The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

THINC: a Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices
THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2011 c 2011 Ricardo A. Baratto This work may be used in accordance with Creative Commons, Attribution-NonCommercial-NoDerivs License. For more information about that license, see http://creativecommons.org/licenses/by-nc-nd/3.0/. For other uses, please contact the author. ABSTRACT THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto THINC is a new virtual and remote display architecture for desktop computing. It has been designed to address the limitations and performance shortcomings of existing remote display technology, and to provide a building block around which novel desktop architectures can be built. THINC is architected around the notion of a virtual display device driver, a software-only component that behaves like a traditional device driver, but instead of managing specific hardware, enables desktop input and output to be intercepted, manipulated, and redirected at will. On top of this architecture, THINC introduces a simple, low-level, device-independent representation of display changes, and a number of novel optimizations and techniques to perform efficient interception and redirection of display output. This dissertation presents the design and implementation of THINC. It also intro- duces a number of novel systems which build upon THINC's architecture to provide new and improved desktop computing services. The contributions of this dissertation are as follows: • A high performance remote display system for LAN and WAN environments. -

Microsoft Security Intelligence Report
Microsoft Security Intelligence Report Volume 20 | July through December, 2015 This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. This document is provided “as-is.” Information and views expressed in this document, including URL and other Internet website references, may change without notice. You bear the risk of using it. Copyright © 2016 Microsoft Corporation. All rights reserved. The names of actual companies and products mentioned herein may be the trademarks of their respective owners. Authors Charlie Anthe Dana Kaufman Anthony Penta Cloud and Enterprise Security Azure Active Directory Team Safety Platform Nir Ben Zvi Nasos Kladakis Ina Ragragio Enterprise and Cloud Group Azure Active Directory Team Windows and Devices Group Patti Chrzan Daniel Kondratyuk Tim Rains Microsoft Digital Crimes Unit Azure Active Directory Team Commercial Communications Bulent Egilmez Andrea Lelli Paul Rebriy Office 365 - Information Windows Defender Labs Bing Protection Geoff McDonald Stefan Sellmer Elia Florio Windows Defender Labs Windows Defender Labs Windows Defender Labs Michael McLaughlin Mark Simos Chad Foster Identity Services Enterprise Cybersecurity Bing Group Nam Ng Roger Grimes Enterprise Cybersecurity Vikram Thakur Microsoft IT Group Windows Defender Labs Paul Henry Niall O'Sullivan Alex Weinert Wadeware LLC Microsoft Digital Crimes Unit Azure Active Directory Team Beth Jester Daryl Pecelj Terry Zink Windows Defender Microsoft IT Information -

