User Authentication and Cryptographic Primitives
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Intro to Cryptography 1 Introduction 2 Secure Password Manager
Programming Assignment 1 Winter 2021 CS 255: Intro to Cryptography Prof. Dan Boneh Due Monday, Feb. 8, 11:59pm 1 Introduction In many software systems today, the primary weakness often lies in the user’s password. This is especially apparent in light of recent security breaches that have highlighted some of the weak passwords people commonly use (e.g., 123456 or password). It is very important, then, that users choose strong passwords (or “passphrases”) to secure their accounts, but strong passwords can be long and unwieldy. Even more problematic, the user generally has many different services that use password authentication, and as a result, the user has to recall many different passwords. One way for users to address this problem is to use a password manager, such as LastPass and KeePass. Password managers make it very convenient for users to use a unique, strong password for each service that requires password authentication. However, given the sensitivity of the data contained in the password manager, it takes considerable care to store the information securely. In this assignment, you will be writing a secure and efficient password manager. In your implemen- tation, you will make use of various cryptographic primitives we have discussed in class—notably, authenticated encryption and collision-resistant hash functions. Because it is ill-advised to imple- ment your own primitives in cryptography, you should use an established library: in this case, the Stanford Javascript Crypto Library (SJCL). We will provide starter code that contains a basic tem- plate, which you will be able to fill in to satisfy the functionality and security properties described below. -

Truecrack Bruteforcing Per Volumi Truecrypt
Luca Vaccaro http://code.google.com/p/truecrack/ [email protected] User development guide. TrueCrypt © . software application used for on-the-fly encryption (OTFE). TrueCrack . bruteforce password cracker for TrueCrypt © (Copyrigth) volume files, optimazed with Nvidia Cuda technology. This software is Based on TrueCrypt, freely available athttp://www.truecrypt.org/ Master key . Crypt the volume of data. Generated one time in the volume creation phase from random value. Write inside the header section of the volume file. Header key . Crypt the header section of the volume file. Generated from a user password and a random salt (64 bytes). The salt is write in plain text in the first 64 bytes of volume file. Hard disk encryption: . Standard block cipher: XTS . Hash availables: AES, Serpent, Twofish . Default: AES Key derivation function: . Standard algorithm: PBKDF2 . Hash availables: RIPEMD160, SHA-512, Whirpool . Default: RIPEMD160 Master Header Key Key Plain Cipher Volume data data + file header Opening a TrueCrypt volume means to retrieve the Master Key from the Header section In the Header there are some fields (true, crc32) for checking the success of the decipher operation . If the password is right or wrong Header key User password salt Volume Master file key CUDA or Compute Unified Device Architecture is a parallel computing architecture developed by Nvidia. CUDA gives developers access to the virtual instruction set and memory of the parallel computational elements in CUDA GPUs. Each GPU is a collection of multicores. Each core can run mmore cuda «block», and each block can run a numbers of parallel «thread» 1. Level of parallilism : block 2. -

Analysis of Password Cracking Methods & Applications
The University of Akron IdeaExchange@UAkron The Dr. Gary B. and Pamela S. Williams Honors Honors Research Projects College Spring 2015 Analysis of Password Cracking Methods & Applications John A. Chester The University Of Akron, [email protected] Please take a moment to share how this work helps you through this survey. Your feedback will be important as we plan further development of our repository. Follow this and additional works at: http://ideaexchange.uakron.edu/honors_research_projects Part of the Information Security Commons Recommended Citation Chester, John A., "Analysis of Password Cracking Methods & Applications" (2015). Honors Research Projects. 7. http://ideaexchange.uakron.edu/honors_research_projects/7 This Honors Research Project is brought to you for free and open access by The Dr. Gary B. and Pamela S. Williams Honors College at IdeaExchange@UAkron, the institutional repository of The nivU ersity of Akron in Akron, Ohio, USA. It has been accepted for inclusion in Honors Research Projects by an authorized administrator of IdeaExchange@UAkron. For more information, please contact [email protected], [email protected]. Analysis of Password Cracking Methods & Applications John A. Chester The University of Akron Abstract -- This project examines the nature of password cracking and modern applications. Several applications for different platforms are studied. Different methods of cracking are explained, including dictionary attack, brute force, and rainbow tables. Password cracking across different mediums is examined. Hashing and how it affects password cracking is discussed. An implementation of two hash-based password cracking algorithms is developed, along with experimental results of their efficiency. I. Introduction Password cracking is the process of either guessing or recovering a password from stored locations or from a data transmission system [1]. -

