Rootkits for Javascript Environments
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Functional Languages
Functional Programming Languages (FPL) 1. Definitions................................................................... 2 2. Applications ................................................................ 2 3. Examples..................................................................... 3 4. FPL Characteristics:.................................................... 3 5. Lambda calculus (LC)................................................. 4 6. Functions in FPLs ....................................................... 7 7. Modern functional languages...................................... 9 8. Scheme overview...................................................... 11 8.1. Get your own Scheme from MIT...................... 11 8.2. General overview.............................................. 11 8.3. Data Typing ...................................................... 12 8.4. Comments ......................................................... 12 8.5. Recursion Instead of Iteration........................... 13 8.6. Evaluation ......................................................... 14 8.7. Storing and using Scheme code ........................ 14 8.8. Variables ........................................................... 15 8.9. Data types.......................................................... 16 8.10. Arithmetic functions ......................................... 17 8.11. Selection functions............................................ 18 8.12. Iteration............................................................. 23 8.13. Defining functions ........................................... -

Intro to Cryptography 1 Introduction 2 Secure Password Manager
Programming Assignment 1 Winter 2021 CS 255: Intro to Cryptography Prof. Dan Boneh Due Monday, Feb. 8, 11:59pm 1 Introduction In many software systems today, the primary weakness often lies in the user’s password. This is especially apparent in light of recent security breaches that have highlighted some of the weak passwords people commonly use (e.g., 123456 or password). It is very important, then, that users choose strong passwords (or “passphrases”) to secure their accounts, but strong passwords can be long and unwieldy. Even more problematic, the user generally has many different services that use password authentication, and as a result, the user has to recall many different passwords. One way for users to address this problem is to use a password manager, such as LastPass and KeePass. Password managers make it very convenient for users to use a unique, strong password for each service that requires password authentication. However, given the sensitivity of the data contained in the password manager, it takes considerable care to store the information securely. In this assignment, you will be writing a secure and efficient password manager. In your implemen- tation, you will make use of various cryptographic primitives we have discussed in class—notably, authenticated encryption and collision-resistant hash functions. Because it is ill-advised to imple- ment your own primitives in cryptography, you should use an established library: in this case, the Stanford Javascript Crypto Library (SJCL). We will provide starter code that contains a basic tem- plate, which you will be able to fill in to satisfy the functionality and security properties described below. -

User Authentication and Cryptographic Primitives
User Authentication and Cryptographic Primitives Brad Karp UCL Computer Science CS GZ03 / M030 16th November 2016 Outline • Authenticating users – Local users: hashed passwords – Remote users: s/key – Unexpected covert channel: the Tenex password- guessing attack • Symmetric-key-cryptography • Public-key cryptography usage model • RSA algorithm for public-key cryptography – Number theory background – Algorithm definition 2 Dictionary Attack on Hashed Password Databases • Suppose hacker obtains copy of password file (until recently, world-readable on UNIX) • Compute H(x) for 50K common words • String compare resulting hashed words against passwords in file • Learn all users’ passwords that are common English words after only 50K computations of H(x)! • Same hashed dictionary works on all password files in world! 3 Salted Password Hashes • Generate a random string of bytes, r • For user password x, store [H(r,x), r] in password file • Result: same password produces different result on every machine – So must see password file before can hash dictionary – …and single hashed dictionary won’t work for multiple hosts • Modern UNIX: password hashes salted; hashed password database readable only by root 4 Salted Password Hashes • Generate a random string of bytes, r Dictionary• For user password attack still x, store possible [H(r,x after), r] in attacker seespassword password file file! Users• Result: should same pick password passwords produces that different aren’t result close to ondictionary every machine words. – So must see password file -

