Build Muscle in Four Easy Steps!
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
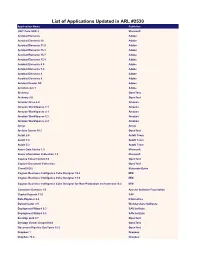
List of Applications Updated in ARL #2530
List of Applications Updated in ARL #2530 Application Name Publisher .NET Core SDK 2 Microsoft Acrobat Elements Adobe Acrobat Elements 10 Adobe Acrobat Elements 11.0 Adobe Acrobat Elements 15.1 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 15.9 Adobe Acrobat Elements 6.0 Adobe Acrobat Elements 7.0 Adobe Application Name Acrobat Elements 8 Adobe Acrobat Elements 9 Adobe Acrobat Reader DC Adobe Acrobat.com 1 Adobe Alchemy OpenText Alchemy 9.0 OpenText Amazon Drive 4.0 Amazon Amazon WorkSpaces 1.1 Amazon Amazon WorkSpaces 2.1 Amazon Amazon WorkSpaces 2.2 Amazon Amazon WorkSpaces 2.3 Amazon Ansys Ansys Archive Server 10.1 OpenText AutoIt 2.6 AutoIt Team AutoIt 3.0 AutoIt Team AutoIt 3.2 AutoIt Team Azure Data Studio 1.9 Microsoft Azure Information Protection 1.0 Microsoft Captiva Cloud Toolkit 3.0 OpenText Capture Document Extraction OpenText CloneDVD 2 Elaborate Bytes Cognos Business Intelligence Cube Designer 10.2 IBM Cognos Business Intelligence Cube Designer 11.0 IBM Cognos Business Intelligence Cube Designer for Non-Production environment 10.2 IBM Commons Daemon 1.0 Apache Software Foundation Crystal Reports 11.0 SAP Data Explorer 8.6 Informatica DemoCreator 3.5 Wondershare Software Deployment Wizard 9.3 SAS Institute Deployment Wizard 9.4 SAS Institute Desktop Link 9.7 OpenText Desktop Viewer Unspecified OpenText Document Pipeline DocTools 10.5 OpenText Dropbox 1 Dropbox Dropbox 73.4 Dropbox Dropbox 74.4 Dropbox Dropbox 75.4 Dropbox Dropbox 76.4 Dropbox Dropbox 77.4 Dropbox Dropbox 78.4 Dropbox Dropbox 79.4 Dropbox Dropbox 81.4 -

Easy Slackware
1 Создание легкой системы на базе Slackware I - Введение Slackware пользуется заслуженной популярностью как классический linux дистрибутив, и поговорка "кто знает Red Hat тот знает только Red Hat, кто знает Slackware тот знает linux" несмотря на явный снобизм поклонников "бога Патре га" все же имеет под собой основания. Одним из преимуществ Slackware является возможность простого создания на ее основе практически любой системы, в том числе быстрой и легкой десктопной, о чем далее и пойдет речь. Есть дис трибутивы, клоны Slackware, созданные именно с этой целью, типа Аbsolute, но все же лучше создавать систему под себя, с максимальным учетом именно своих потребностей, и Slackware пожалуй как никакой другой дистрибутив подходит именно для этой цели. Легкость и быстрота системы определяется выбором WM (DM) , набором программ и оптимизацией программ и системы в целом. Первое исключает KDE, Gnome, даже новые версии XFCЕ, остается разве что LXDE, но набор программ в нем совершенно не устраивает. Оптимизация наиболее часто используемых про грамм и нескольких базовых системных пакетов осуществляется их сборкой из сорцов компилятором, оптимизированным именно под Ваш комп, причем каж дая программа конфигурируется исходя из Ваших потребностей к ее возможно стям. Оптимизация системы в целом осуществляется ее настройкой согласно спе цифическим требованиям к десктопу. Такой подход был выбран по банальной причине, возиться с gentoo нет ни какого желания, комп все таки создан для того чтобы им пользоваться, а не для компиляции программ, в тоже время у каждого есть минимальный набор из не большого количества наиболее часто используемых программ, на которые стоит потратить некоторое, не такое уж большое, время, чтобы довести их до ума. Кро ме того, такой подход позволяет иметь самые свежие версии наиболее часто ис пользуемых программ. -

