Strong Password-Based Authentication in TLS Using the Three-Party Group Diffie–Hellman Protocol
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Intro to Cryptography 1 Introduction 2 Secure Password Manager
Programming Assignment 1 Winter 2021 CS 255: Intro to Cryptography Prof. Dan Boneh Due Monday, Feb. 8, 11:59pm 1 Introduction In many software systems today, the primary weakness often lies in the user’s password. This is especially apparent in light of recent security breaches that have highlighted some of the weak passwords people commonly use (e.g., 123456 or password). It is very important, then, that users choose strong passwords (or “passphrases”) to secure their accounts, but strong passwords can be long and unwieldy. Even more problematic, the user generally has many different services that use password authentication, and as a result, the user has to recall many different passwords. One way for users to address this problem is to use a password manager, such as LastPass and KeePass. Password managers make it very convenient for users to use a unique, strong password for each service that requires password authentication. However, given the sensitivity of the data contained in the password manager, it takes considerable care to store the information securely. In this assignment, you will be writing a secure and efficient password manager. In your implemen- tation, you will make use of various cryptographic primitives we have discussed in class—notably, authenticated encryption and collision-resistant hash functions. Because it is ill-advised to imple- ment your own primitives in cryptography, you should use an established library: in this case, the Stanford Javascript Crypto Library (SJCL). We will provide starter code that contains a basic tem- plate, which you will be able to fill in to satisfy the functionality and security properties described below. -

User Authentication and Cryptographic Primitives
User Authentication and Cryptographic Primitives Brad Karp UCL Computer Science CS GZ03 / M030 16th November 2016 Outline • Authenticating users – Local users: hashed passwords – Remote users: s/key – Unexpected covert channel: the Tenex password- guessing attack • Symmetric-key-cryptography • Public-key cryptography usage model • RSA algorithm for public-key cryptography – Number theory background – Algorithm definition 2 Dictionary Attack on Hashed Password Databases • Suppose hacker obtains copy of password file (until recently, world-readable on UNIX) • Compute H(x) for 50K common words • String compare resulting hashed words against passwords in file • Learn all users’ passwords that are common English words after only 50K computations of H(x)! • Same hashed dictionary works on all password files in world! 3 Salted Password Hashes • Generate a random string of bytes, r • For user password x, store [H(r,x), r] in password file • Result: same password produces different result on every machine – So must see password file before can hash dictionary – …and single hashed dictionary won’t work for multiple hosts • Modern UNIX: password hashes salted; hashed password database readable only by root 4 Salted Password Hashes • Generate a random string of bytes, r Dictionary• For user password attack still x, store possible [H(r,x after), r] in attacker seespassword password file file! Users• Result: should same pick password passwords produces that different aren’t result close to ondictionary every machine words. – So must see password file -

The Twin Diffie-Hellman Problem and Applications
The Twin Diffie-Hellman Problem and Applications David Cash1 Eike Kiltz2 Victor Shoup3 February 10, 2009 Abstract We propose a new computational problem called the twin Diffie-Hellman problem. This problem is closely related to the usual (computational) Diffie-Hellman problem and can be used in many of the same cryptographic constructions that are based on the Diffie-Hellman problem. Moreover, the twin Diffie-Hellman problem is at least as hard as the ordinary Diffie-Hellman problem. However, we are able to show that the twin Diffie-Hellman problem remains hard, even in the presence of a decision oracle that recognizes solutions to the problem — this is a feature not enjoyed by the Diffie-Hellman problem in general. Specifically, we show how to build a certain “trapdoor test” that allows us to effectively answer decision oracle queries for the twin Diffie-Hellman problem without knowing any of the corresponding discrete logarithms. Our new techniques have many applications. As one such application, we present a new variant of ElGamal encryption with very short ciphertexts, and with a very simple and tight security proof, in the random oracle model, under the assumption that the ordinary Diffie-Hellman problem is hard. We present several other applications as well, including: a new variant of Diffie and Hellman’s non-interactive key exchange protocol; a new variant of Cramer-Shoup encryption, with a very simple proof in the standard model; a new variant of Boneh-Franklin identity-based encryption, with very short ciphertexts; a more robust version of a password-authenticated key exchange protocol of Abdalla and Pointcheval. -

