Password Protection for Modern Operating Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Shell Scripting with Bash
Introduction to Shell Scripting with Bash Charles Jahnke Research Computing Services Information Services & Technology Topics for Today ● Introductions ● Basic Terminology ● How to get help ● Command-line vs. Scripting ● Variables ● Handling Arguments ● Standard I/O, Pipes, and Redirection ● Control Structures (loops and If statements) ● SCC Job Submission Example Research Computing Services Research Computing Services (RCS) A group within Information Services & Technology at Boston University provides computing, storage, and visualization resources and services to support research that has specialized or highly intensive computation, storage, bandwidth, or graphics requirements. Three Primary Services: ● Research Computation ● Research Visualization ● Research Consulting and Training Breadth of Research on the Shared Computing Cluster (SCC) Me ● Research Facilitator and Administrator ● Background in biomedical engineering, bioinformatics, and IT systems ● Offices on both CRC and BUMC ○ Most of our staff on the Charles River Campus, some dedicated to BUMC ● Contact: [email protected] You ● Who has experience programming? ● Using Linux? ● Using the Shared Computing Cluster (SCC)? Basic Terminology The Command-line The line on which commands are typed and passed to the shell. Username Hostname Current Directory [username@scc1 ~]$ Prompt Command Line (input) The Shell ● The interface between the user and the operating system ● Program that interprets and executes input ● Provides: ○ Built-in commands ○ Programming control structures ○ Environment -

Windows - Run/Kör Kommando
Windows - Run/Kör kommando Accessibility Controls - access.cpl Network Connections - ncpa.cpl Add Hardware Wizard - hdwwiz.cpl Network Setup Wizard - netsetup.cpl Add/Remove Programs - appwiz.cpl Notepad - notepad Administrative Tools - control admintools Nview Desktop Manager - nvtuicpl.cpl Automatic Updates - wuaucpl.cpl Object Packager - packager Bluetooth Transfer Wizard - fsquirt ODBC Data Source Administrator - odbccp32.cpl Calculator - calc On Screen Keyboard - osk Certificate Manager - certmgr.msc Opens AC3 Filter - ac3filter.cpl Character Map - charmap Password Properties - password.cpl Check Disk Utility - chkdsk Performance Monitor - perfmon.msc Clipboard Viewer - clipbrd Performance Monitor - perfmon Command Prompt - cmd Phone and Modem Options - telephon.cpl Component Services - dcomcnfg Power Configuration - powercfg.cpl Computer Management - compmgmt.msc Printers and Faxes - control printers Control Panel - control panel Printers Folder - printers Date and Time Properties - timedate.cpl Private Character Editor - eudcedit DDE Share - ddeshare Quicktime (If Installed) - QuickTime.cpl Device Manager - devmgmt.msc Regional Settings - intl.cpl Direct X Control Panel -directx.cpl Registry Editor - regedit Direct X Troubleshooter - dxdiag Registry Editor - regedit32 Disk Cleanup Utility - cleanmgr Remote Desktop - mstsc Disk Defragment - dfrg.msc Removable Storage - ntmsmgr.msc Disk Management - diskmgmt.msc Removable Storage Operator Requests - ntmsoprq.msc Disk Partition Manager - diskpart Resultant Set of Policy (XP Prof) -

Intro to Cryptography 1 Introduction 2 Secure Password Manager
Programming Assignment 1 Winter 2021 CS 255: Intro to Cryptography Prof. Dan Boneh Due Monday, Feb. 8, 11:59pm 1 Introduction In many software systems today, the primary weakness often lies in the user’s password. This is especially apparent in light of recent security breaches that have highlighted some of the weak passwords people commonly use (e.g., 123456 or password). It is very important, then, that users choose strong passwords (or “passphrases”) to secure their accounts, but strong passwords can be long and unwieldy. Even more problematic, the user generally has many different services that use password authentication, and as a result, the user has to recall many different passwords. One way for users to address this problem is to use a password manager, such as LastPass and KeePass. Password managers make it very convenient for users to use a unique, strong password for each service that requires password authentication. However, given the sensitivity of the data contained in the password manager, it takes considerable care to store the information securely. In this assignment, you will be writing a secure and efficient password manager. In your implemen- tation, you will make use of various cryptographic primitives we have discussed in class—notably, authenticated encryption and collision-resistant hash functions. Because it is ill-advised to imple- ment your own primitives in cryptography, you should use an established library: in this case, the Stanford Javascript Crypto Library (SJCL). We will provide starter code that contains a basic tem- plate, which you will be able to fill in to satisfy the functionality and security properties described below. -

