Lock-Free Collaboration Support for Cloud Storage Services With
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Compress/Decompress Encrypt/Decrypt
Windows Compress/Decompress WinZip Standard WinZip Pro Compressed Folders Zip and unzip files instantly with 64-bit, best-in-class software ENHANCED! Compress MP3 files by 15 - 20 % on average Open and extract Zipx, RAR, 7Z, LHA, BZ2, IMG, ISO and all other major compression file formats Open more files types as a Zip, including DOCX, XLSX, PPTX, XPS, ODT, ODS, ODP, ODG,WMZ, WSZ, YFS, XPI, XAP, CRX, EPUB, and C4Z Use the super picker to unzip locally or to the cloud Open CAB, Zip and Zip 2.0 Methods Convert other major compressed file formats to Zip format Apply 'Best Compression' method to maximize efficiency automatically based on file type Reduce JPEG image files by 20 - 25% with no loss of photo quality or data integrity Compress using BZip2, LZMA, PPMD and Enhanced Deflate methods Compress using Zip 2.0 compatible methods 'Auto Open' a zipped Microsoft Office file by simply double-clicking the Zip file icon Employ advanced 'Unzip and Try' functionality to review interrelated components contained within a Zip file (such as an HTML page and its associated graphics). Windows Encrypt/Decrypt WinZip Standard WinZip Pro Compressed Folders Apply encryption and conversion options, including PDF conversion, watermarking and photo resizing, before, during or after creating your zip Apply separate conversion options to individual files in your zip Take advantage of hardware support in certain Intel-based computers for even faster AES encryption Administrative lockdown of encryption methods and password policies Check 'Encrypt' to password protect your files using banking-level encryption and keep them completely secure Secure sensitive data with strong, FIPS-197 certified AES encryption (128- and 256- bit) Auto-wipe ('shred') temporarily extracted copies of encrypted files using the U.S. -

IBM Cloud Unit 2016 IBM Cloud Unit Leadership Organization
IBM Cloud Technical Academy IBM Cloud Unit 2016 IBM Cloud Unit Leadership Organization SVP IBM Cloud Robert LeBlanc GM Cloud Platform GM Cloud GM Cloud Managed GM Cloud GM Cloud Object Integration Services Video Storage Offering Bill Karpovich Mike Valente Braxton Jarratt Line Execs Line Execs Marie Wieck John Morris GM Strategy, GM Client Technical VP Development VP Service Delivery Business Dev Engagement Don Rippert Steve Robinson Harish Grama Janice Fischer J. Comfort (GM & CTO) J. Considine (Innovation Lab) Function Function Leadership Leadership VP Marketing GM WW Sales & VP Finance VP Human Quincy Allen Channels Resources Steve Cowley Steve Lasher Sam Ladah S. Carter (GM EcoD) GM Design VP Enterprise Mobile GM Digital Phil Gilbert Phil Buckellew Kevin Eagan Missions Missions Enterprise IBM Confidential IBM Hybrid Cloud Guiding Principles Choice with! Hybrid ! DevOps! Cognitive Powerful, Consistency! Integration! Productivity! Solutions! Accessible Data and Analytics! The right Unlock existing Automation, tooling Applications and Connect and extract workload in the IT investments and composable systems that insight from all types right place and Intellectual services to increase have the ability to of data Property speed learn Three entry points 1. Create! 2. Connect! 3. Optimize! new cloud apps! existing apps and data! any app! 2016 IBM Cloud Offerings aligned to the Enterprise’s hybrid cloud needs IBM Cloud Platform IBM Cloud Integration IBM Cloud Managed Offerings Offerings Services Offerings Mission: Build true cloud platform -

