Email Client Backdoor
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Using Emergent Team Structure to Focus Collaboration
Using Emergent Team Structure to Focus Collaboration by Shawn Minto B.Sc, The University of British Columbia, 2005 A THESIS SUBMITTED IN PARTIAL FULFILMENT OF THE REQUIREMENTS FOR THE DEGREE OF Master of Science The Faculty of Graduate Studies (Computer Science) The University Of British Columbia January 30, 2007 © Shawn Minto 2007 ii Abstract To build successful complex software systems, developers must collaborate with each other to solve issues. To facilitate this collaboration specialized tools are being integrated into development environments. Although these tools facilitate collaboration, they do not foster it. The problem is that the tools require the developers to maintain a list of other developers with whom they may wish to communicate. In any given situation, it is the developer who must determine who within this list has expertise for the specific situation. Unless the team is small and static, maintaining the knowledge about who is expert in particular parts of the system is difficult. As many organizations are beginning to use agile development and distributed software practices, which result in teams with dynamic membership, maintaining this knowledge is impossible. This thesis investigates whether emergent team structure can be used to support collaboration amongst software developers. The membership of an emergent team is determined from analysis of software artifacts. We first show that emergent teams exist within a particular open-source software project, the Eclipse integrated development environment. We then present a tool called Emergent Expertise Locator (EEL) that uses emergent team information to propose experts to a developer within their development environment as the developer works. We validated this approach to support collaboration by applying our ap• proach to historical data gathered from the Eclipse project, Firefox and Bugzilla and comparing the results to an existing heuristic for recommending experts that produces a list of experts based on the revision history of individual files. -

Security Distributed and Networking Systems (507 Pages)
Security in ................................ i Distri buted and /Networking.. .. Systems, . .. .... SERIES IN COMPUTER AND NETWORK SECURITY Series Editors: Yi Pan (Georgia State Univ., USA) and Yang Xiao (Univ. of Alabama, USA) Published: Vol. 1: Security in Distributed and Networking Systems eds. Xiao Yang et al. Forthcoming: Vol. 2: Trust and Security in Collaborative Computing by Zou Xukai et al. Steven - Security Distributed.pmd 2 5/25/2007, 1:58 PM Computer and Network Security Vol. 1 Security in i Distri buted and /Networking . Systems Editors Yang Xiao University of Alabama, USA Yi Pan Georgia State University, USA World Scientific N E W J E R S E Y • L O N D O N • S I N G A P O R E • B E I J I N G • S H A N G H A I • H O N G K O N G • TA I P E I • C H E N N A I Published by World Scientific Publishing Co. Pte. Ltd. 5 Toh Tuck Link, Singapore 596224 USA office: 27 Warren Street, Suite 401-402, Hackensack, NJ 07601 UK office: 57 Shelton Street, Covent Garden, London WC2H 9HE British Library Cataloguing-in-Publication Data A catalogue record for this book is available from the British Library. SECURITY IN DISTRIBUTED AND NETWORKING SYSTEMS Series in Computer and Network Security — Vol. 1 Copyright © 2007 by World Scientific Publishing Co. Pte. Ltd. All rights reserved. This book, or parts thereof, may not be reproduced in any form or by any means, electronic or mechanical, including photocopying, recording or any information storage and retrieval system now known or to be invented, without written permission from the Publisher. -

