XUL – Desenvolvendo Aplicações Com Mozilla / Firefox
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Childnodes 1
Index Home | Projects | Docs | Jargon Bugzilla | LXR | Tree Status | Checkins Feedback | FAQ | Search A - B - C - D - E - F - G - H - I - J - K - L - M - N - O - P - Q - R - S - T - U - V - W - X - Y - Z Index Symbols _content 1 A addEventListener 1 alert() 1 align 1 alinkColor 1 anchors 1 appCodeName 1 appendChild 1 applets 1 appName 1 appVersion 1 attributes 1, 2 http://www.mozilla.org/docs/dom/domref/dom_shortIX.html (1 de 20) [09/06/2003 9:55:09] Index availLeft 1 availTop 1 availWidth 1 B back() 1 bgColor 1 blur 1 blur() 1 body 1 C captureEvents() 1 characterSet 1 childNodes 1 clear 1 clearInterval() 1 clearTimeout() 1 click 1 cloneContents 1 cloneNode 1 cloneRange 1 close 1 http://www.mozilla.org/docs/dom/domref/dom_shortIX.html (2 de 20) [09/06/2003 9:55:09] Index close() 1 closed 1 collapse 1 collapsed 1 colorDepth 1 commonAncestorContainer 1 compareBoundaryPoints 1 Components 1 confirm() 1 contentDocument 1, 2 contentWindow 1, 2 controllers 1 cookie 1 cookieEnabled 1 createAttribute 1 createDocumentFragment 1 createElement 1 createRange 1 createTextNode 1 crypto 1 cssRule 1 cssRule Object 1 http://www.mozilla.org/docs/dom/domref/dom_shortIX.html (3 de 20) [09/06/2003 9:55:09] Index cssRules 1 cssText 1 D defaultStatus 1 deleteContents 1 deleteRule 1 detach 1 directories 1 disabled 1 dispatchEvent 1 doctype 1 document 1 documentElement 1 DOM 1, 2 DOM 2 Range Interface 1 DOM window Interface 1 domain 1 dump() 1 E Elements Interface 1 embeds 1 http://www.mozilla.org/docs/dom/domref/dom_shortIX.html (4 de 20) [09/06/2003 9:55:09] -
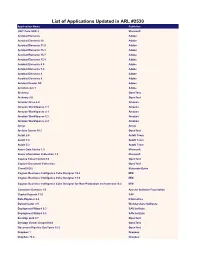
List of Applications Updated in ARL #2530
List of Applications Updated in ARL #2530 Application Name Publisher .NET Core SDK 2 Microsoft Acrobat Elements Adobe Acrobat Elements 10 Adobe Acrobat Elements 11.0 Adobe Acrobat Elements 15.1 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 15.9 Adobe Acrobat Elements 6.0 Adobe Acrobat Elements 7.0 Adobe Application Name Acrobat Elements 8 Adobe Acrobat Elements 9 Adobe Acrobat Reader DC Adobe Acrobat.com 1 Adobe Alchemy OpenText Alchemy 9.0 OpenText Amazon Drive 4.0 Amazon Amazon WorkSpaces 1.1 Amazon Amazon WorkSpaces 2.1 Amazon Amazon WorkSpaces 2.2 Amazon Amazon WorkSpaces 2.3 Amazon Ansys Ansys Archive Server 10.1 OpenText AutoIt 2.6 AutoIt Team AutoIt 3.0 AutoIt Team AutoIt 3.2 AutoIt Team Azure Data Studio 1.9 Microsoft Azure Information Protection 1.0 Microsoft Captiva Cloud Toolkit 3.0 OpenText Capture Document Extraction OpenText CloneDVD 2 Elaborate Bytes Cognos Business Intelligence Cube Designer 10.2 IBM Cognos Business Intelligence Cube Designer 11.0 IBM Cognos Business Intelligence Cube Designer for Non-Production environment 10.2 IBM Commons Daemon 1.0 Apache Software Foundation Crystal Reports 11.0 SAP Data Explorer 8.6 Informatica DemoCreator 3.5 Wondershare Software Deployment Wizard 9.3 SAS Institute Deployment Wizard 9.4 SAS Institute Desktop Link 9.7 OpenText Desktop Viewer Unspecified OpenText Document Pipeline DocTools 10.5 OpenText Dropbox 1 Dropbox Dropbox 73.4 Dropbox Dropbox 74.4 Dropbox Dropbox 75.4 Dropbox Dropbox 76.4 Dropbox Dropbox 77.4 Dropbox Dropbox 78.4 Dropbox Dropbox 79.4 Dropbox Dropbox 81.4 -

Forensics Evaluation of Privacy of Portable Web Browsers