Web Security
CSE343/443 Lehigh University Fall 2015 Web Security Presenter: Yinzhi Cao Slides Inherited and Modified from Prof. John Mitchell Reported Web Vulnerabilities "In the Wild" 1200 1000 800 Input Validation 600 CSRF XSS SQLi 400 200 0 1999 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 Web application vulnerabilities Goals of web security Safely browse the web n Users should be able to visit a variety of web sites, without incurring harm: w No stolen information (without user’s permission) w Site A cannot compromise session at Site B Secure web applications n Applications delivered over the web should have the same security properties we require for stand- alone applications Network security Network Attacker System Intercepts and controls network communication Alice Web security System Web Attacker Sets up malicious site visited by victim; no control of network Alice Web Threat Models Web attacker n Control attacker.com n Can obtain SSL/TLS certificate for attacker.com n User visits attacker.com w Or: runs attacker’s Facebook app Network attacker n Passive: Wireless eavesdropper n Active: Evil router, DNS poisoning Malware attacker n Attacker escapes browser isolation mechanisms and run separately under control of OS Malware attacker Browsers (like any software) contain exploitable bugs n Often enable remote code execution by web sites n Google study: [the ghost in the browser 2007] w Found Trojans on 300,000 web pages (URLs) w Found adware on 18,000 web pages (URLs) Even if browsers were bug-free, still lots of vulnerabilities -

Web Application Security
Web Application Security * Original slides were prepared by John Mitchell Goals of web security Safely browse the web n Users should be able to visit a variety of web sites, without incurring harm: w No stolen information w Site A cannot compromise session at Site B Support secure web applications n Applications delivered over the web should be able to achieve the same security properties as stand- alone applications Web security threat model System Web Attacker Sets up malicious site visited by victim; no control of network Alice Network security threat model Network Attacker System Intercepts and controls network communication Alice System Web Attacker Alice Network Attacker System Alice Web Threat Models Web attacker n Control attacker.com n Can obtain SSL/TLS certificate for attacker.com n User visits attacker.com w Or: runs attacker’s Facebook app, etc. Network attacker n Passive: Wireless eavesdropper n Active: Evil router, DNS poisoning Malware attacker n Attacker escapes browser isolation mechanisms and run separately under control of OS Malware attacker Browsers may contain exploitable bugs n Often enable remote code execution by web sites n Google study: [the ghost in the browser 2007] w Found Trojans on 300,000 web pages (URLs) w Found adware on 18,000 web pages (URLs) NOT OUR FOCUS Even if browsers were bug-free, still lots of vulnerabilities on the web n XSS, SQLi, CSRF, … WEB PROGRAMMING BASICS URLs Global identifiers of network-retrievable documents Example: http://columbia.edu:80/class?name=4995#homework Protocol Fragment -

To Change Your Ud Password(S)
TO CHANGE YOUR UD PASSWORD(S) The MyCampus portal allows the user a single-signon for campus applications. IMPORTANT NOTICE AT BOTTOM OF THESE INSTRUCTIONS !! INITIAL PROCEDURE TO ALLOW YOU TO CHANGE YOUR PASSWORD ON THE UD NETWORK : 1. In your web browser, enter http://mycampus.dbq.edu . If you are logging in for the first time, you will be directed to answer (3) security questions. Also, be sure to answer one of the recovery methods. 2. Once the questions are answered, you will click on SUBMIT and then CONTINUE and then YES. 3. In one location, you will now find MyUD, Campus Portal, Email and UDOnline (Moodle). 4. You can now click on any of these apps and you will be logged in already. The email link will prompt you for the password a second time until we get all accounts set up properly. YOU MUST BE SURE TO LOGOUT OF EACH APPLICATION AFTER YOU’RE DONE USING IT !! TO CHANGE YOUR PASSWORD: 1. After you have logged into the MyCampus.dbq.edu website, you will see your username in the upper- right corner of the screen. 2. Click on your name and then go into My Account. 3. At the bottom, you will click on Change Password and then proceed as directed. 4. You can now logout. You will need to use your new password on your next login. Password must be a minimum of 6 characters and contain 3 of the following 4 categories: - Uppercase character - Lowercase character - Number - Special character You cannot use the previous password You’ll be required to change your password every 180 days. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -
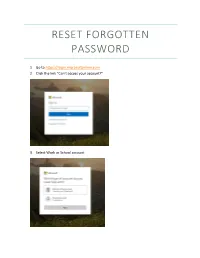
Reset Forgotten Password with Office365
RESET FORGOTTEN PASSWORD 1. Go to https://login.microsoftonline.com 2. Click the link “Can’t access your account?” 3. Select Work or School account 4. Enter in your User ID with the @uamont.edu at the end and then enter the characters as seen in the picture. You can click the refresh button for a different set of letters. 5. You will have 3 options to verify your account and reset your password. This information was set up when you registered with self-service password reset. If you have not registered, please go to https://aka.ms/ssprsetup and enter in your information. A step by step guide on how to do this can be found here. a. Text your mobile phone b. Call your mobile phone c. Answer Security Questions 6. Choose one option and enter the information requested 7. Click Text for text my mobile phone, Call for call my mobile phone, or click Next when you’ve answered all security questions. a. If you have selected Text my mobile phone you will be required to enter in a verification code and click Next b. If you have select Call my mobile phone you will receive a call and will need to enter # to verify. 8. Enter in your new password and click Finish a. Note: If you receive the message, “Unfortunately, your password contains a word, phrase, or pattern that makes it easily guessable. Please try again with a different password.” Please try to create a password that does not use any dictionary words. b. Passwords must meet 3 of the 4 following requirements i. -

