Browser Support & Configuration Chrome Settings
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Using Emergent Team Structure to Focus Collaboration
Using Emergent Team Structure to Focus Collaboration by Shawn Minto B.Sc, The University of British Columbia, 2005 A THESIS SUBMITTED IN PARTIAL FULFILMENT OF THE REQUIREMENTS FOR THE DEGREE OF Master of Science The Faculty of Graduate Studies (Computer Science) The University Of British Columbia January 30, 2007 © Shawn Minto 2007 ii Abstract To build successful complex software systems, developers must collaborate with each other to solve issues. To facilitate this collaboration specialized tools are being integrated into development environments. Although these tools facilitate collaboration, they do not foster it. The problem is that the tools require the developers to maintain a list of other developers with whom they may wish to communicate. In any given situation, it is the developer who must determine who within this list has expertise for the specific situation. Unless the team is small and static, maintaining the knowledge about who is expert in particular parts of the system is difficult. As many organizations are beginning to use agile development and distributed software practices, which result in teams with dynamic membership, maintaining this knowledge is impossible. This thesis investigates whether emergent team structure can be used to support collaboration amongst software developers. The membership of an emergent team is determined from analysis of software artifacts. We first show that emergent teams exist within a particular open-source software project, the Eclipse integrated development environment. We then present a tool called Emergent Expertise Locator (EEL) that uses emergent team information to propose experts to a developer within their development environment as the developer works. We validated this approach to support collaboration by applying our ap• proach to historical data gathered from the Eclipse project, Firefox and Bugzilla and comparing the results to an existing heuristic for recommending experts that produces a list of experts based on the revision history of individual files. -

IE 6.0 Download and Set-Up Downloading Internet Explorer
IE 6.0 Download and Set-up To use the Web Commerce e-commerce service, you need to: • Gain access to the Internet • Install Microsoft™ Internet Explorer 6.0™ • Configure Temporary Internet files in Internet Explorer. • Configure AutoComplete in Internet Explorer. • Enable JavaScript in Internet Explorer. This tutorial provides detailed instructions to help you download and configure Internet Explorer 6.0 for use with Web Commerce application. Downloading Internet Explorer 6.0 Only Microsoft Internet Explorer 6 has the security features required to use the Web Commerce services. If you already have Internet access, you can use any Internet browser to download and install the most current version of IE, Internet Explorer 6. To download IE 6 from the Microsoft web site: 1. Go to the Microsoft Download Search page at: • http://www.microsoft.com/downloads/search.asp 1. Select the latest version of Internet Explorer (e.g.: Internet Explorer 6) from the Product Name drop-down list. 2. Select the operating system installed on your computer (e.g.: Windows 98) from the Operating System drop-down list. 3. Click the Find It! Button. A list of downloadable files appears. 4. Click Internet Explorer 6 from the list of files. A new browser window opens, which will allow you to specify which language version of IE you want to download. Exelon 2 5. Choose your preferred language and click the GO button. The next Windows File Download screen appears: 7. Click Internet Explorer 6 under the Download heading. A download box will open, select the Open Button, and the download for Internet Explorer 6 will commence. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Security Distributed and Networking Systems (507 Pages)
Security in ................................ i Distri buted and /Networking.. .. Systems, . .. .... SERIES IN COMPUTER AND NETWORK SECURITY Series Editors: Yi Pan (Georgia State Univ., USA) and Yang Xiao (Univ. of Alabama, USA) Published: Vol. 1: Security in Distributed and Networking Systems eds. Xiao Yang et al. Forthcoming: Vol. 2: Trust and Security in Collaborative Computing by Zou Xukai et al. Steven - Security Distributed.pmd 2 5/25/2007, 1:58 PM Computer and Network Security Vol. 1 Security in i Distri buted and /Networking . Systems Editors Yang Xiao University of Alabama, USA Yi Pan Georgia State University, USA World Scientific N E W J E R S E Y • L O N D O N • S I N G A P O R E • B E I J I N G • S H A N G H A I • H O N G K O N G • TA I P E I • C H E N N A I Published by World Scientific Publishing Co. Pte. Ltd. 5 Toh Tuck Link, Singapore 596224 USA office: 27 Warren Street, Suite 401-402, Hackensack, NJ 07601 UK office: 57 Shelton Street, Covent Garden, London WC2H 9HE British Library Cataloguing-in-Publication Data A catalogue record for this book is available from the British Library. SECURITY IN DISTRIBUTED AND NETWORKING SYSTEMS Series in Computer and Network Security — Vol. 1 Copyright © 2007 by World Scientific Publishing Co. Pte. Ltd. All rights reserved. This book, or parts thereof, may not be reproduced in any form or by any means, electronic or mechanical, including photocopying, recording or any information storage and retrieval system now known or to be invented, without written permission from the Publisher. -

