Forensics Analysis of Privacy of Portable Web Browsers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
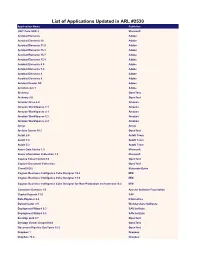
List of Applications Updated in ARL #2530
List of Applications Updated in ARL #2530 Application Name Publisher .NET Core SDK 2 Microsoft Acrobat Elements Adobe Acrobat Elements 10 Adobe Acrobat Elements 11.0 Adobe Acrobat Elements 15.1 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 15.9 Adobe Acrobat Elements 6.0 Adobe Acrobat Elements 7.0 Adobe Application Name Acrobat Elements 8 Adobe Acrobat Elements 9 Adobe Acrobat Reader DC Adobe Acrobat.com 1 Adobe Alchemy OpenText Alchemy 9.0 OpenText Amazon Drive 4.0 Amazon Amazon WorkSpaces 1.1 Amazon Amazon WorkSpaces 2.1 Amazon Amazon WorkSpaces 2.2 Amazon Amazon WorkSpaces 2.3 Amazon Ansys Ansys Archive Server 10.1 OpenText AutoIt 2.6 AutoIt Team AutoIt 3.0 AutoIt Team AutoIt 3.2 AutoIt Team Azure Data Studio 1.9 Microsoft Azure Information Protection 1.0 Microsoft Captiva Cloud Toolkit 3.0 OpenText Capture Document Extraction OpenText CloneDVD 2 Elaborate Bytes Cognos Business Intelligence Cube Designer 10.2 IBM Cognos Business Intelligence Cube Designer 11.0 IBM Cognos Business Intelligence Cube Designer for Non-Production environment 10.2 IBM Commons Daemon 1.0 Apache Software Foundation Crystal Reports 11.0 SAP Data Explorer 8.6 Informatica DemoCreator 3.5 Wondershare Software Deployment Wizard 9.3 SAS Institute Deployment Wizard 9.4 SAS Institute Desktop Link 9.7 OpenText Desktop Viewer Unspecified OpenText Document Pipeline DocTools 10.5 OpenText Dropbox 1 Dropbox Dropbox 73.4 Dropbox Dropbox 74.4 Dropbox Dropbox 75.4 Dropbox Dropbox 76.4 Dropbox Dropbox 77.4 Dropbox Dropbox 78.4 Dropbox Dropbox 79.4 Dropbox Dropbox 81.4 -

Forensics Evaluation of Privacy of Portable Web Browsers
International Journal of Computer Applications (0975 – 8887) Volume 147 – No. 8, August 2016 Forensics Evaluation of Privacy of Portable Web Browsers Ahmad Ghafarian Seyed Amin Hosseini Seno Department of Computer Science Department of Computer Engineering and Information Systems Faculty of Engineering University of North Georgia Ferdowsi University of Mashhad Dahlonega, GA 30005, USA Mashhad, Iran ABSTRACT relation to a computer forensic investigation is that the latter is Browsers claim private mode browsing saves no data on the a less tangible source of evidence [3]. host machine. Most popular web browsers also offer portable A study of tools and techniques for memory forensics can be versions of their browsers which can be launched from a found in [4]. The author has evaluated several command line removable device. When the removable device is removed, it and graphical user interface tools and provide the steps is claimed that traces of browsing activities will be deleted needed for memory forensics. Retrieving portable browsing and consequently private portable browsers offer better forensics artifacts left behind from main memory have privacy. This makes the task of computer forensics recently attracted some attention [5, 6]. The authors used investigators who try to reconstruct the past browsing history, limited memory forensics to retrieve forensics artifacts left in case of any computer incidence, more challenging. after a private portable browsing session. They argue that However, whether or not all data is deleted beyond forensic memory forensics is very promising in establishing a link recovery is a moot point. This research examines privacy of between the suspect and the retrieved data. -

