Piratebrowser Artifacts
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Privacy Resources 2018
Privacy Resources 2018 By Marcus P. Zillman, M.S., A.M.H.A. Executive Director – Virtual Private Library [email protected] Privacy Resources 2018 is a comprehensive listing of privacy resources currently available on the Internet. These include associations, indexes, search engines as well as individual websites and sources that supply the latest technology and information about privacy and how it relates to you and the Internet. The below list of sources is taken from my Subject Tracer™ Information Blog titled Privacy Resources and is constantly updated with Subject Tracer™ bots from the following URL: http://www.PrivacyResources.info/ These resources and sources will help you to discover the many pathways available to you through the Internet to find the latest privacy sources and sites. Figure 1: Privacy Resources 2018 Subject Tracer™ Information Blog 1 [Updated: April 1, 2018] Privacy Resources 2018 White Paper Link Compilation http://www.PrivacyResources.info/ [email protected] Voice: 800-858-1462 © 2007, 2008, 2009, 2010, 2011, 2012, 2013, 2014, 2015, 2016, 2017, 2018 Marcus P. Zillman, M.S., A.M.H.A. Privacy Resources 2018: 10 Best Security and Privacy Apps for Smartphones and Tablets http://drippler.com/drip/10-best-security-privacy-apps-smartphones-tablets 10 Minute Mail http://10minutemail.com/10MinuteMail/index.html 10 Privacy Gadgets To Help You Keep a Secret http://www.popsci.com/keep-your-secrets-a-secret 10 Reasons to Use a VPN for Private Web Browsing http://netforbeginners.about.com/od/readerpicks/tp/Reasons-to-Use-a-VPN-Service.htm -
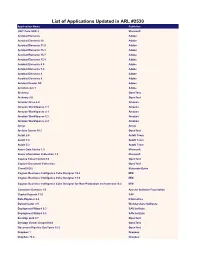
List of Applications Updated in ARL #2530
List of Applications Updated in ARL #2530 Application Name Publisher .NET Core SDK 2 Microsoft Acrobat Elements Adobe Acrobat Elements 10 Adobe Acrobat Elements 11.0 Adobe Acrobat Elements 15.1 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 15.9 Adobe Acrobat Elements 6.0 Adobe Acrobat Elements 7.0 Adobe Application Name Acrobat Elements 8 Adobe Acrobat Elements 9 Adobe Acrobat Reader DC Adobe Acrobat.com 1 Adobe Alchemy OpenText Alchemy 9.0 OpenText Amazon Drive 4.0 Amazon Amazon WorkSpaces 1.1 Amazon Amazon WorkSpaces 2.1 Amazon Amazon WorkSpaces 2.2 Amazon Amazon WorkSpaces 2.3 Amazon Ansys Ansys Archive Server 10.1 OpenText AutoIt 2.6 AutoIt Team AutoIt 3.0 AutoIt Team AutoIt 3.2 AutoIt Team Azure Data Studio 1.9 Microsoft Azure Information Protection 1.0 Microsoft Captiva Cloud Toolkit 3.0 OpenText Capture Document Extraction OpenText CloneDVD 2 Elaborate Bytes Cognos Business Intelligence Cube Designer 10.2 IBM Cognos Business Intelligence Cube Designer 11.0 IBM Cognos Business Intelligence Cube Designer for Non-Production environment 10.2 IBM Commons Daemon 1.0 Apache Software Foundation Crystal Reports 11.0 SAP Data Explorer 8.6 Informatica DemoCreator 3.5 Wondershare Software Deployment Wizard 9.3 SAS Institute Deployment Wizard 9.4 SAS Institute Desktop Link 9.7 OpenText Desktop Viewer Unspecified OpenText Document Pipeline DocTools 10.5 OpenText Dropbox 1 Dropbox Dropbox 73.4 Dropbox Dropbox 74.4 Dropbox Dropbox 75.4 Dropbox Dropbox 76.4 Dropbox Dropbox 77.4 Dropbox Dropbox 78.4 Dropbox Dropbox 79.4 Dropbox Dropbox 81.4 -

