RESEARCH INSIGHTS – Hardware Design: FPGA Security Risks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
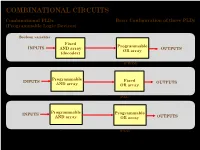
COMBINATIONAL CIRCUITS Combinational Plds Basic Configuration of Three Plds (Programmable Logic Devices)
COMBINATIONAL CIRCUITS Combinational PLDs Basic Configuration of three PLDs (Programmable Logic Devices) Boolean variables Fixed Programmable INPUTS AND array OUTPUTS OR array (decoder) Programmable Read-Only Memory (PROM) Programmable INPUTS Fixed OUTPUTS AND array OR array Programmable Array Logic (PAL) Programmable INPUTS Programmable AND array OR array OUTPUTS (Field) Programmable Logic Array (PLA) 1 ©Loberg COMBINATIONAL CIRCUITS Combinational PLDs Two-level AND-OR Arrays (Programmable Logic Devices) F (C,B, A) = CBA + CB A A AND B + V B C A C B F C F AND F + V 1 B OR C Multiple functions Simplified equivalent circuit for two-level AND-OR array 2 ©Loberg COMBINATIONAL CIRCUITS Combinational PLDs Field-programmable AND and OR Arrays (Programmable Logic Devices) Field-programmable logic elements are devices that contain uncommitted AND/OR arrays that are (programmed) configured by the designer. + V + V A A F (C,B, A) F (C,B, A) = CBA B B C C Unprogrammed AND array Fuse can be "blown" by passing a high current through it. 3 ©Loberg COMBINATIONAL CIRCUITS Combinational PLDs Field-programmable AND and OR Arrays (Programmable Logic Devices) F (P1 ,P2 ,P3 ) = P1 + P3 P1 P1 P2 P2 P3 P3 F F (P1 ,P2 ,P3 ) Unprogrammed OR array Programmed OR array P1 P2 P3 P1 + P3 4 ©Loberg COMBINATIONAL CIRCUITS Combinational PLDs Output Polarity Options (Programmable Logic Devices) I1 Ik Active high Active low Complementary outputs Programmable polarity P P 1 m + V 5 ©Loberg COMBINATIONAL CIRCUITS Combinational PLDs Bidirectional Pins and Feed back Lines (Programmable Logic Devices) I1 Ik Feedback IOm Three-state driver 6 ©Loberg COMBINATIONAL CIRCUITS Combinational PLDs PLA (Programmable Logic Array) (Programmable Logic Devices) If we use ROM to implement the Boolean function we will waste the silicon area. -

Development of a Programmable Array Logic
i DEVELOPMENT OF A PROGRAMMABLE ARRAY LOGIC PROGRAMMER USING A HOME COMPUTER by GERT DANIEL JORDAAN Dissertation submitted in compliance with the requirements for the MASTER'S DIPLOMA in TECHNOLOGY in the Department of Electronics at the TECHNIKON O. F . S . OCTOBER, 1988. Supervisor: Prof. F.W. Bruwer Co-supervisor: Mr. B. de Witt © Central University of Technology, Free State ACKNOWLEDGEMENTS I would like to thank the following persons without whose help this project could hardly have been completed: The supervisor, prof. F.W. Bruwer, and co-supervisor, mr. 8. de Witt, for help and guidance during the course of the project. Mr. H.F. Coetzer for technical as well as philolog ical assistance. It is really appreciated that time could be found in his very full schedule, for this assistance. Dr. C.A.J. van Rensburg for his per_onal interest in the research project and for continuous encouragement and help. Dr. J. van der Mer-we for his assistance - in particular with respect to the registration and other administrative aspects of the project. / Miss M. du Toit who was largely responsible for the word processing. For the guidance provided by my parents and the opportuni- ties which they afforded me. My children, Tania, Johan, Madelie and Lourens,. whose main contribution was to have to forego much of my attention and time for such a long period. Last, but not least, my wife, Christa, for her encouragement and understanding. © Central University of Technology,ii Free State CONTENTS PAGE Cilapter 1 1 Intr--oduc tion 1.1 Recent Trends in Electronics 1 1.2 Problem Investigated 1 1.3 Development of PAL Programmer 3 1.3.1 Generation of Fuse Map 3 1.3.2 Programming of Programmable Array Logic 3 Devices 1 . -