Towards Dependable Dynamic Component-Based Applications
THÈSE Pour obtenir le grade de DOCTEUR DE L’UNIVERSITÉ DE GRENOBLE Spécialité : Informatique Arrêté ministériel : 7 août 2006 Présentée par Kiev SANTOS DA GAMA Thèse dirigée par Didier DONSEZ préparée au sein du Laboratoire d’Informatique de Grenoble dans l'École Doctorale Mathématiques, Sciences et Technologies de l’Information, Informatique (MSTII) Towards Dependable Dynamic Component-based Applications Thèse soutenue publiquement le « 6 Octobre 2011», devant le jury composé de : Mme Claudia RONCANCIO Professeur, Ensimag - Grenoble INP, Président M Gilles MULLER Directeur de Recherche, INRIA, Rapporteur M Lionel SEINTURIER Professeur, Université de Lille & IUF, Rapporteur M Ivica CRNKOVIC Professor, Mälardalen University, Membre M Didier DONSEZ Professeur, Université Joseph Fourier, Membre M Gaël THOMAS Maître de Conférences, Université Pierre et Marie Curie, Membre M Peter KRIENS Technical Director, OSGi Alliance, Invité ABSTRACT Software is moving towards evolutionary architectures that are able to easily accommodate changes and integrate new functionality. This is important in a wide range of applications, from plugin-based end user applications to critical applications with high availability requirements. Dynamic component-based platforms allow software to evolve at runtime, by allowing components to be loaded, and executed without forcing applications to be restarted. However, the flexibility of such mechanism demands applications to cope with errors due to inconsistencies in the update process, or due to faulty behavior from components introduced during execution. This is mainly true when dealing with third-party components, making it harder to predict the impacts (e.g., runtime incompatibilities, application crashes) and to maintain application dependability when integrating such third-party code into the application. -

Peer Participation and Software
Peer Participation and Software This report was made possible by the grants from the John D. and Cath- erine T. MacArthur Foundation in connection with its grant-making initiative on Digital Media and Learning. For more information on the initiative visit www.macfound.org. The John D. and Catherine T. MacArthur Foundation Reports on Digital Media and Learning Peer Participation and Software: What Mozilla Has to Teach Government by David R. Booth The Future of Learning Institutions in a Digital Age by Cathy N. Davidson and David Theo Goldberg with the assistance of Zoë Marie Jones The Future of Thinking: Learning Institutions in a Digital Age by Cathy N. Davidson and David Theo Goldberg with the assistance of Zoë Marie Jones New Digital Media and Learning as an Emerging Area and “Worked Examples” as One Way Forward by James Paul Gee Living and Learning with New Media: Summary of Findings from the Digital Youth Project by Mizuko Ito, Heather Horst, Matteo Bittanti, danah boyd, Becky Herr-Stephenson, Patricia G. Lange, C. J. Pascoe, and Laura Robinson with Sonja Baumer, Rachel Cody, Dilan Mahendran, Katynka Z. Martínez, Dan Perkel, Christo Sims, and Lisa Tripp Young People, Ethics, and the New Digital Media: A Synthesis from the GoodPlay Project by Carrie James with Katie Davis, Andrea Flores, John M. Francis, Lindsay Pettingill, Margaret Rundle, and Howard Gardner Confronting the Challenges of Participatory Culture: Media Education for the 21st Century by Henry Jenkins (P.I.) with Ravi Purushotma, Margaret Weigel, Katie Clinton, and Alice J. Robison The Civic Potential of Video Games by Joseph Kahne, Ellen Middaugh, and Chris Evans Peer Production and Software What Mozilla Has to Teach Government David R. -
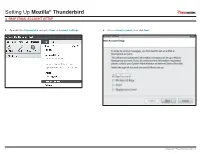
Setting up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP
Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP 1. Open Mozilla Thunderbird and go to Tools -> Account Settings. 2. Choose Email account; then click Next. 1 Copyright © EmailHosting.com LLC Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP (cont.) 3. In the Identity window type your name as you want it to appear on outgoing emails. 4. In the Server Information window select the radio button labeled IMAP. • Then, type your email address in the field labeled Email Address. • Enter imap.emailhosting.com in the field labeled Incoming Server. • Click Next to continue. • Enter smtp.emailhosting.com in the field labeled Outgoing Server. • Click Next to continue. John Smith imap.emailhosting.com [email protected] smtp.emailhosting.com Note: If you have already used Thunderbird in the past the Outgoing Server will not be listed. 2 Copyright © EmailHosting.com LLC Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP (cont.) 5. In the User Names window, the fields should already be filled out correctly. 6. Click Next on the Account Name page to accept the default Account Name. • Confirm that both fields match your EmailHosting username. • In the Congratulations window, verify that all information is correct. • Click Next to continue. • Then click Finish. [email protected] [email protected] [email protected] [email protected] 7. You will be prompted for your password. If you’d like to save your password, make sure Use Password Manager to remember this password is checked before clicking on OK to continue. Note: The field Outgoing Server is only visible during the setup of Mozilla Thunderbird’s first email account. -

