CVE-2021-23987 Published On: 03/31/2021 12:00:00 AM UTC
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Differential Fuzzing the Webassembly
Master’s Programme in Security and Cloud Computing Differential Fuzzing the WebAssembly Master’s Thesis Gilang Mentari Hamidy MASTER’S THESIS Aalto University - EURECOM MASTER’STHESIS 2020 Differential Fuzzing the WebAssembly Fuzzing Différentiel le WebAssembly Gilang Mentari Hamidy This thesis is a public document and does not contain any confidential information. Cette thèse est un document public et ne contient aucun information confidentielle. Thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in Technology. Antibes, 27 July 2020 Supervisor: Prof. Davide Balzarotti, EURECOM Co-Supervisor: Prof. Jan-Erik Ekberg, Aalto University Copyright © 2020 Gilang Mentari Hamidy Aalto University - School of Science EURECOM Master’s Programme in Security and Cloud Computing Abstract Author Gilang Mentari Hamidy Title Differential Fuzzing the WebAssembly School School of Science Degree programme Master of Science Major Security and Cloud Computing (SECCLO) Code SCI3084 Supervisor Prof. Davide Balzarotti, EURECOM Prof. Jan-Erik Ekberg, Aalto University Level Master’s thesis Date 27 July 2020 Pages 133 Language English Abstract WebAssembly, colloquially known as Wasm, is a specification for an intermediate representation that is suitable for the web environment, particularly in the client-side. It provides a machine abstraction and hardware-agnostic instruction sets, where a high-level programming language can target the compilation to the Wasm instead of specific hardware architecture. The JavaScript engine implements the Wasm specification and recompiles the Wasm instruction to the target machine instruction where the program is executed. Technically, Wasm is similar to a popular virtual machine bytecode, such as Java Virtual Machine (JVM) or Microsoft Intermediate Language (MSIL). -

Machine Learning in the Browser
Machine Learning in the Browser The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:38811507 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA Machine Learning in the Browser a thesis presented by Tomas Reimers to The Department of Computer Science in partial fulfillment of the requirements for the degree of Bachelor of Arts in the subject of Computer Science Harvard University Cambridge, Massachusetts March 2017 Contents 1 Introduction 3 1.1 Background . .3 1.2 Motivation . .4 1.2.1 Privacy . .4 1.2.2 Unavailable Server . .4 1.2.3 Simple, Self-Contained Demos . .5 1.3 Challenges . .5 1.3.1 Performance . .5 1.3.2 Poor Generality . .7 1.3.3 Manual Implementation in JavaScript . .7 2 The TensorFlow Architecture 7 2.1 TensorFlow's API . .7 2.2 TensorFlow's Implementation . .9 2.3 Portability . .9 3 Compiling TensorFlow into JavaScript 10 3.1 Motivation to Compile . 10 3.2 Background on Emscripten . 10 3.2.1 Build Process . 12 3.2.2 Dependencies . 12 3.2.3 Bitness Assumptions . 13 3.2.4 Concurrency Model . 13 3.3 Experiences . 14 4 Results 15 4.1 Benchmarks . 15 4.2 Library Size . 16 4.3 WebAssembly . 17 5 Developer Experience 17 5.1 Universal Graph Runner . -
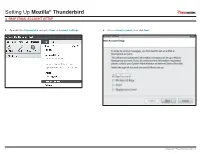
Setting up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP
Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP 1. Open Mozilla Thunderbird and go to Tools -> Account Settings. 2. Choose Email account; then click Next. 1 Copyright © EmailHosting.com LLC Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP (cont.) 3. In the Identity window type your name as you want it to appear on outgoing emails. 4. In the Server Information window select the radio button labeled IMAP. • Then, type your email address in the field labeled Email Address. • Enter imap.emailhosting.com in the field labeled Incoming Server. • Click Next to continue. • Enter smtp.emailhosting.com in the field labeled Outgoing Server. • Click Next to continue. John Smith imap.emailhosting.com [email protected] smtp.emailhosting.com Note: If you have already used Thunderbird in the past the Outgoing Server will not be listed. 2 Copyright © EmailHosting.com LLC Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP (cont.) 5. In the User Names window, the fields should already be filled out correctly. 6. Click Next on the Account Name page to accept the default Account Name. • Confirm that both fields match your EmailHosting username. • In the Congratulations window, verify that all information is correct. • Click Next to continue. • Then click Finish. [email protected] [email protected] [email protected] [email protected] 7. You will be prompted for your password. If you’d like to save your password, make sure Use Password Manager to remember this password is checked before clicking on OK to continue. Note: The field Outgoing Server is only visible during the setup of Mozilla Thunderbird’s first email account. -