Towards Dependable Dynamic Component-Based Applications
THÈSE Pour obtenir le grade de DOCTEUR DE L’UNIVERSITÉ DE GRENOBLE Spécialité : Informatique Arrêté ministériel : 7 août 2006 Présentée par Kiev SANTOS DA GAMA Thèse dirigée par Didier DONSEZ préparée au sein du Laboratoire d’Informatique de Grenoble dans l'École Doctorale Mathématiques, Sciences et Technologies de l’Information, Informatique (MSTII) Towards Dependable Dynamic Component-based Applications Thèse soutenue publiquement le « 6 Octobre 2011», devant le jury composé de : Mme Claudia RONCANCIO Professeur, Ensimag - Grenoble INP, Président M Gilles MULLER Directeur de Recherche, INRIA, Rapporteur M Lionel SEINTURIER Professeur, Université de Lille & IUF, Rapporteur M Ivica CRNKOVIC Professor, Mälardalen University, Membre M Didier DONSEZ Professeur, Université Joseph Fourier, Membre M Gaël THOMAS Maître de Conférences, Université Pierre et Marie Curie, Membre M Peter KRIENS Technical Director, OSGi Alliance, Invité ABSTRACT Software is moving towards evolutionary architectures that are able to easily accommodate changes and integrate new functionality. This is important in a wide range of applications, from plugin-based end user applications to critical applications with high availability requirements. Dynamic component-based platforms allow software to evolve at runtime, by allowing components to be loaded, and executed without forcing applications to be restarted. However, the flexibility of such mechanism demands applications to cope with errors due to inconsistencies in the update process, or due to faulty behavior from components introduced during execution. This is mainly true when dealing with third-party components, making it harder to predict the impacts (e.g., runtime incompatibilities, application crashes) and to maintain application dependability when integrating such third-party code into the application. -

Peer Participation and Software
Peer Participation and Software This report was made possible by the grants from the John D. and Cath- erine T. MacArthur Foundation in connection with its grant-making initiative on Digital Media and Learning. For more information on the initiative visit www.macfound.org. The John D. and Catherine T. MacArthur Foundation Reports on Digital Media and Learning Peer Participation and Software: What Mozilla Has to Teach Government by David R. Booth The Future of Learning Institutions in a Digital Age by Cathy N. Davidson and David Theo Goldberg with the assistance of Zoë Marie Jones The Future of Thinking: Learning Institutions in a Digital Age by Cathy N. Davidson and David Theo Goldberg with the assistance of Zoë Marie Jones New Digital Media and Learning as an Emerging Area and “Worked Examples” as One Way Forward by James Paul Gee Living and Learning with New Media: Summary of Findings from the Digital Youth Project by Mizuko Ito, Heather Horst, Matteo Bittanti, danah boyd, Becky Herr-Stephenson, Patricia G. Lange, C. J. Pascoe, and Laura Robinson with Sonja Baumer, Rachel Cody, Dilan Mahendran, Katynka Z. Martínez, Dan Perkel, Christo Sims, and Lisa Tripp Young People, Ethics, and the New Digital Media: A Synthesis from the GoodPlay Project by Carrie James with Katie Davis, Andrea Flores, John M. Francis, Lindsay Pettingill, Margaret Rundle, and Howard Gardner Confronting the Challenges of Participatory Culture: Media Education for the 21st Century by Henry Jenkins (P.I.) with Ravi Purushotma, Margaret Weigel, Katie Clinton, and Alice J. Robison The Civic Potential of Video Games by Joseph Kahne, Ellen Middaugh, and Chris Evans Peer Production and Software What Mozilla Has to Teach Government David R. -

Internet Explorer Users Are Required to Add the Portal URL to Trusted Sites
CLA Client Portal Browser and Silverlight FAQs 1. Question: I am receiving an “Error 500” when clicking the link to access the CLA Document Portal. Resolution: Verify with your IT department that the portal is not blocked by any internal monitoring or protection applications. 2. Question: How do I know if my computer has Microsoft Silverlight Installed? Resolution: The first time you try and login to the portal you will be prompted to install Silverlight from Microsoft’s website if you don’t have it already installed. The installation typically takes less than one minute and is completely safe. http://www.microsoft.com/getsilverlight/Get-Started/Install/Default.aspx If you cannot, or prefer not to, install Silverlight on your machine, a simplified version of the document portal that does not require Silverlight is available. Click on the Take me to the non- Silverlight login on the CLA Document Portal page (www.claconnect.com/docportal). 3. Question: I cannot access the CLA Document Portal. (Server error/Page not found) Resolution: Check that you are using a Microsoft Silverlight 4 compatible browser on all PC’s or MAC. A complete list of browsers and operating systems that support Silverlight 4 can be found at http://www.microsoft.com/getsilverlight/locale/en-us/html/installation-win-SL4.html Please note: Internet Explorer users are required to add the portal URL to Trusted Sites. Adding to Trusted Sites Internet Explorer settings 1. Open Internet Explorer and browse to https://portal.cchaxcess.com/Portal/. 2. In Internet Explorer, select Tools / Internet Options; then select the Security tab and click Trusted Sites and then Sites. -

