Cyberbullying
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cyber Violence Against Women and Girls
CYBER VIOLENCE AGAINST WOMEN AND GIRLS A WORLD-WIDE WAKE-UP CALL 2015 Photo credits:Shutterstock A REPORT BY THE UN BROADBAND COMMISSION FOR DIGITAL DEVELOPMENT WORKING GROUP ON BROADBAND AND GENDER CYBER VIOLENCE AGAINST WOMEN AND GIRLS: A WORLD-WIDE WAKE-UP CALL Acknowledgements This Report has been written collaboratively, drawing on insights and rich contributions from a range of Commissioners and Expert Members of the Working Group on Broadband and Gender. It has been researched and compiled by lead author Nidhi Tandon, assisted by Shannon Pritchard, with editorial inputs by teams from UN Women, UNDP and ITU. Design concepts were developed by Céline Desthomas of ITU. We wish to thank the following people for their contributions and kind review and comments (listed in alphabetical order of institution, followed by alphabetical order of surname): Dafne Sabanes Plou, Jac sm Kee and Chat Garcia Ramilo (APC); Dr Nancy Hafkin; Minerva Novero- Belec (UNDP); Corat Suniye Gulser (UNESCO); Jennifer Breslin and team (UN Women); Samia Melhem and team (World Bank). About the Commission The Broadband Commission for Digital Development was launched by the International Telecommunication Union (ITU) and the United Nations Educational, Scientific and Cultural Organization (UNESCO) in response to UN Secretary-General Ban Ki-moon’s call to step up efforts to meet the Millennium Development Goals. Established in May 2010, the Commission unites top industry executives with government leaders, thought leaders and policy pioneers and international agencies and organizations concerned with development. The Broadband Commission embraces a range of different perspectives in a multi-stakeholder approach to promoting the roll-out of broadband, as well as providing a fresh approach to UN and business engagement. -

OCSA Bullying/Cyberbullying/Hate Violence Policy
OCSA BULLYING/CYBER BULLYING/HATE VIOLENCE POLICY All students and employees of the Orange County School of the Arts have the right to work, to attend school, and to participate in the educational process in a safe environment that is free from bullying and hate-motivated behavior. Every effort shall be made to promote mutual respect among students and staff and between and among students to encourage safe and harmonious relations that support human dignity and equality. The OCSA Board of Trustees recognizes the harmful effects of bullying on student learning and school attendance and desires to provide safe school environments that protect students from physical and emotional harm. School employees shall establish student safety as a high priority and shall not tolerate bullying of any student. No student or group of students shall, through physical, written, verbal, or other means, harass, sexually harass, threaten, intimidate, cyberbully, cause bodily injury to, or commit hate violence against any other student or school personnel. Students who have been bullied or cyberbullied shall promptly report such incidents to any staff member. Behavior or statements that degrade, intimidate, and/or harm an individual on the basis of his/her race, ethnicity, culture, heritage, immigration status, gender, sexual orientation, physical/mental attributes, religious beliefs or practices shall not be tolerated. Bullying in any form or platform, repeatedly picking fights with, or repeatedly taunting another person shall not be tolerated. This policy applies to all OCSA students and employees. This policy applies to all acts related to school activity or school attendance occurring within a school under the jurisdiction of the Executive Director of the Orange County School of the Arts. -

Competing Theories of Blackmail: an Empirical Research Critique of Criminal Law Theory
Competing Theories of Blackmail: An Empirical Research Critique of Criminal Law Theory Paul H. Robinson,* Michael T. Cahill** & Daniel M. Bartels*** The crime of blackmail has risen to national media attention because of the David Letterman case, but this wonderfully curious offense has long been the favorite of clever criminal law theorists. It criminalizes the threat to do something that would not be criminal if one did it. There exists a rich liter- ature on the issue, with many prominent legal scholars offering their accounts. Each theorist has his own explanation as to why the blackmail offense exists. Most theories seek to justify the position that blackmail is a moral wrong and claim to offer an account that reflects widely shared moral intuitions. But the theories make widely varying assertions about what those shared intuitions are, while also lacking any evidence to support the assertions. This Article summarizes the results of an empirical study designed to test the competing theories of blackmail to see which best accords with pre- vailing sentiment. Using a variety of scenarios designed to isolate and test the various criteria different theorists have put forth as “the” key to blackmail, this study reveals which (if any) of the various theories of blackmail proposed to date truly reflects laypeople’s moral judgment. Blackmail is not only a common subject of scholarly theorizing but also a common object of criminal prohibition. Every American jurisdiction criminalizes blackmail, although there is considerable variation in its formulation. The Article reviews the American statutes and describes the three general approaches these provisions reflect. -

