Festos CMS 2.3B Multiple Remote Vulnerabilities
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
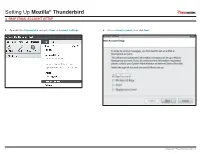
Setting up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP
Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP 1. Open Mozilla Thunderbird and go to Tools -> Account Settings. 2. Choose Email account; then click Next. 1 Copyright © EmailHosting.com LLC Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP (cont.) 3. In the Identity window type your name as you want it to appear on outgoing emails. 4. In the Server Information window select the radio button labeled IMAP. • Then, type your email address in the field labeled Email Address. • Enter imap.emailhosting.com in the field labeled Incoming Server. • Click Next to continue. • Enter smtp.emailhosting.com in the field labeled Outgoing Server. • Click Next to continue. John Smith imap.emailhosting.com [email protected] smtp.emailhosting.com Note: If you have already used Thunderbird in the past the Outgoing Server will not be listed. 2 Copyright © EmailHosting.com LLC Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP (cont.) 5. In the User Names window, the fields should already be filled out correctly. 6. Click Next on the Account Name page to accept the default Account Name. • Confirm that both fields match your EmailHosting username. • In the Congratulations window, verify that all information is correct. • Click Next to continue. • Then click Finish. [email protected] [email protected] [email protected] [email protected] 7. You will be prompted for your password. If you’d like to save your password, make sure Use Password Manager to remember this password is checked before clicking on OK to continue. Note: The field Outgoing Server is only visible during the setup of Mozilla Thunderbird’s first email account. -

Software Management Full Installers Guide
Software Management Full Installers Guide Supported Platforms and Applications | Q1 2020 Software Management Full Installers Guide Release 9.5 | Q1 2020 www.kaseya.com 2 Software Management Full Installers Guide Release 9.5 | Q1 2020 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya’s “Click-Accept” EULATOS as updated from time to time by Kaseya at http://www.kaseya.com/legal.aspx. If Customer does not agree with the Agreement, please do not install, use or purchase any Software and Services from Kaseya as continued use of the Software or Services indicates Customer’s acceptance of the Agreement. www.kaseya.com Software Management Full Installers 3 Guide Release 9.5 | Q1 2020 Contents Installers Available 4 www.kaseya.com 4 Software Management Full Installers Guide Release 9.5 | Q1 2020 Installers Available Title Vendor URL 7-Zip File Archiver (Full Install) for Igor Pavlov http://www.7-zip.org/ Windows Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (Full Install) for Mac Systems, Inc OS X Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (de-DE) (Full Install) Systems, Inc for Windows Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (en-US) (Full Install) Systems, Inc for Windows Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (es-ES) (Full Install) Systems, Inc for Windows -

Instalación Y Administración De Servicios De Correo Electrónico
Servicios de red e internet Instalación y administración de servicios de correo electrónico Raquel Castellanos Crespo Instalación y administración de servicios de correo electrónico Servicios de red e internet Raquel Castellanos Crespo INDICE Características del servicio de correo electrónico Elementos del servicio de correo electrónico -Agentes de correo electrónico. - Servidores de correo electrónico. Open relay y Smart host - Clientes de correo electrónico: entorno-DOS, gráficos y navegadores. - Direcciones, cuentas de correo y servidores DNS - Protocolos y servicios de descarga de correo: SMPT, ESMTP, POP, IMAP. Funcionamiento del servicio de correo electrónico Cuentas de correo, alias y buzones de correo Estructura de mensajes de correo electrónico - Cabecera, cuerpo, MIME Monitorización y registros del servicio de correo electrónico Servicio de correo electrónico vía web Correo seguro - Firma digital y cifrado de mensajes Veracidad del correo - Correo basura ("SPAM”) fraude, engaño, cadenas y virus informáticos 2 Servicios de red e internet | Instalación y administración de servicios de correo electrónico Servicios de red e internet Raquel Castellanos Crespo Características del servicio de correo electrónico Correo electrónico (correo-e, conocido también como e-mail ), es un servicio de red que permite a los usuarios enviar y recibir mensajes y archivos rápidamente (también denominados mensajes electrónicos o cartas electrónicas) mediante sistemas de comunicación electrónicos. Principalmente se usa este nombre para denominar al sistema que provee este servicio en Internet, mediante el protocolo SMTP, aunque por extensión también puede verse aplicado a sistemas análogos que usen otras tecnologías. Por medio de mensajes de correo electrónico se puede enviar, no solamente texto, sino todo tipo de documentos digitales. -

