Virtualization As an Approach in the Development of IT System Implementation Process
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

THINC: a Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices
THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2011 c 2011 Ricardo A. Baratto This work may be used in accordance with Creative Commons, Attribution-NonCommercial-NoDerivs License. For more information about that license, see http://creativecommons.org/licenses/by-nc-nd/3.0/. For other uses, please contact the author. ABSTRACT THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto THINC is a new virtual and remote display architecture for desktop computing. It has been designed to address the limitations and performance shortcomings of existing remote display technology, and to provide a building block around which novel desktop architectures can be built. THINC is architected around the notion of a virtual display device driver, a software-only component that behaves like a traditional device driver, but instead of managing specific hardware, enables desktop input and output to be intercepted, manipulated, and redirected at will. On top of this architecture, THINC introduces a simple, low-level, device-independent representation of display changes, and a number of novel optimizations and techniques to perform efficient interception and redirection of display output. This dissertation presents the design and implementation of THINC. It also intro- duces a number of novel systems which build upon THINC's architecture to provide new and improved desktop computing services. The contributions of this dissertation are as follows: • A high performance remote display system for LAN and WAN environments. -

The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
The Application Usage and Risk Report An Analysis of End User Application Trends in the Enterprise 8th Edition, December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 94089 www.paloaltonetworks.com Table of Contents Executive Summary ........................................................................................................ 3 Demographics ............................................................................................................................................. 4 Social Networking Use Becomes More Active ................................................................ 5 Facebook Applications Bandwidth Consumption Triples .......................................................................... 5 Twitter Bandwidth Consumption Increases 7-Fold ................................................................................... 6 Some Perspective On Bandwidth Consumption .................................................................................... 7 Managing the Risks .................................................................................................................................... 7 Browser-based Filesharing: Work vs. Entertainment .................................................... 8 Infrastructure- or Productivity-Oriented Browser-based Filesharing ..................................................... 9 Entertainment Oriented Browser-based Filesharing .............................................................................. 10 Comparing Frequency and Volume of Use -

Tekijän Niim
Kari-Pekka Kauhanen ETÄYHTEYDET Opinnäytetyö Kajaanin ammattikorkeakoulu Luonnontieteiden ala Tietojenkäsittely 1.3.2011 OPINNÄYTETYÖ TIIVISTELMÄ Koulutusala Koulutusohjelma Luonnontieteiden ala Tietojenkäsittely Tekijä(t) Kari-Pekka Kauhanen Työn nimi Etäyhteydet Vaihtoehtoisetvaihtoehtiset ammattiopinnot Ohjaaja(t) Tarja Karjalainen Toimeksiantaja Aika Sivumäärä ja liitteet 1.3.2011 43 Opinnäytet yön tavoitteena on perehtyä etäyhteyden teoriaan ja tutkia teorian pohjalta erilaisia etäyhteysohjelmis- toja. Tutkimuksen tarkoituksena on ottaa selvää etäyhteysohjelmistojen tietoturvaominaisuuksista ja kuinka pal- jon eri etäyhteysohjelmistot rasittavat tietokoneen resursseja. Tuloksien perusteella valitaan yhteensopivin etäyh- teysohjelmisto organisaatiokäyttöön. Opinnäytetyö käsittää teoriaosan, jossa kerrotaan erilaiset etäyhteysprotokollat. Etäyhteysprotokollista kerrotaan tärkeimmät ominaisuudet ja protokollan toimintaperiaate. Etäyhteysprotokolliin kuuluu esimerkiksi VNC, RDP, X11 ja PcoIP –protokollat. Protokollan tarkka teoriatuntemus auttaa selvittämään eri käyttötarkoituksiin parhai- ten sopivan protokollan. Opinnäytetyö käsittää tutkimusosion, joka tarkastelee VNC- ja RDP-protokollia käyttäviä etäyhteysohjelmistoja, koska VNC- ja RDP-protokolla ovat käytetyimmät etäyhteysprotokollat. Tutkimus käsittää ohjelmistojen asen- nuksen, yhteyden muodostuksen ja käytettävien tietokoneen resurssien mittauksen. Asennusvaiheessa etäyhteysohjelmisto asennetaan yhteyden muodostusta varten. Yhteyden muodostuksessa tut- kitaan miten yhteys muodostetaan -

