Peer-To-Peer Networking with Bittorrent
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Analysis of Bittorrent Protocol and Its Effect on the Network ENSC 427: Final Project Report Spring 2011
SIMON FRASER UNIVERSITY Analysis of BitTorrent Protocol and Its Effect on the Network ENSC 427: Final Project Report Spring 2011 Group 11 www.sfu.ca/~kna5/ensc427 Ken Kyoungwoo Nam 301046747 Kna5 @sfu.ca Yu Jie Xu 301083552 Xya14 @ sfu.ca Abstract The first version of the peer-to-peer file sharing protocol was invented in 1999, called Napster protocol. From then on, the application of peer-to-peer protocol has been widely spread in the internet. The advantage of the network with p2p protocol is that it needs much less server bandwidth compare to the basic client and server network. Moreover, in the p2p network, the client itself is the server, so they can communicate with each other without the central sever. Nowadays, there are two primary peer-to-peer file sharing protocol that dominate in the network: the Gnutella protocol and BitTorrent Protocol. In our project, we will focus on BitTorrent Protocol. To do this, we will create three different networks in OPNET, and investigate the network performance with and without BitTorrent nodes. 2 Table of contents 1. Introduction…………..……………………………………………………………......4 2. Theory……………...………………………………………………………………......4 2.1 Terminology and Definition…………………………………………………......5 2.2 Peer-to-Peer Protocol…………………………………………………………….5 2.3 BitTorrent Protocol………………………………………………………………6 2.4 BitTorrent Tracker………………………………………………………………7 2.5 Rarest Algorithm…………………………………………………………………8 2.6 Choke Algorithm…………………………………………………………………9 3. Implementation…...…………………………………………………………..……...10 3.1 Packet Formats………………………………………………………………….11 3.2 Normal Client and Server Node Models………………………………………11 3.3 Plain Peer-to-Peer Node Model……………………………………..…………12 3.4 BitTorrent Node Model……………………………………………………...…13 3.5 Building the Small Network……………………………………………………14 3.6 Building the Large Network…………………………………………………...15 4. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

What Is Peer-To-Peer File Transfer? Bandwidth It Can Use
sharing, with no cap on the amount of commonly used to trade copyrighted music What is Peer-to-Peer file transfer? bandwidth it can use. Thus, a single NSF PC and software. connected to NSF’s LAN with a standard The Recording Industry Association of A peer-to-peer, or “P2P,” file transfer 100Mbps network card could, with KaZaA’s America tracks users of this software and has service allows the user to share computer files default settings, conceivably saturate NSF’s begun initiating lawsuits against individuals through the Internet. Examples of P2P T3 (45Mbps) internet connection. who use P2P systems to steal copyrighted services include KaZaA, Grokster, Gnutella, The KaZaA software assesses the quality of material or to provide copyrighted software to Morpheus, and BearShare. the PC’s internet connection and designates others to download freely. These services are set up to allow users to computers with high-speed connections as search for and download files to their “Supernodes,” meaning that they provide a How does use of these services computers, and to enable users to make files hub between various users, a source of available for others to download from their information about files available on other create security issues at NSF? computers. users’ PCs. This uses much more of the When configuring these services, it is computer’s resources, including bandwidth possible to designate as “shared” not only the and processing capability. How do these services function? one folder KaZaA sets up by default, but also The free version of KaZaA is supported by the entire contents of the user’s computer as Peer to peer file transfer services are highly advertising, which appears on the user well as any NSF network drives to which the decentralized, creating a network of linked interface of the program and also causes pop- user has access, to be searchable and users. -

