Decentralization and Disintermediation in Blockchain-Based Marketplaces De Vos, M.A
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lab 5: Bittorrent Client Implementation
Lab 5: BitTorrent Client Implementation Due: Nov. 30th at 11:59 PM Milestone: Nov. 19th during Lab Overview In this lab, you and your lab parterner will develop a basic BitTorrent client that can, at minimal, exchange a file between multiple peers, and at best, function as a full feature BitTorrent Client. The programming in this assignment will be in C requiring standard sockets, and thus you will not need to have root access. You should be able to develop your code on any CS lab machine or your personal machine, but all code will be tested on the CS lab. Deliverable Your submission should minimally include the following programs and files: • REDME • Makefile • bencode.c|h • bt lib.c|h • bt setup.c|h • bt client • client trace.[n].log • sample torrent.torrent Your README file should contain a short header containing your name, username, and the assignment title. The README should additionally contain a short description of your code, tasks accomplished, and how to compile, execute, and interpret the output of your programs. Your README should also contain a list of all submitted files and code and the functionality implemented in different code files. This is a large assignment, and this will greatly aid in grading. As always, if there are any short answer questions in this lab write-up, you should provide well marked answers in the README, as well as indicate that you’ve completed any of the extra credit (so that I don’t forget to grade it). Milestones The entire assignment will be submitted and graded, but your group will also hold a milestone meeting to receive feedback on your current implementation. -

A Decentralized Cloud Storage Network Framework
Storj: A Decentralized Cloud Storage Network Framework Storj Labs, Inc. October 30, 2018 v3.0 https://github.com/storj/whitepaper 2 Copyright © 2018 Storj Labs, Inc. and Subsidiaries This work is licensed under a Creative Commons Attribution-ShareAlike 3.0 license (CC BY-SA 3.0). All product names, logos, and brands used or cited in this document are property of their respective own- ers. All company, product, and service names used herein are for identification purposes only. Use of these names, logos, and brands does not imply endorsement. Contents 0.1 Abstract 6 0.2 Contributors 6 1 Introduction ...................................................7 2 Storj design constraints .......................................9 2.1 Security and privacy 9 2.2 Decentralization 9 2.3 Marketplace and economics 10 2.4 Amazon S3 compatibility 12 2.5 Durability, device failure, and churn 12 2.6 Latency 13 2.7 Bandwidth 14 2.8 Object size 15 2.9 Byzantine fault tolerance 15 2.10 Coordination avoidance 16 3 Framework ................................................... 18 3.1 Framework overview 18 3.2 Storage nodes 19 3.3 Peer-to-peer communication and discovery 19 3.4 Redundancy 19 3.5 Metadata 23 3.6 Encryption 24 3.7 Audits and reputation 25 3.8 Data repair 25 3.9 Payments 26 4 4 Concrete implementation .................................... 27 4.1 Definitions 27 4.2 Peer classes 30 4.3 Storage node 31 4.4 Node identity 32 4.5 Peer-to-peer communication 33 4.6 Node discovery 33 4.7 Redundancy 35 4.8 Structured file storage 36 4.9 Metadata 39 4.10 Satellite 41 4.11 Encryption 42 4.12 Authorization 43 4.13 Audits 44 4.14 Data repair 45 4.15 Storage node reputation 47 4.16 Payments 49 4.17 Bandwidth allocation 50 4.18 Satellite reputation 53 4.19 Garbage collection 53 4.20 Uplink 54 4.21 Quality control and branding 55 5 Walkthroughs ............................................... -

Retail 2.0: the Future of Shopping
RETAIL 2.0 This Report • The pandemic has seen a high-street downturn, as consumers move to e-commerce platforms. But whilst the high street may be down, it is most definitely not out • The post-COVID world provides retailers with the opportunity to renew and reinvent • OMG Futures sees a retail future where innovation is not just about wizardry and gadgetry – but also enhancing our experiences and serving our deeper needs • The Future of Shopping envisions a future where embracing and integrating with digital technologies whilst providing a unique human experience in-store can lead to a high street renaissance • This is not a report about e-commerce specifically. This is a report about the shopper of the future and what they will demand from their retail – in all its forms How it unfolds THE THE THE NOW WOW HOW The current state of The next decade in Implications for retail in 2020 retail businesses and brands WHERE WE ARE RIGHT NOW… UK Retail, December 2019 Slowest rate of 85,000 job 9169 store 350 CEO Online sales spending growth losses in retail closures replacements grew by 21% since 2010 Retail was already changing Source: Deloitte: Retail Trends 2020: Finding Purpose Through Challenge, Jan 2019 – Dec 2019 Then, the pandemic arrived… UK Retail, December 2020 Pre-pandemic online Amazon sales up 63% of consumers 36% of online shoppers sales: 20% of 40%. Announced said the way they increased frequency of In Sept, as a 12 month retail Now:30% of 7,000 more permanent obtain goods and online purchase during average, footfall for retail. -