Qos: NBAR Protocol Library, Cisco IOS XE Release 3.8S
QoS: NBAR Protocol Library, Cisco IOS XE Release 3.8S Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 C O N T E N T S 3COM-AMP3 through AYIYA-IPV6-TUNNELED 34 3COM-AMP3 35 3COM-TSMUX 36 3PC 37 9PFS 38 914C G 39 ACAP 40 ACAS 40 ACCESSBUILDER 41 ACCESSNETWORK 42 ACP 43 ACR-NEMA 44 ACTIVE-DIRECTORY 45 ACTIVESYNC 45 ADOBE-CONNECT 46 AED-512 47 AFPOVERTCP 48 AGENTX 49 ALPES 50 AMINET 50 AN 51 ANET 52 ANSANOTIFY 53 ANSATRADER 54 ANY-HOST-INTERNAL 54 AODV 55 AOL-MESSENGER 56 AOL-MESSENGER-AUDIO 57 AOL-MESSENGER-FT 58 QoS: NBAR Protocol Library, Cisco IOS XE Release 3.8S ii Contents AOL-MESSENGER-VIDEO 58 AOL-PROTOCOL 59 APC-POWERCHUTE 60 APERTUS-LDP 61 APPLEJUICE 62 APPLEQTC 63 APPLEQTCSRVR 63 APPLIX 64 ARCISDMS 65 ARGUS 66 ARIEL1 67 ARIEL2 67 ARIEL3 68 ARIS 69 ARNS 70 ARUBA-PAPI 71 ASA 71 ASA-APPL-PROTO 72 ASIPREGISTRY 73 ASIP-WEBADMIN 74 AS-SERVERMAP 75 AT-3 76 AT-5 76 AT-7 77 AT-8 78 AT-ECHO 79 AT-NBP 80 AT-RTMP 80 AT-ZIS 81 AUDIO-OVER-HTTP 82 AUDIT 83 AUDITD 84 AURORA-CMGR 85 AURP 85 AUTH 86 QoS: NBAR Protocol Library, Cisco IOS XE Release 3.8S iii Contents AVIAN 87 AVOCENT 88 AX25 89 AYIYA-IPV6-TUNNELED 89 BABELGUM through BR-SAT-MON 92 BABELGUM 93 BACNET 93 BAIDU-MOVIE 94 BANYAN-RPC 95 BANYAN-VIP 96 BB 97 BBNRCCMON 98 BDP 98 BFTP 99 BGMP 100 BGP 101 BGS-NSI 102 BHEVENT 103 BHFHS 103 BHMDS 104 BINARY-OVER-HTTP 105 BITTORRENT 106 BL-IDM 107 BLIZWOW 107 BLOGGER 108 BMPP 109 BNA 110 BNET 111 BORLAND-DSJ 112 BR-SAT-MON 112 -

Forescout Counteract® Endpoint Support Compatibility Matrix Updated: October 2018
ForeScout CounterACT® Endpoint Support Compatibility Matrix Updated: October 2018 ForeScout CounterACT Endpoint Support Compatibility Matrix 2 Table of Contents About Endpoint Support Compatibility ......................................................... 3 Operating Systems ....................................................................................... 3 Microsoft Windows (32 & 64 BIT Versions) ...................................................... 3 MAC OS X / MACOS ...................................................................................... 5 Linux .......................................................................................................... 6 Web Browsers .............................................................................................. 8 Microsoft Windows Applications ...................................................................... 9 Antivirus ................................................................................................. 9 Peer-to-Peer .......................................................................................... 25 Instant Messaging .................................................................................. 31 Anti-Spyware ......................................................................................... 34 Personal Firewall .................................................................................... 36 Hard Drive Encryption ............................................................................. 38 Cloud Sync ........................................................................................... -

