Windows Remote Desktop Protocol
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

THINC: a Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices
THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2011 c 2011 Ricardo A. Baratto This work may be used in accordance with Creative Commons, Attribution-NonCommercial-NoDerivs License. For more information about that license, see http://creativecommons.org/licenses/by-nc-nd/3.0/. For other uses, please contact the author. ABSTRACT THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto THINC is a new virtual and remote display architecture for desktop computing. It has been designed to address the limitations and performance shortcomings of existing remote display technology, and to provide a building block around which novel desktop architectures can be built. THINC is architected around the notion of a virtual display device driver, a software-only component that behaves like a traditional device driver, but instead of managing specific hardware, enables desktop input and output to be intercepted, manipulated, and redirected at will. On top of this architecture, THINC introduces a simple, low-level, device-independent representation of display changes, and a number of novel optimizations and techniques to perform efficient interception and redirection of display output. This dissertation presents the design and implementation of THINC. It also intro- duces a number of novel systems which build upon THINC's architecture to provide new and improved desktop computing services. The contributions of this dissertation are as follows: • A high performance remote display system for LAN and WAN environments. -

Sun Secure Global Desktop 4.41 Release Notes
Sun Secure Global Desktop 4.41 Release Notes Sun Microsystems, Inc. www.sun.com Part No. 820-4905-12 August 2008, Revision 01 Submit comments about this document at: http://docs.sun.com/app/docs/form/comments Copyright 2008 Sun Microsystems, Inc., 4150 Network Circle, Santa Clara, California 95054, U.S.A. All rights reserved. Sun Microsystems, Inc. has intellectual property rights relating to technology that is described in this document. In particular, and without limitation, these intellectual property rights may include one or more of the U.S. patents listed at http://www.sun.com/patents and one or more additional patents or pending patent applications in the U.S. and in other countries. This document and the product to which it pertains are distributed under licenses restricting their use, copying, distribution, and decompilation. No part of the product or of this document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and in other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, Java, JavaScript, SunSolve, JavaServer, JSP,JDK, JRE, Sun Ray, and Solaris are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and in other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. -

The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
The Application Usage and Risk Report An Analysis of End User Application Trends in the Enterprise 8th Edition, December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 94089 www.paloaltonetworks.com Table of Contents Executive Summary ........................................................................................................ 3 Demographics ............................................................................................................................................. 4 Social Networking Use Becomes More Active ................................................................ 5 Facebook Applications Bandwidth Consumption Triples .......................................................................... 5 Twitter Bandwidth Consumption Increases 7-Fold ................................................................................... 6 Some Perspective On Bandwidth Consumption .................................................................................... 7 Managing the Risks .................................................................................................................................... 7 Browser-based Filesharing: Work vs. Entertainment .................................................... 8 Infrastructure- or Productivity-Oriented Browser-based Filesharing ..................................................... 9 Entertainment Oriented Browser-based Filesharing .............................................................................. 10 Comparing Frequency and Volume of Use -

BSD UNIX Toolbox 1000+ Commands for Freebsd, Openbsd
76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page i BSD UNIX® TOOLBOX 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iv BSD UNIX® Toolbox: 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD® Power Users Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2008 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN: 978-0-470-37603-4 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 Library of Congress Cataloging-in-Publication Data is available from the publisher. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permis- sion should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. -

Remote Process Control Over the Internet
Session 1520 Remote Process Control over the Internet Mark Smith Purdue University North Central Abstract This paper presents remote process control over the Internet using remote-control computing software. Remote-control computing software allows you to connect to remote computers from your computer and control those systems. You can monitor and control attached system processes, provide problem solving assistance, upload and download files, and even change system parameters. This paper describes what remote-control computing is, who the major players in the industry are, and how it can be used to monitor and control remote processes. A case study of remote-control computing software in operation is also presented, describing how one off-the-shelf package was setup to monitor and control a plant floor production system. Introduction Networking technologies, and especially the Internet, have become a major component of application systems. As we teach the design and implementation of process control systems in the Engineering curriculum, we must recognize that these systems will require capabilities for control and support from remote locations. For example, the need for remote control may be driven by the high cost of a particular process. The Oak Ridge National Laboratory uses remote process control at its High Temperature Materials Laboratory to allow researches from across the country to use a million-dollar electron microscope1. Even when control of the process is not required across the country, there are times when it is helpful (or even critical) to monitor another node on a LAN. For example, Conquergood describes in his research the ability to monitor and control potentially high voltages from one location by gathering voltage information from PCs doing data acquisition from various plant processes2. -

