Interim Progress Report
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chartbook on Women's Progress
FUTURE OF WORK@50+ NOVEMBERMONTH 2015 Research Report Looking Back, Looking Ahead: Chartbook on Women’s Progress Ariane Hegewisch Jeff Hayes Jessica Milli Elyse Shaw Heidi Hartmann Institute for Women’s Policy Research Acknowledgments We would like to thank the following members of the AARP Public Policy Institute and AARP’s Office of Policy Integration for their contributions to this paper: Lori Trawinski, Sara Rix, Donald Redfoot, Christina Fitzpatrick, Gary Koenig, Mikki Waid, Alison Shelton, and Julia Alexis. Also, we would like to thank Allison Porter for her assistance as well as an external, anonymous peer reviewer for their time and valuable contributions. AARP’s Public Policy Institute informs and stimulates public debate on the issues we face as we age. Through research, analysis, and dialogue with the About the Future of Work@50+ nation’s leading experts, PPI promotes development of sound, creative policies This report is part of the Future of Work@50+ Initiative. to address our common need for This is a multiyear initiative that examines the challenges economic security, health care, and and opportunities facing older workers. For other reports and quality of life. information, visit: http://www.aarp.org/futureofwork. The views expressed herein are for information, debate, and discussion, and do not necessarily represent official policies of AARP. LOOKING BACK, LOOKING AHEAD: CHARTBOOK ON WOMEN’S PROGRESS i Table of Contents ACKNOWLEDGMENTS ..............................................................................................................................................i -

NAEP 2008 Trends in Academic Progress
Institute of Education Sciences U.S. Department of Education NCES 2009–479 NAEP 2008 Trends in Academic Progress READING 1971–2008 MATHEMATICS 1973–2008 CONTENTS Executive Summary 2 Executive Summary 6 Introduction This report presents the results of the NAEP long- 8 The Long-Term Trend Assessment term trend assessments in reading and mathemat- in Reading ics, which were most recently given in the 2007–08 28 The Long-Term Trend Assessment school year to students at ages 9, 13, and 17. Nationally representative samples of over 26,000 in Mathematics public and private school students were assessed 50 Technical Notes in each subject area. 53 Appendix Tables The long-term trend assessments make it possible to chart educational progress since the early 1970s. Results in reading are available for 12 assessments going back to the rst in 1971. The rst of 11 assess- ments in mathematics was administered in 1973. What is Throughout this report, the most recent results are compared to those from 2004 and from the rst year The Nation’s the assessment was conducted. ™ Report Card ? The original assessment format, content, and proce- dures were revised somewhat in 2004 to update content The Nation’s Report Card™ informs the public about and provide accommodations to students with disabili- the academacademicic achachievementievement ooff elementarelementaryy and ties and English language learners. The knowledge and secondary students in the United StatesStates. Report skills assessed, however, remain essentially the same cards communicate the findings of the National since the rst assessment year. Assessment of Educational Progress (NAEP), a continuing and nationally representative measure Improvements seen in reading and of achievement in various subjects over time. -

Project Progress Report Reporting Period: June 2017 – November 2017
PROJECT PROGRESS REPORT REPORTING PERIOD: JUNE 2017 – NOVEMBER 2017 SIX-MONTHLY PROGRESS REPORT REPORTING PERIOD: JUNE 2017 - NOVEMBER 2017 Report Title : Six-monthly progress report Reporting period: June 2017 to November 2017 Report Status : FINAL Project Ref : WPD/EN/NIC/02 - OpenLV Date : 08.12.2017 Document Control Name Date Prepared by: R. Potter 08.12.2017 Reviewed by: D. Hollingworth/M. 08.12.2017 Dale Recommended by: D.Roberts/ R. Hey 08.12.2017 Approved (WPD): A.Sleightholm 08.12.2017 Revision History Date Issue Status 03.11.2017 0.1 DRAFT 08.12.2017 1.0 FINAL Page 2 of 36 SIX-MONTHLY PROGRESS REPORT REPORTING PERIOD: JUNE 2017 - NOVEMBER 2017 Contents 1 Executive Summary ................................................................................................................ 