Transport Layer Security Protocol for Spwfxxx Module
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Configuring DNS
Configuring DNS The Domain Name System (DNS) is a distributed database in which you can map hostnames to IP addresses through the DNS protocol from a DNS server. Each unique IP address can have an associated hostname. The Cisco IOS software maintains a cache of hostname-to-address mappings for use by the connect, telnet, and ping EXEC commands, and related Telnet support operations. This cache speeds the process of converting names to addresses. Note You can specify IPv4 and IPv6 addresses while performing various tasks in this feature. The resource record type AAAA is used to map a domain name to an IPv6 address. The IP6.ARPA domain is defined to look up a record given an IPv6 address. • Finding Feature Information, page 1 • Prerequisites for Configuring DNS, page 2 • Information About DNS, page 2 • How to Configure DNS, page 4 • Configuration Examples for DNS, page 13 • Additional References, page 14 • Feature Information for DNS, page 15 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required. -

A Survey on Authentication Methods for the Internet of Things
1 A survey on authentication methods for the 2 Internet of Things 1 3 Dylan Sey 1 4 School of Computing, Mathematics and Digital Technology 1 5 Manchester Metropolitan University 6 Corresponding author: 1 7 Dylan Sey 8 Email address: [email protected] 9 ABSTRACT 10 This survey focuses on authentication methods for the Internet of Things (IoT). There are many different 11 authentication methods that are used in the IT industry but not all of these can be adapted for the IoT. 12 Lightweight and mutual authentication methods will be covered in this paper, alongside two authentication 13 methods that are commonly used in other areas of the industry, rather than the IoT area, which are 14 Kerberos and Group audio-based authentication. The survey will find that Mutual authentication is vital 15 for the IoT and, due to the constraints that are apparent within the IoT devices; the lightweight option 16 is very useful when it comes to dealing with areas like low bandwidth. As a result, there will be gaps 17 that could be further investigated such as the advancement of the IoT technology so that more types 18 of authentication are feasible. A conclusion to this paper is that, by combining different methods of 19 encryption and authentication methods, there are always possibilities to make the proposed protocols 20 more lightweight and secure. 21 1 INTRODUCTION 22 This survey will discuss the different methods of the authentication within the Internet of Things (IoT) 23 and then go into one of these methods in further detail. -

V6.5 Data Sheet
Data Sheet Blue Prism Network Connectivity To ensure compatibility with evolving network infrastructures, Blue Prism can be deployed in environments that utilize IPv4 or IPv6 network protocols for all connections as well as those that use a hybrid approach, utilizing a combination of both protocols. This allows all Blue Prism components - Runtimes, Clients, Application Servers - to connect using the preferred or most suitable method. Resource connectivity When establishing connections to Runtime Resources, Blue Prism uses the name specified in the DNS. This is based on the machine name and can either the short name or the Fully Qualified Domain Name (FQDN). If a Resource has both IPv4 and IPv6 addresses in the DNS, the network adapter settings of the connecting device (Application Server, Interactive Client, or Resource) are used to determine which IP address should be used to establish the connection: 1. The connecting device defaults to an IPv6 connection. 2. If an IPv6 connection is not established within 1.5 seconds and if the connecting device has multiple IPv6 addresses listed in the DNS, a connection attempt is made using the next available IPv6 address. 3. If an IPv6 connection is not established, the connecting device automatically attempts to connect using IPv4. 4. If all available IPv4 addresses have been tried without success, the Resource is considered unreachable. Commercial in Confidence Page 1 of 3 ®Blue Prism is a registerd trademark of Blue Prism Limited 6.5 Data Sheet | Blue Prism Network Connectivity Resource connectivity The following diagram illustrates the logic used for connections to Runtime Resources. Commercial in Confidence Page 2 of 3 ®Blue Prism is a registerd trademark of Blue Prism Limited 6.5 Data Sheet | Blue Prism Network Connectivity Application Server connectivity Application Server connectivity Clients and Resources can connect to Application Servers using the host name, IPv4 address, or IPv6 address specified in the connection settings on the Server Configuration Details screen. -