Credssp Required by Server – Solutions
CredSSP required by server – Solutions https://www.syskit.com/blog/credssp-required-b... PRODUCTS COMPANY PARTNERS CUSTOMERS SUPPORT Home > Blog > SysKit Monitor > CredSSP required by server – Solutions CredSSP required by server – Solutions Published: May 16, 2017 Published in: SysKit Monitor Author: Silvio Rahle Failed to connect, CredSSP required by server is an error line returned when trying to connect remotely to a Windows machine using RDP version 6 or newer with the Rdesktop client. It represents a frequent problem for Windows and Linux administrators alike. Rdesktop client is UNIX based client software for Microsoft’s Remote Desktop Protocol. It is commonly used on ReactOS and Linux installations to connect to Windows machines running Remote Desktop Services, which often leads to the CredSSP required by server error. Why does it happen? All Windows clients have a credential cache used for authentication against services in a network called NTLM or Windows NT LAN Manager. RDP supports SSO (single sign-on) authentication enabling a user to log in with a single ID and password to gain access to a connected system. However, Linux clients do not support this type of authentication and they require that credentials are provided, either via a Rdesktop command line or via a login window when initiating the remote session. Linux has Kerberos, which is an authentication mechanism for requesting access to 1 of 5 9/26/17, 9:38 PM CredSSP required by server – Solutions https://www.syskit.com/blog/credssp-required-b... PRODUCTS COMPANY PARTNERS CUSTOMERS SUPPORT Granting Ticket), which is used to access other services, such as RDP. -

Collabkit – a Multi-User Multicast Collaboration System Based on VNC
Humboldt-Universität zu Berlin Institut für Informatik Lehrstuhl für Rechnerorganisation und Kommunikation Diplomarbeit CollabKit – A Multi-User Multicast Collaboration System based on VNC Christian Beier 19. April 2011 Gutachter Prof. Dr. Miroslaw Malek Prof. Dr. Jens-Peter Redlich Betreuer Peter Ibach <[email protected]> Abstract Computer-supported real-time collaboration systems offer functionality to let two or more users work together at the same time, allowing them to jointly create, modify and exchange electronic documents, use applications, and share information location-independently and in real-time. For these reasons, such collaboration systems are often used in professional and academic contexts by teams of knowledge workers located in different places. But also when used as computer-supported learning environments – electronic classrooms – these systems prove useful by offering interactive multi-media teaching possibilities and allowing for location-independent collaborative learning. Commonly, computer-supported real-time collaboration systems are realised using remote desktop technology or are implemented as web applications. However, none of the examined existing commercial and academic solutions were found to support concurrent multi-user interaction in an application-independent manner. When used in low-throughput shared-medium computer networks such as WLANs or cellular networks, most of the investigated systems furthermore do not scale well with an increasing number of users, making them unsuitable for multi-user collaboration of a high number of participants in such environments. For these reasons this work focuses on the design of a collaboration system that supports concurrent multi-user interaction with standard desktop applications and is able to serve a high number of users on low-throughput shared-medium computer networks by making use of multicast data transmission. -