6 1.1 Overall Project Progress ............................................................................................... 6 1.2 Business Case ............................................................................................................... 6 1.3 Project Learning and Dissemination ............................................................................ 6 1.4 Risks .............................................................................................................................. 7 2 Project Manager’s Report ...................................................................................................... 8 2.1 Project Background ..................................................................................................... -

Module 3 Slide Handouts
Pathways of Progress™ Module 3: The Logic Behind Pathways of Progress TM Three Guiding Principles in Establishing Pathways of Progress Matter Individual Student Learning Goals • We know that the level of skills for a student at the Meaningful. beginning of the year is an important predictor of their – Goals should support students to achieve meaningful outcomes or increase the likelihood of achieving meaningful and important end of year outcome (partial eta squared = 71%). outcomes. • Pathways of Progress contributes to initial skills in Ambitious. predicting later outcomes (partial eta squared = 17%). – Above typical or well above typical progress are ambitious goals. – Typical progress may be sufficient for students who are at or above benchmark – Typical progress may not be adequate for students who are likely to need additional support to achieve benchmark goals. – Below typical or well below typical progress are just not very ambitious. Attainable. – High in the well above typical range is probably not attainable. – Typical and above typical progress is readily attainable. – Well below typical and below typical progress may be attainable, but are not ambitious or meaningful. Pathways of ProgressTM ©2015 Dynamic Measurement Group 33 Pathways of ProgressTM ©2015 Dynamic Measurement Group 34 Considerations in Establishing Considerations in Establishing Student Learning Goals Student Learning Goals DIBELS Next informed considerations: Other considerations: What rate of progress is above typical progress What rate of progress is possible with a very compared to other students with similar initial skills? effective, research based intervention? What rate of progress is necessary to narrow the What resources are available to support instruction achievement gap with students making adequate and intervention? progress? What is the student attendance pattern? What rate of progress is necessary to achieve important benchmark goals. -
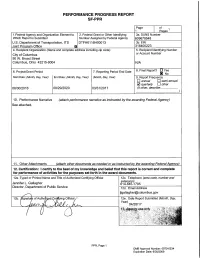
Quarterly Progress Report
Quarterly Progress Report Award Information Title Award # Awardee Smart City Challenge DTFH6116H00013 City of Columbus Demonstration Report Information Date Submitted Submitted To Period Covered by Report May 18, 2017 Kate Hartman January 2017 - March 2017 Project Scope Scope Statement Implementation of the Smart Columbus Smart City Demonstration consisting of 15 projects spread across 2 enabling Technologies and 4 Districts: 1. Columbus Connected Transportation Network (CCTN) 1. Connected Vehicle Environment 2. Smart Street Lighting 3. Transit Pedestrian Collision Avoidance System 2. Integrated Data Exchange (IDE) 4. IDE 3. Residential District 5. Common Payment System 6. Multi-Modal Trip Planning Application 7. Smart Mobility Hubs 8. Mobility Assistance for People with Cognitive Disabilities 4. Commercial District 9. Connected Electric Automated Vehicles 5. Downtown District 10. Delivery Zone Availability 11. Enhanced Permit Parking 12. Event Parking Management 6. Logistics District 13. Truck Platooning 14. Oversize Vehicle Routing 15. Interstate Truck Parking Availability 1 Financial Status Task Financial Summary (See Note 1) Note 1: After last quarter’s report we agreed the City’s labor cost would all stay within Program Management. Task 3 was to be broken down by its two components and Task 4 was to be broken down by its four components. We are still working on breaking task 3 and 4 into the components and anticipate reporting expenses that way on the next quarterly report. Costs Incurred vs Budgeted Costs Costs Incurred vs Obligated Federal Funding Direct Labor Hours Worked (See Note 2) 2 Note 2: Some hours were estimated on the last quarterly report. There are no estimated hours on this report. -