Organizational Search in Email Systems Sruthi Bhushan Pitla Western Kentucky University, [email protected]
Western Kentucky University TopSCHOLAR® Masters Theses & Specialist Projects Graduate School 5-2012 Organizational Search in Email Systems Sruthi Bhushan Pitla Western Kentucky University, [email protected] Follow this and additional works at: http://digitalcommons.wku.edu/theses Part of the Databases and Information Systems Commons Recommended Citation Pitla, Sruthi Bhushan, "Organizational Search in Email Systems" (2012). Masters Theses & Specialist Projects. Paper 1161. http://digitalcommons.wku.edu/theses/1161 This Thesis is brought to you for free and open access by TopSCHOLAR®. It has been accepted for inclusion in Masters Theses & Specialist Projects by an authorized administrator of TopSCHOLAR®. For more information, please contact [email protected]. ORGANIZATIONAL SEARCH IN EMAIL SYSTEMS A Thesis Presented to The Faculty of the Department of Mathematics and Computer Science Western Kentucky University Bowling Green, Kentucky In Partial Fulfillment Of the Requirements for the Degree Master of Science By Sruthi Bhushan Pitla May 2012 ACKNOWLEDGMENTS It was a great pleasure working under my graduate advisor, Dr. Guangming Xing, who provided me with everything I need to succeed. His inspiration and guidance at each and every step made this Master of Science degree so rewarding and satisfactory. He always encouraged my work in every possible way and also gave me the freedom to express and implement my ideas without any restrictions. I feel very fortunate and proud to have been his student and really think the experience which I gained working under him is invaluable. I would like to whole heartedly thank Dr. Xing for the immense trust and patience he has over me. -

Bachelorarbeit
BACHELORARBEIT Frau Kristina Martin Extraktion von Passworthashes und Ermittlung von Passwörtern aus Browserapplikationen im Rahmen der Post-Mortem-Analyse 2018 Fakultät Angewandte Computer- und Biowissenschaften BACHELORARBEIT Extraktion von Passworthashes und Ermittlung von Passwörtern aus Browserapplikationen im Rahmen der Post-Mortem-Analyse Autorin: Kristina Martin Studiengang: Allgemeine und digitale Forensik Seminargruppe: FO15w3-B Betreuer der Hochschule:: Prof. Dr. rer. nat. Christian Hummert Betreuer am Landeskriminalamt Thüringen: Dipl.-Inf. Andreas Sommer Mittweida, August 2018 Faculty Applied Computer Sciences & Biosciences BACHELOR THESIS Extraction of Password Hashes and Decryption of Passwords stored by Browser Applications on the Basis of a Post-Mortem-Analysis Authorin: Kristina Martin Study Programme: General and Digital Forensic Science Seminar Group: FO15w3-B First Referee:: Prof. Dr. rer. nat. Christian Hummert Second Referee: Dipl.-Inf. Andreas Sommer Mittweida, August 2018 Bibliografische Angaben Martin, Kristina: Extraktion von Passworthashes und Ermittlung von Passwörtern aus Browser- applikationen im Rahmen der Post-Mortem-Analyse, 95 Seiten, 49 Abbildungen, Hochschule Mittweida, University of Applied Sciences, Fakultät Angewandte Computer- und Biowissen- schaften Bachelorarbeit, 2018 Dieses Werk ist urheberrechtlich geschützt. Referat Die vorliegende Arbeit erläutert, wo Browser gespeicherte Nutzerpasswörter ablegen und wie die- se zu entschlüsseln sind. Die Untersuchungen beziehen sich auf die vier derzeit meistgenutzten Browser Deutschlands, namentlich Google Chrome, Mozilla Firefox, Internet Explorer und Mi- crosoft Edge. Dabei wird auf diverse Verschlüsselungs-, Hashing- und Kodierungsverfahren ein- gegangen, die bei der Ver- und Entschlüsselung von Bedeutung sind. Insbesondere die Windows- eigene Data Protection API spielt eine übergeordnete Rolle bei der sicheren Speicherung von Passwörtern. Weiterführend wird die Entwicklung eines Programmes beschrieben, das die Browser-Passwörter per Knopfdruck aus Dateien bzw. -