Malware Extorts Cash from Bittorrent Users | Torrentfreak
Malware Extorts Cash From BitTorrent Users | TorrentFreak http://torrentfreak.com/malware-extort-cash-from-bittorrent-use... TorrentFreak Home Contact About Archives Forum Malware Extorts Cash From BitTorrent Users Written by enigmax on April 11, 2010 A new type of malware is riding the wave of file-sharing pre-settlement letters by infecting BitTorrent users’ machines and then demanding payments in order to make imaginary lawsuits go away. ICPP Foundation try to give the impression they are RIAA and MPAA affiliated but the whole thing is a scam to extort cash and obtain credit card details. ICCP Foundation claims to be an international company operating out of Switzerland. They say they are “committed to promoting the cultural and economic benefits of copyright” while assisting their partners to fight “copyright theft around the world”. In fact what they really do is operate a scam to extort money from BitTorrent users. Right at this moment we are unsure of the exact route of infection, but somehow malware (probably in either fake file or attached virus form) is displaying a “copyright violation alert” on the victim’s screen, locking it, and redirecting users to the ICPP site where they are told they have been caught infringing copyright. There they are warned their offenses could result in 5 years in prison and a $250,000 fine and are given the option to take the (fake) case to court. They are also offered a chance to make the whole thing go away for the payment of a ‘fine’ of around $400. Victims are also prompted to give their name, address and full credit card details – it is unclear how this information is further abused but it doesn’t look good. -

Forensics Evaluation of Privacy of Portable Web Browsers
International Journal of Computer Applications (0975 – 8887) Volume 147 – No. 8, August 2016 Forensics Evaluation of Privacy of Portable Web Browsers Ahmad Ghafarian Seyed Amin Hosseini Seno Department of Computer Science Department of Computer Engineering and Information Systems Faculty of Engineering University of North Georgia Ferdowsi University of Mashhad Dahlonega, GA 30005, USA Mashhad, Iran ABSTRACT relation to a computer forensic investigation is that the latter is Browsers claim private mode browsing saves no data on the a less tangible source of evidence [3]. host machine. Most popular web browsers also offer portable A study of tools and techniques for memory forensics can be versions of their browsers which can be launched from a found in [4]. The author has evaluated several command line removable device. When the removable device is removed, it and graphical user interface tools and provide the steps is claimed that traces of browsing activities will be deleted needed for memory forensics. Retrieving portable browsing and consequently private portable browsers offer better forensics artifacts left behind from main memory have privacy. This makes the task of computer forensics recently attracted some attention [5, 6]. The authors used investigators who try to reconstruct the past browsing history, limited memory forensics to retrieve forensics artifacts left in case of any computer incidence, more challenging. after a private portable browsing session. They argue that However, whether or not all data is deleted beyond forensic memory forensics is very promising in establishing a link recovery is a moot point. This research examines privacy of between the suspect and the retrieved data. -

Digital Fountain Erasure-Recovery in Bittorrent
UNIVERSITÀ DEGLI STUDI DI BERGAMO Facoltà di Ingegneria Corso di Laurea Specialistica in Ingegneria Informatica Classe n. 35/S – Sistemi Informatici Digital Fountain Erasure Recovery in BitTorrent: integration and security issues Relatore: Chiar.mo Prof. Stefano Paraboschi Correlatore: Chiar.mo Prof. Andrea Lorenzo Vitali Tesi di Laurea Specialistica Michele BOLOGNA Matricola n. 56108 ANNO ACCADEMICO 2007 / 2008 This thesis has been written, typeset and prepared using LATEX 2". Printed on December 5, 2008. Alla mia famiglia “Would you tell me, please, which way I ought to go from here?” “That depends a good deal on where you want to get to,” said the Cat. “I don’t much care where —” said Alice. “Then it doesn’t matter which way you go,” said the Cat. “— so long as I get somewhere,” Alice added as an explanation. “Oh, you’re sure to do that,” said the Cat, “if you only walk enough.” Lewis Carroll Alice in Wonderland Acknowledgments (in Italian) Ci sono molte persone che mi hanno aiutato durante lo svolgimento di questo lavoro. Il primo ringraziamento va ai proff. Stefano Paraboschi e Andrea Vitali per la disponibilità, la competenza, i consigli, la pazienza e l’aiuto tecnico che mi hanno saputo dare. Grazie di avermi dato la maggior parte delle idee che sono poi confluite nella mia tesi. Un sentito ringraziamento anche a Andrea Rota e Ruben Villa per l’aiuto e i chiarimenti che mi hanno gentilmente fornito. Vorrei ringraziare STMicroelectronics, ed in particolare il gruppo Advanced System Technology, per avermi offerto le infrastrutture, gli spa- zi e tutto il necessario per svolgere al meglio il mio periodo di tirocinio. -