User Authentication and Cryptographic Primitives
User Authentication and Cryptographic Primitives Brad Karp UCL Computer Science CS GZ03 / M030 16th November 2016 Outline • Authenticating users – Local users: hashed passwords – Remote users: s/key – Unexpected covert channel: the Tenex password- guessing attack • Symmetric-key-cryptography • Public-key cryptography usage model • RSA algorithm for public-key cryptography – Number theory background – Algorithm definition 2 Dictionary Attack on Hashed Password Databases • Suppose hacker obtains copy of password file (until recently, world-readable on UNIX) • Compute H(x) for 50K common words • String compare resulting hashed words against passwords in file • Learn all users’ passwords that are common English words after only 50K computations of H(x)! • Same hashed dictionary works on all password files in world! 3 Salted Password Hashes • Generate a random string of bytes, r • For user password x, store [H(r,x), r] in password file • Result: same password produces different result on every machine – So must see password file before can hash dictionary – …and single hashed dictionary won’t work for multiple hosts • Modern UNIX: password hashes salted; hashed password database readable only by root 4 Salted Password Hashes • Generate a random string of bytes, r Dictionary• For user password attack still x, store possible [H(r,x after), r] in attacker seespassword password file file! Users• Result: should same pick password passwords produces that different aren’t result close to ondictionary every machine words. – So must see password file -

Modern Password Security for System Designers What to Consider When Building a Password-Based Authentication System
Modern password security for system designers What to consider when building a password-based authentication system By Ian Maddox and Kyle Moschetto, Google Cloud Solutions Architects This whitepaper describes and models modern password guidance and recommendations for the designers and engineers who create secure online applications. A related whitepaper, Password security for users, offers guidance for end users. This whitepaper covers the wide range of options to consider when building a password-based authentication system. It also establishes a set of user-focused recommendations for password policies and storage, including the balance of password strength and usability. The technology world has been trying to improve on the password since the early days of computing. Shared-knowledge authentication is problematic because information can fall into the wrong hands or be forgotten. The problem is magnified by systems that don't support real-world secure use cases and by the frequent decision of users to take shortcuts. According to a 2019 Yubico/Ponemon study, 69 percent of respondents admit to sharing passwords with their colleagues to access accounts. More than half of respondents (51 percent) reuse an average of five passwords across their business and personal accounts. Furthermore, two-factor authentication is not widely used, even though it adds protection beyond a username and password. Of the respondents, 67 percent don’t use any form of two-factor authentication in their personal life, and 55 percent don’t use it at work. Password systems often allow, or even encourage, users to use insecure passwords. Systems that allow only single-factor credentials and that implement ineffective security policies add to the problem. -

