Musings Rity Professionals and CS Researchers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Downloadable Email Program for My Pc 32 Best Free Email Clients
downloadable email program for my pc 32 Best Free Email Clients. Here are 32 best free email client software . These let you manage and access all of your email accounts in one single place easily. All these email client software are completely free and can be downloaded to Windows PC. These free software offer various features, like: can be used with IMAP, SMTP, POP3 and Gmail, keeps your emails safe and secure, lets you open various emails simultaneously, provide protection from spam, lets you view your emails offline, manage and access all of your email accounts in one single place, supports PH, LDAP, IMAP4, POP3 and SMPT mail protocols etc. So, go through this list of free email client software and see which ones you like the most. Thunderbird. Thunderbird is a free and handy email client software for your computer. It can be used with IMAP, SMTP, POP3 and Gmail. It will also work with email accounts provided by MS Exchange Server. The user interface of Thunderbird is tabbed. It lets you open various emails simultaneously. Thunderbird keeps your emails safe and secure. It also has special filters for filtering the mail. Windows Live Mail. Windows Live Mail is a free email client for your computer. It works with various email accounts. It lets you access Yahoo, Gmail, Hotmail and emails from different servers which supports POP3 and SMTP. Its security features are excellent it will also provide protection from spam. You can also view your emails offline in this freeware. Zimbra Desktop. Zimbra Desktop is a free email client. -

Web Browser a C-Class Article from Wikipedia, the Free Encyclopedia
Web browser A C-class article from Wikipedia, the free encyclopedia A web browser or Internet browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier (URI) and may be a web page, image, video, or other piece of content.[1] Hyperlinks present in resources enable users to easily navigate their browsers to related resources. Although browsers are primarily intended to access the World Wide Web, they can also be used to access information provided by Web servers in private networks or files in file systems. Some browsers can also be used to save information resources to file systems. Contents 1 History 2 Function 3 Features 3.1 User interface 3.2 Privacy and security 3.3 Standards support 4 See also 5 References 6 External links History Main article: History of the web browser The history of the Web browser dates back in to the late 1980s, when a variety of technologies laid the foundation for the first Web browser, WorldWideWeb, by Tim Berners-Lee in 1991. That browser brought together a variety of existing and new software and hardware technologies. Ted Nelson and Douglas Engelbart developed the concept of hypertext long before Berners-Lee and CERN. It became the core of the World Wide Web. Berners-Lee does acknowledge Engelbart's contribution. The introduction of the NCSA Mosaic Web browser in 1993 – one of the first graphical Web browsers – led to an explosion in Web use. Marc Andreessen, the leader of the Mosaic team at NCSA, soon started his own company, named Netscape, and released the Mosaic-influenced Netscape Navigator in 1994, which quickly became the world's most popular browser, accounting for 90% of all Web use at its peak (see usage share of web browsers). -

