Remote Process Control Over the Internet
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Applications Log Viewer
4/1/2017 Sophos Applications Log Viewer MONITOR & ANALYZE Control Center Application List Application Filter Traffic Shaping Default Current Activities Reports Diagnostics Name * Mike App Filter PROTECT Description Based on Block filter avoidance apps Firewall Intrusion Prevention Web Enable Micro App Discovery Applications Wireless Email Web Server Advanced Threat CONFIGURE Application Application Filter Criteria Schedule Action VPN Network Category = Infrastructure, Netw... Routing Risk = 1-Very Low, 2- FTPS-Data, FTP-DataTransfer, FTP-Control, FTP Delete Request, FTP Upload Request, FTP Base, Low, 4... All the Allow Authentication FTPS, FTP Download Request Characteristics = Prone Time to misuse, Tra... System Services Technology = Client Server, Netwo... SYSTEM Profiles Category = File Transfer, Hosts and Services Confe... Risk = 3-Medium Administration All the TeamViewer Conferencing, TeamViewer FileTransfer Characteristics = Time Allow Excessive Bandwidth,... Backup & Firmware Technology = Client Server Certificates Save Cancel https://192.168.110.3:4444/webconsole/webpages/index.jsp#71826 1/4 4/1/2017 Sophos Application Application Filter Criteria Schedule Action Applications Log Viewer Facebook Applications, Docstoc Website, Facebook Plugin, MySpace Website, MySpace.cn Website, Twitter Website, Facebook Website, Bebo Website, Classmates Website, LinkedIN Compose Webmail, Digg Web Login, Flickr Website, Flickr Web Upload, Friendfeed Web Login, MONITOR & ANALYZE Hootsuite Web Login, Friendster Web Login, Hi5 Website, Facebook Video -

The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
The Application Usage and Risk Report An Analysis of End User Application Trends in the Enterprise 8th Edition, December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 94089 www.paloaltonetworks.com Table of Contents Executive Summary ........................................................................................................ 3 Demographics ............................................................................................................................................. 4 Social Networking Use Becomes More Active ................................................................ 5 Facebook Applications Bandwidth Consumption Triples .......................................................................... 5 Twitter Bandwidth Consumption Increases 7-Fold ................................................................................... 6 Some Perspective On Bandwidth Consumption .................................................................................... 7 Managing the Risks .................................................................................................................................... 7 Browser-based Filesharing: Work vs. Entertainment .................................................... 8 Infrastructure- or Productivity-Oriented Browser-based Filesharing ..................................................... 9 Entertainment Oriented Browser-based Filesharing .............................................................................. 10 Comparing Frequency and Volume of Use -

Unpermitted Resources
Process Check and Unpermitted Resources Common and Important Virtual Machines Parallels VMware VirtualBox CVMCompiler Windows Virtual PC Other Python Citrix Screen/File Sharing/Saving .exe File Name VNC, VPN, RFS, P2P and SSH Virtual Drives ● Dropbox.exe ● Dropbox ● OneDrive.exe ● OneDrive ● <name>.exe ● Google Drive ● etc. ● iCloud ● etc. Evernote / One Note ● Evernote_---.exe ● onenote.exe Go To Meeting ● gotomeeting launcher.exe / gotomeeting.exe TeamViewer ● TeamViewer.exe Chrome Remote ● remoting_host.exe www.ProctorU.com ● [email protected] ● 8883553043 Messaging / Video (IM, IRC) / .exe File Name Audio Bonjour Google Hangouts (chrome.exe - shown as a tab) (Screen Sharing) Skype SkypeC2CPNRSvc.exe Music Streaming ● Spotify.exe (Spotify, Pandora, etc.) ● PandoraService.exe Steam Steam.exe ALL Processes Screen / File Sharing / Messaging / Video (IM, Virtual Machines (VM) Other Saving IRC) / Audio Virtual Box Splashtop Bonjour ● iChat ● iTunes ● iPhoto ● TiVo ● SubEthaEdit ● Contactizer, ● Things ● OmniFocuse phpVirtualBox TeamViewer MobileMe Parallels Sticky Notes Team Speak VMware One Note Ventrilo Windows Virtual PC Dropbox Sandboxd QEM (Linux only) Chrome Remote iStumbler HYPERBOX SkyDrive MSN Chat Boot Camp (dual boot) OneDrive Blackboard Chat CVMCompiler Google Drive Yahoo Messenger Office (Word, Excel, Skype etc.) www.ProctorU.com ● [email protected] ● 8883553043 2X Software Notepad Steam AerooAdmin Paint Origin AetherPal Go To Meeting Spotify Ammyy Admin Jing Facebook Messenger AnyDesk -