Organizational Search in Email Systems Sruthi Bhushan Pitla Western Kentucky University, [email protected]
Western Kentucky University TopSCHOLAR® Masters Theses & Specialist Projects Graduate School 5-2012 Organizational Search in Email Systems Sruthi Bhushan Pitla Western Kentucky University, [email protected] Follow this and additional works at: http://digitalcommons.wku.edu/theses Part of the Databases and Information Systems Commons Recommended Citation Pitla, Sruthi Bhushan, "Organizational Search in Email Systems" (2012). Masters Theses & Specialist Projects. Paper 1161. http://digitalcommons.wku.edu/theses/1161 This Thesis is brought to you for free and open access by TopSCHOLAR®. It has been accepted for inclusion in Masters Theses & Specialist Projects by an authorized administrator of TopSCHOLAR®. For more information, please contact [email protected]. ORGANIZATIONAL SEARCH IN EMAIL SYSTEMS A Thesis Presented to The Faculty of the Department of Mathematics and Computer Science Western Kentucky University Bowling Green, Kentucky In Partial Fulfillment Of the Requirements for the Degree Master of Science By Sruthi Bhushan Pitla May 2012 ACKNOWLEDGMENTS It was a great pleasure working under my graduate advisor, Dr. Guangming Xing, who provided me with everything I need to succeed. His inspiration and guidance at each and every step made this Master of Science degree so rewarding and satisfactory. He always encouraged my work in every possible way and also gave me the freedom to express and implement my ideas without any restrictions. I feel very fortunate and proud to have been his student and really think the experience which I gained working under him is invaluable. I would like to whole heartedly thank Dr. Xing for the immense trust and patience he has over me. -

Bachelorarbeit
BACHELORARBEIT Frau Kristina Martin Extraktion von Passworthashes und Ermittlung von Passwörtern aus Browserapplikationen im Rahmen der Post-Mortem-Analyse 2018 Fakultät Angewandte Computer- und Biowissenschaften BACHELORARBEIT Extraktion von Passworthashes und Ermittlung von Passwörtern aus Browserapplikationen im Rahmen der Post-Mortem-Analyse Autorin: Kristina Martin Studiengang: Allgemeine und digitale Forensik Seminargruppe: FO15w3-B Betreuer der Hochschule:: Prof. Dr. rer. nat. Christian Hummert Betreuer am Landeskriminalamt Thüringen: Dipl.-Inf. Andreas Sommer Mittweida, August 2018 Faculty Applied Computer Sciences & Biosciences BACHELOR THESIS Extraction of Password Hashes and Decryption of Passwords stored by Browser Applications on the Basis of a Post-Mortem-Analysis Authorin: Kristina Martin Study Programme: General and Digital Forensic Science Seminar Group: FO15w3-B First Referee:: Prof. Dr. rer. nat. Christian Hummert Second Referee: Dipl.-Inf. Andreas Sommer Mittweida, August 2018 Bibliografische Angaben Martin, Kristina: Extraktion von Passworthashes und Ermittlung von Passwörtern aus Browser- applikationen im Rahmen der Post-Mortem-Analyse, 95 Seiten, 49 Abbildungen, Hochschule Mittweida, University of Applied Sciences, Fakultät Angewandte Computer- und Biowissen- schaften Bachelorarbeit, 2018 Dieses Werk ist urheberrechtlich geschützt. Referat Die vorliegende Arbeit erläutert, wo Browser gespeicherte Nutzerpasswörter ablegen und wie die- se zu entschlüsseln sind. Die Untersuchungen beziehen sich auf die vier derzeit meistgenutzten Browser Deutschlands, namentlich Google Chrome, Mozilla Firefox, Internet Explorer und Mi- crosoft Edge. Dabei wird auf diverse Verschlüsselungs-, Hashing- und Kodierungsverfahren ein- gegangen, die bei der Ver- und Entschlüsselung von Bedeutung sind. Insbesondere die Windows- eigene Data Protection API spielt eine übergeordnete Rolle bei der sicheren Speicherung von Passwörtern. Weiterführend wird die Entwicklung eines Programmes beschrieben, das die Browser-Passwörter per Knopfdruck aus Dateien bzw. -

