Apple Remote Desktop Protocol Specification
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Software Catalog for Patch Management and Software Deployment
Software Catalog for Patch Management and Software Deployment Find all supported 3rd party applications that can be patched and deployed in Monitoring & Asset Management below. Click on a software to get a more detailed view of the respective versions. (Last Update: 2021/03/23) Vendors # Citrix 4 7-Zip 4 Code4ward.net 5 A CoreFTP 5 Acro 4 Corel 5 Adobe 4 CrowdStrike, Inc 5 AdoptOpenJDK 4 D AIMP Dev Team 4 dotPDN LLC 5 Amazon Services LLC 4 Dropbox 5 Apache Software Foundation 4 E Apple 4 Evernote Corporation 5 Atlassian 4 F Audacity 4 FileZilla 5 Azul Systems, Inc 4 Foxit Corporation 5 B G Bandicam Company 4 GIT 5 Barco, Inc 4 GIMP.org 5 BlueJeans Network, Inc. 4 Glavsoft 5 Botkind, Inc. 4 Google 5 Box.com 4 Gretech Corp 5 C Inkscape 5 CDBurnerXP 4 IrfanView 5 Cisco 4 Software Catalog for Patch Management and Software Deployment J P Jabra 5 PeaZip 10 JAM Software 5 Pidgin 10 Juraj Simlovic 5 Piriform 11 K Plantronics, Inc. 11 KeePass 5 Plex, Inc 11 L Prezi Inc 11 LibreOffice 5 Programmer‘s Notepad 11 Lightning UK 5 PSPad 11 LogMeIn, Inc. 5 Q M QSR International 11 Malwarebytes Corporation 5 Quest Software, Inc 11 Microsoft 6 R MIT 10 R Foundation 11 Morphisec 10 RarLab 11 Mozilla Foundation 10 Real 11 N RealVNC 11 Neevia Technology 10 RingCentral, Inc. 11 NextCloud GmbH 10 S Nitro Software, Inc. 10 Scooter Software, Inc 11 Nmap Project 10 Siber Systems 11 Node.js Foundation 10 Simon Tatham 11 Notepad++ 10 Skype Technologies S.A. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

THINC: a Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices
THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2011 c 2011 Ricardo A. Baratto This work may be used in accordance with Creative Commons, Attribution-NonCommercial-NoDerivs License. For more information about that license, see http://creativecommons.org/licenses/by-nc-nd/3.0/. For other uses, please contact the author. ABSTRACT THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto THINC is a new virtual and remote display architecture for desktop computing. It has been designed to address the limitations and performance shortcomings of existing remote display technology, and to provide a building block around which novel desktop architectures can be built. THINC is architected around the notion of a virtual display device driver, a software-only component that behaves like a traditional device driver, but instead of managing specific hardware, enables desktop input and output to be intercepted, manipulated, and redirected at will. On top of this architecture, THINC introduces a simple, low-level, device-independent representation of display changes, and a number of novel optimizations and techniques to perform efficient interception and redirection of display output. This dissertation presents the design and implementation of THINC. It also intro- duces a number of novel systems which build upon THINC's architecture to provide new and improved desktop computing services. The contributions of this dissertation are as follows: • A high performance remote display system for LAN and WAN environments. -

Realvnc @ LC August 2018 LC User Meeting
RealVNC @ LC August 2018 LC User Meeting Cameron Harr Title (optional) Aug. 21, 2018 LLNL-PRES-XXXXXX This work was performed under the auspices of the U.S. Department of Energy by Lawrence Livermore National Laboratory under contract DE-AC52-07NA27344. Lawrence Livermore National Security, LLC RealVNC @ LC § What is RealVNC? § What did we have? § What do we have now? § What’s coming in the future? § How do you use it? 2 LLNL-PRES-xxxxxx Cloud versus direct with VNC Connect VNC Connect is unique among remote access software in its ability to offer both cloud and direct connectivity methods within a single product. At first glance, knowing whether to connect directly or via our cloud service can seem confusing. However, there are clear benefits to each connection method. The trick is knowing how to maximize these benefits. This brief product guide provides an overview of the differences between cloud and direct connectivity, and offers some advice on how each method can be used to your greatest advantage. Key terminology Throughout this guide, we refer to certain RealVNC-specific terminology. VNC Connect is comprised of two separate apps: VNC Server and VNC Viewer. You must install and license VNC Server on the computer you want to control. This is known as your VNC Server computer. You must then install VNC Viewer on the computer or device you want to take control from, which is known as your VNC Viewer device. You do not need to license this device, meaning you can freely connect to your VNC Server computer from as many devices as you wish. -

