(Hardening) De Navegadores Web Más Utilizados
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
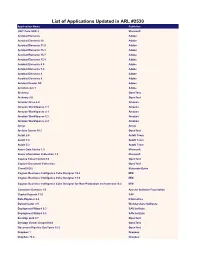
List of Applications Updated in ARL #2530
List of Applications Updated in ARL #2530 Application Name Publisher .NET Core SDK 2 Microsoft Acrobat Elements Adobe Acrobat Elements 10 Adobe Acrobat Elements 11.0 Adobe Acrobat Elements 15.1 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 15.9 Adobe Acrobat Elements 6.0 Adobe Acrobat Elements 7.0 Adobe Application Name Acrobat Elements 8 Adobe Acrobat Elements 9 Adobe Acrobat Reader DC Adobe Acrobat.com 1 Adobe Alchemy OpenText Alchemy 9.0 OpenText Amazon Drive 4.0 Amazon Amazon WorkSpaces 1.1 Amazon Amazon WorkSpaces 2.1 Amazon Amazon WorkSpaces 2.2 Amazon Amazon WorkSpaces 2.3 Amazon Ansys Ansys Archive Server 10.1 OpenText AutoIt 2.6 AutoIt Team AutoIt 3.0 AutoIt Team AutoIt 3.2 AutoIt Team Azure Data Studio 1.9 Microsoft Azure Information Protection 1.0 Microsoft Captiva Cloud Toolkit 3.0 OpenText Capture Document Extraction OpenText CloneDVD 2 Elaborate Bytes Cognos Business Intelligence Cube Designer 10.2 IBM Cognos Business Intelligence Cube Designer 11.0 IBM Cognos Business Intelligence Cube Designer for Non-Production environment 10.2 IBM Commons Daemon 1.0 Apache Software Foundation Crystal Reports 11.0 SAP Data Explorer 8.6 Informatica DemoCreator 3.5 Wondershare Software Deployment Wizard 9.3 SAS Institute Deployment Wizard 9.4 SAS Institute Desktop Link 9.7 OpenText Desktop Viewer Unspecified OpenText Document Pipeline DocTools 10.5 OpenText Dropbox 1 Dropbox Dropbox 73.4 Dropbox Dropbox 74.4 Dropbox Dropbox 75.4 Dropbox Dropbox 76.4 Dropbox Dropbox 77.4 Dropbox Dropbox 78.4 Dropbox Dropbox 79.4 Dropbox Dropbox 81.4 -

Forensics Evaluation of Privacy of Portable Web Browsers
International Journal of Computer Applications (0975 – 8887) Volume 147 – No. 8, August 2016 Forensics Evaluation of Privacy of Portable Web Browsers Ahmad Ghafarian Seyed Amin Hosseini Seno Department of Computer Science Department of Computer Engineering and Information Systems Faculty of Engineering University of North Georgia Ferdowsi University of Mashhad Dahlonega, GA 30005, USA Mashhad, Iran ABSTRACT relation to a computer forensic investigation is that the latter is Browsers claim private mode browsing saves no data on the a less tangible source of evidence [3]. host machine. Most popular web browsers also offer portable A study of tools and techniques for memory forensics can be versions of their browsers which can be launched from a found in [4]. The author has evaluated several command line removable device. When the removable device is removed, it and graphical user interface tools and provide the steps is claimed that traces of browsing activities will be deleted needed for memory forensics. Retrieving portable browsing and consequently private portable browsers offer better forensics artifacts left behind from main memory have privacy. This makes the task of computer forensics recently attracted some attention [5, 6]. The authors used investigators who try to reconstruct the past browsing history, limited memory forensics to retrieve forensics artifacts left in case of any computer incidence, more challenging. after a private portable browsing session. They argue that However, whether or not all data is deleted beyond forensic memory forensics is very promising in establishing a link recovery is a moot point. This research examines privacy of between the suspect and the retrieved data. -