Short-Format Workshops Build Skills and Confidence for Researchers to Work with Data
Paper ID #23855 Short-format Workshops Build Skills and Confidence for Researchers to Work with Data Kari L. Jordan Ph.D., The Carpentries Dr. Kari L. Jordan is the Director of Assessment and Community Equity for The Carpentries, a non-profit that develops and teaches core data science skills for researchers. Marianne Corvellec, Institute for Globally Distributed Open Research and Education (IGDORE) Marianne Corvellec has worked in industry as a data scientist and a software developer since 2013. Since then, she has also been involved with the Carpentries, pursuing interests in community outreach, educa- tion, and assessment. She holds a PhD in statistical physics from Ecole´ Normale Superieure´ de Lyon, France (2012). Elizabeth D. Wickes, University of Illinois at Urbana-Champaign Elizabeth Wickes is a Lecturer at the School of Information Sciences at the University of Illinois, where she teaches foundational programming and information technology courses. She was previously a Data Curation Specialist for the Research Data Service at the University Library of the University of Illinois, and the Curation Manager for WolframjAlpha. She currently co-organizes the Champaign-Urbana Python user group, has been a Carpentries instructor since 2015 and trainer since 2017, and elected member of The Carpentries’ Executive Council for 2018. Dr. Naupaka B. Zimmerman, University of San Francisco Mr. Jonah M. Duckles, Software Carpentry Jonah Duckles works to accelerate data-driven inquiry by catalyzing digital skills and building organiza- tional capacity. As a part of the leadership team, he helped to grow Software and Data Carpentry into a financially sustainable non-profit with a robust organization membership in 10 countries. -
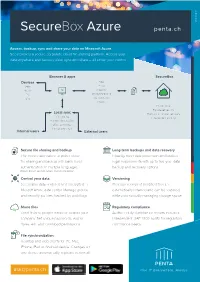
Securebox Azure
General Electronics E-Commerce General Web General General General Electronics General Location Electronics E-Commerce Electronics Electronics Arrows General Web Electronics E-Commerce E-Commerce E-Commerce Web Location GeneraE-Col mmerce Weather Web Arrows WeWeb b Electronics Location Weather Miscellaneous Location Arrows Location Location Arrows Arrows Miscellaneous Electronics E-Commerce Arrows Weather Weather Weather Miscellaneous Web 28/03/2019 Weather SecureBox Azure penta.ch General Miscellaneous Access, backup, sync and share your data on Microsoft Azure SecureBox is a secure corporate cloud file sharing platform. Access your data anywhere and backup, view, sync and share – all under your control. Miscellaneous E-Commerce Browser & apps General SecureBox Devices Files Tablet Email Mobile Calendar PC Word processing Mac Spreadsheets Miscellaneous Photos Private cloud Bank-level security Local sync Backups & disaster recovery File sharing Independent auditing Password protection Editing permissions Link expiry dates Internal users External users SecureLo filecati sharingon and backup Long-term backups and data recovery The secure alternative to public cloud Instantly meet data protection and backup file sharing and backup with bank-level legal requirements with up to five-year data authentication. In multiple languages. backup and recovery options. English, French, German, Italian, Spanish and Arabic Web Control your data Versioning SecureBox data is stored and encrypted in Previous version of modified files are Microsft Azure data center. Manage groups automatically retained and can be restored, and security policies, backed by audit logs. while automatically managing storage space. Share files Regulatory compliance Send Arrolinks to wspeople inside or outside your Auditor-ready compliance reports included. company. Set unique passwords, expiry IndependentElec ISAEtr onic3402 auditss for regulatory dates, edit and download permissions. -

Mimioclassroom User Guide for Windows
MimioClassroom User Guide For Windows mimio.com © 2012 Sanford, L.P. All rights reserved. Revised 12/4/2012. No part of this document or the software may be reproduced or transmitted in any form or by any means or translated into another language without the prior written consent of Sanford, L.P. Mimio, MimioClassroom, MimioTeach, MimioCapture, MimioVote, MimioView, MimioHub, MimioPad, and MimioStudio are registered marks in the United States and other countries. All other trademarks are the property of their respective holders. Contents About MimioClassroom 1 MimioStudio 1 MimioTeach 1 Mimio Interactive 1 MimioCapture 2 Mimio Capture Kit 2 MimioVote 2 MimioView 2 MimioPad 2 Minimum System Requirements 2 Using this Guide 3 MimioStudio 7 About MimioStudio 7 About MimioStudio Notebook 7 About MimioStudio Tools 7 About MimioStudio Gallery 9 Getting Started with MimioStudio 9 Accessing MimioStudio Notebook 9 Accessing MimioStudio Tools 10 Accessing MimioStudio Gallery 10 Using MimioStudio Notebook 10 Working with Pages 11 Creating an Activity 14 Creating an Activity - Step 1: Define 14 Creating an Activity - Step 2: Select 14 Creating an Activity - Step 3: Refine 15 Creating an Activity - Step 4: Review 16 Working with an Activity 17 Writing an Objective 17 Attaching Files 18 Using MimioStudio Tools 18 Creating Objects 18 Manipulating Objects 21 Adding Actions to Objects 25 Using MimioStudio Gallery 26 iii Importing Gallery Items into a Notebook 27 Customizing the Content of the Gallery 27 Exporting a Gallery Folder to a Gallery File 29 Working -