Password Cracking Using Cain & Abel
Password Cracking Using Cain & Abel Learning Objectives: This exercise demonstrates how password could be cracked through various methods, specifically regarding MD5 encrypted passwords. Summary: You will use Cain & Abel for this exercise. Deliverables: Submit a lab report by answering the review questions. In some review questions, you may provide screen captures. Dictionary attack Dictionary attack uses a predetermined list of words from a dictionary to generate possible passwords that may match the MD5 encrypted password. This is one of the easiest and quickest way to obtain any given password. 1. Start Cain & Abel via the Desktop Shortcut ‘Cain’ or Start menu. a. (Start > Programs > Cain > Cain). 2. Choose ‘Yes’ to proceed when a ‘User Account Control’ notification pops up regarding software authorization. 3. Once on, select the ‘Cracker’ tab with the key symbol, then click on MD5 Hashes. The result should look like the image below. 1 Collaborative Virtual Computer Lab (CVCLAB) Penn State Berks 4. As you might have noticed we don’t have any passwords to crack, thus for the next few steps we will create our own MD5 encrypted passwords. First, locate the Hash Calculator among a row of icons near the top. Open it. 5. Next, type into ‘Text to Hash’ the word password. It will generate a list of hashes pertaining to different types of hash algorithms. We will be focusing on MD5 hash so copy it. Then exit calculator by clicking ‘Cancel’ (Fun Fact: Hashes are case sensitive so any slight changes to the text will change the hashes generated, try changing a letter or two and you will see. -

To Change Your Ud Password(S)
TO CHANGE YOUR UD PASSWORD(S) The MyCampus portal allows the user a single-signon for campus applications. IMPORTANT NOTICE AT BOTTOM OF THESE INSTRUCTIONS !! INITIAL PROCEDURE TO ALLOW YOU TO CHANGE YOUR PASSWORD ON THE UD NETWORK : 1. In your web browser, enter http://mycampus.dbq.edu . If you are logging in for the first time, you will be directed to answer (3) security questions. Also, be sure to answer one of the recovery methods. 2. Once the questions are answered, you will click on SUBMIT and then CONTINUE and then YES. 3. In one location, you will now find MyUD, Campus Portal, Email and UDOnline (Moodle). 4. You can now click on any of these apps and you will be logged in already. The email link will prompt you for the password a second time until we get all accounts set up properly. YOU MUST BE SURE TO LOGOUT OF EACH APPLICATION AFTER YOU’RE DONE USING IT !! TO CHANGE YOUR PASSWORD: 1. After you have logged into the MyCampus.dbq.edu website, you will see your username in the upper- right corner of the screen. 2. Click on your name and then go into My Account. 3. At the bottom, you will click on Change Password and then proceed as directed. 4. You can now logout. You will need to use your new password on your next login. Password must be a minimum of 6 characters and contain 3 of the following 4 categories: - Uppercase character - Lowercase character - Number - Special character You cannot use the previous password You’ll be required to change your password every 180 days. -
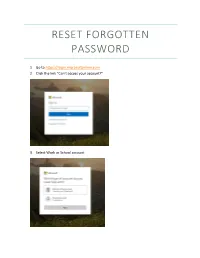
Reset Forgotten Password with Office365
RESET FORGOTTEN PASSWORD 1. Go to https://login.microsoftonline.com 2. Click the link “Can’t access your account?” 3. Select Work or School account 4. Enter in your User ID with the @uamont.edu at the end and then enter the characters as seen in the picture. You can click the refresh button for a different set of letters. 5. You will have 3 options to verify your account and reset your password. This information was set up when you registered with self-service password reset. If you have not registered, please go to https://aka.ms/ssprsetup and enter in your information. A step by step guide on how to do this can be found here. a. Text your mobile phone b. Call your mobile phone c. Answer Security Questions 6. Choose one option and enter the information requested 7. Click Text for text my mobile phone, Call for call my mobile phone, or click Next when you’ve answered all security questions. a. If you have selected Text my mobile phone you will be required to enter in a verification code and click Next b. If you have select Call my mobile phone you will receive a call and will need to enter # to verify. 8. Enter in your new password and click Finish a. Note: If you receive the message, “Unfortunately, your password contains a word, phrase, or pattern that makes it easily guessable. Please try again with a different password.” Please try to create a password that does not use any dictionary words. b. Passwords must meet 3 of the 4 following requirements i. -