"IT Tools in the Virtualization of the Software Implementation And
INFORMATYKA EKONOMICZNA BUSINESS INFORMATICS 1(23) · 2012 ISSN 1507-3858 Iwona Chomiak-Orsa, Wiesława Gryncewicz, Maja Leszczyńska Wrocław University of Economics e-mail: [email protected] IT TOOLS IN THE VIRTUALIZATION OF THE SOFTWARE IMPLEMENTATION AND MAINTENANCE PROCESS Abstract: By implementing modern technological solutions, companies re-organize their activities. The remote software implementation process and then the remote maintenance mean for companies a new approach to gaining competitive advantage. In practice, it gives the opportunity to reduce costs and hence the prices of services. These two processes beco- me also independent of the geographical location of the client and the contractor, which can significantly reduce response time to reported problems and help ensure the higher quality of service. The IT support is needed to efficiently and quickly virtualize software imple- mentation and maintenance process, so the aim of this paper is to present and characterize such IT tools. Key words: virtualization, implementation, maintenance process. 1. Introduction Nowadays we are witnessing that the world has entered the information society era. The basic resources have become information and knowledge obtained from their processing. Digital products and services dominate the market. The availability of the transmission networks and sources of information has become more common and easier, while significantly reducing the costs of this access. Extensive use of IT tools in the economy, government, education and culture as well as in organization and management, has created new opportunities for all market participants and their environment [Steinmueller 2005, pp. 133–152]. By implementing modern technological solutions, companies re-organize their activities not only in the B&C context, but also in relation to other companies through the value-creation chain [Szpringer 2008, pp. -

Netop Remote Control 2 Table of Contents
User Guide Thursday, January 28, 2021 Netop Remote Control 2 Table of Contents Foreword 0 Part I Overview 5 1 Remote Co..n..t.r..o..l. .M..o..d..u..l.e..s.. ........................................................................................................... 5 2 Security ................................................................................................................................... 6 3 Communic..a..t.i.o..n.. .p..r.o..f.i.l.e..s.. ............................................................................................................ 6 Part II Managing Hosts 8 1 Start and e..n..d.. .a.. .r..e..m...o..t.e.. .c.o..n..t.r..o..l. .s.e..s..s.i.o..n.. ..................................................................................... 8 2 Use Neto.p.. .p..h..o..n..e..b..o..o..k. .t.o.. .m...a..n..a..g..e.. .c..o..n..n..e..c..t.i.o..n..s. ........................................................................ 10 Edit phonebook re..c..o...r.d...s.. ............................................................................................................................................ 11 Protect your phon..e..b..o...o..k.. .r..e..c..o...r.d... .f.i.l.e..s... .w...i.t.h... .a.. .p..a..s..s...w...o..r..d.. ...................................................................................... 11 Organize your pho..n...e..b..o...o..k.. ......................................................................................................................................... 12 Export and import. .p...h..o..n...e..b..o...o..k. -

