Tip Sheet for Coping with Any Sort of Bully
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Influence of Behavioural Psychology on Consumer Psychology and Marketing
This is a repository copy of The influence of behavioural psychology on consumer psychology and marketing. White Rose Research Online URL for this paper: http://eprints.whiterose.ac.uk/94148/ Version: Accepted Version Article: Wells, V.K. (2014) The influence of behavioural psychology on consumer psychology and marketing. Journal of Marketing Management, 30 (11-12). pp. 1119-1158. ISSN 0267-257X https://doi.org/10.1080/0267257X.2014.929161 Reuse Unless indicated otherwise, fulltext items are protected by copyright with all rights reserved. The copyright exception in section 29 of the Copyright, Designs and Patents Act 1988 allows the making of a single copy solely for the purpose of non-commercial research or private study within the limits of fair dealing. The publisher or other rights-holder may allow further reproduction and re-use of this version - refer to the White Rose Research Online record for this item. Where records identify the publisher as the copyright holder, users can verify any specific terms of use on the publisher’s website. Takedown If you consider content in White Rose Research Online to be in breach of UK law, please notify us by emailing [email protected] including the URL of the record and the reason for the withdrawal request. [email protected] https://eprints.whiterose.ac.uk/ Behavioural psychology, marketing and consumer behaviour: A literature review and future research agenda Victoria K. Wells Durham University Business School, Durham University, UK Contact Details: Dr Victoria Wells, Senior Lecturer in Marketing, Durham University Business School, Wolfson Building, Queens Campus, University Boulevard, Thornaby, Stockton on Tees, TS17 6BH t: +44 (0) 191 3345099, e: [email protected] Biography: Victoria Wells is Senior Lecturer in Marketing at Durham University Business School and Mid-Career Fellow at the Durham Energy Institute (DEI). -

Competing Theories of Blackmail: an Empirical Research Critique of Criminal Law Theory
Competing Theories of Blackmail: An Empirical Research Critique of Criminal Law Theory Paul H. Robinson,* Michael T. Cahill** & Daniel M. Bartels*** The crime of blackmail has risen to national media attention because of the David Letterman case, but this wonderfully curious offense has long been the favorite of clever criminal law theorists. It criminalizes the threat to do something that would not be criminal if one did it. There exists a rich liter- ature on the issue, with many prominent legal scholars offering their accounts. Each theorist has his own explanation as to why the blackmail offense exists. Most theories seek to justify the position that blackmail is a moral wrong and claim to offer an account that reflects widely shared moral intuitions. But the theories make widely varying assertions about what those shared intuitions are, while also lacking any evidence to support the assertions. This Article summarizes the results of an empirical study designed to test the competing theories of blackmail to see which best accords with pre- vailing sentiment. Using a variety of scenarios designed to isolate and test the various criteria different theorists have put forth as “the” key to blackmail, this study reveals which (if any) of the various theories of blackmail proposed to date truly reflects laypeople’s moral judgment. Blackmail is not only a common subject of scholarly theorizing but also a common object of criminal prohibition. Every American jurisdiction criminalizes blackmail, although there is considerable variation in its formulation. The Article reviews the American statutes and describes the three general approaches these provisions reflect. -

Model of How Perspective Is Formed in the Mind
Model of how perspective is formed in the mind • Version 1.1 • Last update: 5/6/2007 Simple model of information processing, perception generation, and behavior Feedback can distort data from input Information channels Data Emotional Filter Cognitive Filter Input Constructed External Impact Analysis Channels Perspective information “How do I feel about it?” “What do I think about it? ” “How will it affect Sight Perceived Reality i.e. news, ETL Process ETL Process me?” Hearing environment, Take what feels good, Take what seems good, Touch Word View etc. reject the rest or flag reject the rest or flag Smell as undesirable. as undesirable. Taste Modeling of Results Action possible behaviors Motivation Impact on Behavior “What might I do?” Anticipation of Gain world around Or you “I do something” Options are constrained Fear of loss by emotional and cognitive filters i.e bounded by belief system Behavior Perspective feedback feedback World View Conditioning feedback Knowledge Emotional Response Information Information Experience Experience Filtered by perspective and emotional response conditioning which creates “perception” Data Data Data Data Data Data Data Data Data Newspapers Television Movies Radio Computers Inter-person conversations Educational and interactions Magazines Books Data sources system Internet Data comes from personal experience, and “information” sources. Note that media is designed to feed preconceived “information” directly into the consciousness of the populace. This bypasses most of the processing, gathering, manipulating and organizing of data and hijacks the knowledge of the receiver. In other words, the data is taken out of context or in a pre selected context. If the individual is not aware of this model and does not understand the process of gathering, manipulating and organizing data in a way that adds to the knowledge of the receiver, then the “information” upon which their “knowledge” is based can enter their consciousness without the individual being aware of it or what impact it has on their ability to think. -