Design of a Rad-Hard Efuse Trimming Circuit For
Master Thesis 2018 DESIGN OF A RAD-HARD EFUSE TRIMMING CIRCUIT FOR BANDGAP VOLTAGE REFERENCE FOR LHC EXPERIMENTS UPGRADES Supervisors: Student: Prof. Maher Kayal1 Mustafa Beşirli Dr. Adil Koukab1 Dr. Stefano Michelis2 CERN-THESIS-2018-084 28/06/2018 1School of Engineering (STI), Electronics Laboratory (ELAB), EPFL. 2Experimental Physics Department, Microelectronics Section (EP-ESE-ME), CERN. Electronics Laboratory, STI/ELAB Electrical and Electronic Engineering Section 22 June 2018 2 ACKNOWLEDGEMENTS At the end of the two years of my master’s studies, I would like to thank all the people who supported me during this significant period of my life. First, I would like to thank Prof. Maher Kayal for having given me the chance to work in ELAB and I would like to express my gratitude to Prof. Adil Koukab for having given me the opportunity to work in collaboration with CERN and for supervising my thesis. I would like to express my appreciation to Stefano Michelis for his constant help and precious advices during the development of this project and for providing me vast amount of knowledge on rad-hard analog design. I would also like to thank Federico Faccio for his valuable advices and I would like to express my gratitude to Giacomo Ripamonti for his consistent support during the design and test of my chip. These years were very important for my professional career and personal development. I would like to thank all my friends at EPFL and at CERN; it was nice to meet them. I would also like to express my gratitude to my friends in Turkey for their consistent supports. -

VLSI Design: a New Approach
International Journal of Information Theory Volume 1, Issue 1, 2011, pp-01-04 Available online at: http://www.bioinfo.in/contents.php?id=103 VLSI Design: A New Approach M.B. Swami and V.P. Pawar Department of Physics/Electronics/Computer Science, Maharashtra Udyagiri Mahavidyalaya, Udgir, India e-mail: [email protected] Abstract—This paper presents the different • Cores such as PCI are available and able to Programmable Logic Array is an important building circuit integrate with relative ease Getting started in of VLSI chips and some of the FPGA architectures have FPGA design is easy. evolved from the basic Programmable Logic Array The tools are cheap (and sometimes free) for low- architectures. In this paper the new concepts of Verilog Hardware Description language is included in VLSI Design. end devices and affordable for the high end. Modern Keywords: Programmable Logic Array, FPGA, Verilog. HDL (hardware design language) environments are very powerful for creating and verifying a design. There I. INTRODUCTION is plenty of documentation available for using different vendor’s FPGA design tools and exploiting features of Very-large-scale integration (VLSI) is the process of different FPGAs. creating integrated circuits by combining thousands of Even with modern tools, the fundamentals of transistor-based circuits into a single chip. digital design still remain intact and must be Implementation is based on FPGA design flow with understood. If the fundamentals are ignored, there is a Xilinx tools which will help you to design complex good chance that your design will not work consistently digital systems using HDL and also to get experience of and will probably exhibit intermittent modes of processor and controller implementations on FPGAs. -

Introduction to ASIC Design
’14EC770 : ASIC DESIGN’ An Introduction Application - Specific Integrated Circuit Dr.K.Kalyani AP, ECE, TCE. 1 VLSI COMPANIES IN INDIA • Motorola India – IC design center • Texas Instruments – IC design center in Bangalore • VLSI India – ASIC design and FPGA services • VLSI Software – Design of electronic design automation tools • Microchip Technology – Offers VLSI CMOS semiconductor components for embedded systems • Delsoft – Electronic design automation, digital video technology and VLSI design services • Horizon Semiconductors – ASIC, VLSI and IC design training • Bit Mapper – Design, development & training • Calorex Institute of Technology – Courses in VLSI chip design, DSP and Verilog HDL • ControlNet India – VLSI design, network monitoring products and services • E Infochips – ASIC chip design, embedded systems and software development • EDAIndia – Resource on VLSI design centres and tutorials • Cypress Semiconductor – US semiconductor major Cypress has set up a VLSI development center in Bangalore • VDAT 2000 – Info on VLSI design and test workshops 2 VLSI COMPANIES IN INDIA • Sandeepani – VLSI design training courses • Sanyo LSI Technology – Semiconductor design centre of Sanyo Electronics • Semiconductor Complex – Manufacturer of microelectronics equipment like VLSIs & VLSI based systems & sub systems • Sequence Design – Provider of electronic design automation tools • Trident Techlabs – Power systems analysis software and electrical machine design services • VEDA IIT – Offers courses & training in VLSI design & development • Zensonet Technologies – VLSI IC design firm eg3.com – Useful links for the design engineer • Analog Devices India Product Development Center – Designs DSPs in Bangalore • CG-CoreEl Programmable Solutions – Design services in telecommunications, networking and DSP 3 Physical Design, CAD Tools. • SiCore Systems Pvt. Ltd. 161, Greams Road, ... • Silicon Automation Systems (India) Pvt. Ltd. ( SASI) ... • Tata Elxsi Ltd. -

