Setting up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Install and Configure Cisco Anyconnect VPN
Install and Configure Cisco AnyConnect VPN PURPOSE: • Installing and configuring Cisco AnyConnect • Enabling and Disabling Cisco AnyConnect VERSION SUPPORTED: 4.5.02033 HOW TO INSTALL AND CONFIGURE CISCO ANYCONNECT VPN FOR WINDOWS: From the desktop, open up a web browser (Google Chrome, Mozilla Firefox, Microsoft Edge, or Internet Explorer). Note: Google Chrome will be used in this example. Type in vpn01.cu.edu into the address bar. You will reach a login page, login using your CU System Username and Password. Contact UIS Call: 303-860-4357 Email:[email protected] Click on the AnyConnect button on the bottom of the list on the left-hand side. Select the “Start AnyConnect” button on that page. It will then load a few items, after it finishes click the blue link for “AnyConnect VPN” Contact UIS Call: 303-860-4357 Email:[email protected] This will download the client in the web browser, in Google Chrome this shows up on the bottom section of the page, but other browsers may place the download in a different location. If you cannot find the download, it should go to the Downloads folder within Windows. Contact UIS Call: 303-860-4357 Email:[email protected] We will then run this download by clicking on it in Chrome. Other browsers may offer a “Run” option instead, which acts the same. It will then open up an installer. Click “Next.” Select the “I accept the terms in the License Agreement” button. Click “Next.” Contact UIS Call: 303-860-4357 Email:[email protected] Select “Install”, this will require the username and password you use to login to your personal computer. -

Machine Learning in the Browser
Machine Learning in the Browser The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:38811507 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA Machine Learning in the Browser a thesis presented by Tomas Reimers to The Department of Computer Science in partial fulfillment of the requirements for the degree of Bachelor of Arts in the subject of Computer Science Harvard University Cambridge, Massachusetts March 2017 Contents 1 Introduction 3 1.1 Background . .3 1.2 Motivation . .4 1.2.1 Privacy . .4 1.2.2 Unavailable Server . .4 1.2.3 Simple, Self-Contained Demos . .5 1.3 Challenges . .5 1.3.1 Performance . .5 1.3.2 Poor Generality . .7 1.3.3 Manual Implementation in JavaScript . .7 2 The TensorFlow Architecture 7 2.1 TensorFlow's API . .7 2.2 TensorFlow's Implementation . .9 2.3 Portability . .9 3 Compiling TensorFlow into JavaScript 10 3.1 Motivation to Compile . 10 3.2 Background on Emscripten . 10 3.2.1 Build Process . 12 3.2.2 Dependencies . 12 3.2.3 Bitness Assumptions . 13 3.2.4 Concurrency Model . 13 3.3 Experiences . 14 4 Results 15 4.1 Benchmarks . 15 4.2 Library Size . 16 4.3 WebAssembly . 17 5 Developer Experience 17 5.1 Universal Graph Runner . -