To Change Your Ud Password(S)
TO CHANGE YOUR UD PASSWORD(S) The MyCampus portal allows the user a single-signon for campus applications. IMPORTANT NOTICE AT BOTTOM OF THESE INSTRUCTIONS !! INITIAL PROCEDURE TO ALLOW YOU TO CHANGE YOUR PASSWORD ON THE UD NETWORK : 1. In your web browser, enter http://mycampus.dbq.edu . If you are logging in for the first time, you will be directed to answer (3) security questions. Also, be sure to answer one of the recovery methods. 2. Once the questions are answered, you will click on SUBMIT and then CONTINUE and then YES. 3. In one location, you will now find MyUD, Campus Portal, Email and UDOnline (Moodle). 4. You can now click on any of these apps and you will be logged in already. The email link will prompt you for the password a second time until we get all accounts set up properly. YOU MUST BE SURE TO LOGOUT OF EACH APPLICATION AFTER YOU’RE DONE USING IT !! TO CHANGE YOUR PASSWORD: 1. After you have logged into the MyCampus.dbq.edu website, you will see your username in the upper- right corner of the screen. 2. Click on your name and then go into My Account. 3. At the bottom, you will click on Change Password and then proceed as directed. 4. You can now logout. You will need to use your new password on your next login. Password must be a minimum of 6 characters and contain 3 of the following 4 categories: - Uppercase character - Lowercase character - Number - Special character You cannot use the previous password You’ll be required to change your password every 180 days. -
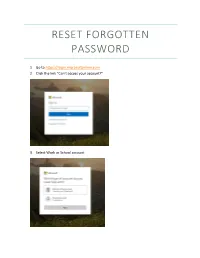
Reset Forgotten Password with Office365
RESET FORGOTTEN PASSWORD 1. Go to https://login.microsoftonline.com 2. Click the link “Can’t access your account?” 3. Select Work or School account 4. Enter in your User ID with the @uamont.edu at the end and then enter the characters as seen in the picture. You can click the refresh button for a different set of letters. 5. You will have 3 options to verify your account and reset your password. This information was set up when you registered with self-service password reset. If you have not registered, please go to https://aka.ms/ssprsetup and enter in your information. A step by step guide on how to do this can be found here. a. Text your mobile phone b. Call your mobile phone c. Answer Security Questions 6. Choose one option and enter the information requested 7. Click Text for text my mobile phone, Call for call my mobile phone, or click Next when you’ve answered all security questions. a. If you have selected Text my mobile phone you will be required to enter in a verification code and click Next b. If you have select Call my mobile phone you will receive a call and will need to enter # to verify. 8. Enter in your new password and click Finish a. Note: If you receive the message, “Unfortunately, your password contains a word, phrase, or pattern that makes it easily guessable. Please try again with a different password.” Please try to create a password that does not use any dictionary words. b. Passwords must meet 3 of the 4 following requirements i. -