(Hardening) De Navegadores Web Más Utilizados
UNIVERSIDAD DON BOSCO VICERRECTORÍA DE ESTUDIOS DE POSTGRADO TRABAJO DE GRADUACIÓN Endurecimiento (Hardening) de navegadores web más utilizados. Caso práctico: Implementación de navegadores endurecidos (Microsoft Internet Explorer, Mozilla Firefox y Google Chrome) en un paquete integrado para Microsoft Windows. PARA OPTAR AL GRADO DE: MAESTRO EN SEGURIDAD Y GESTION DEL RIESGO INFORMATICO ASESOR: Mg. JOSÉ MAURICIO FLORES AVILÉS PRESENTADO POR: ERICK ALFREDO FLORES AGUILAR Antiguo Cuscatlán, La Libertad, El Salvador, Centroamérica Febrero de 2015 AGRADECIMIENTOS A Dios Todopoderoso, por regalarme vida, salud y determinación para alcanzar un objetivo más en mi vida. A mi amada esposa, que me acompaño durante toda mi carrera, apoyó y comprendió mi dedicación de tiempo y esfuerzo a este proyecto y nunca dudó que lo concluiría con bien. A mis padres y hermana, que siempre han sido mis pilares y me enseñaron que lo mejor que te pueden regalar en la vida es una buena educación. A mis compañeros de trabajo, que mediante su esfuerzo extraordinario me han permitido contar con el tiempo necesario para dedicar mucho más tiempo a la consecución de esta meta. A mis amigos de los que siempre he tenido una palabra de aliento cuando la he necesitado. A mi supervisor y compañeros de la Escuela de Computación de la Universidad de Queens por facilitarme espacio, recursos, tiempo e información valiosa para la elaboración de este trabajo. A mi asesor de tesis, al director del programa de maestría y mis compañeros de la carrera, que durante estos dos años me han ayudado a lograr esta meta tan importante. Erick Alfredo Flores Aguilar INDICE I. -
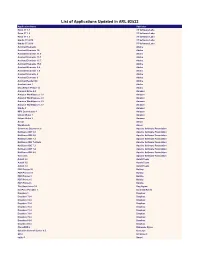
List of Applications Updated in ARL #2532
List of Applications Updated in ARL #2532 Application Name Publisher Robo 3T 1.1 3T Software Labs Robo 3T 1.2 3T Software Labs Robo 3T 1.3 3T Software Labs Studio 3T 2018 3T Software Labs Studio 3T 2019 3T Software Labs Acrobat Elements Adobe Acrobat Elements 10 Adobe Acrobat Elements 11.0 Adobe Acrobat Elements 15.1 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 15.9 Adobe Acrobat Elements 6.0 Adobe Acrobat Elements 7.0 Adobe Acrobat Elements 8 Adobe Acrobat Elements 9 Adobe Acrobat Reader DC Adobe Acrobat.com 1 Adobe Shockwave Player 12 Adobe Amazon Drive 4.0 Amazon Amazon WorkSpaces 1.1 Amazon Amazon WorkSpaces 2.1 Amazon Amazon WorkSpaces 2.2 Amazon Amazon WorkSpaces 2.3 Amazon Kindle 1 Amazon MP3 Downloader 1 Amazon Unbox Video 1 Amazon Unbox Video 2 Amazon Ansys Ansys Workbench Ansys Commons Daemon 1.0 Apache Software Foundation NetBeans IDE 5.0 Apache Software Foundation NetBeans IDE 5.5 Apache Software Foundation NetBeans IDE 7.2 Apache Software Foundation NetBeans IDE 7.2 Beta Apache Software Foundation NetBeans IDE 7.3 Apache Software Foundation NetBeans IDE 7.4 Apache Software Foundation NetBeans IDE 8.0 Apache Software Foundation Tomcat 5 Apache Software Foundation AutoIt 2.6 AutoIt Team AutoIt 3.0 AutoIt Team AutoIt 3.2 AutoIt Team PDF Printer 10 Bullzip PDF Printer 11 Bullzip PDF Printer 3 Bullzip PDF Printer 5 Bullzip PDF Printer 6 Bullzip The Unarchiver 3.1 Dag Agren KeePass Portable 1 Dominik Reichl Dropbox 1 Dropbox Dropbox 73.4 Dropbox Dropbox 74.4 Dropbox Dropbox 75.4 Dropbox Dropbox 76.4 Dropbox Dropbox 77.4 Dropbox -

