Sok: Tools for Game Theoretic Models of Security for Cryptocurrencies
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Potential Games. Congestion Games. Price of Anarchy and Price of Stability
8803 Connections between Learning, Game Theory, and Optimization Maria-Florina Balcan Lecture 13: October 5, 2010 Reading: Algorithmic Game Theory book, Chapters 17, 18 and 19. Price of Anarchy and Price of Staility We assume a (finite) game with n players, where player i's set of possible strategies is Si. We let s = (s1; : : : ; sn) denote the (joint) vector of strategies selected by players in the space S = S1 × · · · × Sn of joint actions. The game assigns utilities ui : S ! R or costs ui : S ! R to any player i at any joint action s 2 S: any player maximizes his utility ui(s) or minimizes his cost ci(s). As we recall from the introductory lectures, any finite game has a mixed Nash equilibrium (NE), but a finite game may or may not have pure Nash equilibria. Today we focus on games with pure NE. Some NE are \better" than others, which we formalize via a social objective function f : S ! R. Two classic social objectives are: P sum social welfare f(s) = i ui(s) measures social welfare { we make sure that the av- erage satisfaction of the population is high maxmin social utility f(s) = mini ui(s) measures the satisfaction of the most unsatisfied player A social objective function quantifies the efficiency of each strategy profile. We can now measure how efficient a Nash equilibrium is in a specific game. Since a game may have many NE we have at least two natural measures, corresponding to the best and the worst NE. We first define the best possible solution in a game Definition 1. -

Lab 5: Bittorrent Client Implementation
Lab 5: BitTorrent Client Implementation Due: Nov. 30th at 11:59 PM Milestone: Nov. 19th during Lab Overview In this lab, you and your lab parterner will develop a basic BitTorrent client that can, at minimal, exchange a file between multiple peers, and at best, function as a full feature BitTorrent Client. The programming in this assignment will be in C requiring standard sockets, and thus you will not need to have root access. You should be able to develop your code on any CS lab machine or your personal machine, but all code will be tested on the CS lab. Deliverable Your submission should minimally include the following programs and files: • REDME • Makefile • bencode.c|h • bt lib.c|h • bt setup.c|h • bt client • client trace.[n].log • sample torrent.torrent Your README file should contain a short header containing your name, username, and the assignment title. The README should additionally contain a short description of your code, tasks accomplished, and how to compile, execute, and interpret the output of your programs. Your README should also contain a list of all submitted files and code and the functionality implemented in different code files. This is a large assignment, and this will greatly aid in grading. As always, if there are any short answer questions in this lab write-up, you should provide well marked answers in the README, as well as indicate that you’ve completed any of the extra credit (so that I don’t forget to grade it). Milestones The entire assignment will be submitted and graded, but your group will also hold a milestone meeting to receive feedback on your current implementation. -

Electronic Commerce (Algorithmic Game Theory) (Tentative Syllabus)
EECS 547: Electronic Commerce (Algorithmic Game Theory) (Tentative Syllabus) Lecture: Tuesday and Thursday 10:30am-Noon in 1690 BBB Section: Friday 3pm-4pm in EECS 3427 Email: [email protected] Instructor: Grant Schoenebeck Office Hours: Wednesday 3pm and by appointment; 3636 BBBB Graduate Student Instructor: Biaoshuai Tao Office Hours: 4-5pm Friday in Learning Center (between BBB and Dow in basement) Introduction: As the internet draws together strategic actors, it becomes increasingly important to understand how strategic agents interact with computational artifacts. Algorithmic game theory studies both how to models strategic agents (game theory) and how to design systems that take agent strategies into account (mechanism design). On-line auction sites (including search word auctions), cyber currencies, and crowd-sourcing are all obvious applications. However, even more exist such as designing non- monetary award systems (reputation systems, badges, leader-boards, Facebook “likes”), recommendation systems, and data-analysis when strategic agents are involved. In this particular course, we will especially focus on information elicitation mechanisms (crowd- sourcing). Description: Modeling and analysis for strategic decision environments, combining computational and economic perspectives. Essential elements of game theory, including solution concepts and equilibrium computation. Design of mechanisms for resource allocation and social choice, for example as motivated by problems in electronic commerce and social computing. Format: The two weeks will be background lectures. The next half of the class will be seminar style and will focus on crowd-sourcing, and especially information elicitation mechanisms. Each class period, the class will read a paper (or set of papers), and a pair of students will briefly present the papers and lead a class discussion. -

