A Packet-Level Simulation and Emulation Platform for Bittorrent Journal of Applied Research and Technology, Vol
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lab 5: Bittorrent Client Implementation
Lab 5: BitTorrent Client Implementation Due: Nov. 30th at 11:59 PM Milestone: Nov. 19th during Lab Overview In this lab, you and your lab parterner will develop a basic BitTorrent client that can, at minimal, exchange a file between multiple peers, and at best, function as a full feature BitTorrent Client. The programming in this assignment will be in C requiring standard sockets, and thus you will not need to have root access. You should be able to develop your code on any CS lab machine or your personal machine, but all code will be tested on the CS lab. Deliverable Your submission should minimally include the following programs and files: • REDME • Makefile • bencode.c|h • bt lib.c|h • bt setup.c|h • bt client • client trace.[n].log • sample torrent.torrent Your README file should contain a short header containing your name, username, and the assignment title. The README should additionally contain a short description of your code, tasks accomplished, and how to compile, execute, and interpret the output of your programs. Your README should also contain a list of all submitted files and code and the functionality implemented in different code files. This is a large assignment, and this will greatly aid in grading. As always, if there are any short answer questions in this lab write-up, you should provide well marked answers in the README, as well as indicate that you’ve completed any of the extra credit (so that I don’t forget to grade it). Milestones The entire assignment will be submitted and graded, but your group will also hold a milestone meeting to receive feedback on your current implementation. -

A Decentralized Cloud Storage Network Framework
Storj: A Decentralized Cloud Storage Network Framework Storj Labs, Inc. October 30, 2018 v3.0 https://github.com/storj/whitepaper 2 Copyright © 2018 Storj Labs, Inc. and Subsidiaries This work is licensed under a Creative Commons Attribution-ShareAlike 3.0 license (CC BY-SA 3.0). All product names, logos, and brands used or cited in this document are property of their respective own- ers. All company, product, and service names used herein are for identification purposes only. Use of these names, logos, and brands does not imply endorsement. Contents 0.1 Abstract 6 0.2 Contributors 6 1 Introduction ...................................................7 2 Storj design constraints .......................................9 2.1 Security and privacy 9 2.2 Decentralization 9 2.3 Marketplace and economics 10 2.4 Amazon S3 compatibility 12 2.5 Durability, device failure, and churn 12 2.6 Latency 13 2.7 Bandwidth 14 2.8 Object size 15 2.9 Byzantine fault tolerance 15 2.10 Coordination avoidance 16 3 Framework ................................................... 18 3.1 Framework overview 18 3.2 Storage nodes 19 3.3 Peer-to-peer communication and discovery 19 3.4 Redundancy 19 3.5 Metadata 23 3.6 Encryption 24 3.7 Audits and reputation 25 3.8 Data repair 25 3.9 Payments 26 4 4 Concrete implementation .................................... 27 4.1 Definitions 27 4.2 Peer classes 30 4.3 Storage node 31 4.4 Node identity 32 4.5 Peer-to-peer communication 33 4.6 Node discovery 33 4.7 Redundancy 35 4.8 Structured file storage 36 4.9 Metadata 39 4.10 Satellite 41 4.11 Encryption 42 4.12 Authorization 43 4.13 Audits 44 4.14 Data repair 45 4.15 Storage node reputation 47 4.16 Payments 49 4.17 Bandwidth allocation 50 4.18 Satellite reputation 53 4.19 Garbage collection 53 4.20 Uplink 54 4.21 Quality control and branding 55 5 Walkthroughs ............................................... -