Tim Berners-Lee, Lauréat Du Prix Turing 2016 Pour Avoir Inventé... Le Web Fabien Gandon
Pour tout le monde : Tim Berners-Lee, lauréat du prix Turing 2016 pour avoir inventé... le Web Fabien Gandon To cite this version: Fabien Gandon. Pour tout le monde : Tim Berners-Lee, lauréat du prix Turing 2016 pour avoir inventé... le Web. 1024 : Bulletin de la Société Informatique de France, Société Informatique de France, 2017, <http://www.societe-informatique-de-france.fr/bulletin/1024-numero-11/>. <hal-01623368> HAL Id: hal-01623368 https://hal.inria.fr/hal-01623368 Submitted on 25 Oct 2017 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. PRIX ET DISTINCTIONS Pour tout le monde : Tim Berners-Lee, lauréat du prix Turing 2016 pour avoir inventé... le Web Fabien Gandon 1 Introduction « Je suis moi et mes circonstances. » – Jose Ortega Quel pourrait être un point commun entre se renseigner à propos d’un concert, effectuer un virement depuis son compte bancaire, publier une base de données gé- nomiques, échanger avec ses enfants à l’autre bout du monde et accéder aux données de sa voiture [1] ? Le fait de pouvoir le faire à travers le Web. Il est en effet difficile de trouver une activité humaine qui n’ait pas été impactée par le Web et, alors que j’écris cet article en avril 2017, on estime que le Web compte plus de trois milliards d’uti- lisateurs directs de par le monde. -