Firefox Hacks Is Ideal for Power Users Who Want to Maximize The
Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader Firefox Hacks is ideal for power users who want to maximize the • Reviews effectiveness of Firefox, the next-generation web browser that is quickly • Errata gaining in popularity. This highly-focused book offers all the valuable tips • Academic and tools you need to enjoy a superior and safer browsing experience. Learn how to customize its deployment, appearance, features, and functionality. Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader • Reviews • Errata • Academic Copyright Credits About the Author Contributors Acknowledgments Preface Why Firefox Hacks? How to Use This Book How This Book Is Organized Conventions Used in This Book Using Code Examples Safari® Enabled How to Contact Us Got a Hack? Chapter 1. Firefox Basics Section 1.1. Hacks 1-10 Section 1.2. Get Oriented Hack 1. Ten Ways to Display a Web Page Hack 2. Ten Ways to Navigate to a Web Page Hack 3. Find Stuff Hack 4. Identify and Use Toolbar Icons Hack 5. Use Keyboard Shortcuts Hack 6. Make Firefox Look Different Hack 7. Stop Once-Only Dialogs Safely Hack 8. Flush and Clear Absolutely Everything Hack 9. Make Firefox Go Fast Hack 10. Start Up from the Command Line Chapter 2. Security Section 2.1. Hacks 11-21 Hack 11. Drop Miscellaneous Security Blocks Hack 12. Raise Security to Protect Dummies Hack 13. Stop All Secret Network Activity Hack 14. -

Software Management Full Installers Guide
Software Management Full Installers Guide Supported Platforms and Applications | Q1 2020 Software Management Full Installers Guide Release 9.5 | Q1 2020 www.kaseya.com 2 Software Management Full Installers Guide Release 9.5 | Q1 2020 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya’s “Click-Accept” EULATOS as updated from time to time by Kaseya at http://www.kaseya.com/legal.aspx. If Customer does not agree with the Agreement, please do not install, use or purchase any Software and Services from Kaseya as continued use of the Software or Services indicates Customer’s acceptance of the Agreement. www.kaseya.com Software Management Full Installers 3 Guide Release 9.5 | Q1 2020 Contents Installers Available 4 www.kaseya.com 4 Software Management Full Installers Guide Release 9.5 | Q1 2020 Installers Available Title Vendor URL 7-Zip File Archiver (Full Install) for Igor Pavlov http://www.7-zip.org/ Windows Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (Full Install) for Mac Systems, Inc OS X Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (de-DE) (Full Install) Systems, Inc for Windows Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (en-US) (Full Install) Systems, Inc for Windows Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (es-ES) (Full Install) Systems, Inc for Windows -

