Anti-Cyber Bullying Statutes: Threat to Student Free Speech
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Competing Theories of Blackmail: an Empirical Research Critique of Criminal Law Theory
Competing Theories of Blackmail: An Empirical Research Critique of Criminal Law Theory Paul H. Robinson,* Michael T. Cahill** & Daniel M. Bartels*** The crime of blackmail has risen to national media attention because of the David Letterman case, but this wonderfully curious offense has long been the favorite of clever criminal law theorists. It criminalizes the threat to do something that would not be criminal if one did it. There exists a rich liter- ature on the issue, with many prominent legal scholars offering their accounts. Each theorist has his own explanation as to why the blackmail offense exists. Most theories seek to justify the position that blackmail is a moral wrong and claim to offer an account that reflects widely shared moral intuitions. But the theories make widely varying assertions about what those shared intuitions are, while also lacking any evidence to support the assertions. This Article summarizes the results of an empirical study designed to test the competing theories of blackmail to see which best accords with pre- vailing sentiment. Using a variety of scenarios designed to isolate and test the various criteria different theorists have put forth as “the” key to blackmail, this study reveals which (if any) of the various theories of blackmail proposed to date truly reflects laypeople’s moral judgment. Blackmail is not only a common subject of scholarly theorizing but also a common object of criminal prohibition. Every American jurisdiction criminalizes blackmail, although there is considerable variation in its formulation. The Article reviews the American statutes and describes the three general approaches these provisions reflect. -

Definitions of Child Abuse and Neglect
STATE STATUTES Current Through March 2019 WHAT’S INSIDE Defining child abuse or Definitions of Child neglect in State law Abuse and Neglect Standards for reporting Child abuse and neglect are defined by Federal Persons responsible for the child and State laws. At the State level, child abuse and neglect may be defined in both civil and criminal Exceptions statutes. This publication presents civil definitions that determine the grounds for intervention by Summaries of State laws State child protective agencies.1 At the Federal level, the Child Abuse Prevention and Treatment To find statute information for a Act (CAPTA) has defined child abuse and neglect particular State, as "any recent act or failure to act on the part go to of a parent or caregiver that results in death, https://www.childwelfare. serious physical or emotional harm, sexual abuse, gov/topics/systemwide/ or exploitation, or an act or failure to act that laws-policies/state/. presents an imminent risk of serious harm."2 1 States also may define child abuse and neglect in criminal statutes. These definitions provide the grounds for the arrest and prosecution of the offenders. 2 CAPTA Reauthorization Act of 2010 (P.L. 111-320), 42 U.S.C. § 5101, Note (§ 3). Children’s Bureau/ACYF/ACF/HHS 800.394.3366 | Email: [email protected] | https://www.childwelfare.gov Definitions of Child Abuse and Neglect https://www.childwelfare.gov CAPTA defines sexual abuse as follows: and neglect in statute.5 States recognize the different types of abuse in their definitions, including physical abuse, The employment, use, persuasion, inducement, neglect, sexual abuse, and emotional abuse. -