Replication: Why We Still Can't Browse in Peace
Replication: Why We Still Can’t Browse in Peace: On the Uniqueness and Reidentifiability of Web Browsing Histories Sarah Bird, Ilana Segall, and Martin Lopatka, Mozilla https://www.usenix.org/conference/soups2020/presentation/bird This paper is included in the Proceedings of the Sixteenth Symposium on Usable Privacy and Security. August 10–11, 2020 978-1-939133-16-8 Open access to the Proceedings of the Sixteenth Symposium on Usable Privacy and Security is sponsored by USENIX. Replication: Why We Still Can’t Browse in Peace: On the Uniqueness and Reidentifiability of Web Browsing Histories Sarah Bird Ilana Segall Martin Lopatka Mozilla Mozilla Mozilla Abstract This work seeks to reproduce the findings of Olejnik, Castel- We examine the threat to individuals’ privacy based on the luccia, and Janc [48] regarding the leakage of private infor- feasibility of reidentifying users through distinctive profiles mation when users browse the web. The reach of large-scale of their browsing history visible to websites and third par- providers of analytics and advertisement services into the ties. This work replicates and extends the 2012 paper Why overall set of web properties shows a continued increase in Johnny Can’t Browse in Peace: On the Uniqueness of Web visibility [64] by such parties across a plurality of web prop- Browsing History Patterns [48]. The original work demon- erties. This makes the threat of history-based profiling even strated that browsing profiles are highly distinctive and stable. more tangible and urgent now than when originally proposed. We reproduce those results and extend the original work to detail the privacy risk posed by the aggregation of browsing 2 Background and related work histories. -
![Browser Versions Carry 10.5 Bits of Identifying Information on Average [Forthcoming Blog Post]](https://docslib.b-cdn.net/cover/0737/browser-versions-carry-10-5-bits-of-identifying-information-on-average-forthcoming-blog-post-190737.webp)
Browser Versions Carry 10.5 Bits of Identifying Information on Average [Forthcoming Blog Post]
Browser versions carry 10.5 bits of identifying information on average [forthcoming blog post] Technical Analysis by Peter Eckersley This is part 3 of a series of posts on user tracking on the modern web. You can also read part 1 and part 2. Whenever you visit a web page, your browser sends a "User Agent" header to the website saying what precise operating system and browser you are using. We recently ran an experiment to see to what extent this information could be used to track people (for instance, if someone deletes their browser cookies, would the User Agent, alone or in combination with some other detail, be enough to re-create their old cookie?). Our experiment to date has shown that the browser User Agent string usually carries 5-15 bits of identifying information (about 10.5 bits on average). That means that on average, only one person in about 1,500 (210.5) will have the same User Agent as you. On its own, that isn't enough to recreate cookies and track people perfectly, but in combination with another detail like an IP address, geolocation to a particular ZIP code, or having an uncommon browser plugin installed, the User Agent string becomes a real privacy problem. User Agents: An Example of Browser Characteristics Doubling As Tracking Tools When we analyse the privacy of web users, we usually focus on user accounts, cookies, and IP addresses, because those are the usual means by which a request to a web server can be associated with other requests and/or linked back to an individual human being, computer, or local network. -

Marcia Knous: My Name Is Marcia Knous
Olivia Ryan: Can you just state your name? Marcia Knous: My name is Marcia Knous. OR: Just give us your general background. How did you come to work at Mozilla and what do you do for Mozilla now? MK: Basically, I started with Mozilla back in the Netscape days. I started working with Mozilla.org shortly after AOL acquired Netscape which I believe was in like the ’99- 2000 timeframe. I started working at Netscape and then in one capacity in HR shortly after I moved working with Mitchell as part of my shared responsibility, I worked for Mozilla.org and sustaining engineering to sustain the communicator legacy code so I supported them administratively. That’s basically what I did for Mozilla. I did a lot of I guess what you kind of call of blue activities where we have a process whereby people get access to our CVS repository so I was the gatekeeper for all the CVS forms and handle all the bugs that were related to CVS requests, that kind of thing. Right now at Mozilla, I do quality assurance and I run both our domestic online store as well as our international store where we sell all of our Mozilla gear. Tom Scheinfeldt: Are you working generally alone in small groups? In large groups? How do you relate to other people working on the project? MK: Well, it’s a rather interesting project. My capacity as a QA person, we basically relate with the community quite a bit because we have a very small internal QA organization. -
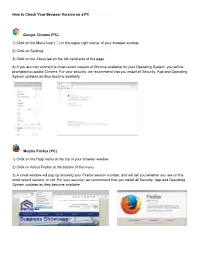
How to Check Your Browser Version on a PC
How to Check Your Browser Version on a PC Google Chrome (PC) 1) Click on the Menu Icon ( ) in the upper right corner of your browser window. 2) Click on Settings 3) Click on the About tab on the left-hand side of the page. 4) If you are not running the most recent version of Chrome available for your Operating System, you will be prompted to update Chrome. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Mozilla Firefox (PC) 1) Click on the Help menu at the top of your browser window. 2) Click on About Firefox at the bottom of the menu. 3) A small window will pop up showing your Firefox version number, and will tell you whether you are on the most recent version, or not. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Internet Explorer (PC) 1) Click on the Gear Icon at the top of your browser window. 2) Click on the About Internet Explorer option. 3) A window will pop up showing you your Internet Explorer version. 4) If you are using Internet Explorer 9 or 10, you will need to make sure that you have TLS 1.2 enabled by: A) Clicking on the Gear Icon again. B) Click on Internet Options. C) Click on the Advanced Tab and scroll down to the option titled “Use TLS 1.2”. (This should be found at the bottome of the list of options.) The box next to this should be checked. -