5V/12V Efuse with Over Voltage Protection and Blocking FET Control Check for Samples: TPS2592AA, TPS2592AL, TPS2592BA, TPS2592BL, TPS2592ZA
TPS2592AA, TPS2592AL TPS2592BA, TPS2592BL TPS2592ZA www.ti.com SLVSC11B –JUNE 2013–REVISED NOVEMBER 2013 5V/12V eFuse with Over Voltage Protection and Blocking FET Control Check for Samples: TPS2592AA, TPS2592AL, TPS2592BA, TPS2592BL, TPS2592ZA 1FEATURES APPLICATIONS 2• 12 V eFuse – TPS2592Ax • HDD and SSD Drives • 5 V eFuse – TPS2592Bx • Set Top Boxes • 4.5 V – 18 V Protection – TPS2592Zx • Servers / AUX Supplies • Integrated 28mΩ Pass MOSFET • Fan Control • Fixed Over-Voltage Clamp (TPS2592Ax/Bx) • PCI/PCIe Cards • Absolute Maximum Voltage of 20V • Switches/Routers • 2 A to 5 A Adjustable I (±15% Accuracy) LIMIT PRODUCT INFORMATION(1) • Reverse Current Blocking Support FAULT PART NO UV OV CLAMP Status • Programmable OUT Slew Rate, UVLO RESPONSE • Built-in Thermal Shutdown TPS2592AA 4.3 V 15 V Auto Retry Active • UL Recognition Pending TPS2592BA 4.3 V 6.1 V Auto Retry Active TPS2592AL 4.3 V 15 V Latched Active • Safe during Single Point Failure Test TPS2592BL 4.3 V 6.1 V Latched Active (UL60950) TPS2592ZA 4.3 V — Auto-retry Active • Small Foot Print – 10L (3mm x 3mm) VSON TPS2592ZL 4.3 V — Latched Preview (1) For the most current package and ordering information, see the Package Option Addendum at the end of this document, or see the TI web site at www.ti.com DESCRIPTION The TPS2592xx family of eFuses is a highly integrated circuit protection and power management solution in a tiny package. The devices use few external components and provide multiple protection modes. They are a robust defense against overloads, shorts circuits, voltage surges, excessive inrush current, and reverse current. -

Design of Variation-Tolerant Circuits for Nanometer CMOS Technology: Circuits and Architecture Co-Design
Design of Variation-Tolerant Circuits for Nanometer CMOS Technology: Circuits and Architecture Co-Design by Mohamed Hassan Abu-Rahma A thesis presented to the University of Waterloo in ful¯llment of the thesis requirement for the degree of Doctor of Philosophy in Electrical and Computer Engineering Waterloo, Ontario, Canada, 2008 °c Mohamed Hassan Abu-Rahma 2008 I hereby declare that I am the sole author of this thesis. This is a true copy of the thesis, including any required ¯nal revisions, as accepted by my examiners. I understand that my thesis may be made electronically available to the public. ii Abstract Aggressive scaling of CMOS technology in sub-90nm nodes has created huge challenges. Variations due to fundamental physical limits, such as random dopants fluctuation (RDF) and line edge roughness (LER) are increasing signi¯cantly with technology scaling. In addition, manufacturing tolerances in process technology are not scaling at the same pace as transistor's channel length due to process control limitations (e.g., sub-wavelength lithography). Therefore, within-die process varia- tions worsen with successive technology generations. These variations have a strong impact on the maximum clock frequency and leakage power for any digital circuit, and can also result in functional yield losses in variation-sensitive digital circuits (such as SRAM). Moreover, in nanometer technologies, digital circuits show an in- creased sensitivity to process variations due to low-voltage operation requirements, which are aggravated by the strong demand for lower power consumption and cost while achieving higher performance and density. It is therefore not surprising that the International Technology Roadmap for Semiconductors (ITRS) lists variability as one of the most challenging obstacles for IC design in nanometer regime. -