Optimizing a Password Hashing Function with Hardware-Accelerated Symmetric Encryption
S S symmetry Article Optimizing a Password Hashing Function with Hardware-Accelerated Symmetric Encryption Rafael Álvarez 1,* , Alicia Andrade 2 and Antonio Zamora 3 1 Departamento de Ciencia de la Computación e Inteligencia Artificial (DCCIA), Universidad de Alicante, 03690 Alicante, Spain 2 Fac. Ingeniería, Ciencias Físicas y Matemática, Universidad Central, Quito 170129, Ecuador; [email protected] 3 Departamento de Ciencia de la Computación e Inteligencia Artificial (DCCIA), Universidad de Alicante, 03690 Alicante, Spain; [email protected] * Correspondence: [email protected] Received: 2 November 2018; Accepted: 22 November 2018; Published: 3 December 2018 Abstract: Password-based key derivation functions (PBKDFs) are commonly used to transform user passwords into keys for symmetric encryption, as well as for user authentication, password hashing, and preventing attacks based on custom hardware. We propose two optimized alternatives that enhance the performance of a previously published PBKDF. This design is based on (1) employing a symmetric cipher, the Advanced Encryption Standard (AES), as a pseudo-random generator and (2) taking advantage of the support for the hardware acceleration for AES that is available on many common platforms in order to mitigate common attacks to password-based user authentication systems. We also analyze their security characteristics, establishing that they are equivalent to the security of the core primitive (AES), and we compare their performance with well-known PBKDF algorithms, such as Scrypt and Argon2, with favorable results. Keywords: symmetric; encryption; password; hash; cryptography; PBKDF 1. Introduction Key derivation functions are employed to obtain one or more keys from a master secret. This is especially useful in the case of user passwords, which can be of arbitrary length and are unsuitable to be used directly as fixed-size cipher keys, so, there must be a process for converting passwords into secret keys. -

Strong Password-Based Authentication in TLS Using the Three-Party Group Diffie–Hellman Protocol
284 Int. J. Security and Networks, Vol. 2, Nos. 3/4, 2007 Strong password-based authentication in TLS using the three-party group Diffie–Hellman protocol Michel Abdalla* École normale supérieure – CNRS, LIENS, Paris, France E-mail: [email protected] *Corresponding author Emmanuel Bresson Department of Cryptology, CELAR Technology Center, Bruz, France E-mail: [email protected] Olivier Chevassut Lawrence Berkeley National Laboratory, Berkeley, CA, USA E-mail: [email protected] Bodo Möller Horst Görtz Institute for IT Security, Ruhr-Universität Bochum, Bochum, Germany E-mail: [email protected] David Pointcheval École normale supérieure – CNRS, LIENS, Paris, France E-mail: [email protected] Abstract: The internet has evolved into a very hostile ecosystem where ‘phishing’ attacks are common practice. This paper shows that the three-party group Diffie-Hellman key exchange can help protect against these attacks. We have developed password-based ciphersuites for the Transport Layer Security (TLS) protocol that are not only provably secure but also believed to be free from patent and licensing restrictions based on an analysis of relevant patents in the area. Keywords: password authentication; group Diffie–Hellman key exchange; transport layer security; TLS. Reference to this paper should be made as follows: Abdalla, M., Bresson, E., Chevassut, O., Möller, B. and Pointcheval, D. (2007) ‘Strong password-based authentication in TLS using the three-party group Diffie-Hellman protocol’, Int. J. Security and Networks, Vol. 2, Nos. 3/4, pp.284–296. Biographical notes: Michel Abdalla is currently a Researcher with the Centre National de la Recherche Scientifique (CNRS), France and a Member of the Cryptography Team at the Ecole Normale Supérieure (ENS), France. -

Passwords CS 166: Information Security Authentication: Passwords
Passwords CS 166: Information Security Authentication: Passwords Prof. Tom Austin San José State University Access Control • Authentication: Are you who you say you are? – Determine whether access is allowed – human to machine, or machine to machine • Authorization: Are you allowed to do that? – Once you have access, what can you do? – Enforces limits on actions Chapter 7: Authentication Guard: Halt! Who goes there? Arthur: It is I, Arthur, son of Uther Pendragon, from the castle of Camelot. King of the Britons, defeater of the Saxons, sovereign of all England! ¾ Monty Python and the Holy Grail Then said they unto him, Say now Shibboleth: and he said Sibboleth: for he could not frame to pronounce it right. Then they took him, and slew him at the passages of Jordan: and there fell at that time of the Ephraimites forty and two thousand. ¾ Judges 12:6 Authentication: Are You Who You Say You Are? • How to authenticate human a machine? • Can be based on… –Something you know • e.g. password –Something you have • e.g. smartcard –Something you are • e.g. fingerprint Something You Know • Passwords • Lots of things act as passwords! –PIN –Social security number –Mother’s maiden name –Date of birth –Name of your pet, etc. Why Passwords? • Why is “something you know” more popular than “something you have” and “something you are”? • Cost: passwords are free • Convenience: easier for admin to reset pwd than to issue a new thumb Authenticating with Passwords I am Thor Prove it My password is Mjölnir Authenticating with Passwords I am Thor Prove it My -