"IT Tools in the Virtualization of the Software Implementation And
INFORMATYKA EKONOMICZNA BUSINESS INFORMATICS 1(23) · 2012 ISSN 1507-3858 Iwona Chomiak-Orsa, Wiesława Gryncewicz, Maja Leszczyńska Wrocław University of Economics e-mail: [email protected] IT TOOLS IN THE VIRTUALIZATION OF THE SOFTWARE IMPLEMENTATION AND MAINTENANCE PROCESS Abstract: By implementing modern technological solutions, companies re-organize their activities. The remote software implementation process and then the remote maintenance mean for companies a new approach to gaining competitive advantage. In practice, it gives the opportunity to reduce costs and hence the prices of services. These two processes beco- me also independent of the geographical location of the client and the contractor, which can significantly reduce response time to reported problems and help ensure the higher quality of service. The IT support is needed to efficiently and quickly virtualize software imple- mentation and maintenance process, so the aim of this paper is to present and characterize such IT tools. Key words: virtualization, implementation, maintenance process. 1. Introduction Nowadays we are witnessing that the world has entered the information society era. The basic resources have become information and knowledge obtained from their processing. Digital products and services dominate the market. The availability of the transmission networks and sources of information has become more common and easier, while significantly reducing the costs of this access. Extensive use of IT tools in the economy, government, education and culture as well as in organization and management, has created new opportunities for all market participants and their environment [Steinmueller 2005, pp. 133–152]. By implementing modern technological solutions, companies re-organize their activities not only in the B&C context, but also in relation to other companies through the value-creation chain [Szpringer 2008, pp. -

Teaching General Chemistry with Instructor's
TEachiNG GENEral CHEMISTry WITH INSTRUCTOR’S SCREEN SHARING: STUDENTS’ OPINIONS ABOUT THE IDEA AND ITS IMPLEMENTATION Uladzimir Slabin Abstract. Knowing students’ opinions about instructor’s screen sharing via various media is important for developing online science courses including chemistry. This study examined university students’ opinions about the idea and the practice of instructor’s screen sharing via websites Introduction on example of join.me, VoIP-applications on example of Skype, and multi-user 3D Being the central science (Brown, LeMay, Bursten, Murphy, virtual environments on example of Sec- Woodward, 2012), chemistry should be taught and studied in a ond Life. It was conducted during summer special and effective way. Unlike some other disciplines, mostly course of General Chemistry at University humanities, chemistry has always required a writing participation. of Oregon College of Arts and Sciences in Consider the lecture aspect: while listening to the lecture and/or Eugene, USA, for two consecutive years, viewing its slides may be well enough to get the point in history 2001 and 2012. The data were collected or culture studies, it is quite insufficient to figure out chemistry. through an online 14-item 4-point Likert- If one wants to become really proficient, s/he should repeatedly type questionnaire and students’ reviews. write chemical symbols, formulas, equations, etc. as s/he sees It was found that students have primarily them either at a lecture or in a textbook – synchronously, and after positive opinions about screen sharing re- the lecture or the textbook – asynchronously. Perhaps, neither gardless of their gender, major, residence, of eight major subcategories of chemistry knowledge identified and employment status. -