2.4 the Random Oracle Model
國 立 交 通 大 學 資訊工程學系 博 士 論 文 可證明安全的公開金鑰密碼系統與通行碼驗證金鑰 交換 Provably Secure Public Key Cryptosystems and Password Authenticated Key Exchange Protocols 研 究 生:張庭毅 指導教授:楊維邦 教授 黃明祥 教授 中 華 民 國 九 十 五 年 十 二 月 可證明安全的公開金鑰密碼系統與通行碼驗證金鑰交換 Provably Secure Public Key Cryptosystems and Password Authenticated Key Exchange Protocols 研 究 生:張庭毅 Student:Ting-Yi Chang 指導教授:楊維邦 博士 Advisor:Dr. Wei-Pang Yang 黃明祥 博士 Dr. Min-Shiang Hwang 國 立 交 通 大 學 資 訊 工 程 學 系 博 士 論 文 A Dissertation Submitted to Department of Computer Science College of Computer Science National Chiao Tung University in partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy in Computer Science December 2006 Hsinchu, Taiwan, Republic of China 中華民國九十五年十二月 ¡¢£¤¥¦§¨© ª« ¬ Æ ¯ « ¡¨ © ¡¢£¤¥ ¦§¨©¢ª«¬ Æ ¯ Æ Æ Æ ¡ ElGamal ¦§ °±¥ ²³´ ·§±¥¸¹º»¼½¶¾¿§¾¿¸¹³ °µ¶ p ° p§¾¿ ElGamal Hwang §°À¡Á²±¥·§ÂÃÄŨ© ElGamal-like È ÆǧȤÉÀÊËÌ¡ÍÎϧElGamal-like IND-CPA ¡¦ÃÅ Á²±¥·ÁÃÄŧ¨©§Æ ° ½¡ÐÑÒµ§ IND-CPA ElGamal IND- ±È¤±¥ÓÔÕ§ CCA2§ ElGamal-extended ¡Ö×جٶÚÀÛÜ°§¨©ÝÞ°ÛÜߧ ¡¦§ËÌ IND-CPAPAIR ElGamal-extended Ô°°ÃÄÅ ¬§DZàáâ ãäåæçèé°¡êÛÜ°ëìíîï§åÉ i ïíîÛܰ먩ǰ § ðñòóô ¨©õö÷°§Àäå øù×Øú§ûüÀÆý°þÿì° ÛÜµÌ °Ûܱ¡ Bellare-Pointcheval-Rogaway ¯À°úÐÑÒ·§¨© ° Diffie-Hellman õ°Ý§¡¦§ ò°¥§§±¥§Diffie- Hellman ¯§¥§§È秧 È秧ô§§ç±Ûܧ §ÐÑÒ ii Provably Secure Public Key Cryptosystems and Password Authenticated Key Exchange Protocols Student: Ting-Yi Chang Advisor: Dr. Wei-Pang Yang Dr. Min-Shiang Hwang Institute of Computer Science and Engineering National Chiao Tung University ABSTRACT In this thesis, we focus on two topics: public key cryptosystems and pass- word authenticated key exchange protocols. -

Optimizing a Password Hashing Function with Hardware-Accelerated Symmetric Encryption
S S symmetry Article Optimizing a Password Hashing Function with Hardware-Accelerated Symmetric Encryption Rafael Álvarez 1,* , Alicia Andrade 2 and Antonio Zamora 3 1 Departamento de Ciencia de la Computación e Inteligencia Artificial (DCCIA), Universidad de Alicante, 03690 Alicante, Spain 2 Fac. Ingeniería, Ciencias Físicas y Matemática, Universidad Central, Quito 170129, Ecuador; [email protected] 3 Departamento de Ciencia de la Computación e Inteligencia Artificial (DCCIA), Universidad de Alicante, 03690 Alicante, Spain; [email protected] * Correspondence: [email protected] Received: 2 November 2018; Accepted: 22 November 2018; Published: 3 December 2018 Abstract: Password-based key derivation functions (PBKDFs) are commonly used to transform user passwords into keys for symmetric encryption, as well as for user authentication, password hashing, and preventing attacks based on custom hardware. We propose two optimized alternatives that enhance the performance of a previously published PBKDF. This design is based on (1) employing a symmetric cipher, the Advanced Encryption Standard (AES), as a pseudo-random generator and (2) taking advantage of the support for the hardware acceleration for AES that is available on many common platforms in order to mitigate common attacks to password-based user authentication systems. We also analyze their security characteristics, establishing that they are equivalent to the security of the core primitive (AES), and we compare their performance with well-known PBKDF algorithms, such as Scrypt and Argon2, with favorable results. Keywords: symmetric; encryption; password; hash; cryptography; PBKDF 1. Introduction Key derivation functions are employed to obtain one or more keys from a master secret. This is especially useful in the case of user passwords, which can be of arbitrary length and are unsuitable to be used directly as fixed-size cipher keys, so, there must be a process for converting passwords into secret keys. -