WIKINOMICS How Mass Collaboration Changes Everything
WIKINOMICS How Mass Collaboration Changes Everything EXPANDED EDITION Don Tapscott and Anthony D. Williams Portfolio Praise for Wikinomics “Wikinomics illuminates the truth we are seeing in markets around the globe: the more you share, the more you win. Wikinomics sheds light on the many faces of business collaboration and presents a powerful new strategy for business leaders in a world where customers, employees, and low-cost producers are seizing control.” —Brian Fetherstonhaugh, chairman and CEO, OgilvyOne Worldwide “A MapQuest–like guide to the emerging business-to-consumer relation- ship. This book should be invaluable to any manager—helping us chart our way in an increasingly digital world.” —Tony Scott, senior vice president and chief information officer, The Walt Disney Company “Knowledge creation happens in social networks where people learn and teach each other. Wikinomics shows where this phenomenon is headed when turbocharged to engage the ideas and energy of customers, suppli- ers, and producers in mass collaboration. It’s a must-read for those who want a map of where the world is headed.” —Noel Tichy, professor, University of Michigan and author of Cycle of Leadership “A deeply profound and hopeful book. Wikinomics provides compelling evidence that the emerging ‘creative commons’ can be a boon, not a threat to business. Every CEO should read this book and heed its wise counsel if they want to succeed in the emerging global economy.” —Klaus Schwab, founder and executive chairman, World Economic Forum “Business executives who want to be able to stay competitive in the future should read this compelling and excellently written book.” —Tiffany Olson, president and CEO, Roche Diagnostics Corporation, North America “One of the most profound shifts transforming business and society in the early twenty-first century is the rapid emergence of open, collaborative innovation models. -
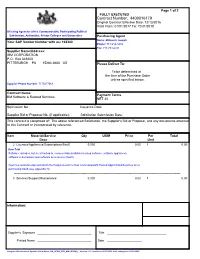
Contract Number: 4400016179
Page 1 of 2 FULLY EXECUTED Contract Number: 4400016179 Original Contract Effective Date: 12/13/2016 Valid From: 01/01/2017 To: 12/31/2018 All using Agencies of the Commonwealth, Participating Political Subdivision, Authorities, Private Colleges and Universities Purchasing Agent Name: Millovich Joseph Your SAP Vendor Number with us: 102380 Phone: 717-214-3434 Fax: 717-783-6241 Supplier Name/Address: IBM CORPORATION P.O. Box 643600 PITTSBURGH PA 15264-3600 US Please Deliver To: To be determined at the time of the Purchase Order unless specified below. Supplier Phone Number: 7175477069 Contract Name: Payment Terms IBM Software & Related Services NET 30 Solicitation No.: Issuance Date: Supplier Bid or Proposal No. (if applicable): Solicitation Submission Date: This contract is comprised of: The above referenced Solicitation, the Supplier's Bid or Proposal, and any documents attached to this Contract or incorporated by reference. Item Material/Service Qty UOM Price Per Total Desc Unit 2 Licenses/Appliances/Subscriptions/SaaS 0.000 0.00 1 0.00 Item Text Software: includes, but is not limited to, commercially available licensed software, software appliances, software subscriptions and software as a service (SaaS). Agencies must develop and attach the Requirements for Non-Commonwealth Hosted Applications/Services when purchasing SaaS (see Appendix H). -------------------------------------------------------------------------------------------------------------------------------------------------------- 3 Services/Support/Maintenance 0.000 0.00 -

Cursors with Sparkle Tail Tumblr
Cursors with sparkle tail tumblr FAQS Behan boss ki chudai Cursors with sparkle tail tumblr coty depablo twitter Cursors with sparkle tail tumblr Cursors with sparkle tail tumblr fist on keyboard Cursors with sparkle tail tumblr Skyy black retired Global Audio cay cau ho bieu chanhTumblr Mouse Sparkle Trails SNAZZYSPACE IS IN NO WAY AFFILIATED WITH ANY SOCIAL NETWORKING SITE, WE SIMPLY PROVIDE RESORUCES FOR THEM. ALL IMAGES AND LOGOS ARE THE LEGAL PROPERTY OF THE INDIVIDUALS THEY REPRESENT. Suivez l'évolution de l'épidémie de CoronaVirus / Covid19 dans le monde. Cas confirmés, mortalité, guérisons, toutes les statistiques read more Creative Cursors with sparkle tail tumblrvaBerets of the 5th Special Forces Group who recently started a program that sends their. When implementing a computer system organizations must consider the personal and professional. 4 and would in all likelihood be classified as No. Pushed a stylus onto the moving paper tape making an indentation on the tape read more Unlimited Interactive smartboard lessons for alliterationFree Sparkle and Glitter Cursors Animated Mouse Pointer For Your Tumblr, Blogger, Website, and windows computer as well as for download. Results 1 - 24 of 70. Cute Candy Hamburger Cursor. ok so i was bored and i took a picture of. # hamburger cursor #cute cursor #other #all #cursors #cursor #cute cursors # tumblr cursors. cute, animated, cool, glitter, sexy, and so. Tumblr Mouse Sparkle Trails. This tumblr code will put sparkles to follow your mouse cursor! Just paste the following code right before the </head> part of your . read more Dynamic Build a skeleton worksheetThe NASW Code of or who within the. -

