What Did You Do in School Today Junior? an Analysis of Application Usage on K-12 School Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Adobe Application Manager Enterprise Edition Deployment Guide
ADOBE® APPLICATION MANAGER ENTERPRISE EDITION GUIDE DE DEPLOIEMENT EN ENTREPRISE Adobe® Application Manager Enterprise Edition version 3.1 Version de document 3.1 Date du document : Septembre 2012 © 2012 Adobe Systems Incorporated and its licensors. All rights reserved. Adobe® Application Manager Enterprise Edition Guide de déploiement en entreprise This guide is licensed for use under the terms of the Creative Commons Attribution Non-Commercial 3.0 License. This License allows users to copy, distribute, and transmit the guide for noncommercial purposes only so long as (1) proper attribution to Adobe is given as the owner of the guide; and (2) any reuse or distribution of the guide contains a notice that use of the guide is governed by these terms. The best way to provide notice is to include the following link. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc-sa/3.0/ Adobe, the Adobe logo, Acrobat, Adobe Audition, Adobe Bridge, Adobe Device Central, Adobe OnLocation, Adobe Premiere, Adobe Premiere Pro, Adobe Technical Communication Suite, After Effects, Contribute, Captivate, Creative Suite, CS Live, Dreamweaver, Encore, Fireworks, Flash, Flash Builder, Flash Catalyst, FrameMaker, Illustrator, InDesign, Photoshop, RoboHelp, SiteCatalyst, and Soundbooth are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. Apple, Mac, and Mac OS are trademarks of Apple Inc., registered in the United States and other countries. Microsoft, Windows, and Windows Vista are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. UNIX is a registered trademark of The Open Group in the US and other countries. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

THINC: a Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices
THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2011 c 2011 Ricardo A. Baratto This work may be used in accordance with Creative Commons, Attribution-NonCommercial-NoDerivs License. For more information about that license, see http://creativecommons.org/licenses/by-nc-nd/3.0/. For other uses, please contact the author. ABSTRACT THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto THINC is a new virtual and remote display architecture for desktop computing. It has been designed to address the limitations and performance shortcomings of existing remote display technology, and to provide a building block around which novel desktop architectures can be built. THINC is architected around the notion of a virtual display device driver, a software-only component that behaves like a traditional device driver, but instead of managing specific hardware, enables desktop input and output to be intercepted, manipulated, and redirected at will. On top of this architecture, THINC introduces a simple, low-level, device-independent representation of display changes, and a number of novel optimizations and techniques to perform efficient interception and redirection of display output. This dissertation presents the design and implementation of THINC. It also intro- duces a number of novel systems which build upon THINC's architecture to provide new and improved desktop computing services. The contributions of this dissertation are as follows: • A high performance remote display system for LAN and WAN environments. -

Volume 2014, No. 1 Law Office Computing Page Puritas Springs Software Law Office Computing
Volume 2014, No. 1 Law Office Computing Page Puritas Springs Software Law Office Computing VOLUME 2014 NO. 1 $ 7 . 9 9 PURITAS SPRINGS SOFTWARE Best Home Pages We think the importance of the through which you accessed INSIDE THIS ISSUE: home page has been greatly the world wide web. Once 1-3 reduced due to the invention of tabbed browsers arrived on the tabbed browsers. Although scene it was possible to create 1,4,5 conceived a group of 4 earlier in 1988, home pages Digital Inklings 6,7 tabbed brows- with each page Child Support 8 ing didn’t go being able to Spousal Support 10 mainstream “specialize” in a Uniform DR Forms 12 until the re- specific area of lease of Micro- your interest. Family Law Documents 13 soft’s Windows Take the Probate Forms 14 Internet Ex- weather for Ohio Estate Tax 16 plorer 7 in example. Every U.S. Income Tax (1041) 18 2006. Until then, your Home good home page should have Ohio Fiduciary Tax 19 page was the sole portal a minimal weather information; (Continued on page 2) Ohio Adoption Forms 20 OH Guardianship Forms 21 OH Wrongful Death 22 Loan Amortizer 23 # More Law Office Tech Tips Advanced Techniques 24 Deed & Document Pro 25 Bankruptcy Forms 26 XX. Quick Launch. The patch the application that you’re Law Office Management 28 of little icons to the right of the working in is maximized. If OH Business Forms 30 Start button is called the Quick you’re interested, take a look Launch toolbar. Sure, you can at the sidebar on page XX of Business Dissolutions 31 put much-used shortcuts on this issue. -