IBM Cloud Unit 2016 IBM Cloud Unit Leadership Organization
IBM Cloud Technical Academy IBM Cloud Unit 2016 IBM Cloud Unit Leadership Organization SVP IBM Cloud Robert LeBlanc GM Cloud Platform GM Cloud GM Cloud Managed GM Cloud GM Cloud Object Integration Services Video Storage Offering Bill Karpovich Mike Valente Braxton Jarratt Line Execs Line Execs Marie Wieck John Morris GM Strategy, GM Client Technical VP Development VP Service Delivery Business Dev Engagement Don Rippert Steve Robinson Harish Grama Janice Fischer J. Comfort (GM & CTO) J. Considine (Innovation Lab) Function Function Leadership Leadership VP Marketing GM WW Sales & VP Finance VP Human Quincy Allen Channels Resources Steve Cowley Steve Lasher Sam Ladah S. Carter (GM EcoD) GM Design VP Enterprise Mobile GM Digital Phil Gilbert Phil Buckellew Kevin Eagan Missions Missions Enterprise IBM Confidential IBM Hybrid Cloud Guiding Principles Choice with! Hybrid ! DevOps! Cognitive Powerful, Consistency! Integration! Productivity! Solutions! Accessible Data and Analytics! The right Unlock existing Automation, tooling Applications and Connect and extract workload in the IT investments and composable systems that insight from all types right place and Intellectual services to increase have the ability to of data Property speed learn Three entry points 1. Create! 2. Connect! 3. Optimize! new cloud apps! existing apps and data! any app! 2016 IBM Cloud Offerings aligned to the Enterprise’s hybrid cloud needs IBM Cloud Platform IBM Cloud Integration IBM Cloud Managed Offerings Offerings Services Offerings Mission: Build true cloud platform -
Securebox Azure
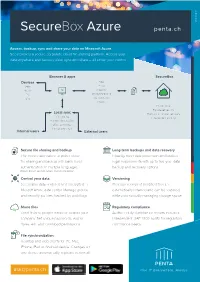
General Electronics E-Commerce General Web General General General Electronics General Location Electronics E-Commerce Electronics Electronics Arrows General Web Electronics E-Commerce E-Commerce E-Commerce Web Location GeneraE-Col mmerce Weather Web Arrows WeWeb b Electronics Location Weather Miscellaneous Location Arrows Location Location Arrows Arrows Miscellaneous Electronics E-Commerce Arrows Weather Weather Weather Miscellaneous Web 28/03/2019 Weather SecureBox Azure penta.ch General Miscellaneous Access, backup, sync and share your data on Microsoft Azure SecureBox is a secure corporate cloud file sharing platform. Access your data anywhere and backup, view, sync and share – all under your control. Miscellaneous E-Commerce Browser & apps General SecureBox Devices Files Tablet Email Mobile Calendar PC Word processing Mac Spreadsheets Miscellaneous Photos Private cloud Bank-level security Local sync Backups & disaster recovery File sharing Independent auditing Password protection Editing permissions Link expiry dates Internal users External users SecureLo filecati sharingon and backup Long-term backups and data recovery The secure alternative to public cloud Instantly meet data protection and backup file sharing and backup with bank-level legal requirements with up to five-year data authentication. In multiple languages. backup and recovery options. English, French, German, Italian, Spanish and Arabic Web Control your data Versioning SecureBox data is stored and encrypted in Previous version of modified files are Microsft Azure data center. Manage groups automatically retained and can be restored, and security policies, backed by audit logs. while automatically managing storage space. Share files Regulatory compliance Send Arrolinks to wspeople inside or outside your Auditor-ready compliance reports included. company. Set unique passwords, expiry IndependentElec ISAEtr onic3402 auditss for regulatory dates, edit and download permissions. -

Mimioclassroom User Guide for Windows
MimioClassroom User Guide For Windows mimio.com © 2012 Sanford, L.P. All rights reserved. Revised 12/4/2012. No part of this document or the software may be reproduced or transmitted in any form or by any means or translated into another language without the prior written consent of Sanford, L.P. Mimio, MimioClassroom, MimioTeach, MimioCapture, MimioVote, MimioView, MimioHub, MimioPad, and MimioStudio are registered marks in the United States and other countries. All other trademarks are the property of their respective holders. Contents About MimioClassroom 1 MimioStudio 1 MimioTeach 1 Mimio Interactive 1 MimioCapture 2 Mimio Capture Kit 2 MimioVote 2 MimioView 2 MimioPad 2 Minimum System Requirements 2 Using this Guide 3 MimioStudio 7 About MimioStudio 7 About MimioStudio Notebook 7 About MimioStudio Tools 7 About MimioStudio Gallery 9 Getting Started with MimioStudio 9 Accessing MimioStudio Notebook 9 Accessing MimioStudio Tools 10 Accessing MimioStudio Gallery 10 Using MimioStudio Notebook 10 Working with Pages 11 Creating an Activity 14 Creating an Activity - Step 1: Define 14 Creating an Activity - Step 2: Select 14 Creating an Activity - Step 3: Refine 15 Creating an Activity - Step 4: Review 16 Working with an Activity 17 Writing an Objective 17 Attaching Files 18 Using MimioStudio Tools 18 Creating Objects 18 Manipulating Objects 21 Adding Actions to Objects 25 Using MimioStudio Gallery 26 iii Importing Gallery Items into a Notebook 27 Customizing the Content of the Gallery 27 Exporting a Gallery Folder to a Gallery File 29 Working -

