond some point, adding more pipe stages doesn’t help, because Control/data hazards increase, and become costlier • (Recall that in a pipelined CPU, CPI=1 only w/o hazards) • So what can we do next? Reduce the CPI by utilizing ILP (instruction level parallelism) We will need to duplicate HW for this purpose… 2 Computer Architecture 2013– Out-of-Order Execution A simple superscalar CPU • Duplicates the pipeline to accommodate ILP (IPC > 1) ILP=instruction-level parallelism • Note that duplicating HW in just one pipe stage doesn’t help e.g., when having 2 ALUs, the bottleneck moves to other stages IF ID EXE MEM WB • Conclusion: Getting IPC > 1 requires to fetch/decode/exe/retire >1 instruction per clock: IF ID EXE MEM WB 3 Computer Architecture 2013– Out-of-Order Execution Example: Pentium Processor • Pentium fetches & decodes 2 instructions per cycle • Before register file read, decide on pairing Can the two instructions be executed in parallel? (yes/no) u-pipe IF ID v-pipe • Pairing decision is based… On data -

Advanced Architecture Intel Microprocessor History
Advanced Architecture Intel microprocessor history Computer Organization and Assembly Languages Yung-Yu Chuang with slides by S. Dandamudi, Peng-Sheng Chen, Kip Irvine, Robert Sedgwick and Kevin Wayne Early Intel microprocessors The IBM-AT • Intel 8080 (1972) • Intel 80286 (1982) – 64K addressable RAM – 16 MB addressable RAM – 8-bit registers – Protected memory – CP/M operating system – several times faster than 8086 – 5,6,8,10 MHz – introduced IDE bus architecture – 29K transistors – 80287 floating point unit • Intel 8086/8088 (1978) my first computer (1986) – Up to 20MHz – IBM-PC used 8088 – 134K transistors – 1 MB addressable RAM –16-bit registers – 16-bit data bus (8-bit for 8088) – separate floating-point unit (8087) – used in low-cost microcontrollers now 3 4 Intel IA-32 Family Intel P6 Family • Intel386 (1985) • Pentium Pro (1995) – 4 GB addressable RAM – advanced optimization techniques in microcode –32-bit registers – More pipeline stages – On-board L2 cache – paging (virtual memory) • Pentium II (1997) – Up to 33MHz – MMX (multimedia) instruction set • Intel486 (1989) – Up to 450MHz – instruction pipelining • Pentium III (1999) – Integrated FPU – SIMD (streaming extensions) instructions (SSE) – 8K cache – Up to 1+GHz • Pentium (1993) • Pentium 4 (2000) – Superscalar (two parallel pipelines) – NetBurst micro-architecture, tuned for multimedia – 3.8+GHz • Pentium D (2005, Dual core) 5 6 IA32 Processors ARM history • Totally Dominate Computer Market • 1983 developed by Acorn computers • Evolutionary Design – To replace 6502 in -

Parallel Computing
Lecture 1: Computer Organization 1 Outline • Overview of parallel computing • Overview of computer organization – Intel 8086 architecture • Implicit parallelism • von Neumann bottleneck • Cache memory – Writing cache-friendly code 2 Why parallel computing • Solving an × linear system Ax=b by using Gaussian elimination takes ≈ flops. 1 • On Core i7 975 @ 4.0 GHz,3 which is capable of about 3 60-70 Gigaflops flops time 1000 3.3×108 0.006 seconds 1000000 3.3×1017 57.9 days 3 What is parallel computing? • Serial computing • Parallel computing https://computing.llnl.gov/tutorials/parallel_comp 4 Milestones in Computer Architecture • Analytic engine (mechanical device), 1833 – Forerunner of modern digital computer, Charles Babbage (1792-1871) at University of Cambridge • Electronic Numerical Integrator and Computer (ENIAC), 1946 – Presper Eckert and John Mauchly at the University of Pennsylvania – The first, completely electronic, operational, general-purpose analytical calculator. 30 tons, 72 square meters, 200KW. – Read in 120 cards per minute, Addition took 200µs, Division took 6 ms. • IAS machine, 1952 – John von Neumann at Princeton’s Institute of Advanced Studies (IAS) – Program could be represented in digit form in the computer memory, along with data. Arithmetic could be implemented using binary numbers – Most current machines use this design • Transistors was invented at Bell Labs in 1948 by J. Bardeen, W. Brattain and W. Shockley. • PDP-1, 1960, DEC – First minicomputer (transistorized computer) • PDP-8, 1965, DEC – A single bus -

