(Pdf) of from Push/Enter to Eval/Apply by Program Transformation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Functional Languages
Functional Programming Languages (FPL) 1. Definitions................................................................... 2 2. Applications ................................................................ 2 3. Examples..................................................................... 3 4. FPL Characteristics:.................................................... 3 5. Lambda calculus (LC)................................................. 4 6. Functions in FPLs ....................................................... 7 7. Modern functional languages...................................... 9 8. Scheme overview...................................................... 11 8.1. Get your own Scheme from MIT...................... 11 8.2. General overview.............................................. 11 8.3. Data Typing ...................................................... 12 8.4. Comments ......................................................... 12 8.5. Recursion Instead of Iteration........................... 13 8.6. Evaluation ......................................................... 14 8.7. Storing and using Scheme code ........................ 14 8.8. Variables ........................................................... 15 8.9. Data types.......................................................... 16 8.10. Arithmetic functions ......................................... 17 8.11. Selection functions............................................ 18 8.12. Iteration............................................................. 23 8.13. Defining functions ........................................... -

Stepping Ocaml
Stepping OCaml TsukinoFurukawa YouyouCong KenichiAsai Ochanomizu University Tokyo, Japan {furukawa.tsukino, so.yuyu, asai}@is.ocha.ac.jp Steppers, which display all the reduction steps of a given program, are a novice-friendly tool for un- derstanding program behavior. Unfortunately, steppers are not as popular as they ought to be; indeed, the tool is only available in the pedagogical languages of the DrRacket programming environment. We present a stepper for a practical fragment of OCaml. Similarly to the DrRacket stepper, we keep track of evaluation contexts in order to reconstruct the whole program at each reduction step. The difference is that we support effectful constructs, such as exception handling and printing primitives, allowing the stepper to assist a wider range of users. In this paper, we describe the implementationof the stepper, share the feedback from our students, and show an attempt at assessing the educational impact of our stepper. 1 Introduction Programmers spend a considerable amount of time and effort on debugging. In particular, novice pro- grammers may find this process extremely painful, since existing debuggers are usually not friendly enough to beginners. To use a debugger, we have to first learn what kinds of commands are available, and figure out which would be useful for the current purpose. It would be even harder to use the com- mand in a meaningful manner: for instance, to spot the source of an unexpected behavior, we must be able to find the right places to insert breakpoints, which requires some programming experience. Then, is there any debugging tool that is accessible to first-day programmers? In our view, the algebraic stepper [1] of DrRacket, a pedagogical programming environment for the Racket language, serves as such a tool. -

A Practical Introduction to Python Programming
A Practical Introduction to Python Programming Brian Heinold Department of Mathematics and Computer Science Mount St. Mary’s University ii ©2012 Brian Heinold Licensed under a Creative Commons Attribution-Noncommercial-Share Alike 3.0 Unported Li- cense Contents I Basics1 1 Getting Started 3 1.1 Installing Python..............................................3 1.2 IDLE......................................................3 1.3 A first program...............................................4 1.4 Typing things in...............................................5 1.5 Getting input.................................................6 1.6 Printing....................................................6 1.7 Variables...................................................7 1.8 Exercises...................................................9 2 For loops 11 2.1 Examples................................................... 11 2.2 The loop variable.............................................. 13 2.3 The range function............................................ 13 2.4 A Trickier Example............................................. 14 2.5 Exercises................................................... 15 3 Numbers 19 3.1 Integers and Decimal Numbers.................................... 19 3.2 Math Operators............................................... 19 3.3 Order of operations............................................ 21 3.4 Random numbers............................................. 21 3.5 Math functions............................................... 21 3.6 Getting -

Making a Faster Curry with Extensional Types
Making a Faster Curry with Extensional Types Paul Downen Simon Peyton Jones Zachary Sullivan Microsoft Research Zena M. Ariola Cambridge, UK University of Oregon [email protected] Eugene, Oregon, USA [email protected] [email protected] [email protected] Abstract 1 Introduction Curried functions apparently take one argument at a time, Consider these two function definitions: which is slow. So optimizing compilers for higher-order lan- guages invariably have some mechanism for working around f1 = λx: let z = h x x in λy:e y z currying by passing several arguments at once, as many as f = λx:λy: let z = h x x in e y z the function can handle, which is known as its arity. But 2 such mechanisms are often ad-hoc, and do not work at all in higher-order functions. We show how extensional, call- It is highly desirable for an optimizing compiler to η ex- by-name functions have the correct behavior for directly pand f1 into f2. The function f1 takes only a single argu- expressing the arity of curried functions. And these exten- ment before returning a heap-allocated function closure; sional functions can stand side-by-side with functions native then that closure must subsequently be called by passing the to practical programming languages, which do not use call- second argument. In contrast, f2 can take both arguments by-name evaluation. Integrating call-by-name with other at once, without constructing an intermediate closure, and evaluation strategies in the same intermediate language ex- this can make a huge difference to run-time performance in presses the arity of a function in its type and gives a princi- practice [Marlow and Peyton Jones 2004]. -