18 Free Ways to Download Any Video Off the Internet Posted on October 2, 2007 by Aseem Kishore Ads by Google
http://www.makeuseof.com/tag/18-free-ways-to-download-any-video-off-the-internet/ 18 Free Ways To Download Any Video off the Internet posted on October 2, 2007 by Aseem Kishore Ads by Google Download Videos Now download.cnet.com Get RealPlayer® & Download Videos from the web. 100% Secure Download. Full Movies For Free www.YouTube.com/BoxOffice Watch Full Length Movies on YouTube Box Office. Absolutely Free! HD Video Players from US www.20north.com/ Coby, TV, WD live, TiVo and more. Shipped from US to India Video Downloading www.VideoScavenger.com 100s of Video Clips with 1 Toolbar. Download Video Scavenger Today! It seems like everyone these days is downloading, watching, and sharing videos from video-sharing sites like YouTube, Google Video, MetaCafe, DailyMotion, Veoh, Break, and a ton of other similar sites. Whether you want to watch the video on your iPod while working out, insert it into a PowerPoint presentation to add some spice, or simply download a video before it’s removed, it’s quite essential to know how to download, convert, and play these videos. There are basically two ways to download videos off the Internet and that’s how I’ll split up this post: either via a web app or via a desktop application. Personally, I like the web applications better simply because you don’t have to clutter up and slow down your computer with all kinds of software! UPDATE: MakeUseOf put together an excellent list of the best websites for watching movies, TV shows, documentaries and standups online. -

Comodo System Cleaner Version 3.0
Comodo System Cleaner Version 3.0 User Guide Version 3.0.122010 Versi Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Comodo System Cleaner - User Guide Table of Contents 1.Comodo System-Cleaner - Introduction ............................................................................................................ 3 1.1.System Requirements...........................................................................................................................................5 1.2.Installing Comodo System-Cleaner........................................................................................................................5 1.3.Starting Comodo System-Cleaner..........................................................................................................................9 1.4.The Main Interface...............................................................................................................................................9 1.5.The Summary Area.............................................................................................................................................11 1.6.Understanding Profiles.......................................................................................................................................12 2.Registry Cleaner............................................................................................................................................. 15 2.1.Clean.................................................................................................................................................................16 -

The Edonkey File-Sharing Network
The eDonkey File-Sharing Network Oliver Heckmann, Axel Bock, Andreas Mauthe, Ralf Steinmetz Multimedia Kommunikation (KOM) Technische Universitat¨ Darmstadt Merckstr. 25, 64293 Darmstadt (heckmann, bock, mauthe, steinmetz)@kom.tu-darmstadt.de Abstract: The eDonkey 2000 file-sharing network is one of the most successful peer- to-peer file-sharing applications, especially in Germany. The network itself is a hybrid peer-to-peer network with client applications running on the end-system that are con- nected to a distributed network of dedicated servers. In this paper we describe the eDonkey protocol and measurement results on network/transport layer and application layer that were made with the client software and with an open-source eDonkey server we extended for these measurements. 1 Motivation and Introduction Most of the traffic in the network of access and backbone Internet service providers (ISPs) is generated by peer-to-peer (P2P) file-sharing applications [San03]. These applications are typically bandwidth greedy and generate more long-lived TCP flows than the WWW traffic that was dominating the Internet traffic before the P2P applications. To understand the influence of these applications and the characteristics of the traffic they produce and their impact on network design, capacity expansion, traffic engineering and shaping, it is important to empirically analyse the dominant file-sharing applications. The eDonkey file-sharing protocol is one of these file-sharing protocols. It is imple- mented by the original eDonkey2000 client [eDonkey] and additionally by some open- source clients like mldonkey [mlDonkey] and eMule [eMule]. According to [San03] it is with 52% of the generated file-sharing traffic the most successful P2P file-sharing net- work in Germany, even more successful than the FastTrack protocol used by the P2P client KaZaa [KaZaa] that comes to 44% of the traffic. -

Further Reading and What's Next
APPENDIX Further Reading and What’s Next I hope you have gotten an idea of how, as a penetration tester, you could test a web application and find its security flaws by hunting bugs. In this concluding chapter, we will see how we can extend our knowledge of what we have learned so far. In the previous chapter, we saw how SQL injection has been done; however, we have not seen the automated part of SQL injection, which can be done by other tools alongside Burp Suite. We will use sqlmap, a very useful tool, for this purpose. Tools that Can Be Used Alongside Burp Suite We have seen earlier that the best alternative to Burp Suite is OWASP ZAP. Where Burp Community edition has some limitations, ZAP can help you overcome them. Moreover, ZAP is an open source free tool; it is community-based, so you don’t have to pay for it for using any kind of advanced technique. We have also seen how ZAP works. Here, we will therefore concentrate on sqlmap only, another very useful tool we need for bug hunting. The sqlmap is command line based. It comes with Kali Linux by default. You can just open your terminal and start scanning by using sqlmap. However, as always, be careful about using it against any live © Sanjib Sinha 2019 197 S. Sinha, Bug Bounty Hunting for Web Security, https://doi.org/10.1007/978-1-4842-5391-5 APPENDIX FuRtHeR Reading and What’s Next system; don’t use it without permission. If your client’s web application has vulnerabilities, you can use sqlmap to detect the database, table names, columns, and even read the contents inside. -