Programmable Digital Microcircuits - a Survey with Examples of Use
- 237 - PROGRAMMABLE DIGITAL MICROCIRCUITS - A SURVEY WITH EXAMPLES OF USE C. Verkerk CERN, Geneva, Switzerland 1. Introduction For most readers the title of these lecture notes will evoke microprocessors. The fixed instruction set microprocessors are however not the only programmable digital mi• crocircuits and, although a number of pages will be dedicated to them, the aim of these notes is also to draw attention to other useful microcircuits. A complete survey of programmable circuits would fill several books and a selection had therefore to be made. The choice has rather been to treat a variety of devices than to give an in- depth treatment of a particular circuit. The selected devices have all found useful ap• plications in high-energy physics, or hold promise for future use. The microprocessor is very young : just over eleven years. An advertisement, an• nouncing a new era of integrated electronics, and which appeared in the November 15, 1971 issue of Electronics News, is generally considered its birth-certificate. The adver• tisement was for the Intel 4004 and its three support chips. The history leading to this announcement merits to be recalled. Intel, then a very young company, was working on the design of a chip-set for a high-performance calculator, for and in collaboration with a Japanese firm, Busicom. One of the Intel engineers found the Busicom design of 9 different chips too complicated and tried to find a more general and programmable solu• tion. His design, the 4004 microprocessor, was finally adapted by Busicom, and after further négociation, Intel acquired marketing rights for its new invention. -

H&P Chapter 1 Supplement: but First, What Is Security? Assets
H&P Chapter 1 Supplement: Introduction to Security for Computer Architecture Students https://doi.org/10.7916/d8-7r78-2635 Adam Hastings Mohammed Tarek Simha Sethumadhavan October 1, 2019 For decades, the role of the computer architect has been to design systems that meet requirements, defined primarily by speed, area, and energy efficiency. However, as humans become more and more reliant on computers, it becomes increasingly obvious that our specifications have failed us on one key design requirement – Security, – as evidenced by nearly weeklynews of high-profile security breaches. In the face of such damaging consequences, it becomes clear that the security of our technology must no longer be relegated as an afterthought, but must be a first-order design requirement, from the very beginning—security must be “built-in” rather than “bolted on”, so to speak. In particular, it becomes important, even necessary, for security to be built into the lowest levels of the computing stack. It is for this reason that security must become a fundamental part of computer architecture, and must be included in any serious study of the subject. But First, What is Security? In its broadest sense, security is about protecting assets. An asset is anything of value that is worth protecting, e.g. anything from the valuables in a bank vault to a secret message shared between friends to classified government information to objects of personal sentimental value. As long as an asset is valued, its owners should work to secure it. For an asset to be secure, security professionals generally think of the asset as maintaining three essential properties: • Confidentiality—Is the asset only accessible to those authorized to access it? In computer systems, maintaining confidentiality means controlling who can read some piece of information. -
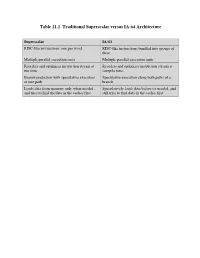
Table 21.1 Traditional Superscalar Versus IA-64 Architecture
Table 21.1 Traditional Superscalar versus IA-64 Architecture Superscalar IA-64 RISC-like instructions, one per word RISC-like instructions bundled into groups of three Multiple parallel execution units Multiple parallel execution units Reorders and optimizes instruction stream at Reorders and optimizes instruction stream at run time compile time Branch prediction with speculative execution Speculative execution along both paths of a of one path branch Loads data from memory only when needed, Speculatively loads data before its needed, and and tries to find the data in the caches first still tries to find data in the caches first Table 21.2 Relationship Between Instruction Type and Execution Unit Type Instruction Type Description Execution Unit Type A Integer ALU I-unit or M-unit I Non-ALU integer I-unit M Memory M-unit F Floating-point F-unit B Branch B-unit X Extended I-unit/B-unit Table 21.3 Template Field Encoding and Instruction Set Mapping Template Slot 0 Slot 1 Slot 2 00 M-unit I-unit I-unit 01 M-unit I-unit I-unit 02 M-unit I-unit I-unit 03 M-unit I-unit I-unit 04 M-unit L-unit X-unit 05 M-unit L-unit X-unit 08 M-unit M-unit I-unit 09 M-unit M-unit I-unit 0A M-unit M-unit I-unit 0B M-unit M-unit I-unit 0C M-unit F-unit I-unit 0D M-unit F-unit I-unit 0E M-unit M-unit F-unit 0F M-unit M-unit F-unit 10 M-unit I-unit B-unit 11 M-unit I-unit B-unit 12 M-unit B-unit B-unit 13 M-unit B-unit B-unit 16 B-unit B-unit B-unit 17 B-unit B-unit B-unit 18 M-unit M-unit B-unit 19 M-unit M-unit B-unit 1C M-unit F-unit B-unit 1D M-unit F-unit B-unit Table 21.5 IA-64 Application Registers Kernel registers (KR0-7) Convey information from the operating system to the application.