National Seed Strategy
NATIONAL SEED STRATEGY for Rehabilitation and Restoration Making Progress The Plant Conservation Alliance (PCA) is a public-private partnership of organizations that share the same goal: to protect native plants by ensuring that native plant populations and their communities are maintained, enhanced, and restored. The PCA Federal Committee, chaired by the Bureau of Land Management, developed the “National Seed Strategy for Rehabilitation and Restoration 2015-2020” in cooperation with federal and non-federal partners. For more information on the Plant Conservation Alliance and its members and activities, please visit http://www.blm.gov/pca. Copies of this publication may be obtained online at www.blm.gov/seedstrategy. NATIONAL SEED STRATEGY Making Progress 2 Table of Contents National Seed Strategy for Rehabilitation and Restoration: Making Progress ............................................ 5 Status by Goal ............................................................................................................................................... 6 Goal One ............................................................................................................................................... 6 Goal Two ............................................................................................................................................... 8 Goal Three ............................................................................................................................................. 9 Goal Four ............................................................................................................................................ -
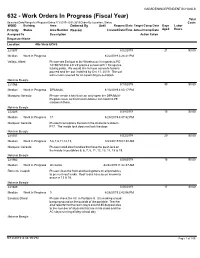
Work Orders in Progress
GADSDEN INDEPENDENT SCHOOLS 632 - Work Orders In Progress (Fiscal Year) Total Selected Date Range for Request Dates:7/1/2019 - 8/31/2019 Order By Location, Status Costs WOID Building Area Deferred By Until Request Date Target Comp Date Days Labor Priority Status Area Number Reason Created Date/Time Actual Comp Date Aged Hours Assigned To Description Action Taken Requester Name Location: Alta Vista ECHS 221677 8/22/2019 21 $0.00 Medium Work In Progress 8/22/2019 3:24:41 PM Vallejo, Albert Please see Enrique at the Warehouse in regards to PO 181907203 for a 5' x 5' plasma cut owl with 1 1/4 square tubing posts. We would like to have concrete footers poured and the owl installed by Oct. 11, 2019. The owl will remain covered for an assembly presentation. Melanie Beegle 221066 8/13/2019 30 $0.00 Medium Work In Progress DPA Multi- 8/13/2019 4:03:17 PM Marquez, Gerardo Please create a key that can only open the DPA Multi- Purpose room so that Coach Adame can hold his PE classes in there. Melanie Beegle 222025 8/28/2019 15 $0.00 Medium Work In Progress 17 8/28/2019 4:47:32 PM Marquez, Gerardo Please fix or replace the lock in the students restroom, P17. The inside lock does not lock the door. Melanie Beegle 221707 8/23/2019 20 $0.00 Medium Work In Progress 5,6,7,8,11,12,13, 8/23/2019 9:03:30 AM Marquez, Gerardo Please install door handles that have the push lock on the inside in portables 5, 6, 7, 8, 11, 12, 13, 14, 18 & 19. -

Pilgim's Progress by John Bunyan
Bunyan: Pilgrim’s Progress 1 The Pilgrim's Progress By John Bunyan, John (1628-1688) www.ccel.org Public Domain Bunyan: Pilgrim’s Progress 2 The Pilgrim's Progress From This World to That Which is to Come; Delivered under the Similitude of a Dream by John Bunyan (1628-1688) Auburn: Derby and Miller. Buffalo: Geo. H. Derby and Co. 1853 Bunyan: Pilgrim’s Progress 3 CONTENTS [1]Author's Apology for his Book [2]PART I. [3]The First Stage. --Christian's deplorable condition--Evangelist directs him--Obstinate and Pliable--Slough of Despond--Worldly Wiseman--Mount Sinai--Conversation with Evangelist [4]The Second Stage. --The Gate--conversation with Good-Will--the Interpreter's House--Christian entertained--the sights there shown him [5]The Third Stage. --Loses his burden at the Cross--Simple, Sloth, Presumption, Formalist, Hypocrisy--hill Difficulty--the