The Edonkey File-Sharing Network
The eDonkey File-Sharing Network Oliver Heckmann, Axel Bock, Andreas Mauthe, Ralf Steinmetz Multimedia Kommunikation (KOM) Technische Universitat¨ Darmstadt Merckstr. 25, 64293 Darmstadt (heckmann, bock, mauthe, steinmetz)@kom.tu-darmstadt.de Abstract: The eDonkey 2000 file-sharing network is one of the most successful peer- to-peer file-sharing applications, especially in Germany. The network itself is a hybrid peer-to-peer network with client applications running on the end-system that are con- nected to a distributed network of dedicated servers. In this paper we describe the eDonkey protocol and measurement results on network/transport layer and application layer that were made with the client software and with an open-source eDonkey server we extended for these measurements. 1 Motivation and Introduction Most of the traffic in the network of access and backbone Internet service providers (ISPs) is generated by peer-to-peer (P2P) file-sharing applications [San03]. These applications are typically bandwidth greedy and generate more long-lived TCP flows than the WWW traffic that was dominating the Internet traffic before the P2P applications. To understand the influence of these applications and the characteristics of the traffic they produce and their impact on network design, capacity expansion, traffic engineering and shaping, it is important to empirically analyse the dominant file-sharing applications. The eDonkey file-sharing protocol is one of these file-sharing protocols. It is imple- mented by the original eDonkey2000 client [eDonkey] and additionally by some open- source clients like mldonkey [mlDonkey] and eMule [eMule]. According to [San03] it is with 52% of the generated file-sharing traffic the most successful P2P file-sharing net- work in Germany, even more successful than the FastTrack protocol used by the P2P client KaZaa [KaZaa] that comes to 44% of the traffic. -

Lab 5: Bittorrent Client Implementation
Lab 5: BitTorrent Client Implementation Due: Nov. 30th at 11:59 PM Milestone: Nov. 19th during Lab Overview In this lab, you and your lab parterner will develop a basic BitTorrent client that can, at minimal, exchange a file between multiple peers, and at best, function as a full feature BitTorrent Client. The programming in this assignment will be in C requiring standard sockets, and thus you will not need to have root access. You should be able to develop your code on any CS lab machine or your personal machine, but all code will be tested on the CS lab. Deliverable Your submission should minimally include the following programs and files: • REDME • Makefile • bencode.c|h • bt lib.c|h • bt setup.c|h • bt client • client trace.[n].log • sample torrent.torrent Your README file should contain a short header containing your name, username, and the assignment title. The README should additionally contain a short description of your code, tasks accomplished, and how to compile, execute, and interpret the output of your programs. Your README should also contain a list of all submitted files and code and the functionality implemented in different code files. This is a large assignment, and this will greatly aid in grading. As always, if there are any short answer questions in this lab write-up, you should provide well marked answers in the README, as well as indicate that you’ve completed any of the extra credit (so that I don’t forget to grade it). Milestones The entire assignment will be submitted and graded, but your group will also hold a milestone meeting to receive feedback on your current implementation. -

Asynchronous Covert Communication Using Bittorrent Trackers Mathieu Cunche, Mohamed Ali Kaafar, Roksana Boreli
Asynchronous Covert Communication Using BitTorrent Trackers Mathieu Cunche, Mohamed Ali Kaafar, Roksana Boreli To cite this version: Mathieu Cunche, Mohamed Ali Kaafar, Roksana Boreli. Asynchronous Covert Communication Using BitTorrent Trackers. International Symposium on Cyberspace Safety and Security (CSS), Aug 2014, Paris, France. hal-01053147 HAL Id: hal-01053147 https://hal.inria.fr/hal-01053147 Submitted on 29 Jul 2014 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Asynchronous Covert Communication Using BitTorrent Trackers Mathieu Cunche∗†, Mohamed-Ali Kaafar†‡, Roksana Boreli‡ †Inria, France ∗INSA-Lyon CITI, France ‡National ICT Australia fi[email protected] fi[email protected] Abstract—Covert channels enable communicating parties to in a swarm (set of peers downloading and/or sharing a given exchange messages without being detected by an external ob- content). Our contributions are as follows. server. We propose a novel covert channel mechanism based We present a communication scheme that enables two on BitTorrent trackers. The proposed mechanism uses common HTTP commands, thus having the appearance of genuine web parties to perform a hidden exchange of information through traffic and consists of communications that are both indirect and the centralized BitTorrent tracker. -
![[Hal-00744922, V1] Improving Content Availability in the I2P Anonymous](https://docslib.b-cdn.net/cover/4228/hal-00744922-v1-improving-content-availability-in-the-i2p-anonymous-324228.webp)
[Hal-00744922, V1] Improving Content Availability in the I2P Anonymous
Improving Content Availability in the I2P Anonymous File-Sharing Environment Juan Pablo Timpanaro, Isabelle Chrisment*, Olivier Festor INRIA Nancy-Grand Est, France *LORIA - ESIAL, Universit´ede Lorraine Email: fjuanpablo.timpanaro, [email protected] Email: [email protected] Abstract. Anonymous communication has gained more and more inter- est from Internet users as privacy and anonymity problems have emerged. Dedicated anonymous networks such as Freenet and I2P allow anony- mous file-sharing among users. However, one major problem with anony- mous file-sharing networks is that the available content is highly reduced, mostly with outdated files, and non-anonymous networks, such as the BitTorrent network, are still the major source of content: we show that in a 30-days period, 21648 new torrents were introduced in the BitTor- rent community, whilst only 236 were introduced in the anonymous I2P network, for four different categories of content. Therefore, how can a user of these anonymous networks access this varied and non-anonymous content without compromising its anonymity? In this paper, we improve content availability in an anonymous environment by proposing the first internetwork model allowing anonymous users to access and share content in large public communities while remaining anonymous. We show that our approach can efficiently interconnect I2P users and public BitTorrent swarms without affecting their anonymity nor their performance. Our model is fully implemented and freely usable. 1 Introduction Peer-to-peer file-sharing has always been one of the major sources of the Internet hal-00744922, version 1 - 24 Oct 2012 traffic, since its early beginnings in 2000. It has been moving from semi-central approaches (eDonkey2000, for example), to semi-decentralized approaches (Kazaa, for instance) to fully decentralized file-sharing architectures (like the KAD net- work). -