A Decentralized Cloud Storage Network Framework
Storj: A Decentralized Cloud Storage Network Framework Storj Labs, Inc. October 30, 2018 v3.0 https://github.com/storj/whitepaper 2 Copyright © 2018 Storj Labs, Inc. and Subsidiaries This work is licensed under a Creative Commons Attribution-ShareAlike 3.0 license (CC BY-SA 3.0). All product names, logos, and brands used or cited in this document are property of their respective own- ers. All company, product, and service names used herein are for identification purposes only. Use of these names, logos, and brands does not imply endorsement. Contents 0.1 Abstract 6 0.2 Contributors 6 1 Introduction ...................................................7 2 Storj design constraints .......................................9 2.1 Security and privacy 9 2.2 Decentralization 9 2.3 Marketplace and economics 10 2.4 Amazon S3 compatibility 12 2.5 Durability, device failure, and churn 12 2.6 Latency 13 2.7 Bandwidth 14 2.8 Object size 15 2.9 Byzantine fault tolerance 15 2.10 Coordination avoidance 16 3 Framework ................................................... 18 3.1 Framework overview 18 3.2 Storage nodes 19 3.3 Peer-to-peer communication and discovery 19 3.4 Redundancy 19 3.5 Metadata 23 3.6 Encryption 24 3.7 Audits and reputation 25 3.8 Data repair 25 3.9 Payments 26 4 4 Concrete implementation .................................... 27 4.1 Definitions 27 4.2 Peer classes 30 4.3 Storage node 31 4.4 Node identity 32 4.5 Peer-to-peer communication 33 4.6 Node discovery 33 4.7 Redundancy 35 4.8 Structured file storage 36 4.9 Metadata 39 4.10 Satellite 41 4.11 Encryption 42 4.12 Authorization 43 4.13 Audits 44 4.14 Data repair 45 4.15 Storage node reputation 47 4.16 Payments 49 4.17 Bandwidth allocation 50 4.18 Satellite reputation 53 4.19 Garbage collection 53 4.20 Uplink 54 4.21 Quality control and branding 55 5 Walkthroughs ............................................... -

Correlated Equilibrium Is a Distribution D Over Action Profiles a Such That for Every ∗ Player I, and Every Action Ai
NETS 412: Algorithmic Game Theory February 9, 2017 Lecture 8 Lecturer: Aaron Roth Scribe: Aaron Roth Correlated Equilibria Consider the following two player traffic light game that will be familiar to those of you who can drive: STOP GO STOP (0,0) (0,1) GO (1,0) (-100,-100) This game has two pure strategy Nash equilibria: (GO,STOP), and (STOP,GO) { but these are clearly not ideal because there is one player who never gets any utility. There is also a mixed strategy Nash equilibrium: Suppose player 1 plays (p; 1 − p). If the equilibrium is to be fully mixed, player 2 must be indifferent between his two actions { i.e.: 0 = p − 100(1 − p) , 101p = 100 , p = 100=101 So in the mixed strategy Nash equilibrium, both players play STOP with probability p = 100=101, and play GO with probability (1 − p) = 1=101. This is even worse! Now both players get payoff 0 in expectation (rather than just one of them), and risk a horrific negative utility. The four possible action profiles have roughly the following probabilities under this equilibrium: STOP GO STOP 98% <1% GO <1% ≈ 0.01% A far better outcome would be the following, which is fair, has social welfare 1, and doesn't risk death: STOP GO STOP 0% 50% GO 50% 0% But there is a problem: there is no set of mixed strategies that creates this distribution over action profiles. Therefore, fundamentally, this can never result from Nash equilibrium play. The reason however is not that this play is not rational { it is! The issue is that we have defined Nash equilibria as profiles of mixed strategies, that require that players randomize independently, without any communication. -