Sok: Tools for Game Theoretic Models of Security for Cryptocurrencies
SoK: Tools for Game Theoretic Models of Security for Cryptocurrencies Sarah Azouvi Alexander Hicks Protocol Labs University College London University College London Abstract form of mining rewards, suggesting that they could be prop- erly aligned and avoid traditional failures. Unfortunately, Cryptocurrencies have garnered much attention in recent many attacks related to incentives have nonetheless been years, both from the academic community and industry. One found for many cryptocurrencies [45, 46, 103], due to the interesting aspect of cryptocurrencies is their explicit consid- use of lacking models. While many papers aim to consider eration of incentives at the protocol level, which has motivated both standard security and game theoretic guarantees, the vast a large body of work, yet many open problems still exist and majority end up considering them separately despite their current systems rarely deal with incentive related problems relation in practice. well. This issue arises due to the gap between Cryptography Here, we consider the ways in which models in Cryptog- and Distributed Systems security, which deals with traditional raphy and Distributed Systems (DS) can explicitly consider security problems that ignore the explicit consideration of in- game theoretic properties and incorporated into a system, centives, and Game Theory, which deals best with situations looking at requirements based on existing cryptocurrencies. involving incentives. With this work, we offer a systemati- zation of the work that relates to this problem, considering papers that blend Game Theory with Cryptography or Dis- Methodology tributed systems. This gives an overview of the available tools, and we look at their (potential) use in practice, in the context As we are covering a topic that incorporates many different of existing blockchain based systems that have been proposed fields coming up with an extensive list of papers would have or implemented. -

Blockchain and The
NOTES ACKNOWLEDGMENTS INDEX Notes Introduction 1. The manifesto dates back to 1988. See Timothy May, “The Crypto Anarchist Manifesto” (1992), https:// www . activism . net / cypherpunk / crypto - anarchy . html. 2. Ibid. 3. Ibid. 4. Ibid. 5. Ibid. 6. Timothy May, “Crypto Anarchy and Virtual Communities” (1994), http:// groups . csail . mit . edu / mac / classes / 6 . 805 / articles / crypto / cypherpunks / may - virtual - comm . html. 7. Ibid. 8. For example, as we wi ll describe in more detail in Chapter 1, the Bitcoin blockchain is currently stored on over 6,000 computers in eighty- nine jurisdictions. See “Global Bitcoin Node Distribution,” Bitnodes, 21 . co, https:// bitnodes . 21 . co / . Another large blockchain- based network, Ethereum, has over 12,000 nodes, also scattered across the globe. See Ethernodes, https:// www . ethernodes . org / network / 1. 9. See note 8. 10. Some blockchains are not publicly accessible (for more on this, see Chapter 1). These blockchains are referred to as “private blockchains” and are not the focus of this book. 11. See Chapter 1. 12. The Eu ro pean Securities and Market Authority, “Discussion Paper: The Dis- tributed Ledger Technology Applied to Securities Markets,” ESMA / 2016 / 773, June 2, 2016: at 17, https:// www . esma . europa . eu / sites / default / files / library / 2016 - 773 _ dp _ dlt . pdf. 213 214 NOTES TO PAGES 5–13 13. The phenomena of order without law also has been described in other con- texts, most notably by Robert Ellickson in his seminal work Order without Law (Cambridge, MA: Harvard University Press, 1994). 14. Joel Reidenberg has used the term “lex informatica” to describe rules imple- mented by centralized operators online. -