Mitigating Javascript's Overhead with Webassembly
Samuli Ylenius Mitigating JavaScript’s overhead with WebAssembly Faculty of Information Technology and Communication Sciences M. Sc. thesis March 2020 ABSTRACT Samuli Ylenius: Mitigating JavaScript’s overhead with WebAssembly M. Sc. thesis Tampere University Master’s Degree Programme in Software Development March 2020 The web and web development have evolved considerably during its short history. As a result, complex applications aren’t limited to desktop applications anymore, but many of them have found themselves in the web. While JavaScript can meet the requirements of most web applications, its performance has been deemed to be inconsistent in applications that require top performance. There have been multiple attempts to bring native speed to the web, and the most recent promising one has been the open standard, WebAssembly. In this thesis, the target was to examine WebAssembly, its design, features, background, relationship with JavaScript, and evaluate the current status of Web- Assembly, and its future. Furthermore, to evaluate the overhead differences between JavaScript and WebAssembly, a Game of Life sample application was implemented in three splits, fully in JavaScript, mix of JavaScript and WebAssembly, and fully in WebAssembly. This allowed to not only compare the performance differences between JavaScript and WebAssembly but also evaluate the performance differences between different implementation splits. Based on the results, WebAssembly came ahead of JavaScript especially in terms of pure execution times, although, similar benefits were gained from asm.js, a predecessor to WebAssembly. However, WebAssembly outperformed asm.js in size and load times. In addition, there was minimal additional benefit from doing a WebAssembly-only implementation, as just porting bottleneck functions from JavaScript to WebAssembly had similar performance benefits. -

Giant List of Web Browsers
Giant List of Web Browsers The majority of the world uses a default or big tech browsers but there are many alternatives out there which may be a better choice. Take a look through our list & see if there is something you like the look of. All links open in new windows. Caveat emptor old friend & happy surfing. 1. 32bit https://www.electrasoft.com/32bw.htm 2. 360 Security https://browser.360.cn/se/en.html 3. Avant http://www.avantbrowser.com 4. Avast/SafeZone https://www.avast.com/en-us/secure-browser 5. Basilisk https://www.basilisk-browser.org 6. Bento https://bentobrowser.com 7. Bitty http://www.bitty.com 8. Blisk https://blisk.io 9. Brave https://brave.com 10. BriskBard https://www.briskbard.com 11. Chrome https://www.google.com/chrome 12. Chromium https://www.chromium.org/Home 13. Citrio http://citrio.com 14. Cliqz https://cliqz.com 15. C?c C?c https://coccoc.com 16. Comodo IceDragon https://www.comodo.com/home/browsers-toolbars/icedragon-browser.php 17. Comodo Dragon https://www.comodo.com/home/browsers-toolbars/browser.php 18. Coowon http://coowon.com 19. Crusta https://sourceforge.net/projects/crustabrowser 20. Dillo https://www.dillo.org 21. Dolphin http://dolphin.com 22. Dooble https://textbrowser.github.io/dooble 23. Edge https://www.microsoft.com/en-us/windows/microsoft-edge 24. ELinks http://elinks.or.cz 25. Epic https://www.epicbrowser.com 26. Epiphany https://projects-old.gnome.org/epiphany 27. Falkon https://www.falkon.org 28. Firefox https://www.mozilla.org/en-US/firefox/new 29. -

Software Management Full Installers Guide
Software Management Full Installers Guide Supported Platforms and Applications | Q1 2020 Software Management Full Installers Guide Release 9.5 | Q1 2020 www.kaseya.com 2 Software Management Full Installers Guide Release 9.5 | Q1 2020 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya’s “Click-Accept” EULATOS as updated from time to time by Kaseya at http://www.kaseya.com/legal.aspx. If Customer does not agree with the Agreement, please do not install, use or purchase any Software and Services from Kaseya as continued use of the Software or Services indicates Customer’s acceptance of the Agreement. www.kaseya.com Software Management Full Installers 3 Guide Release 9.5 | Q1 2020 Contents Installers Available 4 www.kaseya.com 4 Software Management Full Installers Guide Release 9.5 | Q1 2020 Installers Available Title Vendor URL 7-Zip File Archiver (Full Install) for Igor Pavlov http://www.7-zip.org/ Windows Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (Full Install) for Mac Systems, Inc OS X Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (de-DE) (Full Install) Systems, Inc for Windows Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (en-US) (Full Install) Systems, Inc for Windows Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (es-ES) (Full Install) Systems, Inc for Windows -