International Journal of Computer Applications (0975 – 8887) Volume 147 – No. 8, August 2016 Forensics Evaluation of Privacy of Portable Web Browsers Ahmad Ghafarian Seyed Amin Hosseini Seno Department of Computer Science Department of Computer Engineering and Information Systems Faculty of Engineering University of North Georgia Ferdowsi University of Mashhad Dahlonega, GA 30005, USA Mashhad, Iran ABSTRACT relation to a computer forensic investigation is that the latter is Browsers claim private mode browsing saves no data on the a less tangible source of evidence [3]. host machine. Most popular web browsers also offer portable A study of tools and techniques for memory forensics can be versions of their browsers which can be launched from a found in [4]. The author has evaluated several command line removable device. When the removable device is removed, it and graphical user interface tools and provide the steps is claimed that traces of browsing activities will be deleted needed for memory forensics. Retrieving portable browsing and consequently private portable browsers offer better forensics artifacts left behind from main memory have privacy. This makes the task of computer forensics recently attracted some attention [5, 6]. The authors used investigators who try to reconstruct the past browsing history, limited memory forensics to retrieve forensics artifacts left in case of any computer incidence, more challenging. after a private portable browsing session. They argue that However, whether or not all data is deleted beyond forensic memory forensics is very promising in establishing a link recovery is a moot point. This research examines privacy of between the suspect and the retrieved data. -

(Hardening) De Navegadores Web Más Utilizados
UNIVERSIDAD DON BOSCO VICERRECTORÍA DE ESTUDIOS DE POSTGRADO TRABAJO DE GRADUACIÓN Endurecimiento (Hardening) de navegadores web más utilizados. Caso práctico: Implementación de navegadores endurecidos (Microsoft Internet Explorer, Mozilla Firefox y Google Chrome) en un paquete integrado para Microsoft Windows. PARA OPTAR AL GRADO DE: MAESTRO EN SEGURIDAD Y GESTION DEL RIESGO INFORMATICO ASESOR: Mg. JOSÉ MAURICIO FLORES AVILÉS PRESENTADO POR: ERICK ALFREDO FLORES AGUILAR Antiguo Cuscatlán, La Libertad, El Salvador, Centroamérica Febrero de 2015 AGRADECIMIENTOS A Dios Todopoderoso, por regalarme vida, salud y determinación para alcanzar un objetivo más en mi vida. A mi amada esposa, que me acompaño durante toda mi carrera, apoyó y comprendió mi dedicación de tiempo y esfuerzo a este proyecto y nunca dudó que lo concluiría con bien. A mis padres y hermana, que siempre han sido mis pilares y me enseñaron que lo mejor que te pueden regalar en la vida es una buena educación. A mis compañeros de trabajo, que mediante su esfuerzo extraordinario me han permitido contar con el tiempo necesario para dedicar mucho más tiempo a la consecución de esta meta. A mis amigos de los que siempre he tenido una palabra de aliento cuando la he necesitado. A mi supervisor y compañeros de la Escuela de Computación de la Universidad de Queens por facilitarme espacio, recursos, tiempo e información valiosa para la elaboración de este trabajo. A mi asesor de tesis, al director del programa de maestría y mis compañeros de la carrera, que durante estos dos años me han ayudado a lograr esta meta tan importante. Erick Alfredo Flores Aguilar INDICE I. -

Two Case Studies of Open Source Software Development: Apache and Mozilla