Brandenburg in a Time of Terror Thomas Healy
Notre Dame Law Review Volume 84 | Issue 2 Article 3 1-1-2009 Brandenburg in a Time of Terror Thomas Healy Follow this and additional works at: http://scholarship.law.nd.edu/ndlr Recommended Citation Thomas Healy, Brandenburg in a Time of Terror, 84 Notre Dame L. Rev. 655 (2009). Available at: http://scholarship.law.nd.edu/ndlr/vol84/iss2/3 This Article is brought to you for free and open access by NDLScholarship. It has been accepted for inclusion in Notre Dame Law Review by an authorized administrator of NDLScholarship. For more information, please contact [email protected]. BRANDENBURG IN A TIME OF TERROR Thomas Healy* Forfour decades, the Supreme Court's decision in Brandenburg v. Ohio has been celebrated as a landmark in First Amendment law. In one short unsigned opinion, the Court distanced itselffrom the embarrassment of the Red Scare and adopted a highly protective test that permits advocacy of unlawful conduct in all but the most dangerous cases. But 9/11 and the threat of terror- ism pose a new challenge to Brandenburg. Although the government has not resorted to the excesses of McCarthyism, it has taken disturbing steps to silence the speech of political dissenters. These efforts raise questions about the ade- quacy of Brandenburg to protect speech during a time of crisis andfear. They also highlight ambiguities in the Brandenburg test that have been largely ignored by courts. For instance, does Brandenburg apply during war as well as peace? Does it apply to private advocacy as well as public advocacy? And is there anything about the current terrorist threat that would make its protections inapplicable? To answer these and other important questions, this Article undertakes a comprehensive reexamination of Brandenburg and the issue of criminal advocacy. -
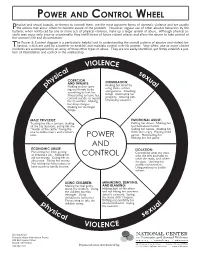
Power and Control Wheel NO SHADING
POOWERWER AANDND COONTROLNTROL WHHEELEEL hysical and sexual assaults, or threats to commit them, are the most apparent forms of domestic violence and are usually Pthe actions that allow others to become aware of the problem. However, regular use of other abusive behaviors by the batterer, when reinforced by one or more acts of physical violence, make up a larger system of abuse. Although physical as- saults may occur only once or occasionally, they instill threat of future violent attacks and allow the abuser to take control of the woman’s life and circumstances. he Power & Control diagram is a particularly helpful tool in understanding the overall pattern of abusive and violent be- Thaviors, which are used by a batterer to establish and maintain control over his partner. Very often, one or more violent incidents are accompanied by an array of these other types of abuse. They are less easily identified, yet firmly establish a pat- tern of intimidation and control in the relationship. VIOLENCE l a se sic x y COERCION u AND THREATS: INTIMIDATION: a h Making her afraid by p Making and/or carry- l ing out threats to do using looks, actions, something to hurt her. and gestures. Smashing Threatening to leave her, things. Destroying her commit suicide, or report property. Abusing pets. her to welfare. Making Displaying weapons. her drop charges. Making her do illegal things. MALE PRIVILEGE: EMOTIONAL ABUSE: Treating her like a servant: making Putting her down. Making her all the big decisions, acting like the feel bad about herself. “master of the castle,” being the Calling her names. -

Retaliatory Hate Crime
Bias Crime Offenders Session C Overview of the Session: At a Glance Presentation: Offender Typology 30 minutes Presentation: Organized Hate Groups 15 minutes Activity: Analysis of Three Video Segments 45 minutes TOTAL TIME 90 minutes Objectives By the end of this session, participants will be able to: • Describe the characteristics of three types of bias crime offenders • Give examples of retaliatory hate crimes and discuss the impor- tance of appropriate responses • Describe the characteristics of organized hate groups • Identify offender typology, given a case example Materials and Equipment Time: 90 minutes Videos: “That Old Gang of Mine” (interview with Eric, former skinhead), 1990 “On Hate Street,” 48 Hours, CBS, 1992 “Licensed to Kill,” Arthur Dong, Deepfocus Productions, 1997 (See page 56 for ordering information.) Handouts: Thrill-Seeking Offenders; Case Studies of Typical Offenders; Reactive Offenders; Mission Offenders; Offender Typology Video Observation Form Transparencies: Important of Understanding Offender Typology; Retaliatory Hate Crimes; Organized Hate Groups Equipment: Overhead projector; screen; VCR; monitor Session C. Bias Crime Offenders Instructor’s Notes I. Presentation: Offender Typology (30 minutes) Explain the following: • Jack Levin and Jack McDevitt of Northeastern University identified three different types of hate crime offenders in their book on bias crime, Hate Crime: The Rising Tide of Bigotry and Bloodshed: thrill-seeking offenders, reactive offenders, and mission offenders. • These are not necessarily -

Supreme Court of the United States ______
Team Q No. 16-9999 IN THE Supreme Court of the United States _________ SCHOOL DISTRICT OF WASHINGTON COUNTY, NEW COLUMBIA Petitioner, v. KIMBERLY CLARK, a minor, by and through her father ALAN CLARK Respondent. _________ On Writ of Certiorari to the United States Court of Appeals for the Fourteenth Circuit _________ BRIEF OF PETITIONER _________ SVEN LINDBLOM BAKER & REILLY, LLP For Petitioner QUESTIONS PRESENTED 1. Whether a public high school student’sFacebook post constituted a “true threat” beyond the protection of the First Amendment? 2. Whether a public school district violated a high school student’sFirst Amendment rights by disciplining her for a Facebook post initiated off campus on her personal computer where school authorities conclude that the post was materially disruptive and collided with the rights of other students to be secure at school? i BRIEF CERTIFICATE Team Letter Q certifies the following: 1. The work product contained in all copies of this team’sbrief is in fact the work product of the team members, 2. This team has complied fully with the school’sgoverning honor code, and 3. This team has complied with all Rules of the Competition. ii TABLE OF CONTENTS QUESTIONS PRESENTED............................................................................................................ i BRIEF CERTIFICATE................................................................................................................... ii TABLE OF CONTENTS.............................................................................................................. -