Functional HCL Notes Email Archiving Solution
AM ™ ArchiveMail DATASHEET Functional HCL Notes™ email archiving solution Key In Detail on Introducti Characteristics Benefits For the Users: Continuous growth in data volumes related to messaging and the practical limits imposed by Notes database architecture make email archiving systems essential. M Improved productivity due to automatic management of archive. COOPERTEAM’s Archive Mail™ is a functional archiving solution which responds to the M needs of administrators by allowing them to manage archiving policies efficiently and Access to archived documents from automatically, whilst still guaranteeing their users access to their documents and the Notes client, iNotes and mobile attached files. devices. Archive Mail™ automates the archiving of messages, calendar entries, tasks and contacts M Multi-criteria searching available for to one archive per year, hosted on either dedicated or shared function servers. Archiving both server & workstation. policies can be based on document ageing criteria. In addition, the archive process can be triggered when the mail database exceeds its For the Administrators: threshold (quota), or manually by users after selecting documents to be archived. M Optimization of the Domino Archive Mail™ allows administrators to manage multiple archive databases and easily infrastructure. implement ILM (Information Lifecycle Management) policies, and to correctly align the M Align messaging storage costs, value storage costs of the archived documents with their value to the business. for the business and quota policies. M Once Archive Mail™ is implemented, documents that meet the configured ageing Automated and centralised parameters for archiving are transferred to an archive database at a frequency predeter- management of archiving mined by their profile administrator. -

Zimbra Tips & Tricks
TOP ZIMBRA 15 TIPS & TRICKS This guide brings you the top 15 Zimbra Tips & Tricks to help you save time while working in Zimbra. If you find these Tips & Tricks helpful, you may also like our tutorial demos: The top 15 Zimbra Tips & Tricks (based on clicks on Zimbra’s “Did You Know?” blog) are: Throughout this guide, look for pop-up boxes highlighting quick tips Email Tips and Tricks and facts. 1 Searching in Zimbra TIP: Skip ahead to any 2 Importing Into and Exporting From Zimbra section of the 15 Tips & 3 Changing Your Zimbra Preferences Tricks by clicking on the 4 Changing Your Zimbra Theme titles to the right. 5 Setting Zimbra Email and SMS (text) Reminders 6 Enabling Zimbra’s Mandatory Spellcheck 7 Sorting Email 8 Creating an Appointment with the Mini Calendar 9 Creating an Email Distribution List or Contact Group 10 Opening an Email in a Separate Window 11 Turning on Zimbra’s Activity Stream 12 Switching from Conversation View to Message View 13 Sharing Your Zimbra Calendar Outside Your Organization 14 Sharing in Zimbra 15 Enabling Zimbra Two-Factor Authentication 1 Searching in Zimbra There are many great and easy ways to search in Zimbra: • Quick keyword search • Complex search • Right-click search Quick Keyword Search You can do a quick search using keywords like from, to, in, etc. Click here to see all search keywords. How much time do you spend searching To search by keyword: for a specific email? keyword: search word(s) Searches are easy and fast in Zimbra. Search Examples: your entire Zimbra • Find all email received from Mark (all email with “Mark” in the From account, including attachments, in seconds. -

The History of Spam Timeline of Events and Notable Occurrences in the Advance of Spam
The History of Spam Timeline of events and notable occurrences in the advance of spam July 2014 The History of Spam The growth of unsolicited e-mail imposes increasing costs on networks and causes considerable aggravation on the part of e-mail recipients. The history of spam is one that is closely tied to the history and evolution of the Internet itself. 1971 RFC 733: Mail Specifications 1978 First email spam was sent out to users of ARPANET – it was an ad for a presentation by Digital Equipment Corporation (DEC) 1984 Domain Name System (DNS) introduced 1986 Eric Thomas develops first commercial mailing list program called LISTSERV 1988 First know email Chain letter sent 1988 “Spamming” starts as prank by participants in multi-user dungeon games by MUDers (Multi User Dungeon) to fill rivals accounts with unwanted electronic junk mail. 1990 ARPANET terminates 1993 First use of the term spam was for a post from USENET by Richard Depew to news.admin.policy, which was the result of a bug in a software program that caused 200 messages to go out to the news group. The term “spam” itself was thought to have come from the spam skit by Monty Python's Flying Circus. In the sketch, a restaurant serves all its food with lots of spam, and the waitress repeats the word several times in describing how much spam is in the items. When she does this, a group of Vikings in the corner start a song: "Spam, spam, spam, spam, spam, spam, spam, spam, lovely spam! Wonderful spam!" Until told to shut up. -