Wandisco Fusion® Microsoft Azure Data Box
WANDISCO FUSION® MICROSOFT AZURE DATA BOX Use WANdisco Fusion with Data Box for bulk transfer of changing data WANdisco Fusion is the only solution that enables Microsoft customers to use the bulk transfer capabilities of the Azure Data Box to transfer static and changing Guaranteed data consistency information from Big Data applications to Azure Cloud with guaranteed data consistency. Users can continue to Take advantage of the storage on Azure Data Box for write to their local cluster while the Azure Data Box is in bulk data transfer while continuing to write to a local transit so when the Azure Data Box is subsequently being cluster and replicate those changes while the Azure uploaded, any changes are replicated to the Azure Cloud Data Box is uploaded to the Azure Cloud. with guaranteed consistency. Easy and intuitive step-by-step operation • Applications write to Azure Data Box using the same API that they use to interact with the Azure Cloud. No downtime and • WANdisco Fusion for Azure Data Box requires no change to applications which can continue to use the no business disruption API as they would normally. Write data to a local HDFS-compatible endpoint • Replication is continuous and recovers from on-premises and replicate to a storage location in intermittent network or system failures automatically. Microsoft Azure with no modification or disruption to applications on-premises. AZURE 2 STORAGE Cost saving MICROSOFT 1 3 AZURE DATA BOX Avoid the high network costs common to large scale data transfers and benefit from a range of FUSION applications available in Azure Cloud. -

Operational Transformation in Co-Operative Editing
INTERNATIONAL JOURNAL OF SCIENTIFIC & TECHNOLOGY RESEARCH VOLUME 5, ISSUE 01, JANUARY 2016 ISSN 2277-8616 Operational Transformation In Co-Operative Editing Mandeep Kaur, Manpreet Singh, Harneet Kaur, Simran Kaur ABSTRACT: Cooperative Editing Systems in real-time allows a virtual team to view and edit a shared document at the same time. The document shared must be synchronized in order to ensure consistency for all the participants. This paper describes the Operational Transformation, the evolution of its techniques, its various applications, major issues, and achievements. In addition, this paper will present working of a platform where two users can edit a code (programming file) at the same time. Index Terms: CodeMirror, code sharing, consistency maintenance, Google Wave, Google Docs, group editors, operational transformation, real-time editing, Web Sockets ———————————————————— 1 INTRODUCTION 1.1 MAIN ISSUES RELATED TO REAL TIME CO- Collaborative editing enables portable professionals to OPERATIVE EDITING share and edit same documents at the same time. Elementally, it is based on operational transformation, that Three inconsistency problems is, it regulates the order of operations according to the Divergence: Contents at all sites in the final document transformed execution order. The idea is to transform are different. received update operation before its execution on a replica Causality-violation: Execution order is different from the of the object. Operational Transformation consists of a cause-effect order. centralized/decentralized integration procedure and a transformation function. Collaborative writing can be E.g., O1 → O3 defined as making changes to one document by a number of persons. The writing can be organized into sub-tasks Intention-violation: The actual effect is different from the assigned to each group member, with the latter part of the intended effect. -