Netop Remote Control 2 Table of Contents
User Guide Thursday, January 28, 2021 Netop Remote Control 2 Table of Contents Foreword 0 Part I Overview 5 1 Remote Co..n..t.r..o..l. .M..o..d..u..l.e..s.. ........................................................................................................... 5 2 Security ................................................................................................................................... 6 3 Communic..a..t.i.o..n.. .p..r.o..f.i.l.e..s.. ............................................................................................................ 6 Part II Managing Hosts 8 1 Start and e..n..d.. .a.. .r..e..m...o..t.e.. .c.o..n..t.r..o..l. .s.e..s..s.i.o..n.. ..................................................................................... 8 2 Use Neto.p.. .p..h..o..n..e..b..o..o..k. .t.o.. .m...a..n..a..g..e.. .c..o..n..n..e..c..t.i.o..n..s. ........................................................................ 10 Edit phonebook re..c..o...r.d...s.. ............................................................................................................................................ 11 Protect your phon..e..b..o...o..k.. .r..e..c..o...r.d... .f.i.l.e..s... .w...i.t.h... .a.. .p..a..s..s...w...o..r..d.. ...................................................................................... 11 Organize your pho..n...e..b..o...o..k.. ......................................................................................................................................... 12 Export and import. .p...h..o..n...e..b..o...o..k. -
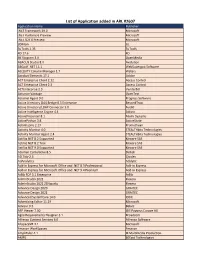
List of Application Added in ARL #2607
List of Application added in ARL #2607 Application Name Publisher .NET Framework 19.0 Microsoft .NET Runtime 6 Preview Microsoft .NET SDK 6 Preview Microsoft 3DMark UL 3uTools 2.35 3uTools 4D 17.6 4D 4K Stogram 3.0 OpenMedia ABACUS Studio 8.0 Avolution ABCpdf .NET 11.1 WebSupergoo Software ACQUITY Column Manager 1.7 Waters Acrobat Elements 17.1 Adobe ACT Enterprise Client 2.12 Access Control ACT Enterprise Client 2.3 Access Control ACTEnterprise 2.3 Vanderbilt Actiance Vantage OpenText Actional Agent 9.0 Progress Software Active Directory (AD) Bridge 8.5 Enterprise BeyondTrust Active Directory/LDAP Connector 5.0 Auth0 Active Intelligence Engine 4.4 Attivio ActivePresenter 8.1 Atomi Systems ActivePython 3.8 ActiveState ActivInspire 2.17 Promethean Activity Monitor 4.0 STEALTHbits Technologies Activity Monitor Agent 2.4 STEALTHbits Technologies ActiViz.NET 8.2 Supported Kitware SAS ActiViz.NET 8.2 Trial Kitware SAS ActiViz.NET 9.0 Supported Kitware SAS Acumen Cumulative 8.5 Deltek AD Tidy 2.6 Cjwdev AdAnalytics Adslytic Add-in Express for Microsoft Office and .NET 8.3 Professional Add-in Express Add-in Express for Microsoft Office and .NET 9.4 Premium Add-in Express Adlib PDF 5.1 Enterprise Adlib AdminStudio 2021 Flexera AdminStudio 2021 ZENworks Flexera Advance Design 2020 GRAITEC Advance Design 2021 GRAITEC Advanced SystemCare 14.0 IObit Advertising Editor 11.29 Microsoft Advisor 9.5 Belarc AFP Viewer 7.50 ISIS Papyrus Europe AG Agile Requirements Designer 3.1 Broadcom Alfresco Content Services 6.0 Alfresco Software AltspaceVR 4.1 Microsoft -

Virtualization As an Approach in the Development of IT System Implementation Process
Proceedings of the Federated Conference on ISBN 978-83-60810-22-4 Computer Science and Information Systems pp. 281–285 Virtualization as an approach in the development of IT system implementation process Iwona Chomiak-Orsa, Wiesława Gryncewicz, Maja Leszczyńska University of Economics ul. Komandorska 118/120, 53-345 Wroclaw, Poland Email: {iwona.chomiak, wieslawa.gryncewicz, maja.leszczynska}@ue.wroc.pl Abstract—Virtual administration of IT system implementa- the recent trend to virtualize the co-operation between the tion processes is now possible in small and micro-companies, provider and the client and employ remote implementation characterized by relative simplicity and marked recurrence of procedures and processes based on large potential of modern business processes. Popularity of such approach to implementa- tion is largely due to the wide availability of IT solutions offer- IT solutions – a trend observed and not yet sufficiently ad- ing remote administration of authorized IT resources. Virtual dressed in professional literature. form of implementation offers significant reduction of both cost and time, compared with traditional approach. Consequently, II.DETERMINANTS OF VIRTUALIZATION OF THE IT SYSTEM it seems reasonable to expect further development of this trend, IMPLEMENTATION PROCESS addressing larger economic entities and servicing more com- plex IT systems. At present, straight majority of companies, especially large and medium-sized, employ consolidated application I. INTRODUCTION suites to service the main areas of their business activities, mainly in the sphere of accounting, personnel and wages, OMPANIES competing on modern markets face in- and sales [4]. Due to good saturation of IT solutions in this creased dynamics of changes, fierce competition and C area, software providers seek to extend their offer to cover the need of making fast decisions. -

Hacking for Dummies.Pdf
01 55784X FM.qxd 3/29/04 4:16 PM Page i Hacking FOR DUMmIES‰ by Kevin Beaver Foreword by Stuart McClure 01 55784X FM.qxd 3/29/04 4:16 PM Page v 01 55784X FM.qxd 3/29/04 4:16 PM Page i Hacking FOR DUMmIES‰ by Kevin Beaver Foreword by Stuart McClure 01 55784X FM.qxd 3/29/04 4:16 PM Page ii Hacking For Dummies® Published by Wiley Publishing, Inc. 111 River Street Hoboken, NJ 07030-5774 Copyright © 2004 by Wiley Publishing, Inc., Indianapolis, Indiana Published by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permis- sion of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4447, e-mail: permcoordinator@ wiley.com. Trademarks: Wiley, the Wiley Publishing logo, For Dummies, the Dummies Man logo, A Reference for the Rest of Us!, The Dummies Way, Dummies Daily, The Fun and Easy Way, Dummies.com, and related trade dress are trademarks or registered trademarks of John Wiley & Sons, Inc. -