Windows Geknackt Die Besten Tools 2013
ttbewerb Mit DVD Preise im Wert We 00001 www.onlinepc.ch Fr. 4.70 von Fr. 7‘154.– 985503 € 4,– Ultrabook, Digicam, WLAN-Bundles, 71422 iPhone-Hüllen und Software S.52 97 System verschlüsseln 51 DVD Zürich So geht‘s: Der wirksamste Schutz gegen Datenklau S.30 Auf 8051 D Nr. 1 – Januar 2013 16 Internet-Tipps Auf DV AZB Das Computer-Magazin Firefox-Befehle, Cloud verschlüsseln, Mails sichern... S.30 D Auf DV Total Mounter Virtuelle CDs und DVDs auf jedem PC brennen – ohne Brenner S.30 ▪ Der Schutz macht Windows unzerstörbar ▪ Nach jedem Neustart ist Windows wie neu ▪ Der Schutz lässt sich ein- und ausschalten S.22 Die besten Tools 2013 Das sind die beliebtesten Open-Source-Programme S.36 D D Auf DV Auf DV Windows geknackt So booten Sie jeden Sicherheit PC mit Windows 7 S.42 am PPaasswortsswort besten Abp Mon 9.0 50 Hammertipps Die Überwacht RAM, CPU, Die besten Tricks für vorbei S.16 Special Netzwerk… S.26 Windows 7 S.14 Mit Sicherheits-Tipps Anzeige EDITORIAL /INHALT INHALT 1/2013 PC am Passwort Schutzmodus für vorbei booten: Windows 7 Ein Trick überlistet Der Schutzmodus den Schutz von macht Windows Windows 16 unzerstörbar 22 Leserumfrage Top-100-Software Virenalarm, was tun? Mitmachen und eine Video-Soft- Aus den monatlichen Top 10 Downloads hat Keine Panik! So ware von Magix die Redaktion für Sie eine Auswahl getrof- werden Sie die gewinnen! 62 fen und die 100 beliebtesten Programme auf Schädlinge los 46 die Heft-DVD gepackt. Die Tools decken ein breites Spektrum ab – vom Browser bis zum E-Mail-Programm, von der Sicherheitssoftware bis zum Videoplayer und vom Backup-Pro- AKTUELL TEST & KAUFBERATUNG gramm bis zum Passwortmanager (Seite 36). -
Features Guide [email protected] Table of Contents
Features Guide [email protected] Table of Contents About Us .................................................................................. 3 Make Firefox Yours ............................................................... 4 Privacy and Security ...........................................................10 The Web is the Platform ...................................................11 Developer Tools ..................................................................13 2 About Us About Mozilla Mozilla is a global community with a mission to put the power of the Web in people’s hands. As a nonprofit organization, Mozilla has been a pioneer and advocate for the Web for more than 15 years and is focused on creating open standards that enable innovation and advance the Web as a platform for all. We are committed to delivering choice and control in products that people love and can take across multiple platforms and devices. For more information, visit www.mozilla.org. About Firefox Firefox is the trusted Web browser of choice for half a billion people around the world. At Mozilla, we design Firefox for how you use the Web. We make Firefox completely customizable so you can be in control of creating your best Web experience. Firefox has a streamlined and extremely intuitive design to let you focus on any content, app or website - a perfect balance of simplicity and power. Firefox makes it easy to use the Web the way you want and offers leading privacy and security features to help keep you safe and protect your privacy online. Mozilla continues to move the Web forward by pioneering new open source technologies such as asm.js, Emscripten and WebAPIs. Firefox also has a range of amazing built-in developer tools to provide a friction-free environment for building Web apps and Web content. -
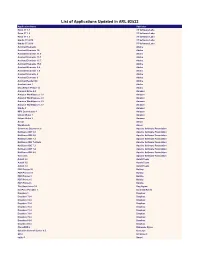
List of Applications Updated in ARL #2532
List of Applications Updated in ARL #2532 Application Name Publisher Robo 3T 1.1 3T Software Labs Robo 3T 1.2 3T Software Labs Robo 3T 1.3 3T Software Labs Studio 3T 2018 3T Software Labs Studio 3T 2019 3T Software Labs Acrobat Elements Adobe Acrobat Elements 10 Adobe Acrobat Elements 11.0 Adobe Acrobat Elements 15.1 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 15.9 Adobe Acrobat Elements 6.0 Adobe Acrobat Elements 7.0 Adobe Acrobat Elements 8 Adobe Acrobat Elements 9 Adobe Acrobat Reader DC Adobe Acrobat.com 1 Adobe Shockwave Player 12 Adobe Amazon Drive 4.0 Amazon Amazon WorkSpaces 1.1 Amazon Amazon WorkSpaces 2.1 Amazon Amazon WorkSpaces 2.2 Amazon Amazon WorkSpaces 2.3 Amazon Kindle 1 Amazon MP3 Downloader 1 Amazon Unbox Video 1 Amazon Unbox Video 2 Amazon Ansys Ansys Workbench Ansys Commons Daemon 1.0 Apache Software Foundation NetBeans IDE 5.0 Apache Software Foundation NetBeans IDE 5.5 Apache Software Foundation NetBeans IDE 7.2 Apache Software Foundation NetBeans IDE 7.2 Beta Apache Software Foundation NetBeans IDE 7.3 Apache Software Foundation NetBeans IDE 7.4 Apache Software Foundation NetBeans IDE 8.0 Apache Software Foundation Tomcat 5 Apache Software Foundation AutoIt 2.6 AutoIt Team AutoIt 3.0 AutoIt Team AutoIt 3.2 AutoIt Team PDF Printer 10 Bullzip PDF Printer 11 Bullzip PDF Printer 3 Bullzip PDF Printer 5 Bullzip PDF Printer 6 Bullzip The Unarchiver 3.1 Dag Agren KeePass Portable 1 Dominik Reichl Dropbox 1 Dropbox Dropbox 73.4 Dropbox Dropbox 74.4 Dropbox Dropbox 75.4 Dropbox Dropbox 76.4 Dropbox Dropbox 77.4 Dropbox -