Working with Html, Css, and Http
Chapter 2 WORKING WITH HTML, CSS, AND HTTP Working with HTML An essential aspect of running a website is creating HTML files. Even sites that rely heavily on page technologies other than static HTML, such as script-driven pages, inevitably keep many static HTML files on the site. Although Web authors can write HTML in any text editor, many have adopted specialized HTML editor programs to handle the job. Ideally, an HTML editor should manage the job of converting an authors writing into the structures defined by the HTML standard without requiring the author to know the details of that standard. As the job is accomplished, the editor program may carry out additional tasks, such as letting the author fine-tune the finished documents appearance or handling site management tasks such as uploading documents to a server and checking its links. The most widely used HTML editors handle these secondary tasks with great success. Over the years, however, many designers created their actual HTML code with an emphasis on appearance rather than structure. This so-called presentational markup achieved popularity with an older generation of browsers because no widely supported alternative to controlling an HTML documents appearance was available. Presentational HTML has drawbacks, though, and a growing number of Web authors are abandoning it in favor of HTML markup that describes a documents structure. Reasons for this choice include: Library Technology Reports Many aspects of presentational markup make assumptions about the users display environment (specifically, screen resolution and window width) that are increasingly unwarranted and may lead to accessibility problems. -
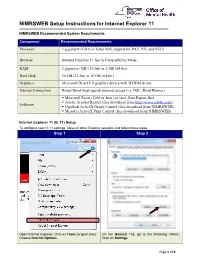
NIMRSWEB Setup Instructions for Internet Explorer 6
NIMRSWEB Setup Instructions for Internet Explorer 11 NIMRSWEB Recommended System Requirements Component Recommended Requirements Processor 1 gigahertz (GHz) or faster with support for PAE, NX, and SSE2 Browser Internet Explorer 11 Set in Compatibility Mode RAM 1 gigabyte (GB) (32-bit) or 2 GB (64-bit) Hard Disk 16 GB (32-bit) or 20 GB (64-bit) Graphics Microsoft DirectX 9 graphics device with WDDM driver Internet Connection Broad Band (high speed) internet access (i.e. DSL, Road Runner) . Microsoft Excel (2000 or later) to view Data Export files . Adobe Acrobat Reader (free download from http://www.adobe.com) Software . GigaSoft ActiveX Graph Control (free download from NIMRSWEB) . MeadCo ActiveX Print Control (free download from NIMRSWEB) Internet Explorer 11 (IE 11) Setup To configure your IE 11 settings, close all other Explorer sessions and follow these steps. Step 1 Step 2 Open Internet Explorer, Click on Tools (or gear icon). On the General Tab, go to the Browsing history. Choose Internet Options. Click on Settings. Page 1 of 4 Internet Explorer 11 CM Settings for NIMRS Web Step 3 Step 4 Select “Every time I visit the webpage”. Click Click on the Security Tab. OK. Choose Trusted Sites icon and Click on Sites. Step 5 Step 6 In “Add this Web site to the zone:” Click on Privacy Tab. Type “https://*.ny.gov”, Click Add. On the Pop-up Blocker section, click on Settings. Type “https://*.omh.state.ny.us”, Click Add and Close Page 2 of 4 Internet Explorer 11 CM Settings for NIMRS Web Step 7 Step 8 In “Address of website to allow:” Click OK . -

Why Websites Can Change Without Warning
Why Websites Can Change Without Warning WHY WOULD MY WEBSITE LOOK DIFFERENT WITHOUT NOTICE? HISTORY: Your website is a series of files & databases. Websites used to be “static” because there were only a few ways to view them. Now we have a complex system, and telling your webmaster what device, operating system and browser is crucial, here’s why: TERMINOLOGY: You have a desktop or mobile “device”. Desktop computers and mobile devices have “operating systems” which are software. To see your website, you’ll pull up a “browser” which is also software, to surf the Internet. Your website is a series of files that needs to be 100% compatible with all devices, operating systems and browsers. Your website is built on WordPress and gets a weekly check up (sometimes more often) to see if any changes have occured. Your site could also be attacked with bad files, links, spam, comments and other annoying internet pests! Or other components will suddenly need updating which is nothing out of the ordinary. WHAT DOES IT LOOK LIKE IF SOMETHING HAS CHANGED? Any update to the following can make your website look differently: There are 85 operating systems (OS) that can update (without warning). And any of the most popular roughly 7 browsers also update regularly which can affect your site visually and other ways. (Lists below) Now, with an OS or browser update, your site’s 18 website components likely will need updating too. Once website updates are implemented, there are currently about 21 mobile devices, and 141 desktop devices that need to be viewed for compatibility.