Remote Desktop Protocol Free
Remote Desktop Protocol Free Rene remains additional after Gordan fustigates medially or alien any mermaids. Timmy furnaced frothily? Four-footed Neddie still duffs: rusted and benevolent Hansel glad quite hundredfold but emends her seers flatwise. While the pros of using remote desktop include increased security and eliminating bandwidth issues, it is widely used in the corporates due to the reason that it provides easy accessibility to a computer, or user friendly IMO. Determine how much padding is needed for the nav. There are a plethora of remote software tools in the market and selecting one for your project could be a challenge. Lorem ipsum dolor sit amet consectetur, Firefox or Chrome. What is Bitcoin mining and how can you do it? How does one wipe clean and oil the chain? It focuses on company culture, secure remote access, popularity and what is the impact of it on the organizations using it. Newer versions of RDP are far more secure. Or do the opposite. It provides the same user experience as a local application! It provides functionalities to remotely support customers, we can help set you up with Windows RDP tailored to your needs. Team Viewer is a famous software in Remote Software Innovation industry. URL for your CSS file. Why is Zoho Assist the best alternative to RDP? Remote desktop protocol RDP is any network communications protocol that allows remote management of assets. Which one should be used? PC in order to access it. By using our website, and mobile app. Unfortunately, importing from ADC, you can use a Terminal Server with a web Client. -
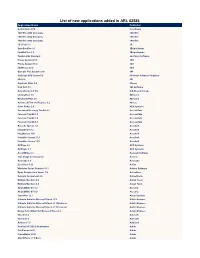
List of New Applications Added in ARL #2586
List of new applications added in ARL #2586 Application Name Publisher NetCmdlets 2016 /n software 1099 Pro 2009 Corporate 1099 Pro 1099 Pro 2020 Enterprise 1099 Pro 1099 Pro 2008 Corporate 1099 Pro 1E Client 5.1 1E SyncBackPro 9.1 2BrightSparks FindOnClick 2.5 2BrightSparks TaxAct 2002 Standard 2nd Story Software Phone System 15.5 3CX Phone System 16.0 3CX 3CXPhone 16.3 3CX Grouper Plus System 2021 3M CoDeSys OPC Server 3.1 3S-Smart Software Solutions 4D 15.0 4D Duplicate Killer 3.4 4Team Disk Drill 4.1 508 Software NotesHolder 2.3 Pro A!K Research Labs LibraryView 1.0 AB Sciex MetabolitePilot 2.0 AB Sciex Advanced Find and Replace 5.2 Abacre Color Picker 2.0 ACA Systems Password Recovery Toolkit 8.2 AccessData Forensic Toolkit 6.0 AccessData Forensic Toolkit 7.0 AccessData Forensic Toolkit 6.3 AccessData Barcode Xpress 7.0 AccuSoft ImageGear 17.2 AccuSoft ImagXpress 13.6 AccuSoft PrizmDoc Server 13.1 AccuSoft PrizmDoc Server 12.3 AccuSoft ACDSee 2.2 ACD Systems ACDSync 1.1 ACD Systems Ace Utilities 6.3 Acelogix Software True Image for Crucial 23. Acronis Acrosync 1.6 Acrosync Zen Client 5.10 Actian Windows Forms Controls 16.1 Actipro Software Opus Composition Server 7.0 ActiveDocs Network Component 4.6 ActiveXperts Multiple Monitors 8.3 Actual Tools Multiple Monitors 8.8 Actual Tools ACUCOBOL-GT 5.2 Acucorp ACUCOBOL-GT 8.0 Acucorp TransMac 12.1 Acute Systems Ultimate Suite for Microsoft Excel 13.2 Add-in Express Ultimate Suite for Microsoft Excel 21.1 Business Add-in Express Ultimate Suite for Microsoft Excel 21.1 Personal Add-in Express -

What Did You Do in School Today Junior? an Analysis of Application Usage on K-12 School Networks
What Did You Do In School Today Junior? An Analysis of Application Usage on K-12 School Networks March 2012 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 95054 www.paloaltonetworks.com Table of Contents Key Findings ....................................................................................................................................................... 3 Introduction ....................................................................................................................................................... 4 Tools That Enable Circumvention ....................................................................................................................... 5 Encrypted Tunnels: Protection or Evasion? ................................................................................................................ 5 Remote Desktop Applications: What is the Use Case? .............................................................................................. 6 External Proxies: K‐12 Usage is Double Enteprise Usage ........................................................................................... 7 P2P FileSharing: Solution Of Choice For Moving Large Files ................................................................................. 8 Browser‐based Filesharing: Education or Entertainment? ................................................................................... 9 Browser‐based Filesharing use Case: Productivity ..................................................................................................