Definitions of Child Abuse and Neglect
STATE STATUTES Current Through March 2019 WHAT’S INSIDE Defining child abuse or Definitions of Child neglect in State law Abuse and Neglect Standards for reporting Child abuse and neglect are defined by Federal Persons responsible for the child and State laws. At the State level, child abuse and neglect may be defined in both civil and criminal Exceptions statutes. This publication presents civil definitions that determine the grounds for intervention by Summaries of State laws State child protective agencies.1 At the Federal level, the Child Abuse Prevention and Treatment To find statute information for a Act (CAPTA) has defined child abuse and neglect particular State, as "any recent act or failure to act on the part go to of a parent or caregiver that results in death, https://www.childwelfare. serious physical or emotional harm, sexual abuse, gov/topics/systemwide/ or exploitation, or an act or failure to act that laws-policies/state/. presents an imminent risk of serious harm."2 1 States also may define child abuse and neglect in criminal statutes. These definitions provide the grounds for the arrest and prosecution of the offenders. 2 CAPTA Reauthorization Act of 2010 (P.L. 111-320), 42 U.S.C. § 5101, Note (§ 3). Children’s Bureau/ACYF/ACF/HHS 800.394.3366 | Email: [email protected] | https://www.childwelfare.gov Definitions of Child Abuse and Neglect https://www.childwelfare.gov CAPTA defines sexual abuse as follows: and neglect in statute.5 States recognize the different types of abuse in their definitions, including physical abuse, The employment, use, persuasion, inducement, neglect, sexual abuse, and emotional abuse. -

On Choice and the Law of Effect
2014, 27(4), 569-584 Stanley J. Weiss, Editor Special Issue Peer-reviewed On Choice and the Law of Effect J. E. R. Staddon Duke University, USA Cumulative records, which show individual responses in real time, are a natural but neglected starting point for understanding the dynamics of operant behavior. To understand the processes that underlie molar laws like matching, it is also helpful to look at choice behavior in situations such as concurrent random ratio that lack the stabilizing feedback intrinsic to concurrent variable-interval schedules. The paper identifies some basic, non-temporal properties of operant learning: Post-reinforcement pulses at the beginning of FI learning, regression, faster reversal learning after shorter periods, and choice distribution on identical random ratios at different absolute ratio values. These properties suggest that any operant-learning model must include silent responses, competing to become the active response, and response strengths that reflect more than immediate past history of reinforcement. The cumulative-effects model is one that satisfies these conditions. Two months before his engagement to his cousin Emma Wedgwood, Charles Darwin wrote copious notes listing the pros and cons of marriage. This is typical human choice behavior, though perhaps more conscious and systematic than most. No one would imagine that animals choose like this. But folk psychology often slips in unannounced. In his famous matching-law experiment, to make his procedure work Richard Herrnstein added what is called a changeover delay (COD): neither response could be rewarded for a second or two after each change from one response to the other. The reason was to prevent a third response: switching. -

Brandenburg in a Time of Terror Thomas Healy
Notre Dame Law Review Volume 84 | Issue 2 Article 3 1-1-2009 Brandenburg in a Time of Terror Thomas Healy Follow this and additional works at: http://scholarship.law.nd.edu/ndlr Recommended Citation Thomas Healy, Brandenburg in a Time of Terror, 84 Notre Dame L. Rev. 655 (2009). Available at: http://scholarship.law.nd.edu/ndlr/vol84/iss2/3 This Article is brought to you for free and open access by NDLScholarship. It has been accepted for inclusion in Notre Dame Law Review by an authorized administrator of NDLScholarship. For more information, please contact [email protected]. BRANDENBURG IN A TIME OF TERROR Thomas Healy* Forfour decades, the Supreme Court's decision in Brandenburg v. Ohio has been celebrated as a landmark in First Amendment law. In one short unsigned opinion, the Court distanced itselffrom the embarrassment of the Red Scare and adopted a highly protective test that permits advocacy of unlawful conduct in all but the most dangerous cases. But 9/11 and the threat of terror- ism pose a new challenge to Brandenburg. Although the government has not resorted to the excesses of McCarthyism, it has taken disturbing steps to silence the speech of political dissenters. These efforts raise questions about the ade- quacy of Brandenburg to protect speech during a time of crisis andfear. They also highlight ambiguities in the Brandenburg test that have been largely ignored by courts. For instance, does Brandenburg apply during war as well as peace? Does it apply to private advocacy as well as public advocacy? And is there anything about the current terrorist threat that would make its protections inapplicable? To answer these and other important questions, this Article undertakes a comprehensive reexamination of Brandenburg and the issue of criminal advocacy. -