A Decentralized Cloud Storage Network Framework
Storj: A Decentralized Cloud Storage Network Framework Storj Labs, Inc. October 30, 2018 v3.0 https://github.com/storj/whitepaper 2 Copyright © 2018 Storj Labs, Inc. and Subsidiaries This work is licensed under a Creative Commons Attribution-ShareAlike 3.0 license (CC BY-SA 3.0). All product names, logos, and brands used or cited in this document are property of their respective own- ers. All company, product, and service names used herein are for identification purposes only. Use of these names, logos, and brands does not imply endorsement. Contents 0.1 Abstract 6 0.2 Contributors 6 1 Introduction ...................................................7 2 Storj design constraints .......................................9 2.1 Security and privacy 9 2.2 Decentralization 9 2.3 Marketplace and economics 10 2.4 Amazon S3 compatibility 12 2.5 Durability, device failure, and churn 12 2.6 Latency 13 2.7 Bandwidth 14 2.8 Object size 15 2.9 Byzantine fault tolerance 15 2.10 Coordination avoidance 16 3 Framework ................................................... 18 3.1 Framework overview 18 3.2 Storage nodes 19 3.3 Peer-to-peer communication and discovery 19 3.4 Redundancy 19 3.5 Metadata 23 3.6 Encryption 24 3.7 Audits and reputation 25 3.8 Data repair 25 3.9 Payments 26 4 4 Concrete implementation .................................... 27 4.1 Definitions 27 4.2 Peer classes 30 4.3 Storage node 31 4.4 Node identity 32 4.5 Peer-to-peer communication 33 4.6 Node discovery 33 4.7 Redundancy 35 4.8 Structured file storage 36 4.9 Metadata 39 4.10 Satellite 41 4.11 Encryption 42 4.12 Authorization 43 4.13 Audits 44 4.14 Data repair 45 4.15 Storage node reputation 47 4.16 Payments 49 4.17 Bandwidth allocation 50 4.18 Satellite reputation 53 4.19 Garbage collection 53 4.20 Uplink 54 4.21 Quality control and branding 55 5 Walkthroughs ............................................... -

Downloading Copyrighted Materials
What you need to know before... Downloading Copyrighted Materials Including movies, TV shows, music, digital books, software and interactive games The Facts and Consequences Who monitors peer-to-peer file sharing? What are the consequences at UAF The Motion Picture Association of America for violators of this policy? (MPAA), Home Box Office, and other copyright Student Services at UAF takes the following holders monitor file-sharing on the Internet minimum actions when the policy is violated: for the illegal distribution of their copyrighted 1st Offense: contents. Once identified they issue DMCA Loss of Internet access until issue is resolved. (Digital Millennium Copyright Act) take-down 2nd Offense: notices to the ISP (Internet Service Provider), in Loss of Internet access pending which the University of Alaska is considered as resolution and a $100 fee assessment. one, requesting the infringement be stopped. If 3rd Offense: not stopped, lawsuit against the user is possible. Loss of Internet access pending resolution and a $250 fee assessment. What is UAF’s responsibility? 4th, 5th, 6th Offense: Under the Digital Millennium Copyright Act and Loss of Internet access pending resolution and Higher Education Opportunity Act, university a $500 fee assessment. administrators are obligated to track these infractions and preserve relevent logs in your What are the Federal consequences student record. This means that if your case goes for violators? to court, your record may be subpoenaed as The MPAA, HBO and similar organizations are evidence. Since illegal file sharing also drains becoming more and more aggressive in finding bandwidth, costing schools money and slowing and prosecuting alleged offenders in criminal Internet connections, for students trying to use court.