Bullying Policy and Procedure
Talmadge Middle School Harassment, Intimidation, and Bullying Policy & Procedures The tactic of making another student’s life miserable, or making him or her feel intimidated or threatened, will not be tolerated. Be Respectful and treat others the way you want to be treated. If you bully another student physically, verbally, or even non-verbally, you will receive immediate consequences. Bullying and harassment are now criminal offenses in the state of Oregon. Depending on the extent of the infraction, local police officials may be called in order to issue a citation along with a referral to juvenile authorities. Students who feel they are being bullied need to seek assistance and report it to an adult. Talmadge staff will protect the identity of those students who report bullying or other behaviors. Students, if you see another student being bullied please show integrity by speaking out: tell the bully to stop and help the student being bullied to seek assistance. Central School District 13J School Board Policy JFCF: Harassment, intimidation, or bullying means any act that substantially interferes with a students’ educational benefits, opportunities or performance, that takes place on or immediately adjacent to district grounds, at any district-sponsored activity, on district- provided transportation or at any official district bus stop, that my be based on, but not limited to, the protected class status of a person, having the effect of: 1. Physically harming a student or damaging a student’s property; 2. Knowingly placing a student in reasonable fear of physical harm to the student or damage to the student’s property; 3. -

Bullying and Harassment - What's the Difference? Bullying and Harassment - What's the Difference?
Leadership & Strategy » HR for Leaders » Bullying » Bullying and Harassment - What's the Difference? Bullying and Harassment - What's the Difference? Bullying and harassment are terms that are used interchangeably by organisations, with bullying often regarded as a type of harassment. There are, however, some notable differences, which are particularly important to bear in mind if you are drawing up an anti-bullying policy. This article gives an overview of what these main differences are. Defining harassment Definitions of harassment tend to refer to behaviour which is offensive and intrusive, with a sexual, racial or physical element. ACAS defines harassment as: ‘Unwanted conduct that violates people’s dignity or creates an intimidating hostile, degrading, humiliating or offensive environment.’ [1] Harassment is covered in law by acts such as the Sex Discrimination Act, the Race Relations Act, the Disability Discrimination Act and the Criminal Justice and Public Order Act, as well as the laws of common assault. Defining bullying There are many ways to define bullying, with no single definition used across the board. ACAS, again, suggests the following: ‘Offensive, intimidating, malicious or insulting behaviour, an abuse or misuse of power through means intended to undermine, humiliate, denigrate or injure the recipient.’ The Andrea Adams Trust defined bullying as: [2] Unwarranted humiliating or offensive behaviour towards an individual or groups of employees. Persistently negative malicious attacks on personal or professional performance typically characterised as unpredictable, unfair, irrational and often unseen. An abuse of power or position that can cause such anxiety that people gradually lose all belief in themselves, suffering physical ill health and mental distress as a direct result. -

Cyberbullying
Cyberbullying: Intervention and Prevention Strategies BY TED FEINBERG, EDD, NCSP, National Association of School Psychologists, Bethesda, MD NICOLE ROBEY, MA, Cumberland County Schools, MD Brian was a shy, quiet boy who was labeled a social outcast by his classmates. A group of students created an online chat room devoted to making fun of Brian, and they invited him to join, telling him that they wanted to be his friends. This harassment drove Brian to depression and he eventually dropped out of school. Jessica and Ashley were best friends until they started liking the same guy. Jessica posted information on a social networking website that Ashley had told her in confidence. She also posted embarrassing pictures of Ashley. Almost everyone at school read about Ashley’s secret and saw the pictures. Ashley was humiliated. American teens make frequent use of the Internet for such activities as communicating with friends, finding information for school assignments, and downloading music. Recent research (e.g., McQuade & Sampat, 2008) suggests that nearly all youth in middle and high school with access to a computer at home or school will use the Internet and that this represents a rapid increase over the past decade. The number of teens with online profiles, including those on social networking sites like Facebook and MySpace, has also increased, and there is evidence that many of these teens who access the Internet at home make efforts to keep their activity away from parental scrutiny. In 2006, national law enforcement leaders estimated that more than 13 million children and adolescents ages 6–17 were victims of cyberbullying (Fight Crime: Invest in Kids, 2006). -

