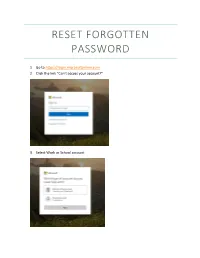
Password
Top View
- Evaluation of Password Hashing Schemes in Open Source Web
- Secure Password Storing Using Prime Decomposition Chaovalit Somboonpattanakit and Nawaporn Wisitpongphan
- SHA-1 Is a Shambles∗ First Chosen-Prefix Collision on SHA-1 and Application to the PGP Web of Trust
- Practical Password Cracking
- The Linkedin Hack: Understanding Why It Was So Easy to Crack the Passwords
- Single Password Authentication
- Simple Password-Hardened Encryption Services
- Experiments with Computer Password Cracking and Shielding Techniques
- STRONGER KEY DERIVATION VIA SEQUENTIAL MEMORY-HARD FUNCTIONS COLIN PERCIVAL 1. Introduction Password-Based Key Derivation Functi
- CRYPTOGRAPHY and NETWORK SECURITY LECTURE NOTES for Bachelor of Technology in Computer Science and Engineering & Information Technology
- Password Authentication with Insecure Communication
- Password Protection for Modern Operating Systems
- Efficient Execution of the MD5 Algorithm in Password Recovery
- Lab Exercise 1 – Introduction to Password Cracking
- Tell MD5 to SCRAM!
- Password Cracking 101
- The Evolution of Secure Hash Algorithms
- SHA-1 Hash Collision Found CS 166: Information Security Password Cracking