VNC Connect Security Whitepaper
VNC Connect security whitepaper VNC Connect security whitepaper Version 1.3 Contents Contents .................................................................................................................................................................... 2 Introduction ............................................................................................................................................................... 3 Security architecture ................................................................................................................................................. 4 Cloud infrastructure ................................................................................................................................................... 7 Client security ........................................................................................................................................................... 9 Development procedures ........................................................................................................................................ 12 Summary ................................................................................................................................................................. 13 VNC Connect security whitepaper Introduction Customer security is of paramount importance to RealVNC. As such, our security strategy is ingrained in all aspects of our VNC Connect software. We have invested extensively in our security, and take great pride in our successful -
Linkedin Corporation Not Just Your Ordinary Network
LinkedIn Corporation Not Just Your Ordinary Network Hardware In the business world, relationships matter, and no company understands this better • Xserve than LinkedIn. Cofounders Reid Hoffman and Jean-Luc Vaillant created the premier • Xsan professional social network to help people open doors to opportunities using the • Mac Pro business relationships they have already established. LinkedIn’s secret is the six- • MacBook degrees-of-separation philosophy, which helps people connect to a broader network, • MacBook Air find each other, and be found. The approach is clearly working. Today, LinkedIn is an • MacBook Pro online network of more than 40 million experienced professionals around the world, • Mac mini representing 150 industries. • iPhone • iPod 99 percent Java, 100 percent Mac • Apple Cinema Display A no-nonsense site with little visual fluff and few distractions, LinkedIn provides the perfect venue for busy professionals who have little time to spare. Behind the scenes, a team of talented engineers and software developers work to keep the site stream- Software lined, responsive, and as useful as possible. To equip technical staff with a powerful • Mac OS X Leopard development environment and the high-performance hardware necessary to write, • Mac OS X Leopard Server debug, and deploy code efficiently, LinkedIn has a standard policy: All development • Apple Remote Desktop is 99 percent Java and 100 percent Mac. • iChat • QuickTime Streaming Server Every new engineer who joins LinkedIn automatically receives a new Mac Pro with • QuickTime Broadcast Server dual quad-core “Nehalem” CPUs and 12GB of RAM, as well as a MacBook. The only • JAMF Casper Suite tough decision: engineers must choose between two 23-inch Apple Cinema Displays • Microsoft Office or one 30-inch Apple Cinema HD Display. -

Automator Workflow Techniques 3/4/09 8:51 AM
Apple - Pro - Techniques - Automator Workflow Techniques 3/4/09 8:51 AM Search Profiles Techniques Pro Tips Resources Automator Workflow Techniques Uploading Aperture Image Previews to Automator Workflow Techniques an FTP Server Creating a Folder Watching Workflow By Ben Waldie Creating a Scheduled Automator Workflow Export presets in Aperture make it easy to quickly export preview versions of selected images in your photo library. But wouldn’t it be great to automatically rename those images and send them to your FTP server at the Individually Processing Files Through an Automator Workflow same time? With Automator, you can. Uploading Aperture Image Previews to an FTP Server The following steps will walk you through the process of creating an Automator workflow that will export selected aperture images as previews, rename them sequentially with the current date, and upload them to your FTP server. Creating a Photo Slideshow DVD This particular workflow uses the popular FTP/SFTP application Fetch to perform the upload process. Creating an iWeb Photo Preview Page Automator support was introduced with Fetch version 5.1, so you will need to make sure that you have Fetch 5.1 or higher installed to use this workflow. A demonstration version of Fetch is available from the Fetch Softworks website. Downloads and Useful Links Step 1: Create a folder named Web Images on the Step 9: Locate and select the Rename Finder Items desktop. action in the Finder category, and drag it into the Download the workflow described here workflow area. Choose Make Sequential from the Learn more about Automator Step 2: Launch Automator, located in the popup at the top of the action. -