PSYCO 282: Operant Conditioning Worksheet
PSYCO 282 Behaviour Modification Operant Conditioning Worksheet Operant Conditioning Examples For each example below, decide whether the situation describes positive reinforcement (PR), negative reinforcement (NR), positive punishment (PP), or negative punishment (NP). Note: the examples are randomly ordered, and there are not equal numbers of each form of operant conditioning. Question Set #1 ___ 1. Johnny puts his quarter in the vending machine and gets a piece of candy. ___ 2. I put on sunscreen to avoid a sunburn. ___ 3. You stick your hand in a flame and you get a painful burn. ___ 4. Bobby fights with his sister and does not get to watch TV that night. ___ 5. A child misbehaves and gets a spanking. ___ 6. You come to work late regularly and you get demoted. ___ 7. You take an aspirin to eliminate a headache. ___ 8. You walk the dog to avoid having dog poop in the house. ___ 9. Nathan tells a good joke and his friends all laugh. ___ 10. You climb on a railing of a balcony and fall. ___ 11. Julie stays out past her curfew and now does not get to use the car for a week. ___ 12. Robert goes to work every day and gets a paycheck. ___ 13. Sue wears a bike helmet to avoid a head injury. ___ 14. Tim thinks he is sneaky and tries to text in class. He is caught and given a long, boring book to read. ___ 15. Emma smokes in school and gets hall privileges taken away. ___ 16. -

Attitude and Behavior Change
MCAT-3200020 C06 November 19, 2015 11:6 CHAPTER 6 Attitude and Behavior Change Read This Chapter to Learn About ➤ Associative Learning ➤ Observational Learning ➤ Theories of Attitudes and Behavior Change ASSOCIATIVE LEARNING Associative learning is a specific type of learning. In this type of learning the individual learns to “associate” or pair a specific stimulus with a specific response based on the environment around him or her. This association is not necessarily a conscious process and can include involuntary learned responses (e.g., children in a classroom becoming restless at 2:55 p.m. on a Friday before the 3 p.m. bell). This category of learning includes classical conditioning and operant conditioning. Classical Conditioning Classical conditioning is one of the first associative learning methods that behavioral researchers understood. Classical conditioning has now been shown to occur across both psychological and physiological processes. Classical conditioning is a form of learning in which a response originally caused by one stimulus is also evoked by a second, unassociated stimulus. The Russian physiologist Ivan Pavlov and his dogs are most famously associated with this type of conditioning. Pavlov noticed that as the dogs’ dinnertime approached (unconditioned stimulus,orUCS), they began to 91 MCAT-3200020 C06 November 19, 2015 11:6 92 UNIT II: salivate (unconditioned response,orUCR). He found this unusual because the dogs Behavior had not eaten anything, so there was no physiological reason for the increased saliva- tion before the dinner was actually served. Pavlov then experimented with ringing a bell (neutral stimulus) before feeding his dogs. As a result, the dogs began to associate the (previously neutral) bell sound with food and would salivate upon hearing the bell. -

Anti-Cyber Bullying Statutes: Threat to Student Free Speech
Cleveland State Law Review Volume 59 Issue 1 Article 5 2011 Anti-Cyber Bullying Statutes: Threat to Student Free Speech John O. Hayward Follow this and additional works at: https://engagedscholarship.csuohio.edu/clevstlrev Part of the Education Law Commons, First Amendment Commons, and the Internet Law Commons How does access to this work benefit ou?y Let us know! Recommended Citation John O. Hayward, Anti-Cyber Bullying Statutes: Threat to Student Free Speech, 59 Clev. St. L. Rev. 85 (2011) available at https://engagedscholarship.csuohio.edu/clevstlrev/vol59/iss1/5 This Article is brought to you for free and open access by the Journals at EngagedScholarship@CSU. It has been accepted for inclusion in Cleveland State Law Review by an authorized editor of EngagedScholarship@CSU. For more information, please contact [email protected]. +(,1 2 1/,1( Citation: 59 Clev. St. L. Rev. 85 2011 Content downloaded/printed from HeinOnline (http://heinonline.org) Tue Jun 4 18:38:38 2013 -- Your use of this HeinOnline PDF indicates your acceptance of HeinOnline's Terms and Conditions of the license agreement available at http://heinonline.org/HOL/License -- The search text of this PDF is generated from uncorrected OCR text. Published by EngagedScholarship@CSU, 2011 1 ANTI-CYBER BULLYING STATUTES: THREAT TO STUDENT FREE SPEECH JOiiN 0. HAYWARD The mere fact that the Internet may be accessed at school does not authorize school officials to become censors of the world-wide web.' I. INTRODUCTION ............................... ....... 86 II. BULLYING AND CYBER BULLYING..................... 87 A. TraditionalBullying ................ ........ 87 B. Cyber Bullying............................ 88 C Media Portrayalsof Cyber Bullying ................ -