Instalación Y Administración De Servicios De Correo Electrónico
Servicios de red e internet Instalación y administración de servicios de correo electrónico Raquel Castellanos Crespo Instalación y administración de servicios de correo electrónico Servicios de red e internet Raquel Castellanos Crespo INDICE Características del servicio de correo electrónico Elementos del servicio de correo electrónico -Agentes de correo electrónico. - Servidores de correo electrónico. Open relay y Smart host - Clientes de correo electrónico: entorno-DOS, gráficos y navegadores. - Direcciones, cuentas de correo y servidores DNS - Protocolos y servicios de descarga de correo: SMPT, ESMTP, POP, IMAP. Funcionamiento del servicio de correo electrónico Cuentas de correo, alias y buzones de correo Estructura de mensajes de correo electrónico - Cabecera, cuerpo, MIME Monitorización y registros del servicio de correo electrónico Servicio de correo electrónico vía web Correo seguro - Firma digital y cifrado de mensajes Veracidad del correo - Correo basura ("SPAM”) fraude, engaño, cadenas y virus informáticos 2 Servicios de red e internet | Instalación y administración de servicios de correo electrónico Servicios de red e internet Raquel Castellanos Crespo Características del servicio de correo electrónico Correo electrónico (correo-e, conocido también como e-mail ), es un servicio de red que permite a los usuarios enviar y recibir mensajes y archivos rápidamente (también denominados mensajes electrónicos o cartas electrónicas) mediante sistemas de comunicación electrónicos. Principalmente se usa este nombre para denominar al sistema que provee este servicio en Internet, mediante el protocolo SMTP, aunque por extensión también puede verse aplicado a sistemas análogos que usen otras tecnologías. Por medio de mensajes de correo electrónico se puede enviar, no solamente texto, sino todo tipo de documentos digitales. -

Whitepaper | IBM Domino Application Migration and Decommissioning
WHITEPAPER IBM Domino Application Migration and Decomissioning 1. Migration vs. Decommissioning As outlined above, an application migration can be very time-consuming - and it’s more likely to be than not to IBM Domino has been around for decades. Mid-sized to be. Therefore, the migration cannot be expected to be very large companies have built hundreds and thousands of completed short-term. In addition, it typically involves huge applications around IBM Domino that support their business financial investments. If the information that the application processes; many of those applications are business critical, maintains needs to be retained, maybe for a long period of e.g. because they store information that is subject to legal time, e.g. due to legal requirements, how should a company requirements. deal with this situation? But the IT world keeps changing. New technologies arise The answer to this question is »decommissioning«. When an nearly every day. Companies need to continuously review application is decommissioned, the application and its logic their IT strategy in order not to fall behind. are discarded whereas the data is maintained and kept in a Regarding IBM’s Domino offering there are quite a few way so that it is still accessible – at least for reading – even reasons why companies reassess their investments into that if the application that was used to create it is not available technology. Many of those companies already have decided anymore. or are in the process of deciding to move away from IBM Domino. They are looking at Enterprise Content Manage- ment (ECM) systems like Alfresco, OpenText Documentum, For the purpose of this document, migration is only OpenText, SharePoint etc. -

USER GUIDE Wwpass Security for Email (Thunderbird) for Wwpass Security Pack 2.6
USER GUIDE WWPass Security for Email (Thunderbird) For WWPass Security Pack 2.6 May 2014 TABLE OF CONTENTS Chapter 1 — Welcome .................................................................................................................................. 3 Introducing WWPass Security for Email (Thunderbird) ............................................................................ 4 Presenting Your PassKey to Your Computer ........................................................................................ 5 Related Documentation ............................................................................................................................. 6 Need Assistance? ..................................................................................................................................... 7 Report a Problem from Dashboard ....................................................................................................... 7 Chapter 2 — Requirements .......................................................................................................................... 8 Requirements for WWPass Security for Email (Thunderbird) .................................................................. 8 Supported Platforms and Browsers .......................................................................................................... 9 Chapter 3 — Setup ..................................................................................................................................... 10 Smart Start for Setup ............................................................................................................................. -