Trend Micro Security (For Mac) 3.0 Administrator's Guide
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes, and the latest version of the applicable user documentation, which are available from the Trend Micro website at: http://docs.trendmicro.com/en-us/enterprise/trend-micro-security-(for-mac).aspx Trend Micro, the Trend Micro t-ball logo, OfficeScan, Worry-Free and TrendLabs are trademarks or registered trademarks of Trend Micro, Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2017 Trend Micro Incorporated. All rights reserved. Document Part No.: TSEM37299/160114 Release Date: February 2017 The user documentation for Trend Micro Security (for Mac) introduces the main features of the software and installation instructions for your production environment. Read through it before installing or using the software. Detailed information about how to use specific features within the software are available in the online help file and the online Knowledge Base at Trend Micro’s website. Trend Micro always seeks to improve its documentation. If you have questions, comments, or suggestions about this or any Trend Micro document, please contact us at [email protected]. Please evaluate this documentation on the following site: http://www.trendmicro.com/download/documentation/rating.asp Table of Contents Preface Preface .............................................................................................................. -

The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
The Application Usage and Risk Report An Analysis of End User Application Trends in the Enterprise 8th Edition, December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 94089 www.paloaltonetworks.com Table of Contents Executive Summary ........................................................................................................ 3 Demographics ............................................................................................................................................. 4 Social Networking Use Becomes More Active ................................................................ 5 Facebook Applications Bandwidth Consumption Triples .......................................................................... 5 Twitter Bandwidth Consumption Increases 7-Fold ................................................................................... 6 Some Perspective On Bandwidth Consumption .................................................................................... 7 Managing the Risks .................................................................................................................................... 7 Browser-based Filesharing: Work vs. Entertainment .................................................... 8 Infrastructure- or Productivity-Oriented Browser-based Filesharing ..................................................... 9 Entertainment Oriented Browser-based Filesharing .............................................................................. 10 Comparing Frequency and Volume of Use -

Institutionen För Datavetenskap Department of Computer and Information Science
Institutionen för datavetenskap Department of Computer and Information Science Final thesis Implementing extended functionality for an HTML5 client for remote desktops by Samuel Mannehed LIU-IDA/LITH-EX-A—14/015--SE 6/28/14 Linköpings universitet Linköpings universitet SE-581 83 Linköping, Sweden 581 83 Linköping Final thesis Implementing extended functionality for an HTML5 client for remote desktops by Samuel Mannehed LIU-IDA/LITH-EX-A--14/015--SE June 28, 2014 Supervisors: Peter Åstrand (Cendio AB), Maria Vasilevskaya (IDA) Examiner: Prof. Simin Nadjm-Tehrani På svenska Detta dokument hålls tillgängligt på Internet – eller dess framtida ersättare – under en längre tid från publiceringsdatum under förutsättning att inga extra-ordinära omständigheter uppstår. Tillgång till dokumentet innebär tillstånd för var och en att läsa, ladda ner, skriva ut enstaka kopior för enskilt bruk och att använda det oförändrat för ickekommersiell forskning och för undervisning. Överföring av upphovsrätten vid en senare tidpunkt kan inte upphäva detta tillstånd. All annan användning av dokumentet kräver upphovsmannens medgivande. För att garantera äktheten, säkerheten och tillgängligheten finns det lösningar av teknisk och administrativ art. Upphovsmannens ideella rätt innefattar rätt att bli nämnd som upphovsman i den omfattning som god sed kräver vid användning av dokumentet på ovan beskrivna sätt samt skydd mot att dokumentet ändras eller presenteras i sådan form eller i sådant sammanhang som är kränkande för upphovsmannens litterära eller konstnärliga anseende eller egenart. För ytterligare information om Linköping University Electronic Press se förlagets hemsida http://www.ep.liu.se/ In English The publishers will keep this document online on the Internet - or its possible replacement - for a considerable time from the date of publication barring exceptional circumstances. -
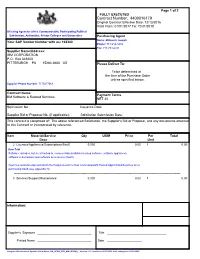
Contract Number: 4400016179
Page 1 of 2 FULLY EXECUTED Contract Number: 4400016179 Original Contract Effective Date: 12/13/2016 Valid From: 01/01/2017 To: 12/31/2018 All using Agencies of the Commonwealth, Participating Political Subdivision, Authorities, Private Colleges and Universities Purchasing Agent Name: Millovich Joseph Your SAP Vendor Number with us: 102380 Phone: 717-214-3434 Fax: 717-783-6241 Supplier Name/Address: IBM CORPORATION P.O. Box 643600 PITTSBURGH PA 15264-3600 US Please Deliver To: To be determined at the time of the Purchase Order unless specified below. Supplier Phone Number: 7175477069 Contract Name: Payment Terms IBM Software & Related Services NET 30 Solicitation No.: Issuance Date: Supplier Bid or Proposal No. (if applicable): Solicitation Submission Date: This contract is comprised of: The above referenced Solicitation, the Supplier's Bid or Proposal, and any documents attached to this Contract or incorporated by reference. Item Material/Service Qty UOM Price Per Total Desc Unit 2 Licenses/Appliances/Subscriptions/SaaS 0.000 0.00 1 0.00 Item Text Software: includes, but is not limited to, commercially available licensed software, software appliances, software subscriptions and software as a service (SaaS). Agencies must develop and attach the Requirements for Non-Commonwealth Hosted Applications/Services when purchasing SaaS (see Appendix H). -------------------------------------------------------------------------------------------------------------------------------------------------------- 3 Services/Support/Maintenance 0.000 0.00 -