Advanced Tcl E D
PART II I I . A d v a n c Advanced Tcl e d T c l Part II describes advanced programming techniques that support sophisticated applications. The Tcl interfaces remain simple, so you can quickly construct pow- erful applications. Chapter 10 describes eval, which lets you create Tcl programs on the fly. There are tricks with using eval correctly, and a few rules of thumb to make your life easier. Chapter 11 describes regular expressions. This is the most powerful string processing facility in Tcl. This chapter includes a cookbook of useful regular expressions. Chapter 12 describes the library and package facility used to organize your code into reusable modules. Chapter 13 describes introspection and debugging. Introspection provides information about the state of the Tcl interpreter. Chapter 14 describes namespaces that partition the global scope for vari- ables and procedures. Namespaces help you structure large Tcl applications. Chapter 15 describes the features that support Internationalization, includ- ing Unicode, other character set encodings, and message catalogs. Chapter 16 describes event-driven I/O programming. This lets you run pro- cess pipelines in the background. It is also very useful with network socket pro- gramming, which is the topic of Chapter 17. Chapter 18 describes TclHttpd, a Web server built entirely in Tcl. You can build applications on top of TclHttpd, or integrate the server into existing appli- cations to give them a web interface. TclHttpd also supports regular Web sites. Chapter 19 describes Safe-Tcl and using multiple Tcl interpreters. You can create multiple Tcl interpreters for your application. If an interpreter is safe, then you can grant it restricted functionality. -
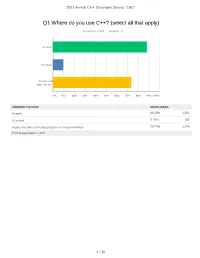
Q1 Where Do You Use C++? (Select All That Apply)
2021 Annual C++ Developer Survey "Lite" Q1 Where do you use C++? (select all that apply) Answered: 1,870 Skipped: 3 At work At school In personal time, for ho... 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES At work 88.29% 1,651 At school 9.79% 183 In personal time, for hobby projects or to try new things 73.74% 1,379 Total Respondents: 1,870 1 / 35 2021 Annual C++ Developer Survey "Lite" Q2 How many years of programming experience do you have in C++ specifically? Answered: 1,869 Skipped: 4 1-2 years 3-5 years 6-10 years 10-20 years >20 years 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES 1-2 years 7.60% 142 3-5 years 20.60% 385 6-10 years 20.71% 387 10-20 years 30.02% 561 >20 years 21.08% 394 TOTAL 1,869 2 / 35 2021 Annual C++ Developer Survey "Lite" Q3 How many years of programming experience do you have overall (all languages)? Answered: 1,865 Skipped: 8 1-2 years 3-5 years 6-10 years 10-20 years >20 years 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES 1-2 years 1.02% 19 3-5 years 12.17% 227 6-10 years 22.68% 423 10-20 years 29.71% 554 >20 years 34.42% 642 TOTAL 1,865 3 / 35 2021 Annual C++ Developer Survey "Lite" Q4 What types of projects do you work on? (select all that apply) Answered: 1,861 Skipped: 12 Gaming (e.g., console and.. -