Two Case Studies of Open Source Software Development: Apache and Mozilla AUDRIS MOCKUS Avaya Labs Research ROY T FIELDING Day Software and JAMES D HERBSLEB Carnegie Mellon University According to its proponents, open source style software development has the capacity to compete successfully, and perhaps in many cases displace, traditional commercial development methods. In order to begin investigating such claims, we examine data from two major open source projects, the Apache web server and the Mozilla browser. By using email archives of source code change history and problem reports we quantify aspects of developer participation, core team size, code ownership, productivity, defect density, and problem resolution intervals for these OSS projects. We develop several hypotheses by comparing the Apache project with several commercial projects. We then test and refine several of these hypotheses, based on an analysis of Mozilla data. We conclude with thoughts about the prospects for high-performance commercial/open source process hybrids. Categories and Subject Descriptors: D.2.9 [Software Engineering]— Life cycle, Productivity, Pro- gramming teams, Software process models, Software Quality assurance, Time estimation; D.2.8 [Software Engineering]— Process metrics, Product metrics; K.6.3 [Software Management]— Software development, Software maintenance, Software process General Terms: Management, Experimentation, Measurement, Human Factors Additional Key Words and Phrases: Open source software, defect density, repair interval, code ownership, Apache, Mozilla This work was done while A. Mockus and J. D. Herbsleb were members of software Production Research Department at Lucent Technologies’ Bell Laboratories. This article is a significant extension to the authors’ paper, “A case study of open source software development: the Apache server,” that appeared in the Proceedings of the 22nd International Con- ference on Software Engineering, Limerick, Ireland, June 2000 (ICSE 2000), 263-272. -

A Review of XML-Compliant User Interface Description Languages
ÊÚÛ Ó ÅĹ ÓÑÔÐÒØ Í×Ö ÁÒØÖ ×ÖÔØÓÒ ÄÒÙ× ÆØÐ ËÓÙÓÒ Ò ÂÒ ÎÒÖÓÒØ ÍÒÚÖ×Ø Ø ÓÐÕÙ ÄÓÙÚ Ò¸ ÁÒ×ØØÙØ ³ÑÒ×ØÖ ØÓÒ Ø ×ØÓÒ ÈÐ × ÓÝÒ׸ ½ ¹ ¹½¿ ! ÄÓÙÚ Ò¹Ð ¹ÆÙÚ¸ Ð#ÙÑ ×ÓÙÓÒ¸ Ú Ò Ö ÓÒ Ø×Ý׺Ùк º ×ØÖغ ÖÚÛ Ó% &ÅĹ ÓÑÔÐ ÒØ Ù×Ö ÒØÖ% × ÖÔØÓÒ Ð Ò¹ #Ù #× × ÔÖÓ Ù Ø Ø ÓÑÔ Ö× ×#Ò¬ ÒØ×Ð ØÓÒÓ%Ú ÖÓÙ× Ð Ò¹ #Ù #× Ö××Ò# «ÖÒØ #Ó Ð׸ ×Ù ×ÑÙÐعÔÐ Ø%ÓÖÑ Ù×Ö ÒØÖ% ׸ Ú ¹ÒÔ ÒÒ ¸ ÓÒØÒØ ÐÚÖݸ Ò Ù×Ö ÒØÖ% × ÚÖØÙ ÐÐÝ ¹ ¬Òº Ì Ö × - Ò ÐÓÒ# ×ØÓÖÝ Ò ØÖ ØÓÒ ØÓ ØØÑÔØ ØÓ ÔØÙÖ Ø ××Ò Ó% Ù×Ö ÒØÖ% × Ø Ú ÖÓÙ× ÐÚÐ× Ó% -×ØÖ ØÓÒ %ÓÖ «Ö¹ ÒØ ÔÙÖÔ Ó×׺ Ì ÖØÙÖÒ Ó% Ø × ÕÙ×ØÓÒ ØÓ Ý # Ò× ÑÓÖ ØØÖ ØÓÒ¸ ÐÓÒ# ÛØ Ø ××ÑÒ ØÓÒ Ó% &ÅÄ Ñ Ö.ÙÔ Ð Ò#Ù #׸ Ò #Ú× -ÖØ ØÓ Ñ ÒÝ ÔÖÓÔ Ó× Ð× %ÓÖ ÒÛ Ù×Ö ÒØÖ% × ÖÔØÓÒ Ð Ò#Ù #º /ÓÒ×¹ ÕÙÒØÐݸ Ø Ö × Ò ØÓ ÓÒÙ Ø Ò Ò¹ÔØ Ò ÐÝ×× Ó% % ØÙÖ× Ø Ø Ñ . ÐÐ Ø × ÔÖÓÔ Ó× Ð× × ÖÑÒ ÒØ Ò ÔÔÖÓÔÖ Ø %ÓÖ ÒÝ×Ô ¬ ÔÙÖÔ Ó׺ Ì ÖÚÛ × ÜØÒ×ÚÐÝ ÓÒÙ Ø ÓÒ ×#Ò¬ ÒØ ×Ù-×Ø Ó% ×Ù Ð Ò#Ù #× - × ÓÒ Ò Ò ÐÝ×× #Ö Ò Ù×Ö ÒØÖ% × Ø Ø Û ØÖ ØÓ ÑÔÐÑÒØ ÖÓ×× Ø × Ð Ò#Ù #׺ ½ ÁÒØÖÓ Ù Ø ÓÒ ÓÖ ÝÖ׸ ÀÙÑÒ¹ÓÑÔÙØÖ ÁÒØÖØÓÒ ´ÀÁµ ÛØÒ×× Ô ÖÒÒÐ Ö ÓÖ Ø ÙÐØÑØ Í×Ö ÁÒØÖ ´ÍÁµ ×ÖÔØÓÒ ÄÒÙ ØØ ÛÓÙÐ ÐÐÝ Ô¹ ØÙÖ Ø ××Ò Ó ÛØ ÍÁ ÓÙÐ ÓÖ ×ÓÙÐ º ÍÁ ×ÖÔØÓÒ ÄÒÙ ´ÍÁĵ ÓÒ××Ø× Ó ¹ÐÚÐ ÓÑÔÙØÖ ÐÒÙ ÓÖ ×ÖÒ ÖØÖ×¹ Ø× Ó ÒØÖ×Ø Ó ÍÁ ÛØ Ö×Ô Ø ØÓ Ø Ö×Ø Ó Ò ÒØÖØÚ ÔÔÐØÓÒº ËÙ ÐÒÙ ÒÚÓÐÚ× ¬ÒÒ ×ÝÒØÜ ´ºº ÓÛ Ø× ÖØÖ×Ø× Ò ÜÔÖ×× Ò ØÖÑ× Ó Ø ÐÒÙµ Ò ×ÑÒØ× ´ºº¸ ÛØ Ó Ø× ÖØÖ¹ ×Ø× ÑÒ Ò Ø ÖÐ ÛÓÖеº ÁØ Ò ÓÒ×Ö × ÓÑÑÓÒ ÛÝ ØÓ ×Ô Ý ÍÁ ÒÔ ÒÒØÐÝ Ó ÒÝ ØÖØ ÐÒÙ ´ºº¸ ÔÖÓÖÑÑÒ ÓÖ ÑÖÙÔµ ØØ ÛÓÙÐ ×ÖÚ ØÓ ÑÔÐÑÒØ Ø× ÍÁº Ì ××Ù Ó ÍÁÄ Û× ¬Ö×Ø Ö× ÛÒ Ø Û× ÖÕÙÖ ØÓ ÚÐÓÔ ÍÁ Ð ÑÓ ÙÐ Ó Ò ÒØÖØÚ ÔÔÐØÓÒ ÖØÖ ØÒ ÑÖÐÝ ×Ö× Ó ÐÒ× Ó ×º ÌÒ¸ Ø× ××Ù Û× ÖÒÓÖ ÛÒ Ø ×Ö ÔÔ Ö× ØÓ ÑÓ Ð ÍÁ Ý×ØÓ ×Ô ¬ØÓÒ× ×Ó × -