Multi-Server Authentication Key Exchange Approach in Bigdata Environment
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 04 Issue: 07 | July -2017 www.irjet.net p-ISSN: 2395-0072 MULTI-SERVER AUTHENTICATION KEY EXCHANGE APPROACH IN BIGDATA ENVIRONMENT Miss. Kiran More1, Prof. Jyoti Raghatwan2 1Kiran More, PG Student. Dept. of Computer Engg. RMD Sinhgad school of Engineering Warje, Pune 2Prof. Jyoti Raghatwan, Dept. of Computer Engg. RMD Sinhgad school of Engineering Warje, Pune ---------------------------------------------------------------------***--------------------------------------------------------------------- Abstract - The key establishment difficulty is the maximum Over-all Equivalent Files System. Which are usually required central issue and we learn the trouble of key organization for for advanced scientific or data exhaustive applications such secure many to many communications for past several years. as digital animation studios, computational fluid dynamics, The trouble is stimulated by the broadcast of huge level and semiconductor manufacturing. detached file organizations behind similar admission to In these milieus, hundreds or thousands of file various storage space tactics. Our chore focal ideas on the structure clients bit data and engender very much high current Internet commonplace for such folder systems that is summative I/O load on the file coordination supporting Parallel Network Folder System [pNFS], which generates petabytes or terabytes scale storage capacities. Liberated of employment of Kerberos to establish up similar session keys the enlargement of the knot and high-performance flanked by customers and storing strategy. Our evaluation of computing, the arrival of clouds and the MapReduce the available Kerberos bottommost procedure validates that it program writing model has resulted in file system such as has a numeral of borders: (a) a metadata attendant make the Hadoop Distributed File System (HDFS). -

Authentication and Key Distribution in Computer Networks and Distributed Systems
13 Authentication and key distribution in computer networks and distributed systems Rolf Oppliger University of Berne Institute for Computer Science and Applied Mathematics {JAM) Neubruckstrasse 10, CH-3012 Bern Phone +41 31 631 89 51, Fax +41 31 631 39 65, [email protected] Abstract Authentication and key distribution systems are used in computer networks and dis tributed systems to provide security services at the application layer. There are several authentication and key distribution systems currently available, and this paper focuses on Kerberos (OSF DCE), NetSP, SPX, TESS and SESAME. The systems are outlined and reviewed with special regard to the security services they offer, the cryptographic techniques they use, their conformance to international standards, and their availability and exportability. Keywords Authentication, key distribution, Kerberos, NetSP, SPX, TESS, SESAME 1 INTRODUCTION Authentication and key distribution systems are used in computer networks and dis tributed systems to provide security services at the application layer. There are several authentication and key distribution systems currently available, and this paper focuses on Kerberos (OSF DCE), NetSP, SPX, TESS and SESAME. The systems are outlined and reviewed with special regard to the security services they offer, the cryptographic techniques they use, their conformance to international standards, and their availability and exportability. It is assumed that the reader of this paper is familiar with the funda mentals of cryptography, and the use of cryptographic techniques in computer networks and distributed systems (Oppliger, 1992 and Schneier, 1994). The following notation is used in this paper: • Capital letters are used to refer to principals (users, clients and servers). -

Fast and Secure Generating and Exchanging a Symmetric Key for TVWS Protocol
International Journal of Computer Science and Telecommunications [Volume 9, Issue 3, May 2018] 15 Fast and Secure Generating and Exchanging a Symmetric Key for TVWS Protocol ISSN 2047-3338 Mubark M. A. Elmubark Department of MIS Blue Nile University, Sudan [email protected] Abstract– In network security, symmetric key encryption security key. So many security protocols can be used in methods are commonly used in order to generate and exchange TVWS with pros and cons. a secret key between the sender and the receiver. The main This paper concentrated on security issues in spectrum drawbacks of this method are that, the attackers might access database access and studies these protocols and proposed new the transmitted data and use it to obtain the key and even methods for key generation and exchange. generate new keys. Also, the process of generating the key is inefficient and time consuming. In this paper a new key PKMv1: WiMAX security, as specified by IEEE 802.16 generation and exchange protocol is proposed to overcome the standard [2] is provided by a security sublayer resided in the aforementioned problems in the conventional symmetric key MAC layer. A protocol called PKM has been adopted in the encryption methods. In the proposed protocol, the results show security sublayer of WiMAX to provide authorization, that the protocol is saved. authentication and keys exchange and distribution between Index Terms– Security, Key Generation and Key Exchange Base Stations (BSs) and Subscriber Stations (SSs). The standard has approved two versions of PKM protocol. PKMv1 which is approved in IEEE 802.16-2004 standards I. -