Proofs of Replication Are Also Relevant in the Private-Verifier Setting of Proofs of Data Replication
PoReps: Proofs of Space on Useful Data Ben Fisch Stanford University, Protocol Labs Abstract A proof-of-replication (PoRep) is an interactive proof system in which a prover defends a publicly verifiable claim that it is dedicating unique resources to storing one or more retrievable replicas of a data file. In this sense a PoRep is both a proof of space (PoS) and a proof of retrievability (PoR). This paper establishes a foundation for PoReps, exploring both their capabilities and their limitations. While PoReps may unconditionally demonstrate possession of data, they fundamentally cannot guarantee that the data is stored redundantly. Furthermore, as PoReps are proofs of space, they must rely either on rational time/space tradeoffs or timing bounds on the online prover's runtime. We introduce a rational security notion for PoReps called -rational replication based on the notion of an -Nash equilibrium, which captures the property that a server does not gain any significant advantage by storing its data in any other (non-redundant) format. We apply our definitions to formally analyze two recently proposed PoRep constructions based on verifiable delay functions and depth robust graphs. Lastly, we reflect on a notable application of PoReps|its unique suitability as a Nakamoto consensus mechanism that replaces proof-of-work with PoReps on real data, simultaneously incentivizing and subsidizing the cost of file storage. 1 Introduction A proof-of-replication (PoRep) builds on the two prior concepts of proofs-of-retrievability (PoR) [30] and proofs-of-space (PoS) [24]. In the former a prover demonstrates that it can retrieve a file and in the latter the prover demonstrates that it is using some minimum amount of space to store information. -
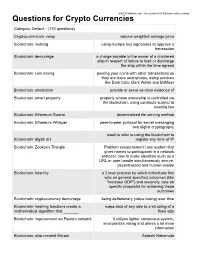
Questions for Crypto Currencies
www.YoYoBrain.com - Accelerators for Memory and Learning Questions for Crypto Currencies Category: Default - (170 questions) Cryptocurrencies: vwap volume weighted average price Blockchain: multisig using multiple key signatures to approve a transaction Blockchain: demurrage a charge payable to the owner of a chartered ship in respect of failure to load or discharge the ship within the time agreed Blockchain: coin mixing pooling your coins with other transactions so they are more anonymous, using services like Dark Coin, Dark Wallet and BitMixer Blockchain: attestation provide or serve as clear evidence of Blockchain: smart property property whose ownership is controlled via the blockchain, using contracts subject to existing law Blockchain: Ethereum Swarm decentralized file serving method Blockchain: Ethereum Whisper peer-to-peer protocol for secret messaging and digital cryptography used to refer to using the blockchain to Blockchain: digital art register any form of IP Blockchain: Zookos's Triangle Problem encountered in any system that gives names to participants in a network protocol: how to make identities such as a URL or user handle simultaneously secure, decentralized and human-usable Blockchain: futarchy a 2 level process by which individuals first vote on general specified outcomes (like "increase GDP") and secondly, vote on specific proposals for achieving those outcomes Blockchain: cryptocurrency demurrage being deflationary (value losing) over time Blockchain: hashing functions create a maps data of any size to a bit string -

HODL Deck V4
BUILDING THE WORLD’S LEADING PRIVACY INVESTMENT VEHICLE Presentation Subtitle 2020 Cypherpunk Holdings Inc. CSE: HODL INVESTOR PRESENTATION January 2021 1 Investor Presentation January 2021 DISCLAIMER - CAUTIONARY NOTE REGARDING FORWARD-LOOKING INFORMATION This presentation contains “forward-looking information” within the meaning of applicable securities laws. Generally, any statements that are not historical facts may contain forward-looking information, and forward-looking information can be identified by the use of forward-looking terminology such as “plans”, “expects” or “does not expect”, “is expected”, “budget”, “scheduled”, “estimates”, “forecasts”, “intends”, “anticipates” or “does not anticipate”, or “believes”, or variations of such words and phrases or indicates that certain actions, events or results “may”, “could”, “would”, “might” or “will be” taken, “occur” or “be achieved”. Forward-looking information includes, but is not limited to the Company’s goal of making investments in, crypto-currencies, digital currencies and assets, the blockchain, software and other sectors, financial information and enhancing value. There is no assurance that the Company’s plans or objectives will be implemented as set out herein, or at all. Forward-looking information is based on certain factors and assumptions the Company believes to be reasonable at the time such statements are made and is subject to known and unknown risks, uncertainties and other factors that may cause the actual results, level of activity, performance or achievements of the Company to be materially different from those expressed or implied by such forward-looking information. There can be no assurance that such forward-looking information will prove to be accurate, as actual results and future events could differ materially from those anticipated in such information. -