Strategic Use of Ict and Communication Tools
02/2021 STRATEGIC USE OF ICT AND COMMUNICATION TOOLS CE RESPONSIBLE | BRODTO | Branimir Radaković Module I - ICT Module II - Module III - tools for Social media Impact tools optimization of working for for SEs everyday work social enterprise TAKING COOPERATION FORWARD 2 Module I - ICT tools for optimization of everyday work Project management / work tracking tools Project management tools in this case mean delegating tasks and internal project segmenting, but most of the chosen categories below can be characterised as project management tools as well. They are a must for a modern company or organization, especially for working remotely. They improve work tracking by superiors or peers, but also allows team members to organize their work in an easy and effective way. Considering the nature of a social enterprise and heterogenic business elements, they are highly recommendable. a) Asana b) Basecamp c) ProofHub d) Trello e) Airtable TAKING COOPERATION FORWARD 3 Module I - ICT tools for optimization of everyday work Project management / work tracking tools Asana Description - a web and mobile application designed to help teams organize, track, and manage work - project management, task management and delegation, productivity software Key features: - categorized by projects - every member has his or her own “profile” viewable by others - task can also be viewed in calendar mode which gives extra plainness in work organisation Pros: - combining factors as file storage, collaboration - helping to manage projects without email Cons: - free version -

Test-Beds and Guidelines for Securing Iot Products and for Secure Set-Up Production Environments
IoT4CPS – Trustworthy IoT for CPS FFG - ICT of the Future Project No. 863129 Deliverable D7.4 Test-beds and guidelines for securing IoT products and for secure set-up production environments The IoT4CPS Consortium: AIT – Austrian Institute of Technology GmbH AVL – AVL List GmbH DUK – Donau-Universit t Krems I!AT – In"neon Technologies Austria AG #KU – JK Universit t Lin$ / Institute for &ervasive 'om(uting #) – Joanneum )esearch !orschungsgesellschaft mbH *+KIA – No,ia -olutions an. Net/or,s 0sterreich GmbH *1& – *1& -emicon.uctors Austria GmbH -2A – -2A )esearch GmbH -)!G – -al$burg )esearch !orschungsgesellschaft -''H – -oft/are 'om(etence 'enter Hagenberg GmbH -AG0 – -iemens AG 0sterreich TTTech – TTTech 'om(utertechni, AG IAIK – TU Gra$ / Institute for A((lie. Information &rocessing an. 'ommunications ITI – TU Gra$ / Institute for Technical Informatics TU3 – TU 3ien / Institute of 'om(uter 4ngineering 1*4T – 1-Net -ervices GmbH © Copyright 2020, the Members of the IoT4CPS Consortium !or more information on this .ocument or the IoT5'&- (ro6ect, (lease contact8 9ario Drobics7 AIT Austrian Institute of Technology7 mario:.robics@ait:ac:at IoT4C&- – <=>?@A Test-be.s an. guidelines for securing IoT (ro.ucts an. for secure set-up (ro.uction environments Dissemination level8 &U2LI' Document Control Title8 Test-be.s an. gui.elines for securing IoT (ro.ucts an. for secure set-u( (ro.uction environments Ty(e8 &ublic 4.itorBsC8 Katharina Kloiber 4-mail8 ,,;D-net:at AuthorBsC8 Katharina Kloiber, Ni,olaus DEr,, -ilvio -tern )evie/erBsC8 -te(hanie von )E.en, Violeta Dam6anovic, Leo Ha((-2otler Doc ID8 DF:5 Amendment History Version Date Author Description/Comments VG:? ?>:G?:@G@G -ilvio -tern Technology Analysis VG:@ ?G:G>:@G@G -ilvio -tern &ossible )esearch !iel.s for the -2I--ystem VG:> >?:G<:@G@G Katharina Kloiber Initial version (re(are. -