CSE 341 : Programming Languages
CSE 341 : Programming Languages Lecture 10 Closure Idioms Zach Tatlock Spring 2014 More idioms • We know the rule for lexical scope and function closures – Now what is it good for A partial but wide-ranging list: • Pass functions with private data to iterators: Done • Combine functions (e.g., composition) • Currying (multi-arg functions and partial application) • Callbacks (e.g., in reactive programming) • Implementing an ADT with a record of functions (optional) 2 Combine functions Canonical example is function composition: fun compose (f,g) = fn x => f (g x) • Creates a closure that “remembers” what f and g are bound to • Type ('b -> 'c) * ('a -> 'b) -> ('a -> 'c) but the REPL prints something equivalent • ML standard library provides this as infix operator o • Example (third version best): fun sqrt_of_abs i = Math.sqrt(Real.fromInt(abs i)) fun sqrt_of_abs i = (Math.sqrt o Real.fromInt o abs) i val sqrt_of_abs = Math.sqrt o Real.fromInt o abs 3 Left-to-right or right-to-left val sqrt_of_abs = Math.sqrt o Real.fromInt o abs As in math, function composition is “right to left” – “take absolute value, convert to real, and take square root” – “square root of the conversion to real of absolute value” “Pipelines” of functions are common in functional programming and many programmers prefer left-to-right – Can define our own infix operator – This one is very popular (and predefined) in F# infix |> fun x |> f = f x fun sqrt_of_abs i = i |> abs |> Real.fromInt |> Math.sqrt 4 Another example • “Backup function” fun backup1 (f,g) = fn x => case -

CSE341, Fall 2011, Lecture 17 Summary
CSE341, Fall 2011, Lecture 17 Summary Standard Disclaimer: This lecture summary is not necessarily a complete substitute for attending class, reading the associated code, etc. It is designed to be a useful resource for students who attended class and are later reviewing the material. This lecture covers three topics that are all directly relevant to the upcoming homework assignment in which you will use Racket to write an interpreter for a small programming language: • Racket's structs for defining new (dynamic) types in Racket and contrasting them with manually tagged lists [This material was actually covered in the \Monday section" and only briefly reviewed in the other materials for this lecture.] • How a programming language can be implemented in another programming language, including key stages/concepts like parsing, compilation, interpretation, and variants thereof • How to implement higher-order functions and closures by explicitly managing and storing environments at run-time One-of types with lists and dynamic typing In ML, we studied one-of types (in the form of datatype bindings) almost from the beginning, since they were essential for defining many kinds of data. Racket's dynamic typing makes the issue less central since we can simply use primitives like booleans and cons cells to build anything we want. Building lists and trees out of dynamically typed pairs is particularly straightforward. However, the concept of one-of types is still prevalent. For example, a list is null or a cons cell where there cdr holds a list. Moreover, Racket extends its Scheme predecessor with something very similar to ML's constructors | a special form called struct | and it is instructive to contrast the two language's approaches. -

Specialising Dynamic Techniques for Implementing the Ruby Programming Language
SPECIALISING DYNAMIC TECHNIQUES FOR IMPLEMENTING THE RUBY PROGRAMMING LANGUAGE A thesis submitted to the University of Manchester for the degree of Doctor of Philosophy in the Faculty of Engineering and Physical Sciences 2015 By Chris Seaton School of Computer Science This published copy of the thesis contains a couple of minor typographical corrections from the version deposited in the University of Manchester Library. [email protected] chrisseaton.com/phd 2 Contents List of Listings7 List of Tables9 List of Figures 11 Abstract 15 Declaration 17 Copyright 19 Acknowledgements 21 1 Introduction 23 1.1 Dynamic Programming Languages.................. 23 1.2 Idiomatic Ruby............................ 25 1.3 Research Questions.......................... 27 1.4 Implementation Work......................... 27 1.5 Contributions............................. 28 1.6 Publications.............................. 29 1.7 Thesis Structure............................ 31 2 Characteristics of Dynamic Languages 35 2.1 Ruby.................................. 35 2.2 Ruby on Rails............................. 36 2.3 Case Study: Idiomatic Ruby..................... 37 2.4 Summary............................... 49 3 3 Implementation of Dynamic Languages 51 3.1 Foundational Techniques....................... 51 3.2 Applied Techniques.......................... 59 3.3 Implementations of Ruby....................... 65 3.4 Parallelism and Concurrency..................... 72 3.5 Summary............................... 73 4 Evaluation Methodology 75 4.1 Evaluation Philosophy -