Blockchain and The
NOTES ACKNOWLEDGMENTS INDEX Notes Introduction 1. The manifesto dates back to 1988. See Timothy May, “The Crypto Anarchist Manifesto” (1992), https:// www . activism . net / cypherpunk / crypto - anarchy . html. 2. Ibid. 3. Ibid. 4. Ibid. 5. Ibid. 6. Timothy May, “Crypto Anarchy and Virtual Communities” (1994), http:// groups . csail . mit . edu / mac / classes / 6 . 805 / articles / crypto / cypherpunks / may - virtual - comm . html. 7. Ibid. 8. For example, as we wi ll describe in more detail in Chapter 1, the Bitcoin blockchain is currently stored on over 6,000 computers in eighty- nine jurisdictions. See “Global Bitcoin Node Distribution,” Bitnodes, 21 . co, https:// bitnodes . 21 . co / . Another large blockchain- based network, Ethereum, has over 12,000 nodes, also scattered across the globe. See Ethernodes, https:// www . ethernodes . org / network / 1. 9. See note 8. 10. Some blockchains are not publicly accessible (for more on this, see Chapter 1). These blockchains are referred to as “private blockchains” and are not the focus of this book. 11. See Chapter 1. 12. The Eu ro pean Securities and Market Authority, “Discussion Paper: The Dis- tributed Ledger Technology Applied to Securities Markets,” ESMA / 2016 / 773, June 2, 2016: at 17, https:// www . esma . europa . eu / sites / default / files / library / 2016 - 773 _ dp _ dlt . pdf. 213 214 NOTES TO PAGES 5–13 13. The phenomena of order without law also has been described in other con- texts, most notably by Robert Ellickson in his seminal work Order without Law (Cambridge, MA: Harvard University Press, 1994). 14. Joel Reidenberg has used the term “lex informatica” to describe rules imple- mented by centralized operators online. -

Proofs of Replication Are Also Relevant in the Private-Verifier Setting of Proofs of Data Replication
PoReps: Proofs of Space on Useful Data Ben Fisch Stanford University, Protocol Labs Abstract A proof-of-replication (PoRep) is an interactive proof system in which a prover defends a publicly verifiable claim that it is dedicating unique resources to storing one or more retrievable replicas of a data file. In this sense a PoRep is both a proof of space (PoS) and a proof of retrievability (PoR). This paper establishes a foundation for PoReps, exploring both their capabilities and their limitations. While PoReps may unconditionally demonstrate possession of data, they fundamentally cannot guarantee that the data is stored redundantly. Furthermore, as PoReps are proofs of space, they must rely either on rational time/space tradeoffs or timing bounds on the online prover's runtime. We introduce a rational security notion for PoReps called -rational replication based on the notion of an -Nash equilibrium, which captures the property that a server does not gain any significant advantage by storing its data in any other (non-redundant) format. We apply our definitions to formally analyze two recently proposed PoRep constructions based on verifiable delay functions and depth robust graphs. Lastly, we reflect on a notable application of PoReps|its unique suitability as a Nakamoto consensus mechanism that replaces proof-of-work with PoReps on real data, simultaneously incentivizing and subsidizing the cost of file storage. 1 Introduction A proof-of-replication (PoRep) builds on the two prior concepts of proofs-of-retrievability (PoR) [30] and proofs-of-space (PoS) [24]. In the former a prover demonstrates that it can retrieve a file and in the latter the prover demonstrates that it is using some minimum amount of space to store information. -