Serializability and Heterogeneous Trust from Two Phase Commit to Blockchains
SERIALIZABILITY AND HETEROGENEOUS TRUST FROM TWO PHASE COMMIT TO BLOCKCHAINS A Dissertation Presented to the Faculty of the Graduate School of Cornell University in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy by Isaac Cameron Sheff August 2019 © 2019 Isaac Cameron Sheff ALL RIGHTS RESERVED SERIALIZABILITY AND HETEROGENEOUS TRUST FROM TWO PHASE COMMIT TO BLOCKCHAINS Isaac Cameron Sheff, Ph.D. Cornell University 2019 As distributed systems become more federated and cross-domain, we are forced to rethink some of our core abstractions. We need heterogeneous systems with rig- orous consistency and self-authentication guarantees, despite a complex landscape of security and failure tolerance assumptions. I have designed, built, and evalu- ated heterogeneous distributed algorithms with broad applications from medical privacy to blockchains. This dissertation examines three novel building blocks for this vision. First, I show that serializable transactions cannot always be securely scheduled when data has different levels of confidentiality. I have identified a useful subset of transactions that can always be securely scheduled, and built a system to check and execute them. Second, I present Charlotte, a heterogeneous system that supports compos- able Authenticated Distributed Data Structures (like Git, PKIs, or Bitcoin). I show that Charlotte produces significant performance improvements compared to a single, universally trusted blockchain. Finally, I develop a rigorous generalization of the consensus problem, and present the first distributed consensus which tolerates heterogeneous failures, het- erogeneous participants, and heterogeneous observers. With this consensus, cross- domain systems can maintain ADDSs, or schedule transactions, without the ex- pensive overhead that comes from tolerating the sum of everyone's fears. -

Decentralization and Disintermediation in Blockchain-Based Marketplaces De Vos, M.A
Delft University of Technology Decentralization and Disintermediation in Blockchain-based Marketplaces de Vos, M.A. DOI 10.4233/uuid:a4f750b6-5ac5-4709-80c5-71eb71ac7b35 Publication date 2021 Document Version Final published version Citation (APA) de Vos, M. A. (2021). Decentralization and Disintermediation in Blockchain-based Marketplaces. https://doi.org/10.4233/uuid:a4f750b6-5ac5-4709-80c5-71eb71ac7b35 Important note To cite this publication, please use the final published version (if applicable). Please check the document version above. Copyright Other than for strictly personal use, it is not permitted to download, forward or distribute the text or part of it, without the consent of the author(s) and/or copyright holder(s), unless the work is under an open content license such as Creative Commons. Takedown policy Please contact us and provide details if you believe this document breaches copyrights. We will remove access to the work immediately and investigate your claim. This work is downloaded from Delft University of Technology. For technical reasons the number of authors shown on this cover page is limited to a maximum of 10. Decentralization and Disintermediation in Blockchain-based Marketplaces Decentralization and Disintermediation in Blockchain-based Marketplaces Proefschrift ter verkrijging van de graad van doctor aan de Technische Universiteit Delft, op gezag van de Rector Magnificus prof. dr. ir. T.H.J.J. van der Hagen, voorzitter van het College voor Promoties, in het openbaar te verdedigen op woensdag 16 juni 2021 om 17:30 uur door Marinus Abraham DE VOS Master of Science in Computer Science, Technische Universiteit Delft, Nederland, geboren te Sint-Maartensdijk, Nederland. -

Blockchain Consensus Algorithms: a Survey
1 Blockchain Consensus Algorithms: A Survey Md Sadek Ferdous, Member, IEEE, Mohammad Jabed Morshed Chowdhury, Mohammad A. Hoque, Member, IEEE, and Alan Colman F Abstract—In recent years, blockchain technology has received unpar- of Bitcoin [1] that was introduced in 2008. While crypto- alleled attention from academia, industry, and governments all around currencies have emerged as the principal and the most pop- the world. It is considered a technological breakthrough anticipated to ular application of blockchain technology, many enthusiasts disrupt several application domains touching all spheres of our lives. from different disciplines have identified and proposed a The sky-rocket anticipation of its potential has caused a wide-scale plethora of applications of blockchain in a multitude of exploration of its usage in different application domains. This has resul- ted in a plethora of blockchain systems for various purposes. However, application domains [2], [3]. The possibility of exploiting many of these blockchain systems suffer from serious shortcomings blockchain in so many areas has created huge anticipation related to their performance and security, which need to be addressed surrounding blockchain systems. Indeed, it is regarded as before any wide-scale adoption can be achieved. A crucial component one of the fundamental technologies to revolutionise the of any blockchain system is its underlying consensus algorithm, which landscapes of the identified application domains. in many ways, determines its performance and security. Therefore, to A blockchain system is, fundamentally, a distributed address the limitations of different blockchain systems, several existing system that relies on a consensus algorithm that ensures as well novel consensus algorithms have been introduced. -