To Change Your Ud Password(S)
TO CHANGE YOUR UD PASSWORD(S) The MyCampus portal allows the user a single-signon for campus applications. IMPORTANT NOTICE AT BOTTOM OF THESE INSTRUCTIONS !! INITIAL PROCEDURE TO ALLOW YOU TO CHANGE YOUR PASSWORD ON THE UD NETWORK : 1. In your web browser, enter http://mycampus.dbq.edu . If you are logging in for the first time, you will be directed to answer (3) security questions. Also, be sure to answer one of the recovery methods. 2. Once the questions are answered, you will click on SUBMIT and then CONTINUE and then YES. 3. In one location, you will now find MyUD, Campus Portal, Email and UDOnline (Moodle). 4. You can now click on any of these apps and you will be logged in already. The email link will prompt you for the password a second time until we get all accounts set up properly. YOU MUST BE SURE TO LOGOUT OF EACH APPLICATION AFTER YOU’RE DONE USING IT !! TO CHANGE YOUR PASSWORD: 1. After you have logged into the MyCampus.dbq.edu website, you will see your username in the upper- right corner of the screen. 2. Click on your name and then go into My Account. 3. At the bottom, you will click on Change Password and then proceed as directed. 4. You can now logout. You will need to use your new password on your next login. Password must be a minimum of 6 characters and contain 3 of the following 4 categories: - Uppercase character - Lowercase character - Number - Special character You cannot use the previous password You’ll be required to change your password every 180 days. -
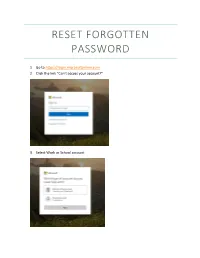
Reset Forgotten Password with Office365
RESET FORGOTTEN PASSWORD 1. Go to https://login.microsoftonline.com 2. Click the link “Can’t access your account?” 3. Select Work or School account 4. Enter in your User ID with the @uamont.edu at the end and then enter the characters as seen in the picture. You can click the refresh button for a different set of letters. 5. You will have 3 options to verify your account and reset your password. This information was set up when you registered with self-service password reset. If you have not registered, please go to https://aka.ms/ssprsetup and enter in your information. A step by step guide on how to do this can be found here. a. Text your mobile phone b. Call your mobile phone c. Answer Security Questions 6. Choose one option and enter the information requested 7. Click Text for text my mobile phone, Call for call my mobile phone, or click Next when you’ve answered all security questions. a. If you have selected Text my mobile phone you will be required to enter in a verification code and click Next b. If you have select Call my mobile phone you will receive a call and will need to enter # to verify. 8. Enter in your new password and click Finish a. Note: If you receive the message, “Unfortunately, your password contains a word, phrase, or pattern that makes it easily guessable. Please try again with a different password.” Please try to create a password that does not use any dictionary words. b. Passwords must meet 3 of the 4 following requirements i. -

Powerview Command Reference
PowerView Command Reference TRACE32 Online Help TRACE32 Directory TRACE32 Index TRACE32 Documents ...................................................................................................................... PowerView User Interface ............................................................................................................ PowerView Command Reference .............................................................................................1 History ...................................................................................................................................... 12 ABORT ...................................................................................................................................... 13 ABORT Abort driver program 13 AREA ........................................................................................................................................ 14 AREA Message windows 14 AREA.CLEAR Clear area 15 AREA.CLOSE Close output file 15 AREA.Create Create or modify message area 16 AREA.Delete Delete message area 17 AREA.List Display a detailed list off all message areas 18 AREA.OPEN Open output file 20 AREA.PIPE Redirect area to stdout 21 AREA.RESet Reset areas 21 AREA.SAVE Save AREA window contents to file 21 AREA.Select Select area 22 AREA.STDERR Redirect area to stderr 23 AREA.STDOUT Redirect area to stdout 23 AREA.view Display message area in AREA window 24 AutoSTOre .............................................................................................................................. -

Implementation and Performance Analysis of PBKDF2, Bcrypt, Scrypt Algorithms
Implementation and Performance Analysis of PBKDF2, Bcrypt, Scrypt Algorithms Levent Ertaul, Manpreet Kaur, Venkata Arun Kumar R Gudise CSU East Bay, Hayward, CA, USA. [email protected], [email protected], [email protected] Abstract- With the increase in mobile wireless or data lookup. Whereas, Cryptographic hash functions are technologies, security breaches are also increasing. It has used for building blocks for HMACs which provides become critical to safeguard our sensitive information message authentication. They ensure integrity of the data from the wrongdoers. So, having strong password is that is transmitted. Collision free hash function is the one pivotal. As almost every website needs you to login and which can never have same hashes of different output. If a create a password, it’s tempting to use same password and b are inputs such that H (a) =H (b), and a ≠ b. for numerous websites like banks, shopping and social User chosen passwords shall not be used directly as networking websites. This way we are making our cryptographic keys as they have low entropy and information easily accessible to hackers. Hence, we need randomness properties [2].Password is the secret value from a strong application for password security and which the cryptographic key can be generated. Figure 1 management. In this paper, we are going to compare the shows the statics of increasing cybercrime every year. Hence performance of 3 key derivation algorithms, namely, there is a need for strong key generation algorithms which PBKDF2 (Password Based Key Derivation Function), can generate the keys which are nearly impossible for the Bcrypt and Scrypt. -