Piratebrowser Artifacts
PirateBrowser Artifacts Written by Chris Antonovich Researched by Olivia Hatalsky 175 Lakeside Ave, Room 300A Phone: 802/865-5744 Fax: 802/865-6446 http://www.lcdi.champlin.edu Published Date Patrick Leahy Center for Digital Investigation (LCDI) Disclaimer: This document contains information based on research that has been gathered by employee(s) of The Senator Patrick Leahy Center for Digital Investigation (LCDI). The data contained in this project is submitted voluntarily and is unaudited. Every effort has been made by LCDI to assure the accuracy and reliability of the data contained in this report. However, LCDI nor any of our employees make no representation, warranty or guarantee in connection with this report and hereby expressly disclaims any liability or responsibility for loss or damage resulting from use of this data. Information in this report can be downloaded and redistributed by any person or persons. Any redistribution must maintain the LCDI logo and any references from this report must be properly annotated. Contents Introduction ............................................................................................................................................................................. 2 Background: ........................................................................................................................................................................ 2 Purpose and Scope: ............................................................................................................................................................ -

Firefox for Android Reviewer's Guide
FIREFOX FOR ANDROID REVIEWER’S GUIDE Contact us: [email protected] FIREFOX FOR ANDROID TABLE OF CONTENTS About Mozilla for Android 1 Get Started 2 Type Less, Browse More 3 Get Up and Go 4 Customize and Go 6 Protecting Your Privacy 7 Favorite Features 8 The Cutting Edge 9 FIREFOX FOR ANDROID ABOUT MOZILLA Mozilla is a global, nonprofit organization dedicated to making the Web better. We believe in principle over profit, and that the Internet is a shared public resource to be cared for, not a commodity to be sold. We work with a worldwide community to create open source software like Mozilla Firefox, and to innovate for the benefit of the individual and the betterment of the Web. The result is great products built by passionate people and better choices for everyone. For more information, visit www.mozilla.org Mozilla Firefox for Android Mozilla Firefox introduces a new Web experience for Android (2.1 and above) devices. Based on the same open technology platform as the desktop version of Firefox, you have an easy, fast and customizable way to take your Firefox anywhere you go. Innovative features in Firefox make browsing the Web on Android devices easy and efficient so you can spend more time browsing and less time typing. Firefox Sync is integrated into Firefox, giving you access to your Awesome Bar history, bookmarks, open tabs and passwords across computers and mobile devices. Firefox respects your privacy and safeguards your security with features like end-to-end encryption in Firefox Sync and Do Not Track.. Firefox for Android enables you to personalize your Firefox with add-ons to change the look, features or functionality of Firefox to fit your needs. -

Of the United States District Court for the District
Case 2:04-cv-01045-JFM Document 61-2 Filed 08/08/11 Page 1 of 25 APPENDIX B This Appendix explains why the Findings of Fact (“Findings”) of the United States District Court for the District of Columbia in the case United States v. Microsoft Corp., 84 F. Supp. 2d 9 (D.D.C. 1999) (the “Government case”), that the United States Court of Appeals for the District of Columbia Circuit affirmed in United States v. Microsoft Corp., 253 F.3d 34 (D.C. Cir. 2001), for which Novell seeks preclusion are (1) material to the issues in this case and (2) necessary to the determinations from the Government case that were affirmed by the D.C. Circuit. The text of the Findings is quoted in Appendix C. The offense of monopolization has two elements: “(1) the possession of monopoly power in the relevant market and (2) the willful acquisition or maintenance of that power as distinguished from growth or development as a consequence of a superior product, business acumen, or historic accident.” United States v. Grinnell Corp., 384 U.S. 563, 570-71 (1966). The D.C. Circuit affirmed the D.C. District Court’s determination that Microsoft Corporation (“Microsoft”) engaged in illegal acts of monopolization for the purpose of thwarting the threat posed by middleware software applications to Microsoft’s monopoly in the personal computer (“PC”) operating systems market. The D.C. District Court based its determination on rulings, also affirmed by the D.C. Circuit, regarding: the definition of the relevant market; Microsoft’s dominant share in the relevant market; the existence of a barrier to entry; Microsoft’s possession of monopoly power; the exclusionary effect of Microsoft’s conduct; the lack of procompetitive justification for Microsoft’s conduct; and the harm caused to competition and consumers. -