Visual Validation of SSL Certificates in the Mozilla Browser Using Hash Images
CS Senior Honors Thesis: Visual Validation of SSL Certificates in the Mozilla Browser using Hash Images Hongxian Evelyn Tay [email protected] School of Computer Science Carnegie Mellon University Advisor: Professor Adrian Perrig Electrical & Computer Engineering Engineering & Public Policy School of Computer Science Carnegie Mellon University Monday, May 03, 2004 Abstract Many internet transactions nowadays require some form of authentication from the server for security purposes. Most browsers are presented with a certificate coming from the other end of the connection, which is then validated against root certificates installed in the browser, thus establishing the server identity in a secure connection. However, an adversary can install his own root certificate in the browser and fool the client into thinking that he is connected to the correct server. Unless the client checks the certificate public key or fingerprint, he would never know if he is connected to a malicious server. These alphanumeric strings are hard to read and verify against, so most people do not take extra precautions to check. My thesis is to implement an additional process in server authentication on a browser, using human recognizable images. The process, Hash Visualization, produces unique images that are easily distinguishable and validated. Using a hash algorithm, a unique image is generated using the fingerprint of the certificate. Images are easily recognizable and the user can identify the unique image normally seen during a secure AND accurate connection. By making a visual comparison, the origin of the root certificate is known. 1. Introduction: The Problem 1.1 SSL Security The SSL (Secure Sockets Layer) Protocol has improved the state of web security in many Internet transactions, but its complexity and neglect of human factors has exposed several loopholes in security systems that use it. -

Organizational Search in Email Systems Sruthi Bhushan Pitla Western Kentucky University, [email protected]
Western Kentucky University TopSCHOLAR® Masters Theses & Specialist Projects Graduate School 5-2012 Organizational Search in Email Systems Sruthi Bhushan Pitla Western Kentucky University, [email protected] Follow this and additional works at: http://digitalcommons.wku.edu/theses Part of the Databases and Information Systems Commons Recommended Citation Pitla, Sruthi Bhushan, "Organizational Search in Email Systems" (2012). Masters Theses & Specialist Projects. Paper 1161. http://digitalcommons.wku.edu/theses/1161 This Thesis is brought to you for free and open access by TopSCHOLAR®. It has been accepted for inclusion in Masters Theses & Specialist Projects by an authorized administrator of TopSCHOLAR®. For more information, please contact [email protected]. ORGANIZATIONAL SEARCH IN EMAIL SYSTEMS A Thesis Presented to The Faculty of the Department of Mathematics and Computer Science Western Kentucky University Bowling Green, Kentucky In Partial Fulfillment Of the Requirements for the Degree Master of Science By Sruthi Bhushan Pitla May 2012 ACKNOWLEDGMENTS It was a great pleasure working under my graduate advisor, Dr. Guangming Xing, who provided me with everything I need to succeed. His inspiration and guidance at each and every step made this Master of Science degree so rewarding and satisfactory. He always encouraged my work in every possible way and also gave me the freedom to express and implement my ideas without any restrictions. I feel very fortunate and proud to have been his student and really think the experience which I gained working under him is invaluable. I would like to whole heartedly thank Dr. Xing for the immense trust and patience he has over me. -