Forensics Evaluation of Privacy of Portable Web Browsers
International Journal of Computer Applications (0975 – 8887) Volume 147 – No. 8, August 2016 Forensics Evaluation of Privacy of Portable Web Browsers Ahmad Ghafarian Seyed Amin Hosseini Seno Department of Computer Science Department of Computer Engineering and Information Systems Faculty of Engineering University of North Georgia Ferdowsi University of Mashhad Dahlonega, GA 30005, USA Mashhad, Iran ABSTRACT relation to a computer forensic investigation is that the latter is Browsers claim private mode browsing saves no data on the a less tangible source of evidence [3]. host machine. Most popular web browsers also offer portable A study of tools and techniques for memory forensics can be versions of their browsers which can be launched from a found in [4]. The author has evaluated several command line removable device. When the removable device is removed, it and graphical user interface tools and provide the steps is claimed that traces of browsing activities will be deleted needed for memory forensics. Retrieving portable browsing and consequently private portable browsers offer better forensics artifacts left behind from main memory have privacy. This makes the task of computer forensics recently attracted some attention [5, 6]. The authors used investigators who try to reconstruct the past browsing history, limited memory forensics to retrieve forensics artifacts left in case of any computer incidence, more challenging. after a private portable browsing session. They argue that However, whether or not all data is deleted beyond forensic memory forensics is very promising in establishing a link recovery is a moot point. This research examines privacy of between the suspect and the retrieved data. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

UTEP Standard 20: Software Licensing 20.1 All Software Used On
UTEP Standard 20: Software Licensing 20.1 All software used on University devices will be used in accordance with the applicable software license. Unauthorized or unlicensed use of software is regarded as a serious violation subject to disciplinary action and any such use is without the consent of the University. (a) UTEP Information Security Policies: UTEP provides a sufficient number of cost-effective, licensed copies of core business software to enable faculty members, staff, and students to perform their work in an expedient and effective manner. (b) Systems administrators have the right to remove software from University devices for cause. For example, if a user in unable to show proof of license, or if the software is not required for University business purpose, or causes problems on the University- owned device. (c) All departments/colleges are responsible for the accurate accounting of software purchased by their respective department/ college and must ensure that the installation of the software complies with the license agreement of the software. For audit purposes, departments/colleges must maintain proof of purchase and/or original installation media for each software package. Third- party software in the possession of UTEP must not be copied unless such copying is consistent with relevant license agreements and prior management approval of such copying has been obtained, or copies are being made for contingency planning purposes. (d) All software purchases shall go through the UTEP Purchasing Department. (e) All commercial software used on computing systems must be supported by a software license agreement that specifically describes the usage rights and restrictions of the product and shall be purchased through the Purchasing Department. -

Conducting and Optimizing Eclipse Attacks in the Kad Peer-To-Peer Network
Conducting and Optimizing Eclipse Attacks in the Kad Peer-to-Peer Network Michael Kohnen, Mike Leske, and Erwin P. Rathgeb University of Duisburg-Essen, Institute for Experimental Mathematics, Ellernstr. 29, 45326 Essen [email protected], [email protected], [email protected] Abstract. The Kad network is a structured P2P network used for file sharing. Research has proved that Sybil and Eclipse attacks have been possible in it until recently. However, the past attacks are prohibited by newly implemented secu- rity measures in the client applications. We present a new attack concept which overcomes the countermeasures and prove its practicability. Furthermore, we analyze the efficiency of our concept and identify the minimally required re- sources. Keywords: P2P security, Sybil attack, Eclipse attack, Kad. 1 Introduction and Related Work P2P networks form an overlay on top of the internet infrastructure. Nodes in a P2P network interact directly with each other, i.e., no central entity is required (at least in case of structured P2P networks). P2P networks have become increasingly popular mainly because file sharing networks use P2P technology. Several studies have shown that P2P traffic is responsible for a large share of the total internet traffic [1, 2]. While file sharing probably accounts for the largest part of the P2P traffic share, also other P2P applications exist which are widely used, e.g., Skype [3] for VoIP or Joost [4] for IPTV. The P2P paradigm is becoming more and more accepted also for professional and commercial applications (e.g., Microsoft Groove [5]), and therefore, P2P technology is one of the key components of the next generation internet. -