Piratebrowser Artifacts
PirateBrowser Artifacts Written by Chris Antonovich Researched by Olivia Hatalsky 175 Lakeside Ave, Room 300A Phone: 802/865-5744 Fax: 802/865-6446 http://www.lcdi.champlin.edu Published Date Patrick Leahy Center for Digital Investigation (LCDI) Disclaimer: This document contains information based on research that has been gathered by employee(s) of The Senator Patrick Leahy Center for Digital Investigation (LCDI). The data contained in this project is submitted voluntarily and is unaudited. Every effort has been made by LCDI to assure the accuracy and reliability of the data contained in this report. However, LCDI nor any of our employees make no representation, warranty or guarantee in connection with this report and hereby expressly disclaims any liability or responsibility for loss or damage resulting from use of this data. Information in this report can be downloaded and redistributed by any person or persons. Any redistribution must maintain the LCDI logo and any references from this report must be properly annotated. Contents Introduction ............................................................................................................................................................................. 2 Background: ........................................................................................................................................................................ 2 Purpose and Scope: ............................................................................................................................................................ -

Ministry of Education EFIS 2.0 - User Set up Guide
Ministry of Education EFIS 2.0 - User Set Up Guide Version 1.9 August 22, 2016 User Setup Guide 1 Table of Contents 1 Table of Contents .............................................................................................................................................. 2 2 Document History ............................................................................................................................................. 3 3 Description and System Requirements ................................................................................................... 4 3.1 Description ............................................................................................................................................... 4 3.2 User System Requirements ............................................................................................................... 5 4 Firefox setup ....................................................................................................................................................... 6 4.1 Recommended Version ....................................................................................................................... 6 4.2 Download File ......................................................................................................................................... 6 4.3 Download from Workspace .............................................................................................................. 6 4.4 Install Firefox ......................................................................................................................................... -

NAVEGAR CON FIREFOX José Lozano Abogado
NAVEGAR CON FIREFOX José Lozano Abogado No, no se trata de un nuevo modelo de embarcación de recreo, ni del último cohete espacial, ni siquiera de un modelo de GPS, sino de un programa para navegar por internet, un navegador. odos sabemos para qué sirve un programa de este tipo y supongo que la mayoría usarán para este fin el programa Internet Explorer, de Microsoft, y sólo unos pocos tendrán experiencia con Firefox. Como considero que éste posee unas características muy interesan- tes que nos pueden ser muy útiles en nuestro trabajo y en nuestro ocio, voy a intentar transmitirles las bondades de este navegador de internet, con la intención, si no de sustituir totalmente al IE de Microsoft, sí al menos de compartir con éste la exploración del universo virtual en que se ha converti- do internet. Mozilla Firefox es un navegador web multiplataforma, que funciona en distintos sistema operativos, Windows, Linux, MacOS, etc... Es un producto gratuito y de código abierto, “open source”. Firefox incorpora numerosas caracte- rísticas avanzadas, siendo las más destacadas el bloqueo de ventanas emergentes, el uso de marcadores dinámicos, so- porte para estándares abiertos, navegación por pestañas, y un mecanismo para añadir funcionalidades mediante extensio- nes. Estas dos últimas son las más atractivas y útiles caracte- rísticas, por lo que voy a detenerme en ellas. Navegación por pestañas.- Consiste en poder abrir en De igual modo, se puede definir un grupo de pestañas una sola ventana del programa varias páginas a la vez, pu- como páginas de inicio, de forma que cada vez que ejecuta- diendo ir de una a otra a través de pestañas. -