Whitepaper | IBM Domino Application Migration and Decommissioning
WHITEPAPER IBM Domino Application Migration and Decomissioning 1. Migration vs. Decommissioning As outlined above, an application migration can be very time-consuming - and it’s more likely to be than not to IBM Domino has been around for decades. Mid-sized to be. Therefore, the migration cannot be expected to be very large companies have built hundreds and thousands of completed short-term. In addition, it typically involves huge applications around IBM Domino that support their business financial investments. If the information that the application processes; many of those applications are business critical, maintains needs to be retained, maybe for a long period of e.g. because they store information that is subject to legal time, e.g. due to legal requirements, how should a company requirements. deal with this situation? But the IT world keeps changing. New technologies arise The answer to this question is »decommissioning«. When an nearly every day. Companies need to continuously review application is decommissioned, the application and its logic their IT strategy in order not to fall behind. are discarded whereas the data is maintained and kept in a Regarding IBM’s Domino offering there are quite a few way so that it is still accessible – at least for reading – even reasons why companies reassess their investments into that if the application that was used to create it is not available technology. Many of those companies already have decided anymore. or are in the process of deciding to move away from IBM Domino. They are looking at Enterprise Content Manage- ment (ECM) systems like Alfresco, OpenText Documentum, For the purpose of this document, migration is only OpenText, SharePoint etc. -

Mailstore Server 7 Technical Specifications
MailStore Server ® 7 Technical Specifications MailStore Server The Standard in Email Archiving Businesses of all sizes can benefit from the legal, technical, and financial advantages of modern and secure email archiving with MailStore Server. MailStore Server 7 - Technical Specifications Archiving Supported Email Servers and Internet Mailboxes General Features Microsoft Exchange Server 2003, 2007, and 2010 (including Windows Small Business Server) No changes made to email servers and emails Hosted Exchange No administrative access to Microsoft O(ce 365 (Exchange Online) the email server required MDaemon Messaging Server Folder structure of mailboxes IceWarp Mail Server is imported into the archive Kerio Connect Size of mailboxes can be IMAP4-compatible email server reduced through rule-based POP3-compatible email server deletion Internet and webmail inboxes such as Gmail or GMX (via IMAP or Emails are archived in a MIME- POP3) compatible manner with no loss of information Archiving Methods Full archiving of all emails as they are sent and received Archiving of existing mailboxes and files (manual or scheduled) Archiving of public folders (manual or scheduled) Supported Email Clients Microsoft Outlook 2000, XP, 2003, 2007, 2010 Microsoft Outlook Express 6.0 Microsoft Windows Mail Microsoft Windows Live Mail Mozilla Thunderbird and SeaMonkey Supported Email File Formats RFC822/MIME-compatible email files (.eml) PST files MSG files (Outlook format) MBOX files Archiving Via MailStore Proxy Server Companies without an email server can automatically archive all incoming and outgoing email correspondence via the MailStore proxy server (SMTP and POP3). 2 MailStore Server 7 - Technical Specifications User Access to the Archive Supported Access Methods General Features MailStore Add-in for Microsoft Outlook MailStore users can access their archives using a convenient add-in for Stub files and other technolo- Microsoft Outlook XP, 2003, 2007, and 2010 (32-bit and 64-bit). -