New Strategies for the Platform Economy
SPECIAL COLLECTION STRATEGY New Strategies for the Platform Economy To reap the rewards and avoid the risks, companies exploring a platform business model must look carefully at their partnerships and growth strategy. Brought to you by: SPRING 2021 NEW STRATEGIES FOR THE PLATFORM ECONOMY SPECIAL REPORT 1 9 17 Competing on How Healthy Is Your Platform Scaling, Platforms Business Ecosystem? Fast and Slow THE DOMINANT DIGITAL PLATFORMS are now among the world’s most phases. At each stage, there are specific early valuable — and most powerful — companies, leaving a huge swath of organizations forced indicators to look for that point to potential to play by their rules. In this new competitive environment, businesses need new ways to failure. Tracking the appropriate metrics gain advantage despite platforms’ constraints and market clout. And businesses seeking to for each stage and being alert to red flags create successful platform ecosystems find that while the rewards can be great, the helps businesses pivot to a new approach or likelihood of failure is high. This special report examines the challenges faced by both limit their losses. platform owners and participants. Platforms aiming for market dominance have typically prioritized rapid growth. The asymmetries in power and infor- attention from U.S. and European regulators, However, Max Büge and Pinar Ozcan have mation between platform owners and the whose scrutiny of dominant platforms’ found that scaling quickly is not the right businesses reliant on them have implications practices may lead to shifts in the prevailing strategy in all circumstances: Pursuing fast for the traditional levers of competitive balance of power. -

The Dealership of Tomorrow 2.0: America’S Car Dealers Prepare for Change
The Dealership of Tomorrow 2.0: America’s Car Dealers Prepare for Change February 2020 An independent study by Glenn Mercer Prepared for the National Automobile Dealers Association The Dealership of Tomorrow 2.0 America’s Car Dealers Prepare for Change by Glenn Mercer Introduction This report is a sequel to the original Dealership of Tomorrow: 2025 (DOT) report, issued by NADA in January 2017. The original report was commissioned by NADA in order to provide its dealer members (the franchised new-car dealers of America) perspectives on the changing automotive retailing environment. The 2017 report was intended to offer “thought starters” to assist dealers in engaging in strategic planning, looking ahead to roughly 2025.1 In early 2019 NADA determined it was time to update the report, as the environment was continuing to shift. The present document is that update: It represents the findings of new work conducted between May and December of 2019. As about two and a half years have passed since the original DOT, focused on 2025, was issued, this update looks somewhat further out, to the late 2020s. Disclaimers As before, we need to make a few things clear at the outset: 1. In every case we have tried to link our forecast to specific implications for dealers. There is much to be said about the impact of things like electric vehicles and connected cars on society, congestion, the economy, etc. But these impacts lie far beyond the scope of this report, which in its focus on dealerships is already significant in size. Readers are encouraged to turn to academic, consulting, governmental and NGO reports for discussion of these broader issues. -

Disruptive Business Models – Challenges and Opportunities for Tax Administrations 3 C O N T E N T
DISRUPTIVE BUSINESS MODELS CHALLENGES AND OPPORTUNITIES FOR TAX ADMINISTRATIONS WWW.IOTA-TAX.ORG Published by IOTA, 2017, Budapest Editorial Board: Miguel Silva Pinto, Neil Sawyer, Ágnes Kővágó Address: Wesselényi utca 16., H-1077, Budapest, Hungary Phone: +36 (1) 478-30-30, Email: [email protected] ISBN 978-615-00-0275-0 WWW.IOTA-TAX.ORG FOREWORD Dear Readers, This publication is founded on the presentations and debates held during the technical session of the 21st IOTA General Assembly, which took place in Kyiv, on 28-30 June 2017. The working programme addressed the changes in the economy driven by technology and multiplication of new and innovative business models. The assembly focused on how this trend is causing both challenges and opportunities for tax administrations to re-invent themselves in order to keep pace with the present and anticipate the future. The book’s structure follows the technical sessions of the assembly and the articles have been prepared by many of the speakers and include not only what they have presented but their further thoughts on the subject as well. Pekka Ruuhonen, Giorgi Tabuashvili and Gerry Harrahill, Commissioners from the Finnish, Georgian and Irish Tax Administrations provide their insights on the strategies their organisations are following to ensure the supply of better services to their taxpayers and to tackle the challenges of digital business models. Chiara Putzolu, Dirk Dierickx and Alan Carter, from the Italian, Belgian and UK’s administrations offer an insight into their country’s compliance models and methodologies to address sharing/collaborative businesses.JB Hillman from Vertex explains the potential of disruptive technologies to improve the effectiveness of tax administrations. -