Guest Artist Agreement
Artists Agreement Unitarian Universalist Congregation of Phoenix 4027 E. Lincoln Drive, Paradise Valley, AZ 85253 Phone: 602-840-8400 Email: [email protected] The Sanctuary Art Team of the Unitarian Universalist Congregation of Phoenix (UUCP) welcomes you. We are pleased that you are participating in our art exhibit. The following guidelines and liability agreement should be helpful to you in preparing for installation of your artwork. 1) All works selected for exhibit will be displayed in the Sanctuary or Hall in spaces reserved for that purpose. 2) An art inventory should be completed before arrival and sent to the email above or as directed. It MUST be completed when the art is delivered to UUCP. Artists must provide the following information: Artist's Name, Title of Work, Medium, Dimensions, and Sale Price or NFS (See inventory form). 3) All work must be ready for hanging. Any work over 600 square inches requiring protective covering must be covered in Plexiglas (NOT glass). 4) All works must remain on display until the termination of the show unless previously arranged with the Sanctuary Art Team. At the close of the show, the lender/artist agrees to remove the pieces on exhibit or arrange for their removal. Any object remaining in the Sanctuary for 30 days following the scheduled close of the show will be handled at the discretion of the Sanctuary Art Team. 5) Each object displayed will be exhibited in such manner as the Sanctuary Art Team decides. 6) The Sanctuary Art Team reserves the right to select and/or reject works, bearing in mind that the Sanctuary is not a conventional gallery and the selected works must be appropriate for all congregational activities. -

Monthly Worship Themes What Does It Mean to Be a People Of
2 Begin Your Journey Here Sunday Worship Monthly Worship Themes What does it mean to be a people of... Welcome to UUCP! This is a religious community September Covenant Welcoming all as we Rev. Susan October Freedom Share our Journeys Frederick-Gray Grow in Spirit November Gratitude Together work to Advance Justice December Tradition The best way to see, feel and get to know this community January Truth is through Sunday morning services. Each month we February Love explore a theme in depth. Our themes challenge us to grow in meaning, build connections across diversities and March Hope make our world a better place. April Service May Peace Service times: May – September 13: 10:30 AM June Strength September 20 – April 17: 9:30 AM and 11:15 AM July/August Spirituality Starting Point Community Nights Are you new to UUCP? Do you have questions Break Bread and Make Friends at UUCP. Community about UUCP and Unitarian Universalism? Nights are a time of fellowship and community building Starting Point is an informal program for all ages. We provide the main dish with a vegetarian especially for you! Meet a representative from option and one side. Just bring your appetite, enthusi- the Membership Committee by the Starting asm, and a side dish or dessert to share if able. You are Point sign in the front lobby any second Sunday of the also welcome to bring a sack supper if you prefer. month. You don’t have to sign up. Just show up! Chalice Kids is a program for children that begins right In twenty to thirty minutes, we will answer questions and after the meal at 6:30 PM. -
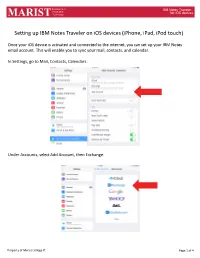
Setting up IBM Notes Traveler on Ios Devices (Iphone, Ipad, Ipod Touch)
Department of IBM Notes Traveler Information for iOS devices MARIST Technology Setting up IBM Notes Traveler on iOS devices (iPhone, iPad, iPod touch) Once your iOS device is activated and connected to the internet, you can set up your IBM Notes email account. This will enable you to sync your mail, contacts, and calendar. In Settings, go to Mail, Contacts, Calendars. Under Accounts, select Add Account, then Exchange. Property of Marist College IT Page 1 of 4 Department of IBM Notes Traveler Information for iOS devices MARIST Technology The Exchange window will display. In the Email field, enter your Marist email address. In the Password field, enter your IBM iNotes password (as you would log in to notes.marist.edu). In the Description field, type “Marist” (without quotation marks). Press “Next” in the upper right corner of the window. The window will expand. In the Server field type in “traveler.notes.marist.edu/traveler” (without quotation marks). In the Username field enter your iNotes username (firstname.lastname). Leave the Domain field blank. Press “Next” in the upper right corner of the window. Information Technology Property of Marist College IT Page 2 of 4 Department of IBM Notes Traveler MARIST Your account will be verified. The next screen displays the Notes data items that will Sync. Slide to the left any item you do not wish to sync, select Save. Information Technology for iOS devices Information Technology for iOS devices The Exchange Account will be created and you will be returned to Settings. Change the ‘Mail Days to Sync’ to your preference.