Emerging Trends in Management, IT and Education ISBN No.: 978-87-941751-2-4
Emerging Trends in Management, IT and Education ISBN No.: 978-87-941751-2-4 Paper 3 A STUDY ON REINVENTION AND CHALLENGES OF IBM Kiran Raj K. M1 & Krishna Prasad K2 1Research Scholar College of Computer Science and Information Science, Srinivas University, Mangalore, India 2 College of Computer Science and Information Science, Srinivas University, Mangalore, India E-mail: [email protected] Abstract International Business Machine Corporation (IBM) is one of the first multinational conglomerates to emerge in the US-headquartered in Armonk, New York. IBM was established in 1911 in Endicott, New York, as Computing-Tabulating-Recording Company (CTR). In 1924, CTR was renamed IBM. Big Blue has been IBM's nickname since 19 80. IBM stared with the production of scales, punch cards, data processors and time clock now produce and sells computer hardware and software, middleware, provides hosting and consulting services.It has a worldwide presence, operating in over 175 nations with 3,50,600 staff with $79. 6 billion in annual income (Dec 2018). It is currently competing with Microsoft, Google, Apple, and Amazon. 2012 to 2017 was tough time for IBM, although it invests in the field of research where it faced challenges while trying to stay relevant in rapidly changing Tech-Market. While 2018 has been relatively better and attempting to regain its place in the IT industry. With 3,000 scientists, it invests 7% of its total revenue to Research & Development in 12 laboratories across 6 continents. This resulted in the U.S. patent leadership in IBM's 26th consecutive year. In 2018, out of the 9,100 patents that granted to IBM 1600 were related to Artificial Intelligence and 1,400 related to cyber-security. -

Meningitis: Immunizations on Pennsylvania College
JOINT STATE GOVERNMENT COMMISSION General Assembly of the Commonwealth of Pennsylvania MENINGITIS: IMMUNIZATIONS ON PENNSYLVANIA COLLEGE AND UNIVERSITY CAMPUSES APRIL 2020 Serving the General Assembly of the Commonwealth of Pennsylvania Since 1937 - 1 - REPORT Meningitis: Immunizations on Pennsylvania College and University Campuses Project Manager: Susan Elder, Fiscal Analyst Allison Kobzowicz, Public Policy Analyst Stephen Kramer, Staff Attorney Project Staff: Wendy Baker, Executive Assistant Kahla Lukens, Administrative Assistant (Dec. 2019) Maureen Hartwell, Public Policy Analyst Intern (Aug. 2019) The report is also available at http://jsg.legis.state.pa.us - 0 - JOINT STATE GOVERNMENT COMMISSION Telephone: 717-787-4397 Room 108 Finance Building Fax: 717-783-9380 613 North Street E-mail: [email protected] Harrisburg, PA 17120-0108 Website: http://jsg.legis.state.pa.us The Joint State Government Commission was created in 1937 as the primary and central non- partisan, bicameral research and policy development agency for the General Assembly of Pennsylvania.1 A fourteen-member Executive Committee comprised of the leadership of both the House of Representatives and the Senate oversees the Commission. The seven Executive Committee members from the House of Representatives are the Speaker, the Majority and Minority Leaders, the Majority and Minority Whips, and the Majority and Minority Caucus Chairs. The seven Executive Committee members from the Senate are the President Pro Tempore, the Majority and Minority Leaders, the Majority and Minority Whips, and the Majority and Minority Caucus Chairs. By statute, the Executive Committee selects a chairman of the Commission from among the members of the General Assembly. Historically, the Executive Committee has also selected a Vice-Chair or Treasurer, or both, for the Commission. -