PDF Link Forces Download Instead of Open Document PDF Link Forces
PDF link forces download instead of open document • mozillaZine Forums http://forums.mozillazine.org/viewtopic.php?f=3&t=3010157&p=14636... Logout [ Andy Boze ] PDF link forces download instead of open document 0 new messages Post a reply User Control Panel View your posts First unread post • 13 posts • Page 1 of 1 Reply with quote ( ./posting.php?mode=quote&f=3&p=14631197 ) FAQ / Rules Report this post ( ./report.php?f=3&p=14631197 ) Members / Staff Posted Wed Jun 15, 2016 8:07 am A website I'm forced to use offers letters as pdf document. They might not want to pay for stamps and/or postage handling. When I click the link I do not get an open pdf document dialogue, but am forced to save the document Search locally. I then have to go to that location before I can open the document. When I complained about this procedure I got the answer that "this function differs per browser" and was invited to use a different browser... Boards (Advanced): I am not quite clear what has to happen behind the scenes to offer a pdf document from a database to the user, but forcing the user to another browser is a bit stiff in my opinion. Knowledge Base: Anyone care to comment? Mozilla/5.0 (Windows NT 10.0; WOW64; rv:43.0) Gecko/20100101 Firefox/43.0 SeaMonkey/2.40 Reply with quote ( ./posting.php?mode=quote&f=3&p=14631263 ) Report this post ( ./report.php?f=3&p=14631263 ) Posted Wed Jun 15, 2016 9:07 am Do other PDFs open in the browser for you? knowledge base If not, I like to install pdf.js ( https://github.com/mozilla/pdf.js/ ) in SeaMonkey to open PDFs (it's built into Firefox) - the XPI is here. -

Instalación Y Administración De Servicios De Correo Electrónico
Servicios de red e internet Instalación y administración de servicios de correo electrónico Raquel Castellanos Crespo Instalación y administración de servicios de correo electrónico Servicios de red e internet Raquel Castellanos Crespo INDICE Características del servicio de correo electrónico Elementos del servicio de correo electrónico -Agentes de correo electrónico. - Servidores de correo electrónico. Open relay y Smart host - Clientes de correo electrónico: entorno-DOS, gráficos y navegadores. - Direcciones, cuentas de correo y servidores DNS - Protocolos y servicios de descarga de correo: SMPT, ESMTP, POP, IMAP. Funcionamiento del servicio de correo electrónico Cuentas de correo, alias y buzones de correo Estructura de mensajes de correo electrónico - Cabecera, cuerpo, MIME Monitorización y registros del servicio de correo electrónico Servicio de correo electrónico vía web Correo seguro - Firma digital y cifrado de mensajes Veracidad del correo - Correo basura ("SPAM”) fraude, engaño, cadenas y virus informáticos 2 Servicios de red e internet | Instalación y administración de servicios de correo electrónico Servicios de red e internet Raquel Castellanos Crespo Características del servicio de correo electrónico Correo electrónico (correo-e, conocido también como e-mail ), es un servicio de red que permite a los usuarios enviar y recibir mensajes y archivos rápidamente (también denominados mensajes electrónicos o cartas electrónicas) mediante sistemas de comunicación electrónicos. Principalmente se usa este nombre para denominar al sistema que provee este servicio en Internet, mediante el protocolo SMTP, aunque por extensión también puede verse aplicado a sistemas análogos que usen otras tecnologías. Por medio de mensajes de correo electrónico se puede enviar, no solamente texto, sino todo tipo de documentos digitales. -

Whitepaper | IBM Domino Application Migration and Decommissioning
WHITEPAPER IBM Domino Application Migration and Decomissioning 1. Migration vs. Decommissioning As outlined above, an application migration can be very time-consuming - and it’s more likely to be than not to IBM Domino has been around for decades. Mid-sized to be. Therefore, the migration cannot be expected to be very large companies have built hundreds and thousands of completed short-term. In addition, it typically involves huge applications around IBM Domino that support their business financial investments. If the information that the application processes; many of those applications are business critical, maintains needs to be retained, maybe for a long period of e.g. because they store information that is subject to legal time, e.g. due to legal requirements, how should a company requirements. deal with this situation? But the IT world keeps changing. New technologies arise The answer to this question is »decommissioning«. When an nearly every day. Companies need to continuously review application is decommissioned, the application and its logic their IT strategy in order not to fall behind. are discarded whereas the data is maintained and kept in a Regarding IBM’s Domino offering there are quite a few way so that it is still accessible – at least for reading – even reasons why companies reassess their investments into that if the application that was used to create it is not available technology. Many of those companies already have decided anymore. or are in the process of deciding to move away from IBM Domino. They are looking at Enterprise Content Manage- ment (ECM) systems like Alfresco, OpenText Documentum, For the purpose of this document, migration is only OpenText, SharePoint etc.