Intro to Cryptography 1 Introduction 2 Secure Password Manager
Programming Assignment 1 Winter 2021 CS 255: Intro to Cryptography Prof. Dan Boneh Due Monday, Feb. 8, 11:59pm 1 Introduction In many software systems today, the primary weakness often lies in the user’s password. This is especially apparent in light of recent security breaches that have highlighted some of the weak passwords people commonly use (e.g., 123456 or password). It is very important, then, that users choose strong passwords (or “passphrases”) to secure their accounts, but strong passwords can be long and unwieldy. Even more problematic, the user generally has many different services that use password authentication, and as a result, the user has to recall many different passwords. One way for users to address this problem is to use a password manager, such as LastPass and KeePass. Password managers make it very convenient for users to use a unique, strong password for each service that requires password authentication. However, given the sensitivity of the data contained in the password manager, it takes considerable care to store the information securely. In this assignment, you will be writing a secure and efficient password manager. In your implemen- tation, you will make use of various cryptographic primitives we have discussed in class—notably, authenticated encryption and collision-resistant hash functions. Because it is ill-advised to imple- ment your own primitives in cryptography, you should use an established library: in this case, the Stanford Javascript Crypto Library (SJCL). We will provide starter code that contains a basic tem- plate, which you will be able to fill in to satisfy the functionality and security properties described below. -

Changing IP Address and Hostname for Cisco Unified Communications Manager and IM and Presence Service, Release 11.5(1) First Published
Changing IP Address and Hostname for Cisco Unified Communications Manager and IM and Presence Service, Release 11.5(1) First Published: Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB's public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS" WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

User Authentication and Cryptographic Primitives
User Authentication and Cryptographic Primitives Brad Karp UCL Computer Science CS GZ03 / M030 16th November 2016 Outline • Authenticating users – Local users: hashed passwords – Remote users: s/key – Unexpected covert channel: the Tenex password- guessing attack • Symmetric-key-cryptography • Public-key cryptography usage model • RSA algorithm for public-key cryptography – Number theory background – Algorithm definition 2 Dictionary Attack on Hashed Password Databases • Suppose hacker obtains copy of password file (until recently, world-readable on UNIX) • Compute H(x) for 50K common words • String compare resulting hashed words against passwords in file • Learn all users’ passwords that are common English words after only 50K computations of H(x)! • Same hashed dictionary works on all password files in world! 3 Salted Password Hashes • Generate a random string of bytes, r • For user password x, store [H(r,x), r] in password file • Result: same password produces different result on every machine – So must see password file before can hash dictionary – …and single hashed dictionary won’t work for multiple hosts • Modern UNIX: password hashes salted; hashed password database readable only by root 4 Salted Password Hashes • Generate a random string of bytes, r Dictionary• For user password attack still x, store possible [H(r,x after), r] in attacker seespassword password file file! Users• Result: should same pick password passwords produces that different aren’t result close to ondictionary every machine words. – So must see password file -

To Change Your Ud Password(S)
TO CHANGE YOUR UD PASSWORD(S) The MyCampus portal allows the user a single-signon for campus applications. IMPORTANT NOTICE AT BOTTOM OF THESE INSTRUCTIONS !! INITIAL PROCEDURE TO ALLOW YOU TO CHANGE YOUR PASSWORD ON THE UD NETWORK : 1. In your web browser, enter http://mycampus.dbq.edu . If you are logging in for the first time, you will be directed to answer (3) security questions. Also, be sure to answer one of the recovery methods. 2. Once the questions are answered, you will click on SUBMIT and then CONTINUE and then YES. 3. In one location, you will now find MyUD, Campus Portal, Email and UDOnline (Moodle). 4. You can now click on any of these apps and you will be logged in already. The email link will prompt you for the password a second time until we get all accounts set up properly. YOU MUST BE SURE TO LOGOUT OF EACH APPLICATION AFTER YOU’RE DONE USING IT !! TO CHANGE YOUR PASSWORD: 1. After you have logged into the MyCampus.dbq.edu website, you will see your username in the upper- right corner of the screen. 2. Click on your name and then go into My Account. 3. At the bottom, you will click on Change Password and then proceed as directed. 4. You can now logout. You will need to use your new password on your next login. Password must be a minimum of 6 characters and contain 3 of the following 4 categories: - Uppercase character - Lowercase character - Number - Special character You cannot use the previous password You’ll be required to change your password every 180 days. -
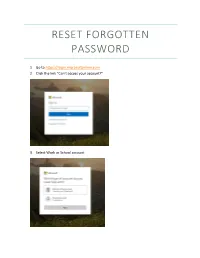
Reset Forgotten Password with Office365
RESET FORGOTTEN PASSWORD 1. Go to https://login.microsoftonline.com 2. Click the link “Can’t access your account?” 3. Select Work or School account 4. Enter in your User ID with the @uamont.edu at the end and then enter the characters as seen in the picture. You can click the refresh button for a different set of letters. 5. You will have 3 options to verify your account and reset your password. This information was set up when you registered with self-service password reset. If you have not registered, please go to https://aka.ms/ssprsetup and enter in your information. A step by step guide on how to do this can be found here. a. Text your mobile phone b. Call your mobile phone c. Answer Security Questions 6. Choose one option and enter the information requested 7. Click Text for text my mobile phone, Call for call my mobile phone, or click Next when you’ve answered all security questions. a. If you have selected Text my mobile phone you will be required to enter in a verification code and click Next b. If you have select Call my mobile phone you will receive a call and will need to enter # to verify. 8. Enter in your new password and click Finish a. Note: If you receive the message, “Unfortunately, your password contains a word, phrase, or pattern that makes it easily guessable. Please try again with a different password.” Please try to create a password that does not use any dictionary words. b. Passwords must meet 3 of the 4 following requirements i. -