Logs & Event Analysis and Password Cracking
Logs & Event Analysis and Password Cracking MODULE 6 Page 1 of 29 Contents 6.1 Learning Objectives ............................................................................................................. 4 6.2 Introduction .......................................................................................................................... 4 6.3 Windows registry ................................................................................................................. 5 6.3.1 Registry and forensics ................................................................................................... 5 6.3.1.1 System information ................................................................................................ 5 6.4 Windows event log file ........................................................................................................ 9 6.4.1 Windows Event Log File Format .................................................................................. 9 6.4.2 Reading from Windows event log file ........................................................................ 11 6.4.3 Using Microsoft log parser ......................................................................................... 11 6.4.4 Understanding Windows user account management logs .......................................... 13 6.4.5 Understanding Windows file and other object Access sets ........................................ 14 6.4.6 Auditing policy change .............................................................................................. -

Key Derivation Functions and Their GPU Implementation
MASARYK UNIVERSITY FACULTY}w¡¢£¤¥¦§¨ OF I !"#$%&'()+,-./012345<yA|NFORMATICS Key derivation functions and their GPU implementation BACHELOR’S THESIS Ondrej Mosnáˇcek Brno, Spring 2015 This work is licensed under a Creative Commons Attribution- NonCommercial-ShareAlike 4.0 International License. https://creativecommons.org/licenses/by-nc-sa/4.0/ cbna ii Declaration Hereby I declare, that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Ondrej Mosnáˇcek Advisor: Ing. Milan Brož iii Acknowledgement I would like to thank my supervisor for his guidance and support, and also for his extensive contributions to the Cryptsetup open- source project. Next, I would like to thank my family for their support and pa- tience and also to my friends who were falling behind schedule just like me and thus helped me not to panic. Last but not least, access to computing and storage facilities owned by parties and projects contributing to the National Grid In- frastructure MetaCentrum, provided under the programme “Projects of Large Infrastructure for Research, Development, and Innovations” (LM2010005), is also greatly appreciated. v Abstract Key derivation functions are a key element of many cryptographic applications. Password-based key derivation functions are designed specifically to derive cryptographic keys from low-entropy sources (such as passwords or passphrases) and to counter brute-force and dictionary attacks. However, the most widely adopted standard for password-based key derivation, PBKDF2, as implemented in most applications, is highly susceptible to attacks using Graphics Process- ing Units (GPUs). -

An Empirical Comparison of Widely Adopted Hash Functions in Digital Forensics: Does the Programming Language and Operating System Make a Difference?
2015 Annual ADFSL Conference on Digital Forensics, Security and Law Proceedings May 19th, 11:45 AM An Empirical Comparison of Widely Adopted Hash Functions in Digital Forensics: Does the Programming Language and Operating System Make a Difference? Satyendra Gurjar Cyber Forensics Research and Education Group (UNHcFREG), Tagliatela College of Engineering, ECECS Department, University of New Haven, [email protected] Ibrahim Baggili Cyber Forensics Research and Education Group (UNHcFREG), Tagliatela College of Engineering, ECECS Department, University of New Haven Frank Breitinger CyberFollow F thisorensics and additional Research worksand Education at: https:/ Gr/commons.eroup (UNHcFREG),au.edu/adfsl Tagliatela College of Engineering, ECECS Depar Partment,t of the Univ Aviationersity ofSaf Newety and Hav Securityen Commons, Computer Law Commons, Defense and Security AliceStudies Fischer Commons , Forensic Science and Technology Commons, Information Security Commons, CyberNational For Securityensics Resear Law Commonsch and Education, OS and GrNetworksoup (UNHcFREG), Commons T, Otheragliatela Computer College Sciences of Engineering, Commons ECECS, and theDepar Socialtment, Contr Univol,ersity Law , ofCrime, New andHav enDe,viance AFischer@newha Commons ven.edu Scholarly Commons Citation Gurjar, Satyendra; Baggili, Ibrahim; Breitinger, Frank; and Fischer, Alice, "An Empirical Comparison of Widely Adopted Hash Functions in Digital Forensics: Does the Programming Language and Operating System Make a Difference?" (2015). Annual ADFSL Conference on Digital Forensics, Security and Law. 6. https://commons.erau.edu/adfsl/2015/tuesday/6 This Peer Reviewed Paper is brought to you for free and open access by the Conferences at Scholarly Commons. It has been accepted for inclusion in Annual ADFSL Conference on Digital Forensics, Security and Law by an (c)ADFSL authorized administrator of Scholarly Commons.