Download Article
Advances in Computer Science Research (ACRS), volume 54 International Conference on Computer Networks and Communication Technology (CNCT2016) Research and Implementation of RDP Proxy Proxy-based Audit System 1 2, 3 Xiao-Liang ZHANG , Xiao-Yu WU and Wu-Xia ZHANG 1,2,3 School of Computer Science and Technology North China Electric Power University Beijing, China [email protected] Keywords: RDP protocol, The agency agreement, The audit system, The operation playback, Security. Abstract. Using the Windows RDP protocol developed by Microsoft Inc to connect and operate the remote machines which base on the same system become a trend. However, the RDP has caused many security problems. It is necessary to design and implement a audit system to ensure the system’s security and guarantee the machines run correctly. It points out improper methods than before and accomplishes the RDP proxy proxy-based audit system to solve the problems. Introduction The expansion of Business Scale have a influence on the working place and implementation in the different workplaces. The operator operate the remote servers in accordance with RDP protocol. RDP provides a graphical interface to help the maintain staffs interact with the remote server system. In comparison to the former, the operations become easier and the efficiency of workers' operation become better[1]. Using the remote desktop client we can connect any server that support the remote control and can decrease the workload. Remote desktop procedure just convey the information of the user’s mouse, keyboard and other device to the remote server system and never involved in the data processing, so that the level of hardware requirements commonly. -
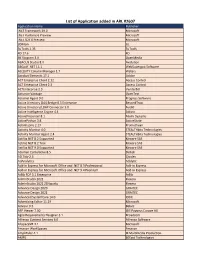
List of Application Added in ARL #2607
List of Application added in ARL #2607 Application Name Publisher .NET Framework 19.0 Microsoft .NET Runtime 6 Preview Microsoft .NET SDK 6 Preview Microsoft 3DMark UL 3uTools 2.35 3uTools 4D 17.6 4D 4K Stogram 3.0 OpenMedia ABACUS Studio 8.0 Avolution ABCpdf .NET 11.1 WebSupergoo Software ACQUITY Column Manager 1.7 Waters Acrobat Elements 17.1 Adobe ACT Enterprise Client 2.12 Access Control ACT Enterprise Client 2.3 Access Control ACTEnterprise 2.3 Vanderbilt Actiance Vantage OpenText Actional Agent 9.0 Progress Software Active Directory (AD) Bridge 8.5 Enterprise BeyondTrust Active Directory/LDAP Connector 5.0 Auth0 Active Intelligence Engine 4.4 Attivio ActivePresenter 8.1 Atomi Systems ActivePython 3.8 ActiveState ActivInspire 2.17 Promethean Activity Monitor 4.0 STEALTHbits Technologies Activity Monitor Agent 2.4 STEALTHbits Technologies ActiViz.NET 8.2 Supported Kitware SAS ActiViz.NET 8.2 Trial Kitware SAS ActiViz.NET 9.0 Supported Kitware SAS Acumen Cumulative 8.5 Deltek AD Tidy 2.6 Cjwdev AdAnalytics Adslytic Add-in Express for Microsoft Office and .NET 8.3 Professional Add-in Express Add-in Express for Microsoft Office and .NET 9.4 Premium Add-in Express Adlib PDF 5.1 Enterprise Adlib AdminStudio 2021 Flexera AdminStudio 2021 ZENworks Flexera Advance Design 2020 GRAITEC Advance Design 2021 GRAITEC Advanced SystemCare 14.0 IObit Advertising Editor 11.29 Microsoft Advisor 9.5 Belarc AFP Viewer 7.50 ISIS Papyrus Europe AG Agile Requirements Designer 3.1 Broadcom Alfresco Content Services 6.0 Alfresco Software AltspaceVR 4.1 Microsoft -

Virtualization As an Approach in the Development of IT System Implementation Process
Proceedings of the Federated Conference on ISBN 978-83-60810-22-4 Computer Science and Information Systems pp. 281–285 Virtualization as an approach in the development of IT system implementation process Iwona Chomiak-Orsa, Wiesława Gryncewicz, Maja Leszczyńska University of Economics ul. Komandorska 118/120, 53-345 Wroclaw, Poland Email: {iwona.chomiak, wieslawa.gryncewicz, maja.leszczynska}@ue.wroc.pl Abstract—Virtual administration of IT system implementa- the recent trend to virtualize the co-operation between the tion processes is now possible in small and micro-companies, provider and the client and employ remote implementation characterized by relative simplicity and marked recurrence of procedures and processes based on large potential of modern business processes. Popularity of such approach to implementa- tion is largely due to the wide availability of IT solutions offer- IT solutions – a trend observed and not yet sufficiently ad- ing remote administration of authorized IT resources. Virtual dressed in professional literature. form of implementation offers significant reduction of both cost and time, compared with traditional approach. Consequently, II.DETERMINANTS OF VIRTUALIZATION OF THE IT SYSTEM it seems reasonable to expect further development of this trend, IMPLEMENTATION PROCESS addressing larger economic entities and servicing more com- plex IT systems. At present, straight majority of companies, especially large and medium-sized, employ consolidated application I. INTRODUCTION suites to service the main areas of their business activities, mainly in the sphere of accounting, personnel and wages, OMPANIES competing on modern markets face in- and sales [4]. Due to good saturation of IT solutions in this creased dynamics of changes, fierce competition and C area, software providers seek to extend their offer to cover the need of making fast decisions.