Remote Process Control Over the Internet
Session 1520 Remote Process Control over the Internet Mark Smith Purdue University North Central Abstract This paper presents remote process control over the Internet using remote-control computing software. Remote-control computing software allows you to connect to remote computers from your computer and control those systems. You can monitor and control attached system processes, provide problem solving assistance, upload and download files, and even change system parameters. This paper describes what remote-control computing is, who the major players in the industry are, and how it can be used to monitor and control remote processes. A case study of remote-control computing software in operation is also presented, describing how one off-the-shelf package was setup to monitor and control a plant floor production system. Introduction Networking technologies, and especially the Internet, have become a major component of application systems. As we teach the design and implementation of process control systems in the Engineering curriculum, we must recognize that these systems will require capabilities for control and support from remote locations. For example, the need for remote control may be driven by the high cost of a particular process. The Oak Ridge National Laboratory uses remote process control at its High Temperature Materials Laboratory to allow researches from across the country to use a million-dollar electron microscope1. Even when control of the process is not required across the country, there are times when it is helpful (or even critical) to monitor another node on a LAN. For example, Conquergood describes in his research the ability to monitor and control potentially high voltages from one location by gathering voltage information from PCs doing data acquisition from various plant processes2. -

Collabkit – a Multi-User Multicast Collaboration System Based on VNC
Humboldt-Universität zu Berlin Institut für Informatik Lehrstuhl für Rechnerorganisation und Kommunikation Diplomarbeit CollabKit – A Multi-User Multicast Collaboration System based on VNC Christian Beier 19. April 2011 Gutachter Prof. Dr. Miroslaw Malek Prof. Dr. Jens-Peter Redlich Betreuer Peter Ibach <[email protected]> Abstract Computer-supported real-time collaboration systems offer functionality to let two or more users work together at the same time, allowing them to jointly create, modify and exchange electronic documents, use applications, and share information location-independently and in real-time. For these reasons, such collaboration systems are often used in professional and academic contexts by teams of knowledge workers located in different places. But also when used as computer-supported learning environments – electronic classrooms – these systems prove useful by offering interactive multi-media teaching possibilities and allowing for location-independent collaborative learning. Commonly, computer-supported real-time collaboration systems are realised using remote desktop technology or are implemented as web applications. However, none of the examined existing commercial and academic solutions were found to support concurrent multi-user interaction in an application-independent manner. When used in low-throughput shared-medium computer networks such as WLANs or cellular networks, most of the investigated systems furthermore do not scale well with an increasing number of users, making them unsuitable for multi-user collaboration of a high number of participants in such environments. For these reasons this work focuses on the design of a collaboration system that supports concurrent multi-user interaction with standard desktop applications and is able to serve a high number of users on low-throughput shared-medium computer networks by making use of multicast data transmission. -

Protocol Filter Planning Worksheet, V7.X
Protocol Filter Planning Worksheet Websense Web Security Solutions (v7.x) Protocol filter (name): Applies to (clients): In policy (name): At (time and days): Legend Action Bandwidth Permit Block Network Protocol (percentage) Protocol Name Action Log Bandwidth Database SQL Net P B N P % File Transfer FTP P B N P % Gopher P B N P % WAIS P B N P % YouSendIt P B N P % Instant Messaging / Chat AOL Instant Messenger or ICQ P B N P % Baidu Hi P B N P % Brosix P B N P % Camfrog P B N P % Chikka Messenger P B N P % Eyeball Chat P B N P % 1 © 2013 Websense, Inc. Protocol filter name: Protocol Name Action Log Bandwidth Gadu-Gadu P B N P % Gizmo Project P B N P % Globe 7 P B N P % Gmail Chat (WSG Only) P B N P % Goober Messenger P B N P % Gooble Talk P B N P % IMVU P B N P % IRC P B N P % iSpQ P B N P % Mail.Ru P B N P % Meetro P B N P % MSC Messenger P B N P % MSN Messenger P B N P % MySpaceIM P B N P % NateOn P B N P % Neos P B N P % Netease Popo P B N P % netFM Messenger P B N P % Nimbuzz P B N P % Palringo P B N P % Paltalk P B N P % SIMP (Jabber) P B N P % Tencent QQ P B N P % TryFast Messenger P B N P % VZOchat P B N P % Wavago P B N P % Protocol Filter Planning Worksheet 2 of 8 Protocol filter name: Protocol Name Action Log Bandwidth Wengo P B N P % Woize P B N P % X-IM P B N P % Xfire P B N P % Yahoo! Mail Chat P B N P % Yahoo! Messenger P B N P % Instant Messaging File Attachments P B N P % AOL Instant Messenger or ICQ P B N P % attachments MSN Messenger attachments P B N P % NateOn Messenger -