Piratez Are Just Disgruntled Consumers Reach Global Theaters That They Overlap the Domestic USA Blu-Ray Release
Moviegoers - or perhaps more accurately, lovers of cinema - are frustrated. Their frustrations begin with the discrepancies in film release strategies and timing. For example, audiences that saw Quentin Tarantino’s1 2 Django Unchained in the United States enjoyed its opening on Christmas day 2012; however, in Europe and other markets, viewers could not pay to see the movie until after the 17th of January 2013. Three weeks may not seem like a lot, but some movies can take months to reach an international audience. Some take so long to Piratez Are Just Disgruntled Consumers reach global theaters that they overlap the domestic USA Blu-Ray release. This delay can seem like an eternity for ultiscreen is at the top of the entertainment a desperate fan. This frustrated enthusiasm, combined industry’s agenda for delivering digital video. This with a lack of timely availability, leads to the feeling of M is discussed in the context of four main screens: being treated as a second class citizen - and may lead TVs, PCs, tablets and mobile phones. The premise being the over-anxious fan to engage in piracy. that multiscreen enables portability, usability and flexibility for consumers. But, there is a fifth screen which There has been some evolution in this practice, with is often overlooked – the cornerstone of the certain films being released simultaneously to a domestic and global audience. For example, Avatar3 was released entertainment industry - cinema. This digital video th th ecosystem is not complete without including cinema, and in theaters on the 10 and 17 of December in most it certainly should be part of the multiscreen discussion. -

(Hardening) De Navegadores Web Más Utilizados
UNIVERSIDAD DON BOSCO VICERRECTORÍA DE ESTUDIOS DE POSTGRADO TRABAJO DE GRADUACIÓN Endurecimiento (Hardening) de navegadores web más utilizados. Caso práctico: Implementación de navegadores endurecidos (Microsoft Internet Explorer, Mozilla Firefox y Google Chrome) en un paquete integrado para Microsoft Windows. PARA OPTAR AL GRADO DE: MAESTRO EN SEGURIDAD Y GESTION DEL RIESGO INFORMATICO ASESOR: Mg. JOSÉ MAURICIO FLORES AVILÉS PRESENTADO POR: ERICK ALFREDO FLORES AGUILAR Antiguo Cuscatlán, La Libertad, El Salvador, Centroamérica Febrero de 2015 AGRADECIMIENTOS A Dios Todopoderoso, por regalarme vida, salud y determinación para alcanzar un objetivo más en mi vida. A mi amada esposa, que me acompaño durante toda mi carrera, apoyó y comprendió mi dedicación de tiempo y esfuerzo a este proyecto y nunca dudó que lo concluiría con bien. A mis padres y hermana, que siempre han sido mis pilares y me enseñaron que lo mejor que te pueden regalar en la vida es una buena educación. A mis compañeros de trabajo, que mediante su esfuerzo extraordinario me han permitido contar con el tiempo necesario para dedicar mucho más tiempo a la consecución de esta meta. A mis amigos de los que siempre he tenido una palabra de aliento cuando la he necesitado. A mi supervisor y compañeros de la Escuela de Computación de la Universidad de Queens por facilitarme espacio, recursos, tiempo e información valiosa para la elaboración de este trabajo. A mi asesor de tesis, al director del programa de maestría y mis compañeros de la carrera, que durante estos dos años me han ayudado a lograr esta meta tan importante. Erick Alfredo Flores Aguilar INDICE I. -

From Sony to SOPA: the Technology-Content Divide
From Sony to SOPA: The Technology-Content Divide The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation John Palfrey, Jonathan Zittrain, Kendra Albert, and Lisa Brem, From Sony to SOPA: The Technology-Content Divide, Harvard Law School Case Studies (2013). Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:11029496 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Open Access Policy Articles, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#OAP http://casestudies.law.harvard.edu By John Palfrey, Jonathan Zittrain, Kendra Albert, and Lisa Brem February 23, 2013 From Sony to SOPA: The Technology-Content Divide Background Note Copyright © 2013 Harvard University. No part of this publication may be reproduced, stored in a retrieval system, used in a spreadsheet, or transmitted in any form or by any means – electronic, mechanical, photocopying, recording, or otherwise – without permission. "There was a time when lawyers were on one side or the other of the technology content divide. Now, the issues are increasingly less black-and-white and more shades of gray. You have competing issues for which good lawyers provide insights on either side." — Laurence Pulgram, partner, Fenwick & Westi Since the invention of the printing press, there has been tension between copyright holders, who seek control over and monetary gain from their creations, and technology builders, who want to invent without worrying how others might use that invention to infringe copyrights. -