Arbor--misses his roll--the palace Beautiful--the lions--talk with Discretion, Piety, Prudence, and Charity--wonders shown to Christian--he is armed [6]The Fourth Stage. --Valley of Humiliation--conflict with Apollyon--Valley of the Shadow of Death--Giants Pope and Pagan [7]The Fifth Stage. --Discourse with Faithful--Talkative and Faithful--Talkative's character [8]The Sixth Stage. --Evangelist overtakes Christian and Faithful--Vanity Fair--the Pilgrims brought to trial--Faithful's mareyrdom [9]The Seventh Stage. --Christian and Hopeful--By-ends and his companions--plain of Ease--Lucre-hill--Demas--the River of Life--Vain-Confidence--Giant Despair--the Pilgrims beaten--the Dungeon--the Key of Promise [10]The Eighth Stage. --The Delectable Mountains--entertained by the Shepherds--a by-way to Hell [11]The Ninth Stage. -

A Revolution in Progress
ADUs in CA: A Revolution in Progress | October 2020 | Center for Community Innovation Authors: Karen Chapple, Audrey Lieberworth, Dori Ganetsos, Eric Valchuis, Andrew Kwang & Rachel Schten Acknowledgments We are grateful to the California Department of Housing and Community Development for the funding that helped support this research. We also thank Jenny Liang, Lauren Hom, Jen Hu, and Isaac Schmidt for their invaluable research assistance. The Center for Community Innovation (CCI) at UC Berkeley nurtures effective solutions that expand economic opportunity, diversify housing options, and strengthen connection to place. Center for Community Innovation c/o Institute of Governmental Studies 109 Moses Hall, #2370 Berkeley, CA 94720-237 Table of Conents Table of Contents Executive Summary . 5 Introduction . 7 Methods . 9 Trends in ADU Implementation . 12 Barriers to ADU Development . 18 Best Practices . 23 Missing Middle . 27 Conclusion & Recommendations. 30 Endnotes . 31 Appendices . 33 ADUs in California: A Revolution in Progress 3 Executive Summary Executive Summary Executive Summary Introduction But Barriers Remain In order to address the California (CA) housing crisis, state leg- • Finances (27%), lack of awareness (16%), and lack of desire islators are pursuing zoning reform to allow more small-scale (16%) remain significant barriers to ADU development. Juris- housing types, particularly in low density neighborhoods. Ac- dictions also report that the State’s top-down approach to cessory dwelling units (ADUs), commonly known as secondary this series of ADU legislation presents challenges for local units, backyard cottages, and in-law units, are one such housing ADU construction. type. Over the past few years, state legislators reduced parking requirements, lot size minimums and setback requirements, and • Although lower income and lower resource communities in development fees to incentivize construction of ADUs. -
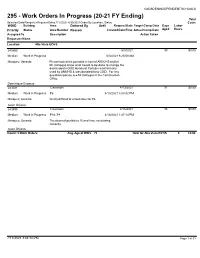
Work Orders in Progress
GADSDEN INDEPENDENT SCHOOLS 295 - Work Orders In Progress (20-21 FY Ending) Total Selected Date Range for Request Dates:7/1/2020 - 6/30/2021 Order By Location, Status Costs WOID Building Area Deferred By Until Request Date Target Comp Date Days Labor Priority Status Area Number Reason Created Date/Time Actual Comp Date Aged Hours Assigned To Description Action Taken Requester Name Location: Alta Vista ECHS 245650 6/3/2021 40 $0.00 Medium Work In Progress 6/3/2021 8:25:08 AM Marquez, Gerardo Please look at the portable in front of AVECHS and let Mr. Gallegos know what needs to be done to change the doorknobs to GISD standard. Portable was formally used by SNMHD & was donated to to GISD. For any questions please see Mr. Gallegos in the Construction Office. Dominique Esparza 243331 Classroom 4/13/2021 91 $0.00 Medium Work In Progress P6 4/13/2021 5:03:42 PM Marquez, Gerardo Really difficult to unlock door for P6 Isaac Grijalva 243490 Classroom 4/16/2021 88 $0.00 Medium Work In Progress P16, P8 4/16/2021 1:47:14 PM Marquez, Gerardo The doors of portables 16 and 8 are not closing correctly. Isaac Grijalva Count: 3 Work Orders Avg. Age of WO's 73 Total for Alta Vista ECHS 0 $0.00 7/13/2021 3:46:14 PM Page 1 of 61 Page 1 of 61 GADSDEN INDEPENDENT SCHOOLS 295 - Work Orders In Progress (20-21 FY Ending) Total Selected Date Range for Request Dates:7/1/2020 - 6/30/2021 Order By Location, Status Costs WOID Building Area Deferred By Until Request Date Target Comp Date Days Labor Priority Status Area Number Reason Created Date/Time Actual Comp Date Aged Hours Assigned To Description Action Taken Requester Name Location: Anthony - On Track Pre-K (Village) 243742 Portables 4/22/2021 82 $0.00 Medium Work In Progress headstart area 4/22/2021 9:18:47 AM Marquez, Gerardo Fix door on the east side of portable due to vandalism Michelle Soto 243817 Classroom 4/23/2021 81 $0.00 Medium Work In Progress 107, 109, 111 4/23/2021 12:03:07 PM Marquez, Gerardo Teachers cannot open their classroom doors. -