The Challenges of Cyberbullying
NEW ENCOUNTERS? THE CHALLENGES OF CYBERBULLYING Professor Shauna Van Praagh & Alyssa Wiseman November 17, 2015 What is Cyberbullying? "A person is bullied when he or she is exposed, repeatedly and over time, to negative actions on the part of one or more other persons, and he or she has difficulty defending himself or herself." - Dan Olweus (1993 and before) -An Act to prevent and stop bullying and violence in schools, 2012 Definition is fairly consistent worldwide—entails three criteria: (1) Verbal or physical aggression; (2) That is repeated over time; and (3) That involves a power differential. “Sticks and Stones” “I couldn’t write about online bullying without writing about face-to-face bullying too because Facebook and other social networking sites aren’t a discrete, walled off universe.” (39) - Emily Bazelon, “Sticks and Stones: Defeating the Culture of Bullying and Rediscovering the Power of Character and Empathy Despite wide media attention, cyberbullying is not necessarily more widespread than face-to-face bullying. Still, cyberbullying presents new concerns... “Sticks and Stones” New concerns include: (1) The Internet makes bullying harder to escape; (2) The Internet allows the perpetrator to bully without having to confront his or her victim; (3) The number of potential witnesses can be exponentially higher; and (4) There is the possibility that comments and images/ videos can go viral. Also, with undefined boundaries, whose responsibility is it to prevent or “deal” with cyberbullying? “It’s Complicated” danah boyd brings to light problematic tendencies and reactions: (1) Scapegoating technology: easier to focus on what is tangible rather than broader systemic issues at play; (2) Parental nostalgia: we idealize our childhoods and forget the problem we faced when we were young; (3) “Digital natives”: draws away attention from the problems children face in the digital era In creating these divides, different stakeholders may absolve themselves of responsibility. -

Definitions of Child Abuse and Neglect
STATE STATUTES Current Through March 2019 WHAT’S INSIDE Defining child abuse or Definitions of Child neglect in State law Abuse and Neglect Standards for reporting Child abuse and neglect are defined by Federal Persons responsible for the child and State laws. At the State level, child abuse and neglect may be defined in both civil and criminal Exceptions statutes. This publication presents civil definitions that determine the grounds for intervention by Summaries of State laws State child protective agencies.1 At the Federal level, the Child Abuse Prevention and Treatment To find statute information for a Act (CAPTA) has defined child abuse and neglect particular State, as "any recent act or failure to act on the part go to of a parent or caregiver that results in death, https://www.childwelfare. serious physical or emotional harm, sexual abuse, gov/topics/systemwide/ or exploitation, or an act or failure to act that laws-policies/state/. presents an imminent risk of serious harm."2 1 States also may define child abuse and neglect in criminal statutes. These definitions provide the grounds for the arrest and prosecution of the offenders. 2 CAPTA Reauthorization Act of 2010 (P.L. 111-320), 42 U.S.C. § 5101, Note (§ 3). Children’s Bureau/ACYF/ACF/HHS 800.394.3366 | Email: [email protected] | https://www.childwelfare.gov Definitions of Child Abuse and Neglect https://www.childwelfare.gov CAPTA defines sexual abuse as follows: and neglect in statute.5 States recognize the different types of abuse in their definitions, including physical abuse, The employment, use, persuasion, inducement, neglect, sexual abuse, and emotional abuse. -

Brandenburg in a Time of Terror Thomas Healy
Notre Dame Law Review Volume 84 | Issue 2 Article 3 1-1-2009 Brandenburg in a Time of Terror Thomas Healy Follow this and additional works at: http://scholarship.law.nd.edu/ndlr Recommended Citation Thomas Healy, Brandenburg in a Time of Terror, 84 Notre Dame L. Rev. 655 (2009). Available at: http://scholarship.law.nd.edu/ndlr/vol84/iss2/3 This Article is brought to you for free and open access by NDLScholarship. It has been accepted for inclusion in Notre Dame Law Review by an authorized administrator of NDLScholarship. For more information, please contact [email protected]. BRANDENBURG IN A TIME OF TERROR Thomas Healy* Forfour decades, the Supreme Court's decision in Brandenburg v. Ohio has been celebrated as a landmark in First Amendment law. In one short unsigned opinion, the Court distanced itselffrom the embarrassment of the Red Scare and adopted a highly protective test that permits advocacy of unlawful conduct in all but the most dangerous cases. But 9/11 and the threat of terror- ism pose a new challenge to Brandenburg. Although the government has not resorted to the excesses of McCarthyism, it has taken disturbing steps to silence the speech of political dissenters. These efforts raise questions about the ade- quacy of Brandenburg to protect speech during a time of crisis andfear. They also highlight ambiguities in the Brandenburg test that have been largely ignored by courts. For instance, does Brandenburg apply during war as well as peace? Does it apply to private advocacy as well as public advocacy? And is there anything about the current terrorist threat that would make its protections inapplicable? To answer these and other important questions, this Article undertakes a comprehensive reexamination of Brandenburg and the issue of criminal advocacy. -