XUL – Desenvolvendo Aplicações Com Mozilla / Firefox
XUL ± Desenvolvendo Aplicações com Mozilla / Firefox Marcio Junior Vieira [email protected] Marcio Junior Vieira www.ambientelivre.com.br Palestrante - Marcio Junior Vieira ● A 7 Anos trabalha da área de Desenvolvimento e Análise de sistemas. ● Trabalha com Software Livre desde 2000. ● Formado em tecnologia em Informática e Pós-Graduado em Informática (Software Livre) pela UFPR. ● Consultor de Soluções em Software Livre pela Ambiente Livre. ● Consultor em Sistemas de Gestão Empresarial GCI Informática. Marcio● JunioPar Vrieticira ip a n te d o g r u p o X U L Br a sil. www.ambientelivre.com.br Construir aplicações web e desktop. Introdução ● O que é XUL? ● Pacotes ( chrome ). ● Histórico. ● RDF ● Firefox. ● XULRunner. ● Arquivo XUL. ● Elementos XUL. ● Suporte XUL. ● XBL. ● XPCOM. ● Ferramentas XUL. ● Exemplos de aplicações. ● Livros. ● Curiosidades ● Links Marcio Junior Vieira www.ambientelivre.com.br O que é XUL ? ● XUL é a sigla para XML User Interface Language. ● Inicialmente foi criado para tornar o desenvolvimento do navegador Mozilla mais fácil, rápido e portável. ● É uma linguagem de tags baseada na tecnologia XML, e como o XML tem as vantagens de outras linguagens de marcação como XHTML, MathML, SVG,etc. ● É uma linguagem multi-plataforma para desenvolver interfaces gráficas de usuários (GUI ± Graphical User Interface). ● Atualmente apenas os browsers da família Mozilla, Netscape e outros baseados neles, tem suporte a tecnologia XUL. ● O nome XUL é uma referência ao filme Caça-Fantasmas. Marcio Junior Vieira www.ambientelivre.com.br Mozilla Firefox ● WEB Browser. ● + de 100 milhões de downloads. Marcio Junior Vieira www.ambientelivre.com.br Histórico. ● 1997 - ªGuerra dos browsersº a Netscape, líder de mercado até o que a Microsoft começou a liberar gratuitamente juntamente seu SO o seu produto o IE. -

MANUAL RÁPIDO TOKEN USO DE TOKEN FÍSICO Marca: Bit4id Modelo
MANUAL RÁPIDO TOKEN USO DE TOKEN FÍSICO Marca: Bit4Id Modelo: key4 V2 – 15/02/2018 Dirección Nacional de Tecnologías de la Información y Comunicaciones Página 1 de 12 Tabla de contenido 1 Inicio ...................................................................................................................................................................3 2 Sistemas operativos ............................................................................................................................................3 3 Firmar .................................................................................................................................................................4 4 Validar. ................................................................................................................................................................5 5 Herramientas ......................................................................................................................................................6 5.1 Opciones .....................................................................................................................................................6 5.2 Token manager ...........................................................................................................................................7 5.3 Modo compatibilidad .................................................................................................................................7 5.4 Firefox Portable ..........................................................................................................................................8 -

Lleva La Solución Contigo
DERM@red Lleva la solución contigo Autor: Luis Arantón Areosa Enfermero. Servizo Galego de Saúde. Máster en Deterioro de la Integridad Cutánea, Úlceras y Heridas [email protected] Estimad@s compañer@s Siguiendo la línea habitual, en esta ocasión dare- mos cuenta de algunas aplicaciones prácticamente imprescindibles que tendremos la ocasión de poder “llevarnos” con nosotros a cualquier parte en una memoria externa USB, o en cualquier disco duro portátil; se trata de las llamadas “versiones PORTA- BLES” de la mayoría de los programas que usamos habitualmente. De esta forma podremos trabajar con nuestras aplicaciones favoritas en cualquier or- denador que no sea el habitual, sin necesidad de Imagen 1.- Firefox Portable. que éste las tenga instaladas, porque ya lo están en el propio “pendrive”. Incluye navegación por pestañas, administrador de descargas, corrector ortográfico, búsqueda progre- Disponemos de versiones “portables” de la mayoría siva, marcadores dinámicos e integración del motor de los principales programas y aplicaciones ofimáti- de búsqueda en otras aplicaciones y programas. cas; se trata de aplicaciones útiles, fáciles de utilizar y absolutamente seguras que podemos descargar- Una de las características más interesantes que po- nos de manera muy sencilla desde la Web (solo ne- see es la posibilidad de realizar navegación privada, cesitamos una conexión Web) y que podrían susti- o sea, que permite navegar en cualquier ordenador tuir a todos los programas y aplicativos ofimáticos sin dejar ningún tipo de rastro de la navegación rea- que utilizamos habitualmente, pero sin coste añadi- do alguno, ya que son GRATUITOS. Vamos a reco- mendar y comentar algunos de ellos: Firefox Portable (Imagen 1) (http://portableapps.com/apps/internet/firefox_portable) Se trata de una versión portátil (“portable”) del nave- gador Mozilla Firefox; navegador web libre y de có- digo abierto desarrollado por la Fundación Mozilla y que en sus diferentes versiones pasa por ser el se- gundo navegador más utilizado de Internet, con más de 450 millones de usuarios. -