Ministry of Education EFIS 2.0 - User Set up Guide
Ministry of Education EFIS 2.0 - User Set Up Guide Version 1.9 August 22, 2016 User Setup Guide 1 Table of Contents 1 Table of Contents .............................................................................................................................................. 2 2 Document History ............................................................................................................................................. 3 3 Description and System Requirements ................................................................................................... 4 3.1 Description ............................................................................................................................................... 4 3.2 User System Requirements ............................................................................................................... 5 4 Firefox setup ....................................................................................................................................................... 6 4.1 Recommended Version ....................................................................................................................... 6 4.2 Download File ......................................................................................................................................... 6 4.3 Download from Workspace .............................................................................................................. 6 4.4 Install Firefox ......................................................................................................................................... -

NAVEGAR CON FIREFOX José Lozano Abogado
NAVEGAR CON FIREFOX José Lozano Abogado No, no se trata de un nuevo modelo de embarcación de recreo, ni del último cohete espacial, ni siquiera de un modelo de GPS, sino de un programa para navegar por internet, un navegador. odos sabemos para qué sirve un programa de este tipo y supongo que la mayoría usarán para este fin el programa Internet Explorer, de Microsoft, y sólo unos pocos tendrán experiencia con Firefox. Como considero que éste posee unas características muy interesan- tes que nos pueden ser muy útiles en nuestro trabajo y en nuestro ocio, voy a intentar transmitirles las bondades de este navegador de internet, con la intención, si no de sustituir totalmente al IE de Microsoft, sí al menos de compartir con éste la exploración del universo virtual en que se ha converti- do internet. Mozilla Firefox es un navegador web multiplataforma, que funciona en distintos sistema operativos, Windows, Linux, MacOS, etc... Es un producto gratuito y de código abierto, “open source”. Firefox incorpora numerosas caracte- rísticas avanzadas, siendo las más destacadas el bloqueo de ventanas emergentes, el uso de marcadores dinámicos, so- porte para estándares abiertos, navegación por pestañas, y un mecanismo para añadir funcionalidades mediante extensio- nes. Estas dos últimas son las más atractivas y útiles caracte- rísticas, por lo que voy a detenerme en ellas. Navegación por pestañas.- Consiste en poder abrir en De igual modo, se puede definir un grupo de pestañas una sola ventana del programa varias páginas a la vez, pu- como páginas de inicio, de forma que cada vez que ejecuta- diendo ir de una a otra a través de pestañas. -

Designing for Extensibility and Planning for Conflict
Designing for Extensibility and Planning for Conflict: Experiments in Web-Browser Design Benjamin S. Lerner A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy University of Washington 2011 Program Authorized to Offer Degree: UW Computer Science & Engineering University of Washington Graduate School This is to certify that I have examined this copy of a doctoral dissertation by Benjamin S. Lerner and have found that it is complete and satisfactory in all respects, and that any and all revisions required by the final examining committee have been made. Chair of the Supervisory Committee: Daniel Grossman Reading Committee: Daniel Grossman Steven Gribble John Zahorjan Date: In presenting this dissertation in partial fulfillment of the requirements for the doctoral degree at the University of Washington, I agree that the Library shall make its copies freely available for inspection. I further agree that extensive copying of this dissertation is allowable only for scholarly purposes, consistent with “fair use” as prescribed in the U.S. Copyright Law. Requests for copying or reproduction of this dissertation may be referred to Proquest Information and Learning, 300 North Zeeb Road, Ann Arbor, MI 48106-1346, 1-800-521-0600, to whom the author has granted “the right to reproduce and sell (a) copies of the manuscript in microform and/or (b) printed copies of the manuscript made from microform.” Signature Date University of Washington Abstract Designing for Extensibility and Planning for Conflict: Experiments in Web-Browser Design Benjamin S. Lerner Chair of the Supervisory Committee: Associate Professor Daniel Grossman UW Computer Science & Engineering The past few years have seen a growing trend in application development toward “web ap- plications”, a fuzzy category of programs that currently (but not necessarily) run within web browsers, that rely heavily on network servers for data storage, and that are developed and de- ployed differently from traditional desktop applications.