CARENA, a Tool to Capture and Replay Web Navigation Sessions
CARENA, a tool to capture and replay web navigation sessions I. J. Niño, B. de la Ossa, J. A. Gil, J. Sahuquillo and A. Pont § Department of Computer Engineering. Polytechnic University of Valencia Camino de Vera, s/n. 46071Valencia (Spain) {innigon1, berospe}@doctor.upv.es, {jagil, jsahuqui, apont}@disca.upv.es Abstract Web user behavior has widely changed over the last years. To perform precise and up-to-date web user behavior characterization is important to carry out representative web performance studies. In this sense, it is valuable to capture detailed information about the user’s experience, which permits to perform a fine grain characterization. Two main types of tools are distinguishable: complex commercial software tools like workload generators and academic tools. The latter mainly concentrate on the development of windows applications which gather web events (e.g., browser events) or tools modifying a part of the web browser code. In this paper, we present CARENA, a client-side browser-embedded tool to capture and replay user navigation sessions. Like some commercial software packages our tool captures information about the user session, which can be used later to replay or mimic the gathered user navigation. Nevertheless, unlike these software packages, our tool emulates the original user think times since these times are important to obtain precise and reliable performance results. Among the main features of CARENA are: multiplatform, open source, lightweight, standards based, easily installable and usable, programmed in JavaScript and XUL. 1. Introduction The main goal of Web performance research is to reduce the users’ perceived latency. An important set of research has concentrated on techniques like caching or prefetching web contents. -

Browser Security Guidance: Mozilla Firefox
GOV.UK Guidance Browser Security Guidance: Mozilla Firefox Published Contents 1. Usage scenario 2. Summary of browser security 3. How the browser can best satisfy the security recommendations 4. Network architecture 5. Deployment process 6. Recommended configuration 7. Enterprise considerations This ALPHA guidance builds on the End User Devices Platform Security Guidance and is applicable to devices running Mozilla Firefox on a supported and well configured version of Windows. This guidance was tested on 64bit Windows 8.1 Enterprise edition running Firefox 31.1.1 ESR. 1. Usage scenario Firefox will be used to access a variety of web services including: accessing intranet services hosted on an enterpriseprovided OFFICIAL network accessing enterprise cloud services sourced from the Digital Marketplace accessing other Internet services and web resources To support these scenarios, the following architectural choices are recommended: All data should be routed through a secure enterprise VPN to ensure the confidentiality and integrity of traffic intended for the enterprise intranet All Internet data should be routed through an enterprisehosted proxy to benefit from enterprise protective monitoring and logging solutions Arbitrary thirdparty extension installation by users is not permitted in the browser. A list of allowed trusted apps and extensions can be configured in Group Policy 2. Summary of browser security This browser has been assessed against each of the 12 security recommendations, and that assessment is shown in the table below. Explanatory text indicates that there is something related to that recommendation that the risk owners should be aware of. Rows marked [!] represent a more significant risk. -