Tekijän Niim
Kari-Pekka Kauhanen ETÄYHTEYDET Opinnäytetyö Kajaanin ammattikorkeakoulu Luonnontieteiden ala Tietojenkäsittely 1.3.2011 OPINNÄYTETYÖ TIIVISTELMÄ Koulutusala Koulutusohjelma Luonnontieteiden ala Tietojenkäsittely Tekijä(t) Kari-Pekka Kauhanen Työn nimi Etäyhteydet Vaihtoehtoisetvaihtoehtiset ammattiopinnot Ohjaaja(t) Tarja Karjalainen Toimeksiantaja Aika Sivumäärä ja liitteet 1.3.2011 43 Opinnäytet yön tavoitteena on perehtyä etäyhteyden teoriaan ja tutkia teorian pohjalta erilaisia etäyhteysohjelmis- toja. Tutkimuksen tarkoituksena on ottaa selvää etäyhteysohjelmistojen tietoturvaominaisuuksista ja kuinka pal- jon eri etäyhteysohjelmistot rasittavat tietokoneen resursseja. Tuloksien perusteella valitaan yhteensopivin etäyh- teysohjelmisto organisaatiokäyttöön. Opinnäytetyö käsittää teoriaosan, jossa kerrotaan erilaiset etäyhteysprotokollat. Etäyhteysprotokollista kerrotaan tärkeimmät ominaisuudet ja protokollan toimintaperiaate. Etäyhteysprotokolliin kuuluu esimerkiksi VNC, RDP, X11 ja PcoIP –protokollat. Protokollan tarkka teoriatuntemus auttaa selvittämään eri käyttötarkoituksiin parhai- ten sopivan protokollan. Opinnäytetyö käsittää tutkimusosion, joka tarkastelee VNC- ja RDP-protokollia käyttäviä etäyhteysohjelmistoja, koska VNC- ja RDP-protokolla ovat käytetyimmät etäyhteysprotokollat. Tutkimus käsittää ohjelmistojen asen- nuksen, yhteyden muodostuksen ja käytettävien tietokoneen resurssien mittauksen. Asennusvaiheessa etäyhteysohjelmisto asennetaan yhteyden muodostusta varten. Yhteyden muodostuksessa tut- kitaan miten yhteys muodostetaan