Proof Systems for Sustainable Decentralized Cryptocurrencies By
Proof Systems for Sustainable Decentralized Cryptocurrencies by Hamza Abusalah A thesis presented to the Graduate School of the Institute of Science and Technology Austria in partial fulfillment of the requirements for the degree of Doctor of Philosophy. Klosterneuburg, Austria. September, 2018. i Abstract A proof system is a protocol between a prover and a verifier over a common input in which an honest prover convinces the verifier of the validity of true statements. Motivated by the success of decentralized cryptocurrencies, exemplified by Bitcoin, the focus of this thesis will be on proof systems which found applications in some sustainable alternatives to Bitcoin, such as the Spacemint and Chia cryptocurrencies. In particular, we focus on proofs of space and proofs of sequential work. Proofs of space (PoSpace) were suggested as more ecological, economical, and egali- tarian alternative to the energy-wasteful proof-of-work mining of Bitcoin. However, the state-of-the-art constructions of PoSpace are based on sophisticated graph pebbling lower bounds, and are therefore complex. Moreover, when these PoSpace are used in cryptocur- rencies like Spacemint, miners can only start mining after ensuring that a commitment to their space is already added in a special transaction to the blockchain. Proofs of sequential work (PoSW) are proof systems in which a prover, upon receiving a statement χ and a time parameter T , computes a proof which convinces the verifier that T time units had passed since χ was received. Whereas Spacemint assumes synchrony to retain some interesting Bitcoin dynamics, Chia requires PoSW with unique proofs, i.e., PoSW in which it is hard to come up with more than one accepting proof for any true statement. -

Cypherpunk Holdings Provides Corporate Update on Equity
Cypherpunk Holdings Provides Corporate Update Update on Equity Holdings and IP Leasing Arrangement TORONTO, ONTARIO, May 28, 2021. ‐ Cypherpunk Holdings Inc. (CSE: HODL, OTC: KHRIF) (the “Company” or “Cypherpunk”), a sector leader for privacy-focused investments, is pleased to provide the following corporate update. Equity stake in Chia Network The Company has been an investor in Chia Network Inc. (“Chia Network”) since July 2018, through its investment of USD $300,000 via a simple agreement for future equity (SAFE). Under the terms of the SAFE, on May 10, 2021, the Company received 19,860 shares of Series B Stock of Chia. Chia Network develops an energy-efficient decentralized blockchain, created by Bram Cohen, the inventor of BitTorrent. In May 2021, Chia Network announced the launch of its digital currency “Chia”. Commenting on this latest update Antanas Guoga, CEO of the Company stated: “We are happy with our decision to invest in Chia Network. The environmental impact caused by cryptocurrencies has been at the forefront of many discussions in the industry and we believe that this is an issue that needs addressing. Chia Network uses spare storage space on hard drives to verify blockchain transactions instead of using the energy-intensive “proof of work” model employed by other cryptocurrencies, which makes Chia an exciting “green” alternative to other digital currencies. We are pleased that Chia Network continues to advance and develop its business.” IPv4 Leasing Arrangement Following the Company’s purchase of 16,384 IPv4 addresses in March 2021, the Company has secured a leasing arrangement. The leasing arrangement is currently generating 14.8% yield per annum on the original investment.