Browser Versions Carry 10.5 Bits of Identifying Information on Average [Forthcoming Blog Post]
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IN-BROWSER BLITZ LITERATURE REVIEWS 1 Submitted to Meta
IN-BROWSER BLITZ LITERATURE REVIEWS 1 Submitted to Meta-Psychology. Participate in open peer review by commenting through hypothes.is directly on this preprint. The full editorial process of all articles under review at Meta-Psychology can be found following this link: https://tinyurl.com/mp-submissions You will find this preprint by searching for the first author's name. Writing a Psychological Blitz Literature Review with Nothing but a Browser Bogdan Cocoş1 1Department of Psychology, University of Bucharest Author Note Correspondence regarding this article should be addressed to Bogdan Cocoş, 90 Panduri Road, Sector 5, 050663, Bucharest, Romania. E-mail: [email protected] https://orcid.org/0000-0003-4098-7551 IN-BROWSER BLITZ LITERATURE REVIEWS 2 Abstract The ways so far of writing literature reviews represent valid, but not sufficient, landmarks, connected to the current technological context. In this sense, this article proposes a research method called blitz literature review, as a way to quickly, transparently, and repeatably consult key references in a particular area of interest, seen as a network composed of elements that are indispensable to such a process. The tutorial consists of six steps explained in detail, easy to follow and reproduce, accompanied by publicly available supplementary material. Finally, the possible implications of this research method are discussed, being brought to the fore a general recommendation regarding the optimization of the citizens’ involvement in the efforts and approaches of open scientific research. Keywords: blitz literature review, open access, open science, research methods IN-BROWSER BLITZ LITERATURE REVIEWS 3 Writing a Psychological Blitz Literature Review with Nothing but a Browser Context The term “blitz literature review” refers to an adaptation of the concept of literature review. -

Install and Configure Cisco Anyconnect VPN
Install and Configure Cisco AnyConnect VPN PURPOSE: • Installing and configuring Cisco AnyConnect • Enabling and Disabling Cisco AnyConnect VERSION SUPPORTED: 4.5.02033 HOW TO INSTALL AND CONFIGURE CISCO ANYCONNECT VPN FOR WINDOWS: From the desktop, open up a web browser (Google Chrome, Mozilla Firefox, Microsoft Edge, or Internet Explorer). Note: Google Chrome will be used in this example. Type in vpn01.cu.edu into the address bar. You will reach a login page, login using your CU System Username and Password. Contact UIS Call: 303-860-4357 Email:[email protected] Click on the AnyConnect button on the bottom of the list on the left-hand side. Select the “Start AnyConnect” button on that page. It will then load a few items, after it finishes click the blue link for “AnyConnect VPN” Contact UIS Call: 303-860-4357 Email:[email protected] This will download the client in the web browser, in Google Chrome this shows up on the bottom section of the page, but other browsers may place the download in a different location. If you cannot find the download, it should go to the Downloads folder within Windows. Contact UIS Call: 303-860-4357 Email:[email protected] We will then run this download by clicking on it in Chrome. Other browsers may offer a “Run” option instead, which acts the same. It will then open up an installer. Click “Next.” Select the “I accept the terms in the License Agreement” button. Click “Next.” Contact UIS Call: 303-860-4357 Email:[email protected] Select “Install”, this will require the username and password you use to login to your personal computer. -

Machine Learning in the Browser
Machine Learning in the Browser The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:38811507 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA Machine Learning in the Browser a thesis presented by Tomas Reimers to The Department of Computer Science in partial fulfillment of the requirements for the degree of Bachelor of Arts in the subject of Computer Science Harvard University Cambridge, Massachusetts March 2017 Contents 1 Introduction 3 1.1 Background . .3 1.2 Motivation . .4 1.2.1 Privacy . .4 1.2.2 Unavailable Server . .4 1.2.3 Simple, Self-Contained Demos . .5 1.3 Challenges . .5 1.3.1 Performance . .5 1.3.2 Poor Generality . .7 1.3.3 Manual Implementation in JavaScript . .7 2 The TensorFlow Architecture 7 2.1 TensorFlow's API . .7 2.2 TensorFlow's Implementation . .9 2.3 Portability . .9 3 Compiling TensorFlow into JavaScript 10 3.1 Motivation to Compile . 10 3.2 Background on Emscripten . 10 3.2.1 Build Process . 12 3.2.2 Dependencies . 12 3.2.3 Bitness Assumptions . 13 3.2.4 Concurrency Model . 13 3.3 Experiences . 14 4 Results 15 4.1 Benchmarks . 15 4.2 Library Size . 16 4.3 WebAssembly . 17 5 Developer Experience 17 5.1 Universal Graph Runner . -