Mozilla and Software Freedom Dwaraka Nath Arun Prakash Harvish Sekar
Mozilla And Software Freedom Dwaraka Nath Arun Prakash Harvish Sekar 17th September 2011, SFD Chennai. About Mozilla •Mozilla is a global community of volunteers, contributors and like – minded people who work towards the same goal Openness, Innovation and Opportunity of the Web and associated Software •Formed on 23rd February of 1998 by Netscape Communications as Mozilla Organization •Mozilla Foundation launched on July 15, 2003. What We Do •We are a non – profit organization who see success with People than with Share and Stake holders. •We try to achieve our goal by building and promoting software like Firefox and movements like Drumbeat •We want to see the Power and potential of Internet and want to see it thrive for everyone, everywhere. Mozilla’s Projects • Mozilla’s Projects have been one of the most successful open—source movements in the recent years. • Some of them are Firefox Internet Browser for Desktop and Mobile Platforms, Thunderbird Email Client, SkSeamonkey (formerl y k nown as th e M ozill a app lica tion suite), Lightning and Sunbird—Calendaring applications and Camino. • We also promote WebFWD and Rainbow as a part of the Mozilla Labs Initiative. Not to mention the CouchDB, ZK, Gecko and the XUL Runner. The Firefox • World’s most advanced and secure Internet Browser. • Accounts for more than a quarter of world’s browser market share[1] • Some of the cool features in Firefox include Tabbed Browsing, Tabbed Browsing, Countless extensions and addons, Built—in RSS, Firefox Sync, Panorama and the awesome bar ☺ • Above all, its free ! [1] – Source : Wikipedia -http://en.wikipedia.org/wiki/Usage_share_of_web_browsers as on 16th September 2011 Firefox – Tech Specs • Crash protection support across multiple OS for Silverlight, Flash, QuickTime plugins • Full WebGL, WebM and HTML5 support (for controls and the new parser) and partial support for CSS Transitions. -

Zimbra Collaboration Suite with Thunderbird - Zimbra :: Wiki
Accessing Zimbra Collaboration Suite with Thunderbird - Zimbra :: Wiki http://wiki.zimbra.com/wiki/Accessing_Zimbra_Collaboration_Suite_w... Zimbra Forums | Blog | Contact Us | About Zimbra :: the leader in next-generation messaging and collaboration Community Forums Wiki Gallery Blog Docs Products Accessing Zimbra Collaboration Suite with Thunderbird From Zimbra :: Wiki With the Zimbra Collaboration Suite, you are able to access your email using Mozilla Thunderbird messaging and collaboration client. Optionally, you can Article view your Zimbra Calendar using the separate Lightning Add-on for Information Thunderbird. This guide shows you how to access to your Zimbra Mail and Calendar using This article applies to the following Thunderbird 2 with the Lightning 0.5 Add-On. ZCS versions. ZCS 5.0 Contents ZCS 4.5 1 Before You Begin 2 Accessing your Zimbra Mail with Thunderbird 2.1 To create a new account in Thunderbird 3 Changing Your Server Settings 3.1 To change the secure connection settings for your incoming mail server 3.2 To change the secure connection settings for your outgoing mail server 3.3 To add an outgoing server to your Zimbra email account 4 Viewing your Zimbra Calendar using Lightning 4.1 To view your Zimbra Calendar using Lightning 4.1.1 Accessing your Zimbra Calendar using Lightning with CalDAV (Only works with ZCS 5.0+ and Lightning 0.8+) 5 Feature Differences When Using Thunderbird Before You Begin 1 of 11 30/8/2010 2:36 PM Accessing Zimbra Collaboration Suite with Thunderbird - Zimbra :: Wiki http://wiki.zimbra.com/wiki/Accessing_Zimbra_Collaboration_Suite_w... This guide assumes that you have already installed Thunderbird 2 and, optionally, have already installed the Lightning Add-on. -

Reply to Pre Bid Queries RFP 032020 - Migration and Maintenance of Bank's E-Mail Messaging Solution on Public Cloud with Archival Facility & E-Mail Security
Reply to pre Bid queries RFP 032020 - Migration and Maintenance of Bank's E-Mail Messaging Solution on Public Cloud with Archival Facility & E-Mail Security Sr Page # Point/Clause # Clarification point as stated in the tender document Comment/ Suggestions Bank's Reply 1 1 1. Invitation to the Tender This is to inform that Bank of Maharashtra (BoM) invites sealed Is bank open to On premises solution RFP Clause is self-explanatory. tenders for Technical bid and Commercial bid from eligible bidders to or the vendor has to go for Public migrate and maintain the Bank’s existing E- Mail Messaging Solution Cloud based solution on Public Cloud with Archival Facility & Gateway Level E-Mail Security Controls as per the requirements mentioned in this RFP 2 1 Annexure 10: Commercial a. Technical Bill of Material Active mailbox are mentioned as 8000 Bank requires the active mailboxes to be migrated and Bill of Material and then there are other mailboxes like remaining count of email IDs to be created in the proposed Designation Based, Vendor etc.: - solution. Please refer Clause 4.3 Project Scope for more Please reconfirm all the 16000 details. mailboxes to be migrated or only active 8000 mailboxes to be migrated. Any specific reason for bifurcation 3 8 Important Price of Tender copy We would like to inform you that Exemption will be allowed only after sharing the credential information Rs.15,000/- + Rs. 2,700/- (GST) = we are MSME registred vendor and documents and further verification by the Bank. regarding Bid Rs.17,700/- Bid Security Deposit as per MSME guide lines the tender submission > Price (EMD) document fee and earnest money of Tender copy & Rs.50,00,000/- deposit is exempted to MSE Bid Security Deposit vendor, would request you to (EMD) accept the MSME registration Certificate against tender copy fee and EMD Bid Security. -