Students Monitor Academic Progress 1 STUDENTS MONITOR
Students Monitor Academic Progress 1 STUDENTS MONITOR ACADEMIC PROGRESS USING DATA FOLDERS TO SEE IF ACADEMIC GAINS ARE MADE By JEANNE PEACOCK Submitted to The Educational Leadership Faculty Northwest Missouri State University Missouri Department of Educational Leadership College of Education and Human Services Maryville, MO 64468 Submitted in Fulfillment for the Requirements for 61‐683 Research Paper Summer 2013 July 19, 2014 Students Monitor Academic Progress 2 ABSTRACT The purpose of this study was to analyze elementary student’s academic gains when they monitored their own progress in the areas of reading Dolch Sight Words, Spelling and Math. These students don’t typically monitor their academic progress; it is done by the Special Education Teacher. Progress towards academic goals is made; but there is often regression and progress is typically slow. The research includes findings that answer the question, “Are there academic gains when elementary students monitor their progress using student Data Folders?” In order for the students to have complete ownership of their learning they created their own Data Folders. They created the graph paper and put a title at the top for each subject. After each informal assessment, the students graphed their percentage on the appropriate data graph. The study was conducted during the 2013-2014 school year and compared to the 2012-2013 school year when these same students did not monitor their progress. Six students were involved in this study and their names are anonymous. The findings were analyzed through A Statistical Program (ASP) software. Findings indicate that there is a difference between the progress elementary students’ make when they monitor their own academic progress and when they do not monitor their own academic progress. -

Developing Achievement Levels on the 2011 National Assessment of Educational Progress in Grades 8 and 12 Writing Process Report
National Assessment Governing Board Developing Achievement Levels on the National Assessment of Educational Progress in Writing Grades 8 and 12 in 2011 Submitted to: National Assessment Governing Board 800 North Capitol Street, NW, Suite 825 Washington, DC 02002-4233 Phone: 202.357.6938 This study was funded by the National Assessment Governing Board under Contract ED-NAG-10-C-0003. Submitted by: Measured Progress 100 Education Way Dover, NH 03820 Phone: 603.749.9102 ALS Writing Process Report September 2012 PANELIST NAMES REDACTED BY GOVERNING BOARD Developing Achievement Levels on the 2011 National Assessment of Educational Progress in Grades 8 and 12 Writing Process Report Luz Bay with Chris Clough Jennifer Dunn Wonsuk Kim Leah McGuire Tia Sukin September 2012 ALS Writing Process Report Measured Progress ii National Assessment Governing Board BOARD MEMBERSHIP (2011–2012) Honorable David P. Driscoll, Chair Former Commissioner of Education Melrose, Massachusetts Mary Frances Taymans, SND, Vice Chair Sisters of Notre Dame National Education Office Bethesda, Maryland Andrés Alonso Shannon Garrison Chief Executive Officer Fourth-Grade Teacher Baltimore City Public Schools Solano Avenue Elementary School Baltimore, Maryland Los Angeles, California David J. Alukonis Doris R. Hicks Former Chairman Principal and Chief Executive Officer Hudson School Board Dr. Martin Luther King, Jr. Charter School Hudson, New Hampshire for Science and Technology New Orleans, Louisiana Louis M. Fabrizio Data, Research and Federal Policy Director Honorable Terry Holliday North Carolina Department of Public Commissioner of Education Instruction Kentucky Department of Education Raleigh, North Carolina Lexington, Kentucky Honorable Anitere Flores Richard Brent Houston Senator Principal Florida State Senate Shawnee Middle School Miami, Florida Shawnee, Oklahoma Alan J.