Replication: Why We Still Can't Browse in Peace
Replication: Why We Still Can’t Browse in Peace: On the Uniqueness and Reidentifiability of Web Browsing Histories Sarah Bird, Ilana Segall, and Martin Lopatka, Mozilla https://www.usenix.org/conference/soups2020/presentation/bird This paper is included in the Proceedings of the Sixteenth Symposium on Usable Privacy and Security. August 10–11, 2020 978-1-939133-16-8 Open access to the Proceedings of the Sixteenth Symposium on Usable Privacy and Security is sponsored by USENIX. Replication: Why We Still Can’t Browse in Peace: On the Uniqueness and Reidentifiability of Web Browsing Histories Sarah Bird Ilana Segall Martin Lopatka Mozilla Mozilla Mozilla Abstract This work seeks to reproduce the findings of Olejnik, Castel- We examine the threat to individuals’ privacy based on the luccia, and Janc [48] regarding the leakage of private infor- feasibility of reidentifying users through distinctive profiles mation when users browse the web. The reach of large-scale of their browsing history visible to websites and third par- providers of analytics and advertisement services into the ties. This work replicates and extends the 2012 paper Why overall set of web properties shows a continued increase in Johnny Can’t Browse in Peace: On the Uniqueness of Web visibility [64] by such parties across a plurality of web prop- Browsing History Patterns [48]. The original work demon- erties. This makes the threat of history-based profiling even strated that browsing profiles are highly distinctive and stable. more tangible and urgent now than when originally proposed. We reproduce those results and extend the original work to detail the privacy risk posed by the aggregation of browsing 2 Background and related work histories. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Marcia Knous: My Name Is Marcia Knous
Olivia Ryan: Can you just state your name? Marcia Knous: My name is Marcia Knous. OR: Just give us your general background. How did you come to work at Mozilla and what do you do for Mozilla now? MK: Basically, I started with Mozilla back in the Netscape days. I started working with Mozilla.org shortly after AOL acquired Netscape which I believe was in like the ’99- 2000 timeframe. I started working at Netscape and then in one capacity in HR shortly after I moved working with Mitchell as part of my shared responsibility, I worked for Mozilla.org and sustaining engineering to sustain the communicator legacy code so I supported them administratively. That’s basically what I did for Mozilla. I did a lot of I guess what you kind of call of blue activities where we have a process whereby people get access to our CVS repository so I was the gatekeeper for all the CVS forms and handle all the bugs that were related to CVS requests, that kind of thing. Right now at Mozilla, I do quality assurance and I run both our domestic online store as well as our international store where we sell all of our Mozilla gear. Tom Scheinfeldt: Are you working generally alone in small groups? In large groups? How do you relate to other people working on the project? MK: Well, it’s a rather interesting project. My capacity as a QA person, we basically relate with the community quite a bit because we have a very small internal QA organization. -
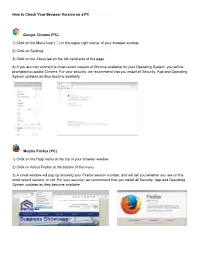
How to Check Your Browser Version on a PC
How to Check Your Browser Version on a PC Google Chrome (PC) 1) Click on the Menu Icon ( ) in the upper right corner of your browser window. 2) Click on Settings 3) Click on the About tab on the left-hand side of the page. 4) If you are not running the most recent version of Chrome available for your Operating System, you will be prompted to update Chrome. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Mozilla Firefox (PC) 1) Click on the Help menu at the top of your browser window. 2) Click on About Firefox at the bottom of the menu. 3) A small window will pop up showing your Firefox version number, and will tell you whether you are on the most recent version, or not. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Internet Explorer (PC) 1) Click on the Gear Icon at the top of your browser window. 2) Click on the About Internet Explorer option. 3) A window will pop up showing you your Internet Explorer version. 4) If you are using Internet Explorer 9 or 10, you will need to make sure that you have TLS 1.2 enabled by: A) Clicking on the Gear Icon again. B) Click on Internet Options. C) Click on the Advanced Tab and scroll down to the option titled “Use TLS 1.2”. (This should be found at the bottome of the list of options.) The box next to this should be checked. -