Diapositiva 1
TRANSFERENCIA O DISTRIBUCIÓN DE ARCHIVOS ENTRE IGUALES (peer-to-peer) Características, Protocolos, Software, Luis Villalta Márquez Configuración Peer-to-peer Una red peer-to-peer, red de pares, red entre iguales, red entre pares o red punto a punto (P2P, por sus siglas en inglés) es una red de computadoras en la que todos o algunos aspectos funcionan sin clientes ni servidores fijos, sino una serie de nodos que se comportan como iguales entre sí. Es decir, actúan simultáneamente como clientes y servidores respecto a los demás nodos de la red. Las redes P2P permiten el intercambio directo de información, en cualquier formato, entre los ordenadores interconectados. Peer-to-peer Normalmente este tipo de redes se implementan como redes superpuestas construidas en la capa de aplicación de redes públicas como Internet. El hecho de que sirvan para compartir e intercambiar información de forma directa entre dos o más usuarios ha propiciado que parte de los usuarios lo utilicen para intercambiar archivos cuyo contenido está sujeto a las leyes de copyright, lo que ha generado una gran polémica entre defensores y detractores de estos sistemas. Las redes peer-to-peer aprovechan, administran y optimizan el uso del ancho de banda de los demás usuarios de la red por medio de la conectividad entre los mismos, y obtienen así más rendimiento en las conexiones y transferencias que con algunos métodos centralizados convencionales, donde una cantidad relativamente pequeña de servidores provee el total del ancho de banda y recursos compartidos para un servicio o aplicación. Peer-to-peer Dichas redes son útiles para diversos propósitos. -

Clubedu Clubdigitalhome Clubdev Strahlung
Nr. 165/Juni 2020 € 5,00 ISSN 1022-1611 · Politik digital aktiv mitgestalten Politik digital aktiv mitgestalten CLUBEDU Wien Teleteaching mit Windows CLUBDIGITALHOME XnView U-2623 CLUBDEV Visual Studio Code Spaces STRAHLUNG Strahlung Schwingkreise Fehleinschätzungen P.b.b. 16Z040679 M ClubComputer, Siccardsburggasse 4/1/22 1100 1100 4/1/22 Siccardsburggasse ClubComputer, M 16Z040679 P.b.b. Inhalt Liebe Leserinnen und Leser! Franz Fiala LIESMICH Dass diese Ausgabe mit etwas Verspätung hergestellt wurde, liegt an diesem winzigen 1 Cover Etwas, das sich zwischen die Menschen geschoben hat und das nicht nur Veranstal- Franz Fiala Fußball und Kunst, tungen verunmöglicht hat, sondern auch den Grenzübertritt zur Slowakei, wo sich die am meisten be- Druckerei der PCNEWS befindet. Dass diese Pandemie auch einen Zusammenhang zu troffen vom Corona- unserem Jahresregenten, dem Thema „Strahlung“, hat, darauf wären wir wohl auch Virus—oder von mit viel Phantasie nicht gekommen. Unwissen macht vieles möglich. docj eher von 5G? Bild: „Strahlung“ ist größtenteils unsichtbar—so wie ein Virus—und die Beschäftigung mit Simpl am 2.1.20202 diesem Thema sollte unser Wissen vertiefen und uns gegen die um sich greifende Wis- senschaftsfeindlichkeit mit abgesichertem Wissen immunisieren. 2 Liebe Leser, Inhalt Es liegt in der Natur der Sache, dass „lehren“ und „belehren“ verwandte Begriffe und Franz Fiala die Vermittlung komplexerer Zusammenhänge von bildungsfernen Schichten eher als 3 Impressum, Autoren, Inserenten, Zweiteres empfunden und daher auch abgelehnt wird und sie gleichzeitig eine verein- Services, Web 2020 fachte Gegenwelt der Verschwörungstheorien und alternativen Fakten errichten. IGITAL OCIETY Typisch für Wissenschaftsgegner ist das Postulieren nicht vorhandener Zusammen- D S hänge, eine „Dummheit zweiter Art“, die meist die „Dummheit der ersten Art“, näm- 4 Politik digital aktiv mitgestalten lich das Nicht-Verstehen von Zusammenhängen voraussetzt.