Custostech Economic White Paper
The Economics of Digital Piracy and CustosTech tech WP 01/2014 June 2014 Executive Summary Custos Media Technologies (CustosTech) provides a novel approach to fighting digital piracy. While the technology itself is cutting edge, the true innovation of the technology is a behavioural one: the incentive structure of the pirating community is warped, leading to a discontinuation of piracy. To understand the innovation, this white paper sets out to explain !the piracy ecosystem within which the technology will be effective. ! The consumer and producer welfare functions are considered from a theoretical point of view. These functions explain the incentive of consumers to choose to pirate movies: consumers who expect a larger net-gain to their utility from piracy will opt to do so. This net gain is determined by the relative valuations of legal to illegal copies, and the relative cost of use. Staying with theoretical considerations, the options facing producers to limit !piracy are investigated: pricing, protection, and value-adding. ! This theoretical framework is then used to understand the incentive structures governing the players in the ecosystem: hosts, uploaders and downloaders. Hosts are found to be almost exclusively profit-motivated, with uploaders motivated by profit or altruism. Downloaders are split into four categories, depending on their main motivation or justification for pirating. An analysis of incumbent anti-piracy technologies shows that these technologies are almost all ineffective, sometimes even acting to increase the !preference for piracy.! With this background, the need for a new solution becomes all too apparent. The CustosTech technology is considered within the piracy framework, and the technological and economic effects explained. -

Antifragile White Paper Draft 3.Pages
Piracy as an Antifragile System tech WP 01/2015 July 2015 Executive Summary Attacks on the piracy economy have thus far been unsuccessful. The piracy community has not only shown resilience to these attacks, but has also become more sophisticated and resilient as a result of them. Systems that show this characteristic response to ex- ternal stressors are defined as antifragile. Traditional centralized attacks are not only ineffective against such systems, but are counter-productive. These systems are not impervious to attacks, however. Decentralized attacks that warp the connections between nodes destroy the system from within. Some system-based attacks on piracy have been attempted, but lacked the technology required to be effec- tive. A new technology, CustosTech, built on the Bitcoin blockchain, attacks the system by turning pirates against each other. The technology enables and incentivizes anyone in the world to anonymously act as an informant, disclosing the identity of the first in- fringer – the pirate uploader. This internal decentralized attack breaks the incentive structures governing the uploader-downloader relationship, and thus provides a sus- tainable deterrent to piracy. Table of Contents Introduction to Antifragility 1 Features of Antifragile Systems 1 Piracy as an Antifragile System 2 Sophisticated Pirates 3 Popcorn Time 5 Attacking 5 Antifragile Systems 5 Attacking Piracy 5 Current Approaches 6 New Tools 6 How it Works 7 Conclusion 7 White paper 01/2015 Introduction to Antifragility Antifragility refers to a system that becomes bet- ter, or stronger, in response to shocks or attacks. Nassim Taleb developed the term1 to explain sys- tems that were not only resilient, but also thrived under stress. -

UK Blocking-2015-12-07-Brd
THE EFFECT OF PIRACY WEBSITE BLOCKING ON CONSUMER BEHAVIOR Brett Danaher‡ [email protected] Michael D. Smith† [email protected] Rahul Telang† [email protected] This Version: November 2015 Acknowledgements: This research was conducted as part of Carnegie Mellon University’s Initiative for Digital Entertainment Analytics (IDEA), which receives unrestricted (gift) funding from the Motion Picture Association of America. Danaher acknowledges support from an NBER Economics of Digitization research grant. This research was conducted independently without any oversight or editorial control. The authors presented this paper at the December 2014 Workshop on Information Systems and Economics and to seminar participants at the University of Arizona’s Eller School of Management and thank participants for their helpful feedback. All findings and errors are entirely our own. ‡ Department of Economics, Wellesley College, Wellesley, MA, 02481 † School of Information Systems and Management, Heinz College, Carnegie Mellon University, Pitts- burgh, PA, 15213. THE EFFECT OF PIRACY WEBSITE BLOCKING ON CONSUMER BEHAVIOR ABSTRACT Understanding the relationship between copyright policy and consumer behavior is an in- creasingly important topic for participants in digital media markets. In this paper we seek to study how consumer behavior changes when Internet Service Providers are required to block access to major piracy websites. We do this in the context of two court-ordered events affecting consumers in the UK: The blocking order directed at The Pirate Bay in May 2012, and blocking orders directed at 19 major piracy sites in October and November 2013. Our results show that blocking The Pirate Bay only caused a small reduction in total pira- cy — instead, consumers seemed to turn to other piracy sites or Virtual Private Networks that allowed them to circumvent the block.