Algorithmic Game Theory
Algorithmic Game Theory 3 Abstract When computers began their emergence some 50 years ago, they were merely standalone machines that could iterate basic computations a fixed number of times. Humanity began to tailor problems so that computers could compute answers, thus forming a language between the two. Al- gorithms that computers could understand began to be made and left computer scientists with the task of determining which algorithms were better than others with respect to running time and complexity. Inde- pendently, right around this time, game theory was beginning to take o↵ with applications, most notably in economics. Game theory studies inter- actions between individuals, whether they are competing or cooperating. Who knew that in almost 50 years time these two seemingly independent entities would be forced together with the emergence of the Internet? The Internet was not simply made by one person but rather was the result of many people wanting to interact. Naturally, Game Theorists stepped in to understand the growing market of the Internet. Additionally, Computer Scientists wished to create new designs and algorithms with Internet ap- plications. With this clash of disciplines, a hybrid subject was born, Algo- rithmic Game Theory (AGT). This paper will showcase the fundamental task of determining the complexity of finding Nash Equilibria, address algorithms that attempt to model how humans would interact with an uncertain environment and quantify inefficiency in equilibria when com- pared to some societal optimum. 4 Contents 1 Introduction 6 2 Computational Complexity of Nash Equilibria 7 2.1 Parity Argument . 8 2.2 The PPAD Complexity Class . -
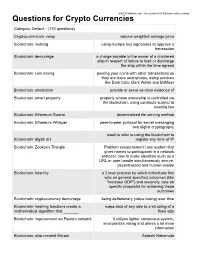
Questions for Crypto Currencies
www.YoYoBrain.com - Accelerators for Memory and Learning Questions for Crypto Currencies Category: Default - (170 questions) Cryptocurrencies: vwap volume weighted average price Blockchain: multisig using multiple key signatures to approve a transaction Blockchain: demurrage a charge payable to the owner of a chartered ship in respect of failure to load or discharge the ship within the time agreed Blockchain: coin mixing pooling your coins with other transactions so they are more anonymous, using services like Dark Coin, Dark Wallet and BitMixer Blockchain: attestation provide or serve as clear evidence of Blockchain: smart property property whose ownership is controlled via the blockchain, using contracts subject to existing law Blockchain: Ethereum Swarm decentralized file serving method Blockchain: Ethereum Whisper peer-to-peer protocol for secret messaging and digital cryptography used to refer to using the blockchain to Blockchain: digital art register any form of IP Blockchain: Zookos's Triangle Problem encountered in any system that gives names to participants in a network protocol: how to make identities such as a URL or user handle simultaneously secure, decentralized and human-usable Blockchain: futarchy a 2 level process by which individuals first vote on general specified outcomes (like "increase GDP") and secondly, vote on specific proposals for achieving those outcomes Blockchain: cryptocurrency demurrage being deflationary (value losing) over time Blockchain: hashing functions create a maps data of any size to a bit string -

Chicago Journal of Theoretical Computer Science the MIT Press
Chicago Journal of Theoretical Computer Science The MIT Press Volume 1997, Article 2 3 June 1997 ISSN 1073–0486. MIT Press Journals, Five Cambridge Center, Cambridge, MA 02142-1493 USA; (617)253-2889; [email protected], [email protected]. Published one article at a time in LATEX source form on the Internet. Pag- ination varies from copy to copy. For more information and other articles see: http://www-mitpress.mit.edu/jrnls-catalog/chicago.html • http://www.cs.uchicago.edu/publications/cjtcs/ • ftp://mitpress.mit.edu/pub/CJTCS • ftp://cs.uchicago.edu/pub/publications/cjtcs • Kann et al. Hardness of Approximating Max k-Cut (Info) The Chicago Journal of Theoretical Computer Science is abstracted or in- R R R dexed in Research Alert, SciSearch, Current Contents /Engineering Com- R puting & Technology, and CompuMath Citation Index. c 1997 The Massachusetts Institute of Technology. Subscribers are licensed to use journal articles in a variety of ways, limited only as required to insure fair attribution to authors and the journal, and to prohibit use in a competing commercial product. See the journal’s World Wide Web site for further details. Address inquiries to the Subsidiary Rights Manager, MIT Press Journals; (617)253-2864; [email protected]. The Chicago Journal of Theoretical Computer Science is a peer-reviewed scholarly journal in theoretical computer science. The journal is committed to providing a forum for significant results on theoretical aspects of all topics in computer science. Editor in chief: Janos Simon Consulting -