Mailstore Server 7 Technical Specifications
MailStore Server ® 7 Technical Specifications MailStore Server The Standard in Email Archiving Businesses of all sizes can benefit from the legal, technical, and financial advantages of modern and secure email archiving with MailStore Server. MailStore Server 7 - Technical Specifications Archiving Supported Email Servers and Internet Mailboxes General Features Microsoft Exchange Server 2003, 2007, and 2010 (including Windows Small Business Server) No changes made to email servers and emails Hosted Exchange No administrative access to Microsoft O(ce 365 (Exchange Online) the email server required MDaemon Messaging Server Folder structure of mailboxes IceWarp Mail Server is imported into the archive Kerio Connect Size of mailboxes can be IMAP4-compatible email server reduced through rule-based POP3-compatible email server deletion Internet and webmail inboxes such as Gmail or GMX (via IMAP or Emails are archived in a MIME- POP3) compatible manner with no loss of information Archiving Methods Full archiving of all emails as they are sent and received Archiving of existing mailboxes and files (manual or scheduled) Archiving of public folders (manual or scheduled) Supported Email Clients Microsoft Outlook 2000, XP, 2003, 2007, 2010 Microsoft Outlook Express 6.0 Microsoft Windows Mail Microsoft Windows Live Mail Mozilla Thunderbird and SeaMonkey Supported Email File Formats RFC822/MIME-compatible email files (.eml) PST files MSG files (Outlook format) MBOX files Archiving Via MailStore Proxy Server Companies without an email server can automatically archive all incoming and outgoing email correspondence via the MailStore proxy server (SMTP and POP3). 2 MailStore Server 7 - Technical Specifications User Access to the Archive Supported Access Methods General Features MailStore Add-in for Microsoft Outlook MailStore users can access their archives using a convenient add-in for Stub files and other technolo- Microsoft Outlook XP, 2003, 2007, and 2010 (32-bit and 64-bit). -

Mozilla Development Roadmap
mozilla development roadmap Brendan Eich, David Hyatt table of contents • introduction • milestone schedule • about ownership... • a new • current release • what all this does not roadmap status mean • discussion • how you can help • application architecture • summary • project • to-do list rationale management introduction Welcome to the Mozilla development roadmap. This is the third major roadmap revision, with a notable recent change to the status of the integrated Mozilla application suite, since the original roadmap that set Mozilla on a new course for standards compliance, modularity, and portability in 1998. The previous roadmap documented milestones and rules of development through Mozilla 1.3, and contains links to older roadmaps. Most of this document reflects the new application architecture proposal made last year. The effort resulting from that proposal has finally borne fruit, or to mix metaphors, hatched new application creatures: Firefox and Thunderbird. The new, significant roadmap update hoped for early in 2004 has been postponed. See Brendan's roadmap blog for thoughts that may feed into it. An interim roadmap update focused on the "aviary 1.0" 1 From www.mozilla.org/roadmap.html 4 August 2004 releases of Firefox 1.0 and Thunderbird 1.0, and the 1.8 milestone that will follow, is coming soon. We have come a long way. We have achieved a Mozilla 1.0 milestone that satisfies the criteria put forth in the Mozilla 1.0 manifesto, giving the community and the wider world a high-quality release, and a stable branch for conservative development and derivative product releases. See the Mozilla Hall of Fame for a list of Mozilla-based projects and products that benefited from 1.0. -

Mechanizing Webassembly Proposals
University of Wisconsin Milwaukee UWM Digital Commons Theses and Dissertations August 2020 Mechanizing Webassembly Proposals Jacob Richard Mischka University of Wisconsin-Milwaukee Follow this and additional works at: https://dc.uwm.edu/etd Part of the Computer Sciences Commons Recommended Citation Mischka, Jacob Richard, "Mechanizing Webassembly Proposals" (2020). Theses and Dissertations. 2565. https://dc.uwm.edu/etd/2565 This Thesis is brought to you for free and open access by UWM Digital Commons. It has been accepted for inclusion in Theses and Dissertations by an authorized administrator of UWM Digital Commons. For more information, please contact [email protected]. MECHANIZING WEBASSEMBLY PROPOSALS by Jacob Mischka A Dissertation Submitted in Partial Fulfillment of the Requirements for the degree of Master of Science in Computer Science at The University of Wisconsin-Milwaukee August 2020 ABSTRACT MECHANIZING WEBASSEMBLY PROPOSALS by Jacob Mischka The University of Wisconsin-Milwaukee, 2020 Under the Supervision of Professor John Boyland WebAssembly is a modern low-level programming language designed to provide high performance and security. To enable these goals, the language specifies a relatively small number of low-level types, instructions, and lan- guage constructs. The language is proven to be sound with respect to its types and execution, and a separate mechanized formalization of the specifi- cation and type soundness proofs confirms this. As an emerging technology, the language is continuously being developed, with modifications being pro- posed and discussed in the open and on a frequent basis. ii In order to ensure the soundness properties exhibited by the original core language are maintained as WebAssembly evolves, these proposals should too be mechanized and verified to be sound.