Configuring Smart Licensing
Configuring Smart Licensing • Prerequisites for Configuring Smart Licensing, on page 1 • Introduction to Smart Licensing, on page 1 • Connecting to CSSM, on page 2 • Linking Existing Licenses to CSSM, on page 4 • Configuring a Connection to CSSM and Setting Up the License Level, on page 4 • Registering a Device on CSSM, on page 14 • Monitoring Smart Licensing Configuration, on page 19 • Configuration Examples for Smart Licensing, on page 20 • Additional References, on page 26 • Feature History for Smart Licensing, on page 27 Prerequisites for Configuring Smart Licensing • Release requirements: Smart Licensing is supported from Cisco IOS XE Fuji 16.9.2 to Cisco IOS XE Amsterdam 17.3.1. (Starting with Cisco IOS XE Amsterdam 17.3.2a, Smart Licensing Using Policy is supported.) • CSSM requirements: • Cisco Smart Account • One or more Virtual Account • User role with proper access rights • You should have accepted the Smart Software Licensing Agreement on CSSM to register devices. • Network reachability to https://tools.cisco.com. Introduction to Smart Licensing Cisco Smart Licensing is a flexible licensing model that provides you with an easier, faster, and more consistent way to purchase and manage software across the Cisco portfolio and across your organization. And it’s secure – you control what users can access. With Smart Licensing you get: Configuring Smart Licensing 1 Configuring Smart Licensing Overview of CSSM • Easy Activation: Smart Licensing establishes a pool of software licenses that can be used across the entire organization—no more PAKs (Product Activation Keys). • Unified Management: My Cisco Entitlements (MCE) provides a complete view into all of your Cisco products and services in an easy-to-use portal, so you always know what you have and what you are using. -

Optimizing a Password Hashing Function with Hardware-Accelerated Symmetric Encryption
S S symmetry Article Optimizing a Password Hashing Function with Hardware-Accelerated Symmetric Encryption Rafael Álvarez 1,* , Alicia Andrade 2 and Antonio Zamora 3 1 Departamento de Ciencia de la Computación e Inteligencia Artificial (DCCIA), Universidad de Alicante, 03690 Alicante, Spain 2 Fac. Ingeniería, Ciencias Físicas y Matemática, Universidad Central, Quito 170129, Ecuador; [email protected] 3 Departamento de Ciencia de la Computación e Inteligencia Artificial (DCCIA), Universidad de Alicante, 03690 Alicante, Spain; [email protected] * Correspondence: [email protected] Received: 2 November 2018; Accepted: 22 November 2018; Published: 3 December 2018 Abstract: Password-based key derivation functions (PBKDFs) are commonly used to transform user passwords into keys for symmetric encryption, as well as for user authentication, password hashing, and preventing attacks based on custom hardware. We propose two optimized alternatives that enhance the performance of a previously published PBKDF. This design is based on (1) employing a symmetric cipher, the Advanced Encryption Standard (AES), as a pseudo-random generator and (2) taking advantage of the support for the hardware acceleration for AES that is available on many common platforms in order to mitigate common attacks to password-based user authentication systems. We also analyze their security characteristics, establishing that they are equivalent to the security of the core primitive (AES), and we compare their performance with well-known PBKDF algorithms, such as Scrypt and Argon2, with favorable results. Keywords: symmetric; encryption; password; hash; cryptography; PBKDF 1. Introduction Key derivation functions are employed to obtain one or more keys from a master secret. This is especially useful in the case of user passwords, which can be of arbitrary length and are unsuitable to be used directly as fixed-size cipher keys, so, there must be a process for converting passwords into secret keys. -