1 Disintermediation in Business-To-Business Service Channels: Mechanisms and Challenges
Disintermediation in Business-to-Business Service Channels: Mechanisms and Challenges Fredrik Nordin, Danilo Brozovic and Maria Holmlund Accepted for publication in Journal of Business-to-Business Marketing Abstract Purpose: The aim of this paper is to delineate a number of different disintermediation mechanisms within the context of business-to-business service channels and to identify the specific challenges associated with adopting these mechanisms. Methodology: The research was conducted in accordance with abductive reasoning, moving continuously between the empirical world of four industrial (B2B) firms and the model world. Findings: This paper delineates a choice of six disintermediation mechanisms and their attendant challenges within the context of industrial service channels. Contribution: The paper provides an original conceptualization of disintermediation, which is detached from the traditional understanding of the concept. As such, it constitutes a useful starting point for the development of a formal theory of disintermediation. Implications for practice: This paper should be useful for practitioners, because it presents various disintermediation options available to industrial firms faced by undesired intermediaries in their industrial service channels. Keywords: service, disintermediation, industrial marketing, intermediaries, servitization 1 Disintermediation in Business-to-Business Service Channels: Mechanisms and Challenges 1. Introduction “Can you help us analyze how to handle the intermediaries and service companies -

Sok: Tools for Game Theoretic Models of Security for Cryptocurrencies
SoK: Tools for Game Theoretic Models of Security for Cryptocurrencies Sarah Azouvi Alexander Hicks Protocol Labs University College London University College London Abstract form of mining rewards, suggesting that they could be prop- erly aligned and avoid traditional failures. Unfortunately, Cryptocurrencies have garnered much attention in recent many attacks related to incentives have nonetheless been years, both from the academic community and industry. One found for many cryptocurrencies [45, 46, 103], due to the interesting aspect of cryptocurrencies is their explicit consid- use of lacking models. While many papers aim to consider eration of incentives at the protocol level, which has motivated both standard security and game theoretic guarantees, the vast a large body of work, yet many open problems still exist and majority end up considering them separately despite their current systems rarely deal with incentive related problems relation in practice. well. This issue arises due to the gap between Cryptography Here, we consider the ways in which models in Cryptog- and Distributed Systems security, which deals with traditional raphy and Distributed Systems (DS) can explicitly consider security problems that ignore the explicit consideration of in- game theoretic properties and incorporated into a system, centives, and Game Theory, which deals best with situations looking at requirements based on existing cryptocurrencies. involving incentives. With this work, we offer a systemati- zation of the work that relates to this problem, considering papers that blend Game Theory with Cryptography or Dis- Methodology tributed systems. This gives an overview of the available tools, and we look at their (potential) use in practice, in the context As we are covering a topic that incorporates many different of existing blockchain based systems that have been proposed fields coming up with an extensive list of papers would have or implemented. -

Blockchain and The
NOTES ACKNOWLEDGMENTS INDEX Notes Introduction 1. The manifesto dates back to 1988. See Timothy May, “The Crypto Anarchist Manifesto” (1992), https:// www . activism . net / cypherpunk / crypto - anarchy . html. 2. Ibid. 3. Ibid. 4. Ibid. 5. Ibid. 6. Timothy May, “Crypto Anarchy and Virtual Communities” (1994), http:// groups . csail . mit . edu / mac / classes / 6 . 805 / articles / crypto / cypherpunks / may - virtual - comm . html. 7. Ibid. 8. For example, as we wi ll describe in more detail in Chapter 1, the Bitcoin blockchain is currently stored on over 6,000 computers in eighty- nine jurisdictions. See “Global Bitcoin Node Distribution,” Bitnodes, 21 . co, https:// bitnodes . 21 . co / . Another large blockchain- based network, Ethereum, has over 12,000 nodes, also scattered across the globe. See Ethernodes, https:// www . ethernodes . org / network / 1. 9. See note 8. 10. Some blockchains are not publicly accessible (for more on this, see Chapter 1). These blockchains are referred to as “private blockchains” and are not the focus of this book. 11. See Chapter 1. 12. The Eu ro pean Securities and Market Authority, “Discussion Paper: The Dis- tributed Ledger Technology Applied to Securities Markets,” ESMA / 2016 / 773, June 2, 2016: at 17, https:// www . esma . europa . eu / sites / default / files / library / 2016 - 773 _ dp _ dlt . pdf. 213 214 NOTES TO PAGES 5–13 13. The phenomena of order without law also has been described in other con- texts, most notably by Robert Ellickson in his seminal work Order without Law (Cambridge, MA: Harvard University Press, 1994). 14. Joel Reidenberg has used the term “lex informatica” to describe rules imple- mented by centralized operators online. -