Photos Copied" Box
Our photos have never been as scattered as they are now... Do you know where your photos are? Digital Photo Roundup Checklist www.theswedishorganizer.com Online Storage Edition Let's Play Digital Photo Roundup! Congrats on making the decision to start organizing your digital photos! I know the task can seem daunting, so hopefully this handy checklist will help get your moving in the right direction. LET'S ORGANIZE! To start organizing your digital photos, you must first gather them all into one place, so that you'll be able to sort and edit your collection. Use this checklist to document your family's online storage accounts (i.e. where you have photos saved online), and whether they are copied onto your Master hub (the place where you are saving EVERYTHING). It'll make the gathering process a whole lot easier if you keep a record of what you have already copied and what is still to be done. HERE'S HOW The services in this checklist are categorized, so that you only need to print out what applies to you. If you have an account with the service listed, simply check the "Have Account" box. When you have copied all the photos, check the "Photos Copied" box. Enter your login credentials under the line between the boxes for easy retrieval. If you don't see your favorite service on the list, just add it to one of the blank lines provided after each category. Once you are done, you should find yourself with all your digital images in ONE place, and when you do, check back on the blog for tools to help you with the next step in the organizing process. -
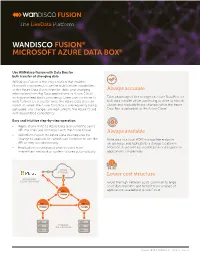
Wandisco Fusion® Microsoft Azure Data Box®
FUSION WANDISCO FUSION® MICROSOFT AZURE DATA BOX® Use WANdisco Fusion with Data Box for bulk transfer of changing data WANdisco Fusion is the only solution that enables Microsoft customers to use the bulk transfer capabilities of the Azure Data Box to transfer static and changing Always accurate information from Big Data applications to Azure Cloud with guaranteed data consistency. Users can continue to Take advantage of the storage on Azure Data Box for write to their local cluster while the Azure Data Box is in bulk data transfer while continuing to write to a local transit so when the Azure Data Box is subsequently being cluster and replicate those changes while the Azure uploaded, any changes are replicated to the Azure Cloud Data Box is uploaded to the Azure Cloud. with guaranteed consistency. Easy and intuitive step-by-step operation • Applications write to Azure Data Box using the same API that they use to interact with the Azure Cloud. Always available • WANdisco Fusion for Azure Data Box requires no change to applications which can continue to use the Write data to a local HDFS-compatible endpoint API as they would normally. on-premises and replicate to a storage location in • Replication is continuous and recovers from Microsoft Azure with no modification or disruption to intermittent network or system failures automatically. applications on-premises. AZURE 2 STORAGE Lower cost structure MICROSOFT 1 3 AZURE DATA BOX Avoid the high network costs common to large scale data transfers and benefit from a range of applications available in Azure Cloud. FUSION FUSION FUSION HADOOP ON-PREMISES Copyright © 2018 WANdisco, Inc. -

Igneous Backup with Microsoft Azure Data Box Executive Overview the Benefits of Cloud Backup, Including Scalability, Accessibility, and Agility, Are Immense
SOLUTION GUIDE Igneous Backup with Microsoft Azure Data Box Executive Overview The benefits of cloud backup, including scalability, accessibility, and agility, are immense. However, significant challenges lie in effectively deploying cloud backups for enterprise. To help enterprises harness the value of cloud backup while overcoming the challenges of massive scale, Igneous Unstructured Data Management as-a-Service and Microsoft Azure Data Box combine to offer an integrated solution that accelerates data migration from network attached storage (NAS) to Microsoft Azure Storage, and manages ongoing replication and tiering to cloud. With backup environments, the challenge of using public cloud is often seeding the initial backup before doing incrementals. Azure Data Box provides an economical way to transport those initial backups (often called “level- 0’s”) into Azure Storage without worrying about network bandwidth between your on-premises environment and Azure Storage. Igneous Unstructured Data Management as-a-Service solution, built for managing file-based backups, provides native integration with Azure Storage, including the Azure Data Box. Together, Igneous and Azure allow you to backup unstructured data stored on your primary network attached storage (NAS) file systems, efficiently move large amounts of data to Azure Storage, and protect and manage your data with tiering and replication to cloud. Microsoft Azure Data Box provides a secure, tamper-resistant method for quick and simple transfer of your data to Azure. Use Azure Data Box service when you want to transfer large amounts of data to Azure but are limited by time, network availability, or costs. Azure Data Box is supported by Igneous as a method to support transfers or initial sync to Azure Storage. -

Chapter 14 This Presentation Covers
Basic Operating Systems Chapter 14 This presentation covers: > Staying Current >Basic Operating Systems Overview > Command Prompts Qualities of a Good Technician “Soft skills” as they are known across many industries are essential Staying Current Benefits of staying current include: >(1) understanding and troubleshooting the latest technologies > (2) recommending upgrades or solutions to customers > (3) saving time troubleshooting (and time is money) > (4) being someone considered for a promotion Staying Current A variety of methods to stay current include: >Subscribe to a magazine or an online magazine > Subscribe to a news list that gives you an update in your email > Join or attend association meetings >Register for and attend a seminar > Attend an online webinar > Take a class > Read books > Talk to your department peers and supervisor Basic Operating Systems Overview Basic Operating Systems > Computers require software to operate >An operating system (OS) is software that coordinates the interaction between hardware and any software applications and the interaction between a user and the computer >An operating system can be a graphical user interface (GUI) or a command line interface, or both > It is responsible for handling file and disk management Popular Operating Systems > Microsoft Windows >Apple macOS > Linux > Chrome OS > Android (mobile) > Apple iOS (mobile) 32- vs 64-bit Operating Systems Windows 7 Editions Windows 10 Editions End-of-Life Concerns > Serious consequences if an operating system or application has reached its