3. Wählen Sie Im Mozilla-Browser Den Menüpunkt "Edit" ("Bearbeiten"), Darunter "Preferences..." ("Einstellungen...")
3. Wählen Sie im Mozilla-Browser den Menüpunkt "Edit" ("Bearbeiten"), darunter "Preferences..." ("Einstellungen..."). Dort öffnen Sie im der Kategorie "Appearance" ("Erscheinungsbild") das Einstellungen-Panel "Languages/Content" ("Sprachen/Inhalt"). 4. Dort wählen Sie die Sprache "Deutsch" aus der oberen Liste, möglichst auch "Inhalte: Österreich" aus der unteren Liste (um z.B. bei "Hilfe" > "Release Notes" auf deren deutsche Version auf mozilla.kairo.at geschickt zu werden). 5. Klicken Sie OK, beenden Sie Mozilla und starten Sie das Programm neu (dazu muss unter Windows auch der eventuell aktivierte Schnellstart beendet werden!). Tun Sie dies, so wird die Oberfläche in deutscher Sprache angezeigt. 6. Wenn Sie schon bisher eine deutsche Version verwendet haben, kann es vorkommen, dass nur Teile übersetzt erscheinen. In diesem Fall stellen Sie mit Hilfe der Punkte 3-5 nochmals auf Englisch zurück und dann wieder auf Deutsch. Dann sollte das Problem behoben sein. Seamonkey.doc Page 41 of 41 Installationsanleitung: Language Packs im XPI-Format ab Mozilla 1.7 Warnung: Seit Mozilla 1.7 können XPI-Pakete nur mehr von erlaubten Webseiten installiert werden, daher schlägt die Installation von unserer Seite bei einer frischen Installation fehl. Bitte lesen Sie unten stehende Vorbereitungsschritte. Stellen Sie sicher, dass die Einstellung 'Software-Installation' unter den Erweiterten Einstellungen aktiviert ist, sonst lässt sich jedenfalls kein XPI- Paket installieren! Vorbereitung: Sie müssen entweder Installationen von Mozilla deutsch erlauben oder das Paket lokal herunterladen: * Installationen von Mozilla deutsch erlauben: Geben Sie "about:config" in die Adressleiste ein. Suchen Sie in der erscheinenden Liste nach der Eigenschaft "xpinstall.whitelist.add" (fast ganz unten in der alphabetischen Liste). -
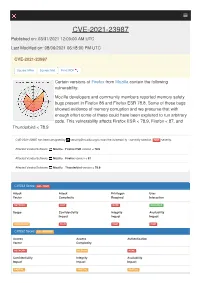
CVE-2021-23987 Published On: 03/31/2021 12:00:00 AM UTC
CVE-2021-23987 Published on: 03/31/2021 12:00:00 AM UTC Last Modified on: 08/06/2021 06:18:00 PM UTC CVE-2021-23987 Source: Mitre Source: Nist Print: PDF Certain versions of Firefox from Mozilla contain the following vulnerability: Mozilla developers and community members reported memory safety bugs present in Firefox 86 and Firefox ESR 78.8. Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code. This vulnerability affects Firefox ESR < 78.9, Firefox < 87, and Thunderbird < 78.9. CVE-2021-23987 has been assigned by [email protected] to track the vulnerability - currently rated as HIGH severity. Affected Vendor/Software: Mozilla - Firefox ESR version < 78.9 Affected Vendor/Software: Mozilla - Firefox version < 87 Affected Vendor/Software: Mozilla - Thunderbird version < 78.9 CVSS3 Score: 8.8 - HIGH Attack Attack Privileges User Vector Complexity Required Interaction NETWORK LOW NONE REQUIRED Scope Confidentiality Integrity Availability Impact Impact Impact UNCHANGED HIGH HIGH HIGH CVSS2 Score: 6.8 - MEDIUM Access Access Authentication Vector Complexity NETWORK MEDIUM NONE Confidentiality Integrity Availability Impact Impact Impact PARTIAL PARTIAL PARTIAL CVE References Description Tags Link Mozilla Firefox: Multiple vulnerabilities (GLSA 202104- security.gentoo.org GENTOO GLSA-202104-10 10) — Gentoo security text/html Security Vulnerabilities fixed in Thunderbird 78.9 — www.mozilla.org MISC www.mozilla.org/security/advisories/mfsa2021-12/ -