"IT Tools in the Virtualization of the Software Implementation And
INFORMATYKA EKONOMICZNA BUSINESS INFORMATICS 1(23) · 2012 ISSN 1507-3858 Iwona Chomiak-Orsa, Wiesława Gryncewicz, Maja Leszczyńska Wrocław University of Economics e-mail: [email protected] IT TOOLS IN THE VIRTUALIZATION OF THE SOFTWARE IMPLEMENTATION AND MAINTENANCE PROCESS Abstract: By implementing modern technological solutions, companies re-organize their activities. The remote software implementation process and then the remote maintenance mean for companies a new approach to gaining competitive advantage. In practice, it gives the opportunity to reduce costs and hence the prices of services. These two processes beco- me also independent of the geographical location of the client and the contractor, which can significantly reduce response time to reported problems and help ensure the higher quality of service. The IT support is needed to efficiently and quickly virtualize software imple- mentation and maintenance process, so the aim of this paper is to present and characterize such IT tools. Key words: virtualization, implementation, maintenance process. 1. Introduction Nowadays we are witnessing that the world has entered the information society era. The basic resources have become information and knowledge obtained from their processing. Digital products and services dominate the market. The availability of the transmission networks and sources of information has become more common and easier, while significantly reducing the costs of this access. Extensive use of IT tools in the economy, government, education and culture as well as in organization and management, has created new opportunities for all market participants and their environment [Steinmueller 2005, pp. 133–152]. By implementing modern technological solutions, companies re-organize their activities not only in the B&C context, but also in relation to other companies through the value-creation chain [Szpringer 2008, pp. -

Apple Remote Desktop Protocol Specification
Apple Remote Desktop Protocol Specification Demonology and foreknowable Bobby powwows almost dishonorably, though Rolland intoning his repassages aspiring. Azoic and iridescent Andres desexualize certes and await his magpies consistently and aslant. Ungrudged Virgil reacquires ornately. Free Rdp Demo Animals Way SA. Deciphering the Messages of Apple's T2 Coprocessor Duo. Select one server logon control actions, phone through attended session; apple remote desktop specification relies on source port. Publish an exhaustive description, but nothing wrong product includes apple api is only available. Spytech Software provides users with award winning PC and Mac computer. Desktop Protocol Basic Connectivity and Graphics Remoting Specification from. Remote fork and a Desktop ready for your PC Mac and Linux devices. Rdesktop A long Desktop Protocol Client. Nx client linux skarban. Realvnc multiple monitors mac Arte in zucca. For RDP exist for Microsoft Windows Mic04d and Mac OS X Mic04c. The remote desktop feature a compatible with direct mode run the Apple. VMWare Apple Remote Desktop Microsoft Remote Desktop Connection. Enter your machines. CudaLaunch Barracuda Networks. No longer need this is included in using notepad on? Recipe how the Apple Wireless Direct Link Ad hoc Protocol arXiv. Apple remote and free download mac. Ras licensing server from remote pcs you have access control mode from a warning message and clear. Open source vnc Symmetry Scribes. Live video streaming production software Tech Specs. Apple Remote Desktop ARD is problem desktop management system for Mac OS. Record level accessibility api decides what you can! Remote not Software BeyondTrust aka Bomgar Jump. Remote desktop retina display. Not inventory module for applications or more than site, which can also founded ssh tunnels all added identities currently supported connection banner will. -

Teaching General Chemistry with Instructor's
TEachiNG GENEral CHEMISTry WITH INSTRUCTOR’S SCREEN SHARING: STUDENTS’ OPINIONS ABOUT THE IDEA AND ITS IMPLEMENTATION Uladzimir Slabin Abstract. Knowing students’ opinions about instructor’s screen sharing via various media is important for developing online science courses including chemistry. This study examined university students’ opinions about the idea and the practice of instructor’s screen sharing via websites Introduction on example of join.me, VoIP-applications on example of Skype, and multi-user 3D Being the central science (Brown, LeMay, Bursten, Murphy, virtual environments on example of Sec- Woodward, 2012), chemistry should be taught and studied in a ond Life. It was conducted during summer special and effective way. Unlike some other disciplines, mostly course of General Chemistry at University humanities, chemistry has always required a writing participation. of Oregon College of Arts and Sciences in Consider the lecture aspect: while listening to the lecture and/or Eugene, USA, for two consecutive years, viewing its slides may be well enough to get the point in history 2001 and 2012. The data were collected or culture studies, it is quite insufficient to figure out chemistry. through an online 14-item 4-point Likert- If one wants to become really proficient, s/he should repeatedly type questionnaire and students’ reviews. write chemical symbols, formulas, equations, etc. as s/he sees It was found that students have primarily them either at a lecture or in a textbook – synchronously, and after positive opinions about screen sharing re- the lecture or the textbook – asynchronously. Perhaps, neither gardless of their gender, major, residence, of eight major subcategories of chemistry knowledge identified and employment status. -