Rootkits for Javascript Environments
Rootkits for JavaScript Environments Ben Adida Adam Barth Collin Jackson Harvard University UC Berkeley Stanford University ben [email protected] [email protected] [email protected] Abstract Web Site Bookmarklet Web Site Bookmarklet A number of commercial cloud-based password managers use bookmarklets to automatically populate and submit login forms. Unfortunately, an attacker web Native JavaScript environment site can maliciously alter the JavaScript environment and, when the login bookmarklet is invoked, steal the Figure 1. Developers assume the bookmarklet in- user’s passwords. We describe general attack tech- teracts with the native JavaScript environment directly niques for altering a bookmarklet’s JavaScript envi- (left). In fact, the bookmarklet’s environment can be ronment and apply them to extracting passwords from manipulated by the current web page (right). six commercial password managers. Our proposed solution has been adopted by several of the commercial vendors. If the user clicks a bookmarklet while visiting an untrusted web page, the bookmarklet’s JavaScript is run in the context of the malicious page, potentially 1. Introduction letting an attacker manipulate its execution by care- fully crafting its JavaScript environment, essentially One promising direction for building engaging web installing a “rootkit” in its own JavaScript environment experiences is to combine content and functionality (See Figure 1). Instead of interacting with the native from multiple sources, often called a “mashup.” In JavaScript objects, the bookmarklet interacts with the a traditional mashup, an integrator combines gadgets attacker’s objects. This attack vector is not much of (such as advertisements [1], maps [2], or contact a concern for Delicious’ social bookmarking service, lists [3]), but an increasingly popular mashup design because the site’s own interests are served by advertis- involves the user adding a bookmarklet [4] (also known ing its true location and title. -

Language Design and Implementation Using Ruby and the Interpreter Pattern
Language Design and Implementation using Ruby and the Interpreter Pattern Ariel Ortiz Information Technology Department Tecnológico de Monterrey, Campus Estado de México Atizapán de Zaragoza, Estado de México, Mexico. 52926 [email protected] ABSTRACT to explore different language concepts and programming styles. In this paper, the S-expression Interpreter Framework (SIF) is Section 4 describes briefly how the SIF has been used in class. presented as a tool for teaching language design and The conclusions are found in section 5. implementation. The SIF is based on the interpreter design pattern and is written in the Ruby programming language. Its core is quite 1.1 S-Expressions S-expressions (symbolic expressions) are a parenthesized prefix small, but it can be easily extended by adding primitive notation, mainly used in the Lisp family languages. They were procedures and special forms. The SIF can be used to demonstrate selected as the framework’s source language notation because advanced language concepts (variable scopes, continuations, etc.) they offer important advantages: as well as different programming styles (functional, imperative, and object oriented). • Both code and data can be easily represented. Adding a new language construct is pretty straightforward. • Categories and Subject Descriptors The number of program elements is minimal, thus a parser is − relatively easy to write. D.3.4 [Programming Languages]: Processors interpreters, • run-time environments. The arity of operators doesn’t need to be fixed, so, for example, the + operator can be defined to accept any number of arguments. General Terms • There are no problems regarding operator precedence or Design, Languages. associativity, because every operator has its own pair of parentheses. -

Functional Programming Lecture 1: Introduction
Functional Programming Lecture 4: Closures and lazy evaluation Viliam Lisý Artificial Intelligence Center Department of Computer Science FEE, Czech Technical University in Prague [email protected] Last lecture • Functions with variable number of arguments • Higher order functions – map, foldr, foldl, filter, compose Binding scopes A portion of the source code where a value is bound to a given name • Lexical scope – functions use bindings available where defined • Dynamic scope – functions use bindings available where executed Ben Wood's slides Eval Eval is a function defined in the top level context (define x 5) (define (f y) (eval '(+ x y))) Fails because of lexical scoping Otherwise the following would be problematic (define (eval x) (eval-expanded (macro-expand x))) Eval in R5RS (eval expression environment) Where the environment is one of (interaction-environment) (global defines) (scheme-report-environment x) (before defines) (null-environment x) (only special forms) None of them allows seeing local bindings Cons (define (my-cons x y) (lambda (m) (m x y))) (define (my-car p) (p (lambda (x y) x))) (define (my-cdr s) (p (lambda (x y) y))) Currying Transforms function to allow partial application not curried 푓: 퐴 × 퐵 → 퐶 curried 푓: 퐴 → (퐵 → 퐶) not curried 푓: 퐴 × 퐵 × 퐶 → 퐷 curried 푓: 퐴 → (퐵 → 퐶 → 퐷 ) Picture: Haskell Curry from Wikipedia Currying (define (my-curry1 f) (lambda args (lambda rest (apply f (append args rest))))) (define (my-curry f) (define (c-wrap f stored-args) (lambda args (let ((all (append stored-args args)))