Migrationsleitfaden
Migrationsleitfaden Leitfaden für die Migration der Basissoftwarekomponenten auf Server- und Arbeitsplatz-Systemen www.kbst.bund.de 2. überarbeitete Auflage Koordinierungs- und Beratungsstelle der Bundesregierung für Informationstechnik in der Bundesverwaltung Schriftenreihe der KBSt ISSN 0179-7263 Band 72 März 2005 Schriftenreihe der KBSt Band 72 ISSN 0179 - 7263 Dieser Band wurde erstellt von der KBSt im Bundesministerium des Innern (BMI) in Zusammenarbeit mit dem Bundesamt für Sicherheit in der Informationstechnik (BSI), dem Bundesverwaltungsamt (BVA) und der EDS Business Solutions GmbH Redaktion: EDS Business Solutions GmbH, Berlin Nachdruck, auch auszugsweise, ist genehmigungspflichtig Interessenten erhalten die derzeit lieferbaren Veröffentlichungen der KBSt und weiterführende Informationen zu den Dokumenten beim Bundesministerium des Innern Referat IT 2 (KBSt) 11014 Berlin Tel.: +49 (0) 1888 681 - 2312 Fax.: +49 (0) 1888 681 - 52312 Homepage der KBSt: www.kbst.bund.de mailto: [email protected] Migrationsleitfaden Leitfaden für die Migration der Basissoftwarekomponenten auf Server- und Arbeitsplatz-Systemen 2. überarbeitete Auflage Berlin, März 2005 Herausgegeben vom Bundesministerium des Innern INHALTSVERZEICHNIS 1 Einleitung ........................................................................ 9 1.1 Über das Vorhaben 9 1.2 Über diesen Leitfaden 10 1.3 Hinweise zur Benutzung des Leitfadens 12 1.4 Hinweise an die Entscheider 14 1.4.1 Grundsätzliche Empfehlungen 14 1.4.2 Fortführende und ablösende Migration 15 1.4.3 -

Using Mozilla® Thunderbird 1.0
Using Mozilla® Thunderbird 1.0 Technical Manual: User Guide Document Updated: 1/06 The Mozilla Thunderbird Window 4. Enter a description of your message in the Menu Bar Subject box. Mail Toolbar Search Bar 5. Enter the text of your message in the Message List message body. 6. When you are Mail Folders Pane ready to send your message, click the Send Message Pane button. Status Bar Saving and Editing a Draft Receiving Messages If you do not have time to finish composing your message, you can save it as a draft. To manually check for incoming mail, click the Get Mail • To save a message as a draft, click the Save button. The button. New messages will appear in the Message List. message will be saved in the Drafts folder. Opening and Closing a Message • To edit a draft, click the Drafts folder, located in the Mail Folders pane. Double-click the draft to open and begin editing • To open a message in its own window, double-click the the message. message name, as it appears in the Message List. • To close a message, select File / Close or click the Close Replying to a Message button, located in the upper right corner of the window. 1. Select or open the message to which you want to reply. Printing a Message 2. Click the Reply button, or click the Reply All 1. Select or open the message you want to print. button to reply to all message recipients. 2. Click the Print button. 3. Enter your reply message in the message body.