Copyrighted Material
05_096970 ch01.qxp 4/20/07 11:27 PM Page 3 1 Introducing Cascading Style Sheets Cascading style sheets is a language intended to simplify website design and development. Put simply, CSS handles the look and feel of a web page. With CSS, you can control the color of text, the style of fonts, the spacing between paragraphs, how columns are sized and laid out, what back- ground images or colors are used, as well as a variety of other visual effects. CSS was created in language that is easy to learn and understand, but it provides powerful control over the presentation of a document. Most commonly, CSS is combined with the markup languages HTML or XHTML. These markup languages contain the actual text you see in a web page — the hyperlinks, paragraphs, headings, lists, and tables — and are the glue of a web docu- ment. They contain the web page’s data, as well as the CSS document that contains information about what the web page should look like, and JavaScript, which is another language that pro- vides dynamic and interactive functionality. HTML and XHTML are very similar languages. In fact, for the majority of documents today, they are pretty much identical, although XHTML has some strict requirements about the type of syntax used. I discuss the differences between these two languages in detail in Chapter 2, and I also pro- vide a few simple examples of what each language looks like and how CSS comes together with the language to create a web page. In this chapter, however, I discuss the following: ❑ The W3C, an organization that plans and makes recommendations for how the web should functionCOPYRIGHTED and evolve MATERIAL ❑ How Internet documents work, where they come from, and how the browser displays them ❑ An abridged history of the Internet ❑ Why CSS was a desperately needed solution ❑ The advantages of using CSS 05_096970 ch01.qxp 4/20/07 11:27 PM Page 4 Part I: The Basics The next section takes a look at the independent organization that makes recommendations about how CSS, as well as a variety of other web-specific languages, should be used and implemented. -

Byos Bug Bounty Program: Las Vegas 2019
Byos Bug Bounty Program: Las Vegas 2019 White Paper Document version: 1.0 August 21st, 2019 Byos Bug Bounty Program - Las Vegas 2019 White Paper - © 2019 Mkit North America Inc. All rights reserved - byos.io Page 1 of 14 1.0 - Introduction 3 2.0 - Findings 5 2.1 - Critical Vulnerabilities 5 2.1.1 - Timing ARP Spoof attack 5 2.2 - High Vulnerabilities 6 2.2.1 - SQL Injection 6 2.2.2 - Authentication bypass (JWT) 7 2.2.3 - Authentication Bypass (Remember Me) 8 2.3 - Medium Vulnerabilities 9 2.3.1 - Persistent XSS 9 2.4 - Low Vulnerabilities 10 2.4.1 - Unicode in SSID 10 2.4.2 - CSRF 11 2.4.3 - Outdated libraries 12 3.0 - Conclusion 12 4.0 - Footnotes 14 Byos Bug Bounty Program - Las Vegas 2019 White Paper - © 2019 Mkit North America Inc. All rights reserved - byos.io Page 2 of 14 1.0 - Introduction 1.1 - Summary Over the course of 3 days, more than 20 security researchers from North America, South America, and Europe participated in our company’s first bug bounty event. The event was by invitation only. 1.2 - Objective The overall objective of the bug bounty program is to validate the security claims of the Byos Portable Secure Gateway and to discover any existing vulnerabilities in the product and its features. Additional benefits include: ● Practising the company’s internal vulnerability handling process ● Increasing our security team’s awareness of how attackers approach the security mechanisms of the product ● Learning and validating security development best practices by having active feedback from researchers ● Gathering external expert opinions on the product’s feature-set, benefits and use-cases 1.3 - Time and Location The Bug Bounty took place during August 8-9-10, 2019, in Las Vegas, NV (USA). -