Introduction to the AI Magazine Special Issue on Algorithmic Game Theory
Introduction to the AI Magazine Special Issue on Algorithmic Game Theory Edith Elkind Kevin Leyton-Brown Abstract We briefly survey the rise of game theory as a topic of study in artifi- cial intelligence, and explain the term algorithmic game theory. We then describe three broad areas of current inquiry by AI researchers in algo- rithmic game theory: game playing, social choice, and mechanism design. Finally, we give short summaries of each of the six articles appearing in this issue. 1 Algorithmic Game Theory and Artificial Intelligence Game theory is a branch of mathematics devoted to studying interaction among rational and self-interested agents. The field took on its modern form in the 1940s and 1950s (von Neumann and Morgenstern, 1947; Nash, 1950; Kuhn, 1953), with even earlier antecedents (e.g., Zermelo, 1913; von Neumann, 1928). Although it has had occasional and significant overlap with computer science over the years, game theory received most of its early study by economists. Indeed, game theory now serves as perhaps the main analytical framework in microeconomic theory, as evidenced by its prominent role in economics text- books (e.g., Mas-Colell, Whinston, and Green, 1995) and by the many Nobel prizes in Economic Sciences awarded to prominent game theorists. Artificial intelligence got its start shortly after game theory (McCarthy et al., 1955), and indeed pioneers such as von Neumann and Simon made early contributions to both fields (see, e.g., Findler, 1988; Simon, 1981). Both game theory and AI draw (non-exclusively) on decision theory (von Neumann and Morgenstern, 1947); e.g., one prominent view defines artificial intelligence as \the study and construction of rational agents" (Russell and Norvig, 2003), and hence takes a decision-theoretic approach when the world is stochastic. -

HODL Deck V4
BUILDING THE WORLD’S LEADING PRIVACY INVESTMENT VEHICLE Presentation Subtitle 2020 Cypherpunk Holdings Inc. CSE: HODL INVESTOR PRESENTATION January 2021 1 Investor Presentation January 2021 DISCLAIMER - CAUTIONARY NOTE REGARDING FORWARD-LOOKING INFORMATION This presentation contains “forward-looking information” within the meaning of applicable securities laws. Generally, any statements that are not historical facts may contain forward-looking information, and forward-looking information can be identified by the use of forward-looking terminology such as “plans”, “expects” or “does not expect”, “is expected”, “budget”, “scheduled”, “estimates”, “forecasts”, “intends”, “anticipates” or “does not anticipate”, or “believes”, or variations of such words and phrases or indicates that certain actions, events or results “may”, “could”, “would”, “might” or “will be” taken, “occur” or “be achieved”. Forward-looking information includes, but is not limited to the Company’s goal of making investments in, crypto-currencies, digital currencies and assets, the blockchain, software and other sectors, financial information and enhancing value. There is no assurance that the Company’s plans or objectives will be implemented as set out herein, or at all. Forward-looking information is based on certain factors and assumptions the Company believes to be reasonable at the time such statements are made and is subject to known and unknown risks, uncertainties and other factors that may cause the actual results, level of activity, performance or achievements of the Company to be materially different from those expressed or implied by such forward-looking information. There can be no assurance that such forward-looking information will prove to be accurate, as actual results and future events could differ materially from those anticipated in such information.