The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
The Application Usage and Risk Report An Analysis of End User Application Trends in the Enterprise 8th Edition, December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 94089 www.paloaltonetworks.com Table of Contents Executive Summary ........................................................................................................ 3 Demographics ............................................................................................................................................. 4 Social Networking Use Becomes More Active ................................................................ 5 Facebook Applications Bandwidth Consumption Triples .......................................................................... 5 Twitter Bandwidth Consumption Increases 7-Fold ................................................................................... 6 Some Perspective On Bandwidth Consumption .................................................................................... 7 Managing the Risks .................................................................................................................................... 7 Browser-based Filesharing: Work vs. Entertainment .................................................... 8 Infrastructure- or Productivity-Oriented Browser-based Filesharing ..................................................... 9 Entertainment Oriented Browser-based Filesharing .............................................................................. 10 Comparing Frequency and Volume of Use -
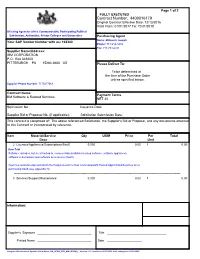
Contract Number: 4400016179
Page 1 of 2 FULLY EXECUTED Contract Number: 4400016179 Original Contract Effective Date: 12/13/2016 Valid From: 01/01/2017 To: 12/31/2018 All using Agencies of the Commonwealth, Participating Political Subdivision, Authorities, Private Colleges and Universities Purchasing Agent Name: Millovich Joseph Your SAP Vendor Number with us: 102380 Phone: 717-214-3434 Fax: 717-783-6241 Supplier Name/Address: IBM CORPORATION P.O. Box 643600 PITTSBURGH PA 15264-3600 US Please Deliver To: To be determined at the time of the Purchase Order unless specified below. Supplier Phone Number: 7175477069 Contract Name: Payment Terms IBM Software & Related Services NET 30 Solicitation No.: Issuance Date: Supplier Bid or Proposal No. (if applicable): Solicitation Submission Date: This contract is comprised of: The above referenced Solicitation, the Supplier's Bid or Proposal, and any documents attached to this Contract or incorporated by reference. Item Material/Service Qty UOM Price Per Total Desc Unit 2 Licenses/Appliances/Subscriptions/SaaS 0.000 0.00 1 0.00 Item Text Software: includes, but is not limited to, commercially available licensed software, software appliances, software subscriptions and software as a service (SaaS). Agencies must develop and attach the Requirements for Non-Commonwealth Hosted Applications/Services when purchasing SaaS (see Appendix H). -------------------------------------------------------------------------------------------------------------------------------------------------------- 3 Services/Support/Maintenance 0.000 0.00 -

Remote Process Control Over the Internet
Session 1520 Remote Process Control over the Internet Mark Smith Purdue University North Central Abstract This paper presents remote process control over the Internet using remote-control computing software. Remote-control computing software allows you to connect to remote computers from your computer and control those systems. You can monitor and control attached system processes, provide problem solving assistance, upload and download files, and even change system parameters. This paper describes what remote-control computing is, who the major players in the industry are, and how it can be used to monitor and control remote processes. A case study of remote-control computing software in operation is also presented, describing how one off-the-shelf package was setup to monitor and control a plant floor production system. Introduction Networking technologies, and especially the Internet, have become a major component of application systems. As we teach the design and implementation of process control systems in the Engineering curriculum, we must recognize that these systems will require capabilities for control and support from remote locations. For example, the need for remote control may be driven by the high cost of a particular process. The Oak Ridge National Laboratory uses remote process control at its High Temperature Materials Laboratory to allow researches from across the country to use a million-dollar electron microscope1. Even when control of the process is not required across the country, there are times when it is helpful (or even critical) to monitor another node on a LAN. For example, Conquergood describes in his research the ability to monitor and control potentially high voltages from one location by gathering voltage information from PCs doing data acquisition from various plant processes2. -

Unpermitted Resources
Process Check and Unpermitted Resources Common and Important Virtual Machines Parallels VMware VirtualBox CVMCompiler Windows Virtual PC Other Python Citrix Screen/File Sharing/Saving .exe File Name VNC, VPN, RFS, P2P and SSH Virtual Drives ● Dropbox.exe ● Dropbox ● OneDrive.exe ● OneDrive ● <name>.exe ● Google Drive ● etc. ● iCloud ● etc. Evernote / One Note ● Evernote_---.exe ● onenote.exe Go To Meeting ● gotomeeting launcher.exe / gotomeeting.exe TeamViewer ● TeamViewer.exe Chrome Remote ● remoting_host.exe www.ProctorU.com ● [email protected] ● 8883553043 Messaging / Video (IM, IRC) / .exe File Name Audio Bonjour Google Hangouts (chrome.exe - shown as a tab) (Screen Sharing) Skype SkypeC2CPNRSvc.exe Music Streaming ● Spotify.exe (Spotify, Pandora, etc.) ● PandoraService.exe Steam Steam.exe ALL Processes Screen / File Sharing / Messaging / Video (IM, Virtual Machines (VM) Other Saving IRC) / Audio Virtual Box Splashtop Bonjour ● iChat ● iTunes ● iPhoto ● TiVo ● SubEthaEdit ● Contactizer, ● Things ● OmniFocuse phpVirtualBox TeamViewer MobileMe Parallels Sticky Notes Team Speak VMware One Note Ventrilo Windows Virtual PC Dropbox Sandboxd QEM (Linux only) Chrome Remote iStumbler HYPERBOX SkyDrive MSN Chat Boot Camp (dual boot) OneDrive Blackboard Chat CVMCompiler Google Drive Yahoo Messenger Office (Word, Excel, Skype etc.) www.ProctorU.com ● [email protected] ● 8883553043 2X Software Notepad Steam AerooAdmin Paint Origin AetherPal Go To Meeting Spotify Ammyy Admin Jing Facebook Messenger AnyDesk -