Informational Blackmail: Survived by Technicality? Chen Yehudai
Marquette Law Review Volume 92 Article 6 Issue 4 Summer 2009 Informational Blackmail: Survived by Technicality? Chen Yehudai Follow this and additional works at: http://scholarship.law.marquette.edu/mulr Part of the Law Commons Repository Citation Chen Yehudai, Informational Blackmail: Survived by Technicality?, 92 Marq. L. Rev. 779 (2009). Available at: http://scholarship.law.marquette.edu/mulr/vol92/iss4/6 This Article is brought to you for free and open access by the Journals at Marquette Law Scholarly Commons. It has been accepted for inclusion in Marquette Law Review by an authorized administrator of Marquette Law Scholarly Commons. For more information, please contact [email protected]. INFORMATIONAL BLACKMAIL: SURVIVED BY TECHNICALITY? CHEN YEHUDAI Blackmail constitutes one of the most intriguing puzzles in criminal law: How can two legal rights—i.e., a threat to disclose true but reputation-damaging information and, independently, a simple demand for money—make a legal wrong? The puzzle gets even more complicated when we take into account that it is not unlawful for one who holds embarrassing information to accept an offer of payment made by an unthreatened recipient in return for a promise not to disclose the information. In order to answer this question, this Article surveys and analyzes the development of the law of informational blackmail and criminal libel in English and American law and argues that the modern crime of blackmail is the result of an “historical accident” stemming from the historical classification of blackmail as a property offense instead of a reputation-protecting offense. The Article argues that when enacted, the prohibition on informational blackmail was meant to protect the interest of reputation as a supplement to the law of criminal libel. -

Taking Psychological Torture Seriously
University of Baltimore Law ScholarWorks@University of Baltimore School of Law All Faculty Scholarship Faculty Scholarship 2019 Taking Psychological Torture Seriously: The Torturous Nature of Credible Death Threats and the Collateral Consequences for Capital Punishment John Bessler University of Baltimore School of Law, [email protected] Follow this and additional works at: https://scholarworks.law.ubalt.edu/all_fac Part of the Criminal Law Commons, and the Criminal Procedure Commons Recommended Citation John Bessler, Taking Psychological Torture Seriously: The Torturous Nature of Credible Death Threats and the Collateral Consequences for Capital Punishment, 11 Northeastern University Law Review 1 (2019). Available at: https://scholarworks.law.ubalt.edu/all_fac/1080 This Article is brought to you for free and open access by the Faculty Scholarship at ScholarWorks@University of Baltimore School of Law. It has been accepted for inclusion in All Faculty Scholarship by an authorized administrator of ScholarWorks@University of Baltimore School of Law. For more information, please contact [email protected]. VOL. 11, NO. 1 NORTHEASTERN UNIVERSITY LAW REVIEW 1 Taking Psychological Torture Seriously: The Torturous Nature of Credible Death Threats and the Collateral Consequences for Capital Punishment By John D. Bessler* * Associate Professor, University of Baltimore School of Law; Adjunct Professor, Georgetown University Law Center; Visiting Scholar/Research Fellow, Human Rights Center, University of Minnesota Law School (Spring 2018); Of Counsel, Berens & Miller, P.A., Minneapolis, Minnesota. 2 Bessler Table of Contents I. Introduction ...................................................................................3 II. The Illegality and Torturous Nature of Threats of Death ....... 14 A. Existing Legal Protections Against Death Threats Against Individuals.................................................................................... 14 B. Death Threats, Persecution, and the U.S. -

Model Hate Crime Protocol
A Model Hate Crime Protocol Appendix A SAN DIEGO COUNTY REGIONAL HATE CRIMES PROCEDURE MANUAL October 1999 The Law Enforcement Training Subcommittee of the San Diego (California) Hate Crimes Community Working Group created this procedure manual. They received help from many experts from the state of California and also borrowed materials from the hate crimes training manuals created by the United States Department of Justice and the training curricula created by the California Peace Officers Standards and Training Hate Crimes Committees. Examples of Hate Crimes vs. Hate Incidents This protocol, developed Hate crimes are crimes motivated by bias against a victim based on his or by the San Diego Hate her actual or perceived race, religion, sexual orientation, gender, ethnicity, Crimes Community national origin, or disability. Hate incidents are similarly motivated but lack Working Group, is the elements of damage to property, harm—or the immediate threat of harm— provided as a useful or violence. Examples of hate incidents as compared to hate crimes are as model for agencies follows: looking to develop policies and procedures I. Example for preventing and A. Hate Incident responding to hate Three young male toughs purposely stand outside a convenience store in a crime. Agencies will residential section of town where young, professional gay men and lesbian find the information on women are known to live. As two men thought to be gay exit the store, all prevention and on the three toughs begin taunting the perceived gay men, calling them insulting roles of law enforce- and derogatory names. No physical contact or threats are made, but the ment officers humiliating verbal barrage does not end until the perceived gay men enter particularly helpful.