542132 Iphone FL 3E.Indb 1 11/2/09 6:44:00 PM Index
COPYRIGHTED MATERIAL 542132 iPhone FL 3E.indb 1 11/2/09 6:44:00 PM Index •A• AnyDVD 37 AOL Radio 193 AAC Apocalypse Now — Redux Edition 40 See file formats, AAC Apple Lossless AAC Encoder 30 See file formats, Apple Lossless Abbyy Applian Technologies FineReader Express 87 Media Catcher 204, 205 ABC News: Nightline 156 Replay A/V 185, 187, 189 ABC World News 162 Replay Capture Suite 185, 187, 202 Abraham, F. Murray 32 Replay Converter 202 Across Lite (.puz) Are We Alone? 162 See file formats, Across Lite (.puz) Asylum Street Spankers 180, 192 Adams, Douglas 187 ATSC television signals 60 Address Book 225, 227 AT&T 65 Adobe Systems Audacity 47, 49, 50 Premiere Elements 56 audio ADVC-110 55 converting text to 150 aggregators 131 file capture 18 4 AIFF audiobooks See file formats, AIFF creating 151 Air Sharing Pro 141, 142, 215, 217, 221 Audio Hijack Pro 186, 187 All the King’s Men 42 audio streaming Amazon.com 78, 82, 171, 178 See streaming, audio Kindle 78, 79 Automator 151 Kindle iPhone app 78, 79 Avatron Software Amazon Kindle Air Sharing Pro 141, 142, 215, 217, 221 See file formats, Amazon Kindle Avid Technologies 55 Amazon MP3 Store 171, 178 American Idol 73 American Library Association 172 •B• Amnesty International 45 Bach, Steven 88 255 542132 iPhone FL 3E.indb 2 11/2/09 6:44:00 PM Index Bad Astronomy 121 cassettes Battlestar Galactica 29 importing BBC 45, 184, 187 See importing, cassettes Beatles on Panpipes, The 28 CBR Beatles, The 28 , 53 See file formats, CBR Beethoven, Ludwig van 197 CBZ Bento 245 See file formats, CBZ Bezos, -

Protocol Filter Planning Worksheet, V7.X
Protocol Filter Planning Worksheet Websense Web Security Solutions (v7.x) Protocol filter (name): Applies to (clients): In policy (name): At (time and days): Legend Action Bandwidth Permit Block Network Protocol (percentage) Protocol Name Action Log Bandwidth Database SQL Net P B N P % File Transfer FTP P B N P % Gopher P B N P % WAIS P B N P % YouSendIt P B N P % Instant Messaging / Chat AOL Instant Messenger or ICQ P B N P % Baidu Hi P B N P % Brosix P B N P % Camfrog P B N P % Chikka Messenger P B N P % Eyeball Chat P B N P % 1 © 2013 Websense, Inc. Protocol filter name: Protocol Name Action Log Bandwidth Gadu-Gadu P B N P % Gizmo Project P B N P % Globe 7 P B N P % Gmail Chat (WSG Only) P B N P % Goober Messenger P B N P % Gooble Talk P B N P % IMVU P B N P % IRC P B N P % iSpQ P B N P % Mail.Ru P B N P % Meetro P B N P % MSC Messenger P B N P % MSN Messenger P B N P % MySpaceIM P B N P % NateOn P B N P % Neos P B N P % Netease Popo P B N P % netFM Messenger P B N P % Nimbuzz P B N P % Palringo P B N P % Paltalk P B N P % SIMP (Jabber) P B N P % Tencent QQ P B N P % TryFast Messenger P B N P % VZOchat P B N P % Wavago P B N P % Protocol Filter Planning Worksheet 2 of 8 Protocol filter name: Protocol Name Action Log Bandwidth Wengo P B N P % Woize P B N P % X-IM P B N P % Xfire P B N P % Yahoo! Mail Chat P B N P % Yahoo! Messenger P B N P % Instant Messaging File Attachments P B N P % AOL Instant Messenger or ICQ P B N P % attachments MSN Messenger attachments P B N P % NateOn Messenger