The Basics of Logic Design
C APPENDIX The Basics of Logic Design C.1 Introduction C-3 I always loved that C.2 Gates, Truth Tables, and Logic word, Boolean. Equations C-4 C.3 Combinational Logic C-9 Claude Shannon C.4 Using a Hardware Description IEEE Spectrum, April 1992 Language (Shannon’s master’s thesis showed that C-20 the algebra invented by George Boole in C.5 Constructing a Basic Arithmetic Logic the 1800s could represent the workings of Unit C-26 electrical switches.) C.6 Faster Addition: Carry Lookahead C-38 C.7 Clocks C-48 AAppendixC-9780123747501.inddppendixC-9780123747501.indd 2 226/07/116/07/11 66:28:28 PPMM C.8 Memory Elements: Flip-Flops, Latches, and Registers C-50 C.9 Memory Elements: SRAMs and DRAMs C-58 C.10 Finite-State Machines C-67 C.11 Timing Methodologies C-72 C.12 Field Programmable Devices C-78 C.13 Concluding Remarks C-79 C.14 Exercises C-80 C.1 Introduction This appendix provides a brief discussion of the basics of logic design. It does not replace a course in logic design, nor will it enable you to design signifi cant working logic systems. If you have little or no exposure to logic design, however, this appendix will provide suffi cient background to understand all the material in this book. In addition, if you are looking to understand some of the motivation behind how computers are implemented, this material will serve as a useful intro- duction. If your curiosity is aroused but not sated by this appendix, the references at the end provide several additional sources of information. -

Full-Custom Ics Standard-Cell-Based
Full-Custom ICs Design a chip from scratch. Engineers design some or all of the logic cells, circuits, and the chip layout specifi- cally for a full-custom IC. Custom mask layers are created in order to fabricate a full-custom IC. Advantages: complete flexibility, high degree of optimization in performance and area. Disadvantages: large amount of design effort, expensive. 1 Standard-Cell-Based ICs Use predesigned, pretested and precharacterized logic cells from standard-cell li- brary as building blocks. The chip layout (defining the location of the building blocks and wiring between them) is customized. As in full-custom design, all mask layers need to be customized to fabricate a new chip. Advantages: save design time and money, reduce risk compared to full-custom design. Disadvantages: still incurs high non-recurring-engineering (NRE) cost and long manufacture time. 2 D A B C A B B D C D A A B B Cell A Cell B Cell C Cell D Feedthrough Cell Standard-cell-based IC design. 3 Gate-Array Parts of the chip are pre-fabricated, and other parts are custom fabricated for a particular customer’s circuit. Idential base cells are pre-fabricated in the form of a 2-D array on a gate-array (this partially finished chip is called gate-array template). The wires between the transistors inside the cells and between the cells are custom fabricated for each customer. Custom masks are made for the wiring only. Advantages: cost saving (fabrication cost of a large number of identical template wafers is amortized over different customers), shorter manufacture lead time. -

Programmable Logic Design Quick Start Hand Book
Second Edition Programmable Logic Design Quick Start Hand Book By Karen Parnell & Nick Mehta January 2002 ABSTRACT Whether you design with discrete logic, base all of your designs on microcontrollers, or simply want to learn how to use the latest and most advanced programmable logic software, you will find this book an interesting insight into a different way to design. Programmable logic devices were invented in the late seventies and since then have proved to be very popular and are now one of the largest growing sectors in the semiconductor industry. Why are programmable logic devices so widely used? Programmable logic devices provide designers ultimate flexibility, time to market advantage, design integration, are easy to design with and can be reprogrammed time and time again even in the field to upgrade system functionality. This book was written to complement the popular XilinxÒ Campus Seminar series but can also be used as a stand-alone tutorial and information source for the first of your many programmable logic designs. After you have finished your first design this book will prove useful as a reference guide or quick start handbook. The book details the history of programmable logic, where and how to use them, how to install the free, full functioning design software (Xilinx WebPACKä ISE included with this book) and then guides you through your first of many designs. There are also sections on VHDL and schematic capture design entry and finally a data bank of useful applications examples. We hope you find the book practical, informative and above all easy to use. -