Anti-Cyber Bullying Statutes: Threat to Student Free Speech
Cleveland State Law Review Volume 59 Issue 1 Article 5 2011 Anti-Cyber Bullying Statutes: Threat to Student Free Speech John O. Hayward Follow this and additional works at: https://engagedscholarship.csuohio.edu/clevstlrev Part of the Education Law Commons, First Amendment Commons, and the Internet Law Commons How does access to this work benefit ou?y Let us know! Recommended Citation John O. Hayward, Anti-Cyber Bullying Statutes: Threat to Student Free Speech, 59 Clev. St. L. Rev. 85 (2011) available at https://engagedscholarship.csuohio.edu/clevstlrev/vol59/iss1/5 This Article is brought to you for free and open access by the Journals at EngagedScholarship@CSU. It has been accepted for inclusion in Cleveland State Law Review by an authorized editor of EngagedScholarship@CSU. For more information, please contact [email protected]. +(,1 2 1/,1( Citation: 59 Clev. St. L. Rev. 85 2011 Content downloaded/printed from HeinOnline (http://heinonline.org) Tue Jun 4 18:38:38 2013 -- Your use of this HeinOnline PDF indicates your acceptance of HeinOnline's Terms and Conditions of the license agreement available at http://heinonline.org/HOL/License -- The search text of this PDF is generated from uncorrected OCR text. Published by EngagedScholarship@CSU, 2011 1 ANTI-CYBER BULLYING STATUTES: THREAT TO STUDENT FREE SPEECH JOiiN 0. HAYWARD The mere fact that the Internet may be accessed at school does not authorize school officials to become censors of the world-wide web.' I. INTRODUCTION ............................... ....... 86 II. BULLYING AND CYBER BULLYING..................... 87 A. TraditionalBullying ................ ........ 87 B. Cyber Bullying............................ 88 C Media Portrayalsof Cyber Bullying ................ -
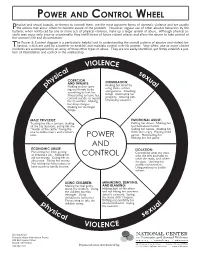
Power and Control Wheel NO SHADING
POOWERWER AANDND COONTROLNTROL WHHEELEEL hysical and sexual assaults, or threats to commit them, are the most apparent forms of domestic violence and are usually Pthe actions that allow others to become aware of the problem. However, regular use of other abusive behaviors by the batterer, when reinforced by one or more acts of physical violence, make up a larger system of abuse. Although physical as- saults may occur only once or occasionally, they instill threat of future violent attacks and allow the abuser to take control of the woman’s life and circumstances. he Power & Control diagram is a particularly helpful tool in understanding the overall pattern of abusive and violent be- Thaviors, which are used by a batterer to establish and maintain control over his partner. Very often, one or more violent incidents are accompanied by an array of these other types of abuse. They are less easily identified, yet firmly establish a pat- tern of intimidation and control in the relationship. VIOLENCE l a se sic x y COERCION u AND THREATS: INTIMIDATION: a h Making her afraid by p Making and/or carry- l ing out threats to do using looks, actions, something to hurt her. and gestures. Smashing Threatening to leave her, things. Destroying her commit suicide, or report property. Abusing pets. her to welfare. Making Displaying weapons. her drop charges. Making her do illegal things. MALE PRIVILEGE: EMOTIONAL ABUSE: Treating her like a servant: making Putting her down. Making her all the big decisions, acting like the feel bad about herself. “master of the castle,” being the Calling her names. -

Retaliatory Hate Crime
Bias Crime Offenders Session C Overview of the Session: At a Glance Presentation: Offender Typology 30 minutes Presentation: Organized Hate Groups 15 minutes Activity: Analysis of Three Video Segments 45 minutes TOTAL TIME 90 minutes Objectives By the end of this session, participants will be able to: • Describe the characteristics of three types of bias crime offenders • Give examples of retaliatory hate crimes and discuss the impor- tance of appropriate responses • Describe the characteristics of organized hate groups • Identify offender typology, given a case example Materials and Equipment Time: 90 minutes Videos: “That Old Gang of Mine” (interview with Eric, former skinhead), 1990 “On Hate Street,” 48 Hours, CBS, 1992 “Licensed to Kill,” Arthur Dong, Deepfocus Productions, 1997 (See page 56 for ordering information.) Handouts: Thrill-Seeking Offenders; Case Studies of Typical Offenders; Reactive Offenders; Mission Offenders; Offender Typology Video Observation Form Transparencies: Important of Understanding Offender Typology; Retaliatory Hate Crimes; Organized Hate Groups Equipment: Overhead projector; screen; VCR; monitor Session C. Bias Crime Offenders Instructor’s Notes I. Presentation: Offender Typology (30 minutes) Explain the following: • Jack Levin and Jack McDevitt of Northeastern University identified three different types of hate crime offenders in their book on bias crime, Hate Crime: The Rising Tide of Bigotry and Bloodshed: thrill-seeking offenders, reactive offenders, and mission offenders. • These are not necessarily -