Password Cracking
Password Cracking Sam Martin and Mark Tokutomi 1 Introduction Passwords are a system designed to provide authentication. There are many different ways to authenticate users of a system: a user can present a physical object like a key card, prove identity using a personal characteristic like a fingerprint, or use something that only the user knows. In contrast to the other approaches listed, a primary benefit of using authentication through a pass- word is that in the event that your password becomes compromised it can be easily changed. This paper will discuss what password cracking is, techniques for password cracking when an attacker has the ability to attempt to log in to the system using a user name and password pair, techniques for when an attacker has access to however passwords are stored on the system, attacks involve observing password entry in some way and finally how graphical passwords and graphical password cracks work. Figure 1: The flow of password attacking possibilities. Figure 1 shows some scenarios attempts at password cracking can occur. The attacker can gain access to a machine through physical or remote access. The user could attempt to try each possible password or likely password (a form of dictionary attack). If the attack can gain access to hashes of the passwords it is possible to use software like OphCrack which utilizes Rainbow Tables to crack passwords[1]. A spammer may use dictionary attacks to gain access to bank accounts or other 1 web services as well. Wireless protocols are vulnerable to some password cracking techniques when packet sniffers are able to gain initialization packets. -

UGRD 2015 Spring Bugg Chris.Pdf (464.4Kb)
We could consider using the Mighty Cracker Logo located in the Network Folder MIGHTY CRACKER Chris Bugg Chris Hamm Jon Wright Nick Baum Password Security • Password security is important. • Users • Weak and/or reused passwords • Developers and Admins • Choose insecure storage algorithms. • Mighty Cracker • Show real world impact of poor password security. OVERVIEW • We made a hash cracker. • Passwords are stored as hashes to protect them from intruders. • Our program uses several methods to ‘crack’ those hashes. • Networking • Spread work to multiple machines. • Cross Platform OTHER HASH CRACKING PRODUCTS • Hashcat • Cain and Abel • John the Ripper • THC-Hydra • Ophcrack • Network support is rare. WHAT IS HASHING • A way to encode a password to help protect it. • A mathematical one-way function. • MD5 hash • cf4ff726403b8a992fd43e09dd7b5717 • SHA-256 hash • 951e689364c979cc3aa17e6b0022ce6e4d0e3200d1c22dd68492c172241e0623 SUPPORTED HASHING ALGORITHMS • Current Algorithms • MD5 • SHA-1 • SHA-224 • SHA-256 • SHA-384 • SHA-512 WAYS TO CRACK • Cracking Modes • Single User • Network Mode • Methods of Cracking: • Brute Force • Dictionary • Rainbow Table • GUI or Console BRUTE FORCE • Systematically checking all possible keys until the correct one is found. • Worst case this would transverse the entire search space. • Slowest but will always find the solution if given enough time. DICTIONARY ATTACK • List of common passwords from leaks/hacks. • Many people choose common passwords • Written works of Shakespeare ~66,000 words • Oxford English Dictionary ~290,000 words • Small dictionary = 900,000 words • Medium dictionary = 14 million words • Large dictionary = 1.2 billion words RAINBOW TABLE • Can’t store all possible hash/key combinations. • 16 character key = 10^40th combinations • 10^50th atoms on earth • Rainbow tables • Reduced storage. -

Modified SHA1: a Hashing Solution to Secure Web Applications Through Login Authentication
36 International Journal of Communication Networks and Information Security (IJCNIS) Vol. 11, No. 1, April 2019 Modified SHA1: A Hashing Solution to Secure Web Applications through Login Authentication Esmael V. Maliberan Graduate Studies, Surigao del Sur State University, Philippines Abstract: The modified SHA1 algorithm has been developed by attack against the SHA-1 hash function, generating two expanding its hash value up to 1280 bits from the original size of different PDF files. The research study conducted by [9] 160 bit. This was done by allocating 32 buffer registers for presented a specific freestart identical pair for SHA-1, i.e. a variables A, B, C and D at 5 bytes each. The expansion was done by collision within its compression function. This was the first generating 4 buffer registers in every round inside the compression appropriate break of the SHA-1, extending all 80 out of 80 function for 8 times. Findings revealed that the hash value of the steps. This attack was performed for only 10 days of modified algorithm was not cracked or hacked during the experiment and testing using powerful online cracking tool, brute computation on a 64-GPU. Thus, SHA1 algorithm is not force and rainbow table such as Cracking Station and Rainbow anymore safe in login authentication and data transfer. For Crack and bruteforcer which are available online thus improved its this reason, there were enhancements and modifications security level compared to the original SHA1. being developed in the algorithm in order to solve these issues [10, 11]. [12] proposed a new approach to enhance Keywords: SHA1, hashing, client-server communication, MD5 algorithm combined with SHA compression function modified SHA1, hacking, brute force, rainbow table that produced a 256-bit hash code.