Longitudinal Characterization of Browsing Habits
Please cite this paper as: Luca Vassio, Idilio Drago, Marco Mellia, Zied Ben Houidi, and Mohamed Lamine Lamali. 2018. You, the Web, and Your Device: Longitudinal Charac- terization of Browsing Habits. ACM Trans. Web 12, 4, Article 24 (November 2018), 30 1 pages. https://doi.org/10.1145/3231466 You, the Web and Your Device: Longitudinal Characterization of Browsing Habits LUCA VASSIO, Politecnico di Torino IDILIO DRAGO, Politecnico di Torino MARCO MELLIA, Politecnico di Torino ZIED BEN HOUIDI, Nokia Bell Labs MOHAMED LAMINE LAMALI, LaBRI, Université de Bordeaux Understanding how people interact with the web is key for a variety of applications – e.g., from the design of eective web pages to the denition of successful online marketing campaigns. Browsing behavior has been traditionally represented and studied by means of clickstreams, i.e., graphs whose vertices are web pages, and edges are the paths followed by users. Obtaining large and representative data to extract clickstreams is however challenging. The evolution of the web questions whether browsing behavior is changing and, by consequence, whether properties of clickstreams are changing. This paper presents a longitudinal study of clickstreams in from 2013 to 2016. We evaluate an anonymized dataset of HTTP traces captured in a large ISP, where thousands of households are connected. We rst propose a methodology to identify actual URLs requested by users from the massive set of requests automatically red by browsers when rendering web pages. Then, we characterize web usage patterns and clickstreams, taking into account both the temporal evolution and the impact of the device used to explore the web. -

Internal Message
Earlier today, Mozilla Corporation CEO and Mozilla Foundation Chairwoman Mitchell Baker sent the following message to Mozilla employees. We are making significant changes at Mozilla Corporation today. Pre-COVID, our plan for 2020 was a year of change: building a better internet by accelerating product value in Firefox, increasing innovation, and adjusting our finances to ensure financial stability over the long term. We started with immediate cost-saving measures such as pausing our hiring, reducing our wellness stipend and cancelling our All-Hands. But COVID-19 has accelerated the need and magnified the depth for these changes. Our pre-COVID plan is no longer workable. We have talked about the need for change — including the likelihood of layoffs — since the spring. Today these changes become real. We are also restructuring to put a crisper focus on new product development and go to market activities. In the long run, I am confident that the new organizational structure will serve our product and market impact goals well, but we will talk in detail about this in a bit. But, before that is the painful part. Yes — we need to reduce the size of our workforce. This is hard to internalize and I desperately wish there was some other way to set Mozilla up for success in building a better internet. I desperately wish that all those who choose Mozilla as an employer could stay as long as interest and skills connect. Unfortunately, we can’t make that happen today. We are reducing the size of the MoCo workforce by approximately 250 roles, including closing our current operations in Taipei, Taiwan. -
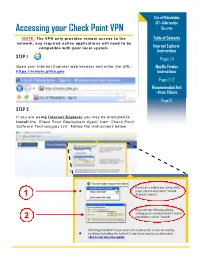
Accessing Your Check Point VPN Security
City of Philadelphia OIT—Information Accessing your Check Point VPN Security NOTE: The VPN only provides remote access to the Table of Contents network, any required native applications will need to be compatible with your local system. Internet Explorer Instructions STEP 1 Pages 1-5 Open your Internet Explorer web browser and enter the URL: Mozilla Firefox https://remote.phila.gov Instructions Pages 6-12 Recommended Anti -Virus Clients Page 13 STEP 2 If you are using Internet Explorer you may be prompted to install the ’Check Point Deployment Agent’ from ’Check Point Software Technologies Ltd.’ Follow the instructions below. 1 2 Page 2 Accessing your Check Point VPN STEP 3 Install the Check Point Deployment Agent when prompted. STEP 4 Check Point will be ask if you trust the server for remote.phila.gov. Click Trust Server. Page 3 Accessing your Check Point VPN STEP 4 Check Point will now scan your computer for security threats and check if your computer’s anti-virus client is in compliance with the City of Philadelphia’s Information Security policies. Note: If the scan is taking a long time or does not finish, please close the browser window and begin the process again at Step 1. NOTE: If your Anti-Virus scan FAILS PROCEED to page 13 of this document to see the list of approved Check Point Anti-virus clients that will allow you to access your VPN! Page 4 Accessing your Check Point VPN STEP 5 If the scan is successfully completed, you will be navigated to the Sign In page.