Sweden National Reporting Procedures for Cyberbullying, Hate Speech and Hate Crime
Reporting in Sweden National reporting procedures for cyberbullying, hate speech and hate crime The information below is extracted from a mapping study of national reporting mechanisms in the countries involved in the No Hate Speech Movement of the Council of Europe. It aims to provide: 1. Contact information of national reporting mechanisms for cyberbullying, hate speech and hate crime where they exist 2. Information about the legal grounds for acting on cyberbullying, hate speech and hate crime where they exist The views expressed in this document do not necessarily reflect the opinions of the Council of Europe1. 1. REPORTING MECHANISMS Reporting hate speech and hate crime Polisen (the police). Website: http://polisen.se Phone:+46 114 14. Reporting cyberbullying If the cyberbullying is connected to the school one should report it to the school management or a teacher. For other cases one can turn to the police. 2. Background information There is no Swedish word that translates hate speech in Swedish. There is a term called “hate against a community”. Another is “discrimination”. Hate speech online can also be called bullying or harassment. Sweden does not have a distinction between hate speech and hate crime that we know of. The Discrimination Act includes discrimination on the basis of sex, transgender identity or expression, ethnicity, disability, sexual orientation and age. People can report everything that is against the law at the police station or by phone. Reports will be investigated by the police. In 2014 there were almost 6270 reports of hate crime in Sweden. That was an increase with 14 % compared to 2015. -

Supreme Court of the United States ______
Team Q No. 16-9999 IN THE Supreme Court of the United States _________ SCHOOL DISTRICT OF WASHINGTON COUNTY, NEW COLUMBIA Petitioner, v. KIMBERLY CLARK, a minor, by and through her father ALAN CLARK Respondent. _________ On Writ of Certiorari to the United States Court of Appeals for the Fourteenth Circuit _________ BRIEF OF PETITIONER _________ SVEN LINDBLOM BAKER & REILLY, LLP For Petitioner QUESTIONS PRESENTED 1. Whether a public high school student’sFacebook post constituted a “true threat” beyond the protection of the First Amendment? 2. Whether a public school district violated a high school student’sFirst Amendment rights by disciplining her for a Facebook post initiated off campus on her personal computer where school authorities conclude that the post was materially disruptive and collided with the rights of other students to be secure at school? i BRIEF CERTIFICATE Team Letter Q certifies the following: 1. The work product contained in all copies of this team’sbrief is in fact the work product of the team members, 2. This team has complied fully with the school’sgoverning honor code, and 3. This team has complied with all Rules of the Competition. ii TABLE OF CONTENTS QUESTIONS PRESENTED............................................................................................................ i BRIEF CERTIFICATE................................................................................................................... ii TABLE OF CONTENTS.............................................................................................................. -

Cyber Bulling
Cyberbullying What Can I Do? Mark S. Borer, MD, DFAPA, DFAACAP 5/16 Subset of: Bullying and Social Aggression in DE Medical Society of Delaware 5/16 © All rights reserved Credits for Archived Slide Set • Dr. Borer has presented on bullying at various schools and staff developments over his years in practice and he has created different portions of this slide set over time. The slide set is updated from time to time from online, organizational, and educational resources, as well as from ongoing clinical experience. • Formatting for the slides was provided in part by Medical Society of Delaware. • Some of the slides present materials available through various referenced websites. Dr. Borer also prepared an educational program on bullying and social aggression for Lorman Seminars in ’06, which informs some of his thoughts and topics in this slide set, and which he references herein. • The presentations by Dr. Borer at the Medical Society of Delaware, as well as this slide set, have been shared for the benefit of Delaware’s youth. Dr. Borer has received no remuneration for use of this slide set. The materials in these slides may inform the presentations of others, but the slide set itself is copyrighted and used with permission by the Medical Society of DE and by the Delaware Bullying Prevention Association. Cyberbullying—A Definition • CYBER OR ELECTRONIC Bullying – using the Internet, email, text messaging, or other social media to threaten, harass, hurt, single out, embarrass, spread rumors, and/or reveal secrets about others. • Engaging others in targeting a particular individual enhances the bullying and the potential hurt and damage to the individual.