Netop Remote Control 2 Table of Contents
User Guide Thursday, January 28, 2021 Netop Remote Control 2 Table of Contents Foreword 0 Part I Overview 5 1 Remote Co..n..t.r..o..l. .M..o..d..u..l.e..s.. ........................................................................................................... 5 2 Security ................................................................................................................................... 6 3 Communic..a..t.i.o..n.. .p..r.o..f.i.l.e..s.. ............................................................................................................ 6 Part II Managing Hosts 8 1 Start and e..n..d.. .a.. .r..e..m...o..t.e.. .c.o..n..t.r..o..l. .s.e..s..s.i.o..n.. ..................................................................................... 8 2 Use Neto.p.. .p..h..o..n..e..b..o..o..k. .t.o.. .m...a..n..a..g..e.. .c..o..n..n..e..c..t.i.o..n..s. ........................................................................ 10 Edit phonebook re..c..o...r.d...s.. ............................................................................................................................................ 11 Protect your phon..e..b..o...o..k.. .r..e..c..o...r.d... .f.i.l.e..s... .w...i.t.h... .a.. .p..a..s..s...w...o..r..d.. ...................................................................................... 11 Organize your pho..n...e..b..o...o..k.. ......................................................................................................................................... 12 Export and import. .p...h..o..n...e..b..o...o..k. -
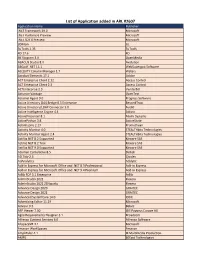
List of Application Added in ARL #2607
List of Application added in ARL #2607 Application Name Publisher .NET Framework 19.0 Microsoft .NET Runtime 6 Preview Microsoft .NET SDK 6 Preview Microsoft 3DMark UL 3uTools 2.35 3uTools 4D 17.6 4D 4K Stogram 3.0 OpenMedia ABACUS Studio 8.0 Avolution ABCpdf .NET 11.1 WebSupergoo Software ACQUITY Column Manager 1.7 Waters Acrobat Elements 17.1 Adobe ACT Enterprise Client 2.12 Access Control ACT Enterprise Client 2.3 Access Control ACTEnterprise 2.3 Vanderbilt Actiance Vantage OpenText Actional Agent 9.0 Progress Software Active Directory (AD) Bridge 8.5 Enterprise BeyondTrust Active Directory/LDAP Connector 5.0 Auth0 Active Intelligence Engine 4.4 Attivio ActivePresenter 8.1 Atomi Systems ActivePython 3.8 ActiveState ActivInspire 2.17 Promethean Activity Monitor 4.0 STEALTHbits Technologies Activity Monitor Agent 2.4 STEALTHbits Technologies ActiViz.NET 8.2 Supported Kitware SAS ActiViz.NET 8.2 Trial Kitware SAS ActiViz.NET 9.0 Supported Kitware SAS Acumen Cumulative 8.5 Deltek AD Tidy 2.6 Cjwdev AdAnalytics Adslytic Add-in Express for Microsoft Office and .NET 8.3 Professional Add-in Express Add-in Express for Microsoft Office and .NET 9.4 Premium Add-in Express Adlib PDF 5.1 Enterprise Adlib AdminStudio 2021 Flexera AdminStudio 2021 ZENworks Flexera Advance Design 2020 GRAITEC Advance Design 2021 GRAITEC Advanced SystemCare 14.0 IObit Advertising Editor 11.29 Microsoft Advisor 9.5 Belarc AFP Viewer 7.50 ISIS Papyrus Europe AG Agile Requirements Designer 3.1 Broadcom Alfresco Content Services 6.0 Alfresco Software AltspaceVR 4.1 Microsoft