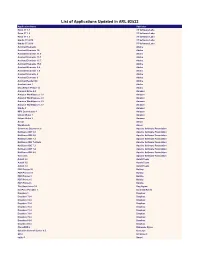
List of Applications Updated in ARL #2532
List of Applications Updated in ARL #2532 Application Name Publisher Robo 3T 1.1 3T Software Labs Robo 3T 1.2 3T Software Labs Robo 3T 1.3 3T Software Labs Studio 3T 2018 3T Software Labs Studio 3T 2019 3T Software Labs Acrobat Elements Adobe Acrobat Elements 10 Adobe Acrobat Elements 11.0 Adobe Acrobat Elements 15.1 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 15.9 Adobe Acrobat Elements 6.0 Adobe Acrobat Elements 7.0 Adobe Acrobat Elements 8 Adobe Acrobat Elements 9 Adobe Acrobat Reader DC Adobe Acrobat.com 1 Adobe Shockwave Player 12 Adobe Amazon Drive 4.0 Amazon Amazon WorkSpaces 1.1 Amazon Amazon WorkSpaces 2.1 Amazon Amazon WorkSpaces 2.2 Amazon Amazon WorkSpaces 2.3 Amazon Kindle 1 Amazon MP3 Downloader 1 Amazon Unbox Video 1 Amazon Unbox Video 2 Amazon Ansys Ansys Workbench Ansys Commons Daemon 1.0 Apache Software Foundation NetBeans IDE 5.0 Apache Software Foundation NetBeans IDE 5.5 Apache Software Foundation NetBeans IDE 7.2 Apache Software Foundation NetBeans IDE 7.2 Beta Apache Software Foundation NetBeans IDE 7.3 Apache Software Foundation NetBeans IDE 7.4 Apache Software Foundation NetBeans IDE 8.0 Apache Software Foundation Tomcat 5 Apache Software Foundation AutoIt 2.6 AutoIt Team AutoIt 3.0 AutoIt Team AutoIt 3.2 AutoIt Team PDF Printer 10 Bullzip PDF Printer 11 Bullzip PDF Printer 3 Bullzip PDF Printer 5 Bullzip PDF Printer 6 Bullzip The Unarchiver 3.1 Dag Agren KeePass Portable 1 Dominik Reichl Dropbox 1 Dropbox Dropbox 73.4 Dropbox Dropbox 74.4 Dropbox Dropbox 75.4 Dropbox Dropbox 76.4 Dropbox Dropbox 77.4 Dropbox -

Firefox Hacks Is Ideal for Power Users Who Want to Maximize The
Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader Firefox Hacks is ideal for power users who want to maximize the • Reviews effectiveness of Firefox, the next-generation web browser that is quickly • Errata gaining in popularity. This highly-focused book offers all the valuable tips • Academic and tools you need to enjoy a superior and safer browsing experience. Learn how to customize its deployment, appearance, features, and functionality. Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader • Reviews • Errata • Academic Copyright Credits About the Author Contributors Acknowledgments Preface Why Firefox Hacks? How to Use This Book How This Book Is Organized Conventions Used in This Book Using Code Examples Safari® Enabled How to Contact Us Got a Hack? Chapter 1. Firefox Basics Section 1.1. Hacks 1-10 Section 1.2. Get Oriented Hack 1. Ten Ways to Display a Web Page Hack 2. Ten Ways to Navigate to a Web Page Hack 3. Find Stuff Hack 4. Identify and Use Toolbar Icons Hack 5. Use Keyboard Shortcuts Hack 6. Make Firefox Look Different Hack 7. Stop Once-Only Dialogs Safely Hack 8. Flush and Clear Absolutely Everything Hack 9. Make Firefox Go Fast Hack 10. Start Up from the Command Line Chapter 2. Security Section 2.1. Hacks 11-21 Hack 11. Drop Miscellaneous Security Blocks Hack 12. Raise Security to Protect Dummies Hack 13. Stop All Secret Network Activity Hack 14.