Efficient Mutual Authentication for Multi-Domain RFID Systems Using
Efficient Mutual Authentication for Multi-domain RFID Systems Using Distributed Signatures Michael Braun1, Ulrike Meyer2, and Susanne Wetzel3 1 University of Applied Sciences Darmstadt, Germany 2 RWTH Aachen University, Germany 3 Stevens Institute of Technology, Hoboken, NJ, US Abstract. The use of RFID technology in complex and distributed en- vironments often leads to a multi-domain RFID system in which security issues such as authentication of tags and readers, granting access to data, and revocation of readers turn into an administrative challenge. In this paper, we propose a new public-key-based mutual authentication pro- tocol that addresses the reader revocation problem while maintaining efficiency and identity privacy. In addition, our new protocol integrates fine-grained access control and key establishment with mutual authenti- cation. The core of our solution is the use of the concepts of key-splitting and distributed signatures to solve the validation and revocation prob- lem. We show that our protocols can be implemented on RFID tags using lightweight implementations of elliptic curve cryptography. Keywords: RFID Security, Elliptic Curve Cryptography, Authentica- tion, Data on Tag, Secret Sharing, Distributed Signatures, Key Splitting, Identity Privacy. 1 Introduction Radio Frequency Identification (RFID) technology has become a ubiquitous part of our daily lives. Prominent applications include logistics and electronic travel documents. While in early applications only a unique identifier was stored on an RFID tag, a more recent trend leans towards storing more information on the tag. For example, the new electronic passports include sensitive data such as fingerprints as well as the facial image of the passport holder. As a consequence, security challenges have evolved from protecting the identifier and preventing tag cloning to enabling fine-grained access control to the data stored on the tag and enabling secure data exchange between the reader and the tag. -

Strong Password-Based Authentication in TLS Using the Three-Party Group Diffie–Hellman Protocol
284 Int. J. Security and Networks, Vol. 2, Nos. 3/4, 2007 Strong password-based authentication in TLS using the three-party group Diffie–Hellman protocol Michel Abdalla* École normale supérieure – CNRS, LIENS, Paris, France E-mail: [email protected] *Corresponding author Emmanuel Bresson Department of Cryptology, CELAR Technology Center, Bruz, France E-mail: [email protected] Olivier Chevassut Lawrence Berkeley National Laboratory, Berkeley, CA, USA E-mail: [email protected] Bodo Möller Horst Görtz Institute for IT Security, Ruhr-Universität Bochum, Bochum, Germany E-mail: [email protected] David Pointcheval École normale supérieure – CNRS, LIENS, Paris, France E-mail: [email protected] Abstract: The internet has evolved into a very hostile ecosystem where ‘phishing’ attacks are common practice. This paper shows that the three-party group Diffie-Hellman key exchange can help protect against these attacks. We have developed password-based ciphersuites for the Transport Layer Security (TLS) protocol that are not only provably secure but also believed to be free from patent and licensing restrictions based on an analysis of relevant patents in the area. Keywords: password authentication; group Diffie–Hellman key exchange; transport layer security; TLS. Reference to this paper should be made as follows: Abdalla, M., Bresson, E., Chevassut, O., Möller, B. and Pointcheval, D. (2007) ‘Strong password-based authentication in TLS using the three-party group Diffie-Hellman protocol’, Int. J. Security and Networks, Vol. 2, Nos. 3/4, pp.284–296. Biographical notes: Michel Abdalla is currently a Researcher with the Centre National de la Recherche Scientifique (CNRS), France and a Member of the Cryptography Team at the Ecole Normale Supérieure (ENS), France.