Collabkit – a Multi-User Multicast Collaboration System Based on VNC
Humboldt-Universität zu Berlin Institut für Informatik Lehrstuhl für Rechnerorganisation und Kommunikation Diplomarbeit CollabKit – A Multi-User Multicast Collaboration System based on VNC Christian Beier 19. April 2011 Gutachter Prof. Dr. Miroslaw Malek Prof. Dr. Jens-Peter Redlich Betreuer Peter Ibach <[email protected]> Abstract Computer-supported real-time collaboration systems offer functionality to let two or more users work together at the same time, allowing them to jointly create, modify and exchange electronic documents, use applications, and share information location-independently and in real-time. For these reasons, such collaboration systems are often used in professional and academic contexts by teams of knowledge workers located in different places. But also when used as computer-supported learning environments – electronic classrooms – these systems prove useful by offering interactive multi-media teaching possibilities and allowing for location-independent collaborative learning. Commonly, computer-supported real-time collaboration systems are realised using remote desktop technology or are implemented as web applications. However, none of the examined existing commercial and academic solutions were found to support concurrent multi-user interaction in an application-independent manner. When used in low-throughput shared-medium computer networks such as WLANs or cellular networks, most of the investigated systems furthermore do not scale well with an increasing number of users, making them unsuitable for multi-user collaboration of a high number of participants in such environments. For these reasons this work focuses on the design of a collaboration system that supports concurrent multi-user interaction with standard desktop applications and is able to serve a high number of users on low-throughput shared-medium computer networks by making use of multicast data transmission. -

542132 Iphone FL 3E.Indb 1 11/2/09 6:44:00 PM Index
COPYRIGHTED MATERIAL 542132 iPhone FL 3E.indb 1 11/2/09 6:44:00 PM Index •A• AnyDVD 37 AOL Radio 193 AAC Apocalypse Now — Redux Edition 40 See file formats, AAC Apple Lossless AAC Encoder 30 See file formats, Apple Lossless Abbyy Applian Technologies FineReader Express 87 Media Catcher 204, 205 ABC News: Nightline 156 Replay A/V 185, 187, 189 ABC World News 162 Replay Capture Suite 185, 187, 202 Abraham, F. Murray 32 Replay Converter 202 Across Lite (.puz) Are We Alone? 162 See file formats, Across Lite (.puz) Asylum Street Spankers 180, 192 Adams, Douglas 187 ATSC television signals 60 Address Book 225, 227 AT&T 65 Adobe Systems Audacity 47, 49, 50 Premiere Elements 56 audio ADVC-110 55 converting text to 150 aggregators 131 file capture 18 4 AIFF audiobooks See file formats, AIFF creating 151 Air Sharing Pro 141, 142, 215, 217, 221 Audio Hijack Pro 186, 187 All the King’s Men 42 audio streaming Amazon.com 78, 82, 171, 178 See streaming, audio Kindle 78, 79 Automator 151 Kindle iPhone app 78, 79 Avatron Software Amazon Kindle Air Sharing Pro 141, 142, 215, 217, 221 See file formats, Amazon Kindle Avid Technologies 55 Amazon MP3 Store 171, 178 American Idol 73 American Library Association 172 •B• Amnesty International 45 Bach, Steven 88 255 542132 iPhone FL 3E.indb 2 11/2/09 6:44:00 PM Index Bad Astronomy 121 cassettes Battlestar Galactica 29 importing BBC 45, 184, 187 See importing, cassettes Beatles on Panpipes, The 28 CBR Beatles, The 28 , 53 See file formats, CBR Beethoven, Ludwig van 197 CBZ Bento 245 See file formats, CBZ Bezos,