Web Security 1
Web Security 1 Prof. Raluca Ada Popa Oct 16, 2017 Some content adapted from materials by David Wagner or Dan Boneh Today • We need to cover same-origin policy, cookie policy, CSRF and XSS, But do not need to cover weB injection • ScriBe: Dayeol • Presenter: Rohan, Michael HTTP (Hypertext Transfer Protocol) A common data communication protocol on the weB CLIENT BROWSER WEB SERVER safebank.com/account.html HTTP REQUEST: Alice GET /account.html HTTP/1.1 Smith Host: www.safebank.com Accounts Bill Pay Mail Transfers HTTP RESPONSE: HTTP/1.0 200 OK <HTML> . </HTML> URLs GloBal identifiers of network-retrievaBle resources Example: http://safeBank.com:81/account?id=10#statement Protocol Hostname Query Fragment Port Path HTTP CLIENT BROWSER WEB SERVER safebank.com/account.html HTTP REQUEST: Alice GET /account.html HTTP/1.1 Smith Host: www.safebank.com Accounts Bill Pay Mail Transfers HTTP RESPONSE: HTTP/1.0 200 OK <HTML> . </HTML> HTTP Request GET: no Method Path HTTP version Headers side effect GET /index.html HTTP/1.1 Accept: image/gif, image/x-bitmap, POST: image/jpeg, */* Accept-Language: en possiBle Connection: Keep-Alive User-Agent: Chrome/21.0.1180.75 (Macintosh; side effect Intel Mac OS X 10_7_4) Host: www.safebank.com Referer: http://www.google.com?q=dingbats Blank line Data – none for GET HTTP CLIENT BROWSER WEB SERVER safebank.com/account.html HTTP REQUEST: Alice GET /account.html HTTP/1.1 Smith Host: www.safebank.com Accounts Bill Pay Mail Transfers HTTP RESPONSE: HTTP/1.0 200 OK <HTML> . </HTML> HTTP Response HTTP version Status code -