Distribution Scheme for Fog Networks Nikkhah Bahrami, P, Javadi, HHS, Dargahi, T, Dehghantanha, a and Choo, KKR
A hierarchical key pre-distribution scheme for fog networks Nikkhah Bahrami, P, Javadi, HHS, Dargahi, T, Dehghantanha, A and Choo, KKR http://dx.doi.org/10.1002/cpe.4776 Title A hierarchical key pre-distribution scheme for fog networks Authors Nikkhah Bahrami, P, Javadi, HHS, Dargahi, T, Dehghantanha, A and Choo, KKR Type Article URL This version is available at: http://usir.salford.ac.uk/id/eprint/47188/ Published Date 2019 USIR is a digital collection of the research output of the University of Salford. Where copyright permits, full text material held in the repository is made freely available online and can be read, downloaded and copied for non-commercial private study or research purposes. Please check the manuscript for any further copyright restrictions. For more information, including our policy and submission procedure, please contact the Repository Team at: [email protected]. ReceivED -; ReVISED -; Accepted 31 MaY 2018 DOI: xxx/XXXX SPECIAL ISSUE PAPER A HierARCHICAL KEY Pre-Distribution Scheme FOR FOG Networks POONEH Nikkhah BahrAMI1 | Hamid H.S.JaVADI2 | TOOSKA Dargahi3 | Ali Dehghantanha4 | Kim-KWANG RaYMOND Choo5 1Department OF Computer Science, TEHRAN UnivERSITY, Kish Campus, IrAN Summary 2Department OF Computer Science, Shahed UnivERSITY, TEHRan, IrAN Security IN FOG COMPUTING IS multi-faceted, AND ONE PARTICULAR CHALLENGE IS ESTABLISHING A SECURE 3 School OF Computing, Science AND Engineering, COMMUNICATION CHANNEL BETWEEN FOG NODES AND END DEvices. This EMPHASIZES THE IMPORTANCE UnivERSITY OF Salford, Manchester, UK 4Department OF Computer Science, UnivERSITY OF DESIGNING EFfiCIENT AND SECRET KEY DISTRIBUTION SCHEME TO FACILITATE FOG NODES AND END DEVICES OF Sheffield, Sheffield, UK TO ESTABLISH SECURE COMMUNICATION channels. -

On Robust Key Agreement Based on Public Key Authentication Feng Hao Thales E-Security, Cambridge, UK [email protected]
1 On Robust Key Agreement Based on Public Key Authentication Feng Hao Thales E-Security, Cambridge, UK [email protected] Abstract—This paper discusses public-key authenticated key Elliptic Curve Cryptography (ECC) [10]. Using ECC essen- agreement protocols. First, we critically analyze several authen- tially replaces the underlying (multiplicative) cyclic group ticated key agreement protocols and uncover various theoretical with another (additive) cyclic group defined over some elliptic and practical flaws. In particular, we present two new attacks on the HMQV protocol, which is currently being standardized curve. The essence of the protocol remains unchanged. by IEEE P1363. The first attack presents a counterexample to The acute problem with the Diffie-Hellman key agreement invalidate the basic authentication in HMQV. The second attack is that it is unauthenticated [2]. While secure against passive is applicable to almost all past schemes, despite that many of attackers, the protocol is inherently vulnerable to active attacks them have formal security proofs. These attacks highlight the such as the man-in-the-middle attack [6]. This is a serious lim- difficulty to design a crypto protocol correctly and suggest the caution one should always take. itation, which for many years has been motivating researchers We further point out that many of the design errors are caused to find a solution [3]–[5], [7], [9], [11], [13], [20]. by sidestepping an important engineering principle, namely To add authentication, we must start with assuming some “Do not assume that a message you receive has a particular shared secret. In general, there are two approaches.