Firefox Download 64 Bit
Firefox download 64 bit Want to switch to the bit version of Firefox? Here's how Go to this Mozilla Firefox download page and click on the Windows bit download link. To download and install the Firefox bit web browser for Windows go to the Firefox All Systems page. For the latest Firefox release, you can. Users on bit Windows who download Firefox will now get our bit version by default. That means they'll install a more secure version of. Better desktop browsing is here. Get Firefox for Windows, Mac, and Linux. Mozilla Firefox is a fast, light and tidy open source web browser. At its public launch in Mozilla Firefox was the first browser to challenge Microsoft Internet. Mozilla Firefox is a fast, full-featured Web browser. Firefox includes pop-up blocking, tab-browsing, integrated Google search, simplified privacy. Firefox bit, free and safe download. Firefox bit latest version: Firefox: Free Web Browser for bit Operating Systems. Those who have updated to a bit. Download Firefox bit for Windows now from Softonic: % safe and virus free. More than downloads this month. Download Firefox bit latest version. Download Latest version of Mozilla Firefox for Windows 10 (64/32 bit). Mozilla Firefox is a popular free internet browser with many additional functions It has. Mozilla Firefox bit is a fast, full-featured Free Web Browser. Firefox includes pop-up blocking, tab-browsing, integrated Google, Yahoo and. Mozilla today shipped Firefox 43, the first edition that lets users download a production-grade bit version for Windows. Most web browsers are installed in Windows as bit versions by default, Firefox being the exception. -
Portableapps.Com
PortableApps.com PortableApps.com (abréviation de portable PortableApps.com Platform applications, en français application portable), est une suite logicielle open Logo source (composée de divers logiciels libres et versions portables de diverses applications) créée par John T. Haller destinée à être utilisée à partir d'un média amovible, tel une clé USB. Sommaire 1 Applications portable 2 Compatibilité 3 Historique 4 Liste des applications 4.1 Accessibilité 4.2 Développement 4.3 Éducation 4.4 Jeux 4.5 Graphiques et images 4.6 Internet Suite d'applications portable 4.7 Musique et vidéo 4.8 Bureautique 4.9 Sécurité Développeur John T. Haller 4.10 Utilitaires Dernière 12.05 5 Notes et références version (http://portableapps.com/download) (10 septembre 2014) 6 Voir aussi Environnement Microsoft Windows, et Wine sous 6.1 Articles connexes Linux/UNIX/BSD/Mac OS X 6.2 Liens externes Langue Multilingue Type Application portable 1 Licence GNU GPL Applications Site web www.portableapps.com portable (http://www.portableapps.com/) Article principal : Application portable. PortableApps.com définit leurs applications portables comme étant: « Une application portable est un programme informatique que vous pouvez transporter avec vous sur un dispositif portable et utiliser sur tout ordinateur Windows. Lorsque votre clé USB, disque dur portable, iPod ou autre appareil portable est branché, vous avez accès à votre logiciel et vos données personnelles, comme vous le feriez sur votre propre PC. Et si vous débranchez l'appareil, aucune de vos données personnelles ne sera 2 laissée sur l'ordinateur. » Compatibilité Les programmes sur PortableApps.com sont des programmes informatiques qui peuvent être stockés sur un périphérique de stockage portable et, ou amovible, sans être installés sur l'ordinateur hôte.