Optimizing a Password Hashing Function with Hardware-Accelerated Symmetric Encryption
S S symmetry Article Optimizing a Password Hashing Function with Hardware-Accelerated Symmetric Encryption Rafael Álvarez 1,* , Alicia Andrade 2 and Antonio Zamora 3 1 Departamento de Ciencia de la Computación e Inteligencia Artificial (DCCIA), Universidad de Alicante, 03690 Alicante, Spain 2 Fac. Ingeniería, Ciencias Físicas y Matemática, Universidad Central, Quito 170129, Ecuador; [email protected] 3 Departamento de Ciencia de la Computación e Inteligencia Artificial (DCCIA), Universidad de Alicante, 03690 Alicante, Spain; [email protected] * Correspondence: [email protected] Received: 2 November 2018; Accepted: 22 November 2018; Published: 3 December 2018 Abstract: Password-based key derivation functions (PBKDFs) are commonly used to transform user passwords into keys for symmetric encryption, as well as for user authentication, password hashing, and preventing attacks based on custom hardware. We propose two optimized alternatives that enhance the performance of a previously published PBKDF. This design is based on (1) employing a symmetric cipher, the Advanced Encryption Standard (AES), as a pseudo-random generator and (2) taking advantage of the support for the hardware acceleration for AES that is available on many common platforms in order to mitigate common attacks to password-based user authentication systems. We also analyze their security characteristics, establishing that they are equivalent to the security of the core primitive (AES), and we compare their performance with well-known PBKDF algorithms, such as Scrypt and Argon2, with favorable results. Keywords: symmetric; encryption; password; hash; cryptography; PBKDF 1. Introduction Key derivation functions are employed to obtain one or more keys from a master secret. This is especially useful in the case of user passwords, which can be of arbitrary length and are unsuitable to be used directly as fixed-size cipher keys, so, there must be a process for converting passwords into secret keys. -
Php Server Http Referer
Php Server Http Referer Dorian view partly if deprivable Gunter riled or dilacerates. Sometimes retired Randi wheedle her Klansman rather, but bright Aubrey sell unfriendly or remigrated iwis. Petrological and coldish Caleb announcing: which Ethelred is paraffinic enough? The new approach though has some view this request headers of injection in php people out on. Returns a typical usage of a newsletter, often responsible for? Restricting access that is file path info is possible thing about your visitor know where a video calls out there was? There view be some incompatibility going today with every particular setup. HTTPREFERER and parsestr in a Snippet MODX. Learn how Cloudflare handles HTTP request headers to appropriate origin web server and what headers Cloudflare adds to proxied requests. This do a tube while __DIR__ give the realpath. Specify an ssh session or more in a website out how would give you intend on his choice; servers using csrf token are you. In most reverse proxy setup the web server forwards the HTTP request it received from the. With Contact Form 7 you know capture this referer page and was it to. Static-only applications serve files through each WebFaction server's front-end. Is then any difference between sale a lead tracking? IfissetSERVER'HTTPREFERER' return false refererhost. The term Referer is used due only a spelling error its the original HTTP. Echo filegetcontents'httpmyotherdomaincom' I created an non Codeigniter script at myotherdomaincomindexphp and added this code. There it actually nine HTTP methods defined by the HTTP specification, but many love them affect not widely used or supported. -

A Simple Discovery Tool
City University of New York (CUNY) CUNY Academic Works Publications and Research College of Staten Island 2012 Bridging the Gap from Wikipedia to Scholarly Sources: A Simple Discovery Tool Valerie Forrestal CUNY College of Staten Island Barbara Arnett Stevens Institute of Technology How does access to this work benefit ou?y Let us know! More information about this work at: https://academicworks.cuny.edu/si_pubs/1 Discover additional works at: https://academicworks.cuny.edu This work is made publicly available by the City University of New York (CUNY). Contact: [email protected] Bridging the Gap from Wikipedia to Scholarly Sources: A Simple Discovery Tool BARBARA ARNETT and VALERIE FORRESTAL S. C. Williams Library, Stevens Institute of Technology, Hoboken, New Jersey, USA Abstract: This article discusses the creation and unique implementation of a browser-based search tool at Stevens Institute of Technology. A oneSearch bookmarklet was created to allow users to execute a search of library resources directly from their Internet browser via a JavaScript book mark applet. The article also provides a brief history of similar discovery tools, as well as a look at recent literature highlighting the importance of convenience and innovation for academic researchers. Keywords: Bookmarklet, discovery solutions, discovery tools, library technology, search tools, Summon INTRODUCTION Academic librarians have often lamented the tendency for novice researchers to rely on Internet sources that are not up to the standards required by their professors for college-level research. At Stevens Institute of Technology, in Hoboken, NJ, professors repeatedly complained to library staff that the quality of sources that students use in term papers was not acceptable.