CPLD and FPGA Architectures
ECE 428 Programmable ASIC Design CPLD and FPGA Architectures Haibo Wang ECE Department Southern Illinois University Carbondale, IL 62901 3-1 Definitions Field Programmable Device (FPD): — a general term that refers to any type of integrated circuit used for implementing digital hardware, where the chip can be configured by the end user to realize different designs. Programming of such a device often involves placing the chip into a special programming unit, but some chips can also be configured “in-system”. Another name for FPDs is programmable logic devices (PLDs). Source: S. Brown and J. Rose, FPGA and CPLD Architectures: A Tutorial, IEEE Design and Test of Computer, 1996 3-2 Classifications PLA — a Programmable Logic Array (PLA) is a relatively small FPD that contains two levels of logic, an AND- plane and an OR-plane, where both levels are programmable PAL — a Programmable Array Logic (PAL) is a relatively small FPD that has a programmable AND-plane followed by a fixed OR-plane SPLD — refers to any type of Simple PLD, usually either a PLA or PAL CPLD — a more Complex PLD that consists of an arrangement of multiple SPLD-like blocks on a single chip. FPGA — a Field-Programmable Gate Array is an FPD featuring a general structure that allows very high logic capacity. 3-3 PLA Programmable AND Plane Programmable OR Plane Programmable Node Un-programmed Connect Disconnect X Y O1 O2 O3 O4 X XY Y XY XY XY XX YY 3-4 PLA Programmable AND Plane Programmable OR Plane YZ XZ XYZ XY XY Z XY+YZ ?? XZ+XYZ 3-5 PAL Programmable AND Plane Fix OR Plane X Y O1 O2 O3 O4 3-6 PAL with Logic Expanders Programmable AND Plane Fix OR Plane ? Logic expanders 3-7 PLA v.s. -

High-Performance Impact-X Programmable
OBSOLETE - No Longer Available TIBPAL16L8-5C, TIBPAL16R4-5C, TIBPAL16R6-5C, TIBPAL16R8-5C TIBPAL16L8-7M, TIBPAL16R4-7M, TIBPAL16R6-7M, TIBPAL16R8-7M HIGH-PERFORMANCE IMPACT-X PAL CIRCUITS SRPS011D – D3359, OCTOBER 1989 – REVISED SEPTEMBER 1992 • High-Performance Operation: TIBPAL16L8’ C SUFFIX . J OR N PACKAGE fmax (no feedback) M SUFFIX . J PACKAGE TIBPAL16R’ -5C Series . 125 MHz Min (TOP VIEW) TIBPAL16R’ -7M Series . 100 MHz Min f (internal feedback) max I 1 20 V TIBPAL16R’ -5C Series . 125 MHz Min CC I 2 19 O TIBPAL16R’ -7M Series . 100 MHz Min I 3 18 I/O f (external feedback) max I TIBPAL16R’ -5C Series . 117 MHz Min 4 17 I/O I TIBPAL16R’ -7M Series . 74 MHz Min 5 16 I/O I Propagation Delay 6 15 I/O I TIBPAL16L8-5C Series . 5 ns Max 7 14 I/O TIBPAL16L8-7M Series . 7 ns Max I 8 13 I/O TIBPAL16R’ -5C Series I 9 12 O (CLK-to-Q) . 4 ns Max GND 10 11 I TIBPAL16R ’ -7M Series (CLK-to-Q) . 6.5 ns Max • Functionally Equivalent, but Faster than, Existing 20-Pin PLDs TIBPAL16L8’ • Preload Capability on Output Registers C SUFFIX . FN PACKAGE Simplifies Testing M SUFFIX . FK PACKAGE • Power-Up Clear on Registered Devices (All (TOP VIEW) Register Outputs are Set Low, but Voltage CC I I I O Levels at the Output Pins Go High) V • Package Options Include Both Plastic and 3 2 1 20 19 I I/O Ceramic Chip Carriers in Addition to Plastic 4 18 I/O and Ceramic DIPs I 5 17 • I 6 16 I/O Security Fuse Prevents Duplication I 7 15 I/O I 8 14 I/O I/O I 3-STATE REGISTERED 910111213 PORT DEVICE INPUTS O OUTPUTS Q OUTPUTS S I I O ’PAL16L8 10 2 0 6 I/O ’PAL16R4 8 0 4 (3-state buffers) 4 GND ’PAL16R6 8 0 6 (3-state buffers) 2 ’PAL16R8 8 0 8 (3-state buffers) 0 Pin assignments in operating mode description These programmable array logic devices feature high speed and functional equivalency when compared with currently available devices.