Proofs of Replication Are Also Relevant in the Private-Verifier Setting of Proofs of Data Replication
PoReps: Proofs of Space on Useful Data Ben Fisch Stanford University, Protocol Labs Abstract A proof-of-replication (PoRep) is an interactive proof system in which a prover defends a publicly verifiable claim that it is dedicating unique resources to storing one or more retrievable replicas of a data file. In this sense a PoRep is both a proof of space (PoS) and a proof of retrievability (PoR). This paper establishes a foundation for PoReps, exploring both their capabilities and their limitations. While PoReps may unconditionally demonstrate possession of data, they fundamentally cannot guarantee that the data is stored redundantly. Furthermore, as PoReps are proofs of space, they must rely either on rational time/space tradeoffs or timing bounds on the online prover's runtime. We introduce a rational security notion for PoReps called -rational replication based on the notion of an -Nash equilibrium, which captures the property that a server does not gain any significant advantage by storing its data in any other (non-redundant) format. We apply our definitions to formally analyze two recently proposed PoRep constructions based on verifiable delay functions and depth robust graphs. Lastly, we reflect on a notable application of PoReps|its unique suitability as a Nakamoto consensus mechanism that replaces proof-of-work with PoReps on real data, simultaneously incentivizing and subsidizing the cost of file storage. 1 Introduction A proof-of-replication (PoRep) builds on the two prior concepts of proofs-of-retrievability (PoR) [30] and proofs-of-space (PoS) [24]. In the former a prover demonstrates that it can retrieve a file and in the latter the prover demonstrates that it is using some minimum amount of space to store information. -

Social & Behavioural Sciences AIMC 2017 Asia International
The European Proceedings of Social & Behavioural Sciences EpSBS Future Academy ISSN: 2357-1330 http://dx.doi.org/10.15405/epsbs.2018.05.16 AIMC 2017 Asia International Multidisciplinary Conference THE REVIEW OF DISINTERMEDIATION STRATEGIES IN TWO SIDED MARKETPLACE Andi Desfiandi (a), Faurani Santi Singagerda (b)*, Novita Sari (c) *Corresponding author (a) Faculty of Economics and Business, IBI Darmajaya, Bandar Lampung, Lampung, Indonesia [email protected] (b) Faculty of Economics, University Sang Bumi Ruwa Jurai, Bandar Lampung, Lampung, Indonesia [email protected] (c) Faculty of Economics and Business, IBI Darmajaya, Bandar Lampung, Lampung, Indonesia [email protected] Abstract Two-sided marketplaces are the type of companies that connect external parties starting from ― vendors such as a seller, host, and driver, and at the same time customers such as buyer, renters and service user, to interact and transact inside the marketplace they had developed. This kind of marketplace often risk disintermediation which happens when users may rely on the market to find the potential problems related current and future transactions without the platform‘s involvement, paying any fees, and the platform may charge. This paper assesses all of the factors that trigger disintermediation happened in the marketplace, how sensitive the price fee or premium determines the level of potential disintermediation might occur, and also a set of strategies that can implement to reduce it. Furthermore, the theory used in assessing these factors includes Customer Lifetime Value, Customer Relationship Management, and Disintermediation theory. The arguments have led this paper to choose the recommendation to the research question as immediately assess the kind of disintermediation occur; other psychological factors can be the solution or ways to better shaped the platform, and always learn the pain point of buyer and seller. -
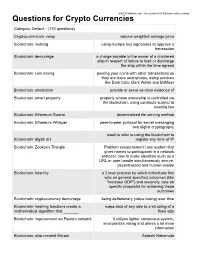
Questions for Crypto Currencies
www.YoYoBrain.com - Accelerators for Memory and Learning Questions for Crypto Currencies Category: Default - (170 questions) Cryptocurrencies: vwap volume weighted average price Blockchain: multisig using multiple key signatures to approve a transaction Blockchain: demurrage a charge payable to the owner of a chartered ship in respect of failure to load or discharge the ship within the time agreed Blockchain: coin mixing pooling your coins with other transactions so they are more anonymous, using services like Dark Coin, Dark Wallet and BitMixer Blockchain: attestation provide or serve as clear evidence of Blockchain: smart property property whose ownership is controlled via the blockchain, using contracts subject to existing law Blockchain: Ethereum Swarm decentralized file serving method Blockchain: Ethereum Whisper peer-to-peer protocol for secret messaging and digital cryptography used to refer to using the blockchain to Blockchain: digital art register any form of IP Blockchain: Zookos's Triangle Problem encountered in any system that gives names to participants in a network protocol: how to make identities such as a URL or user handle simultaneously secure, decentralized and human-usable Blockchain: futarchy a 2 level process by which individuals first vote on general specified outcomes (like "increase GDP") and secondly, vote on specific proposals for achieving those outcomes Blockchain: cryptocurrency demurrage being deflationary (value losing) over time Blockchain: hashing functions create a maps data of any size to a bit string