Operant Conditioning
Psyc 390 – Psychology of Learning Operant Conditioning In CC, the focus is on the two stimuli. In Instrumental Conditioning, the focus is on Operant Conditioning the S and how it affects the response. In Operant co nditio ning, what fo llo ws the response is the most important. Psychology 390 That is, the consequent stimulus. Psychology of Learning R – S Steven E. Meier, Ph.D. Thus, you have a Stimulus that causes a Respo nse, which is in turn fo llo wed, by a Listen to the audio lecture while viewing these slides consequent stimulus. 1 2 Psyc 390 – Psychology of Learning Psyc 390 – Psychology of Learning Differences Between Instrumental and Skinner Operant Conditioning Radical Behaviorism • Instrumental • Probably the most important applied • The environment constrains the opportunity psychologist. for reward. • Principles have been used in everything • A specific behavio r is required fo r the reward. • Medicine •Education •Operant • A specific response is required for •Therapy reinforcement. •Business • The frequency of responding determines the amount of reinforcement given. 3 4 Psyc 390 – Psychology of Learning Psyc 390 – Psychology of Learning Distinguished Between Two Types of Responses. Respondents • Respondents • Are elicited by a UCS •Operants • Are innate • Are regulated by the autonomic NS HR, BP, etc. • Are involuntary • Are classically conditioned. 5 6 1 Psyc 390 – Psychology of Learning Psyc 390 – Psychology of Learning Systematically Demonstrated Operants Several Things • Are emitted If something occurs after the response • Are skeletal (consequent stimulus) and the behavior • Are voluntary increases, • Get lots of feedback The procedure is called reinforcement, and the thing that caused the increase is called a reinforcer. -
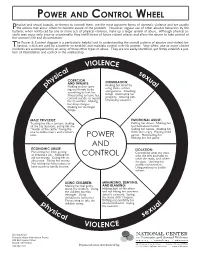
Power and Control Wheel NO SHADING
POOWERWER AANDND COONTROLNTROL WHHEELEEL hysical and sexual assaults, or threats to commit them, are the most apparent forms of domestic violence and are usually Pthe actions that allow others to become aware of the problem. However, regular use of other abusive behaviors by the batterer, when reinforced by one or more acts of physical violence, make up a larger system of abuse. Although physical as- saults may occur only once or occasionally, they instill threat of future violent attacks and allow the abuser to take control of the woman’s life and circumstances. he Power & Control diagram is a particularly helpful tool in understanding the overall pattern of abusive and violent be- Thaviors, which are used by a batterer to establish and maintain control over his partner. Very often, one or more violent incidents are accompanied by an array of these other types of abuse. They are less easily identified, yet firmly establish a pat- tern of intimidation and control in the relationship. VIOLENCE l a se sic x y COERCION u AND THREATS: INTIMIDATION: a h Making her afraid by p Making and/or carry- l ing out threats to do using looks, actions, something to hurt her. and gestures. Smashing Threatening to leave her, things. Destroying her commit suicide, or report property. Abusing pets. her to welfare. Making Displaying weapons. her drop charges. Making her do illegal things. MALE PRIVILEGE: EMOTIONAL ABUSE: Treating her like a servant: making Putting her down. Making her all the big decisions, acting like the feel bad about herself. “master of the castle,” being the Calling her names. -

Retaliatory Hate Crime
Bias Crime Offenders Session C Overview of the Session: At a Glance Presentation: Offender Typology 30 minutes Presentation: Organized Hate Groups 15 minutes Activity: Analysis of Three Video Segments 45 minutes TOTAL TIME 90 minutes Objectives By the end of this session, participants will be able to: • Describe the characteristics of three types of bias crime offenders • Give examples of retaliatory hate crimes and discuss the impor- tance of appropriate responses • Describe the characteristics of organized hate groups • Identify offender typology, given a case example Materials and Equipment Time: 90 minutes Videos: “That Old Gang of Mine” (interview with Eric, former skinhead), 1990 “On Hate Street,” 48 Hours, CBS, 1992 “Licensed to Kill,” Arthur Dong, Deepfocus Productions, 1997 (See page 56 for ordering information.) Handouts: Thrill-Seeking Offenders; Case Studies of Typical Offenders; Reactive Offenders; Mission Offenders; Offender Typology Video Observation Form Transparencies: Important of Understanding Offender Typology; Retaliatory Hate Crimes; Organized Hate Groups Equipment: Overhead projector; screen; VCR; monitor Session C. Bias Crime Offenders Instructor’s Notes I. Presentation: Offender Typology (30 minutes) Explain the following: • Jack Levin and Jack McDevitt of Northeastern University identified three different types of hate crime offenders in their book on bias crime, Hate Crime: The Rising Tide of Bigotry and Bloodshed: thrill-seeking offenders, reactive offenders, and mission offenders. • These are not necessarily