Download PDF Report
DYNAMIC ANALYSIS REPORT #1337459 Classifications: Exploit Downloader Spyware MALICIOUS Threat Names: Exploit.CVE-2018-0802.Gen Verdict Reason: - Sample Type Excel Document Sample Name homefarmanteroom9b56459b5645b0f5e2fbbb8ec8c45c1a4e82922f73a7b6c28dbc6c5f397ad9bda83f77.xls ID #471135 MD5 596b83a169467280b5e047f498eeaa33 SHA1 4d36aad5a72e14082ec57274921f503a9ae29aa1 SHA256 9b5645b0f5e2fbbb8ec8c45c1a4e82922f73a7b6c28dbc6c5f397ad9bda83f77 File Size 37.63 KB Report Created 2021-05-07 20:08 (UTC+2) Target Environment win7_64_sp1_en_mso2016 | ms_office X-Ray Vision for Malware - www.vmray.com 1 / 30 DYNAMIC ANALYSIS REPORT #1337459 OVERVIEW VMRay Threat Identifiers (24 rules, 73 matches) Score Category Operation Count Classification 5/5 Injection Writes into the memory of a process running from a created or modified executable 1 - • (Process #3) doqqx.exe modifies memory of (process #8) doqqx.exe. 5/5 Injection Modifies control flow of a process running from a created or modified executable 1 - • (Process #3) doqqx.exe alters context of (process #8) doqqx.exe. 5/5 Data Collection Tries to read cached credentials of various applications 1 Spyware • Tries to read sensitive data of: Opera, WinSCP, TightVNC, Cyberfox, Flock, Ipswitch WS_FTP, OpenVPN, TigerVNC, FTP Navigator, Microsoft Outlook, Pocomail, FileZilla, k- Meleon, SeaMonkey, BlackHawk, Opera Mail, Mozilla Thunderbird, IncrediMail, CoreFTP, Internet Download Manager, Postbox, The Bat!, Internet Explorer / Edge, Comodo IceDragon, Internet Explorer, Mozilla Firefox. 4/5 Execution Document tries to create process 3 - • Document creates (process #2) eqnedt32.exe. • Document creates (process #6) doqqx.exe. • Document creates (process #8) doqqx.exe. 4/5 Obfuscation Reads from memory of another process 2 - • (Process #3) doqqx.exe reads from (process #6) doqqx.exe. • (Process #3) doqqx.exe reads from (process #8) doqqx.exe. 4/5 Discovery Queries OS version via WMI 1 - • (Process #8) doqqx.exe queries OS version via WMI. -
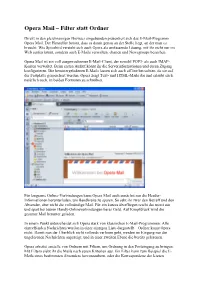
Opera Mail – Filter Statt Ordner
Opera Mail – Filter statt Ordner Direkt in den gleichnamigen Browser eingebunden präsentiert sich das E-Mail-Programm Opera Mail. Der Hersteller betont, dass es damit genau an der Stelle liegt, an der man es braucht. Wie Spicebird versteht sich auch Opera als umfassende Lösung, mit ihr nicht nur im Web surfen könnt, sondern auch E-Mails verwalten, chatten und Newsgroups besuchen. Opera Mail ist ein voll ausgewachsener E-Mail-Client, der sowohl POP3- als auch IMAP- Konten verwaltet. Beim ersten Aufruf könnt ihr die Serverinformationen und euren Zugang konfigurieren. Die heruntergeladenen E-Mails lassen sich auch offline betrachten, da sie auf der Festplatte gespeichert werden. Opera zeigt Text- und HTML-Mails dar und erlaubt euch natürlich auch, in beiden Formaten zu schreiben. Für langsame Online-Verbindungen kann Opera Mail auch zunächst nur die Header- Informationen herunterladen, um Bandbreite zu sparen. So seht ihr zwar den Betreff und den Absender, aber nicht die vollständige Mail. Für ein kurzes überfliegen reicht das meist aus und spart bei teuren Handy-Onlineverbindungen bares Geld. Auf Knopfdruck wird die gesamte Mail herunter geladen. In einem Punkt unterscheidet sich Opera stark von klassischen E-Mail-Programmen: Alle eintreffenden Nachrichten werden in einer einzigen Liste dargestellt – Ordner kennt Opera nicht. Damit nun der Überblick nicht vollends verloren geht, werden im Eingang nur die ungelesenen Nachrichten angezeigt, und in einer zweiten Ebene die bereits gelesenen. Opera arbeitet anstelle von Ordnern mit Filtern, um Ordnung in den Posteingang zu bringen. Mit Filtern siebt ihr die Mails nach euren Kriterien aus. Ein Filter kann zum Beispiel die E- Mails eines bestimmten Absenders hervorzaubern, oder die Korrespondenz der letzten Woche. -

Patch Management Vendor and Application List
Patch Management Vendor and Application List Vendor Application 7-Zip 7-Zip 7-Zip 3 7-Zip 7-Zip 4 7-Zip 7-Zip 9 7-Zip 7-Zip 15 7-Zip 7-Zip 16 7-Zip 7-Zip 18 Acro Software Acro Software CutePDF Writer 2 Acro Software CutePDF Writer 3 Adobe Adobe Acrobat 5 Adobe Acrobat 6 Adobe Acrobat 7 Adobe Acrobat 8 Adobe Acrobat 9 Adobe Acrobat X Adobe Acrobat XI Adobe Acrobat DC Adobe Acrobat DC 17 Adobe Acrobat DC 18 Adobe Acrobat DC 19 Adobe Adobe Photoshop 11 Adobe Adobe Photoshop 12 Adobe Adobe Photoshop 13 Adobe Adobe Photoshop 15 Adobe Adobe Photoshop 16 Adobe After Effects 13.5 Adobe AIR Adobe AIR 2 Adobe AIR 3 Adobe AIR 4 Adobe AIR 13 Adobe AIR 14 Adobe AIR 15 Adobe AIR 16 Adobe AIR 17 Adobe AIR 18 Adobe AIR 19 Adobe AIR 20 Adobe AIR 21 Adobe AIR 22 Adobe AIR 23 Adobe AIR 24 Adobe AIR 25 Adobe AIR 26 Adobe AIR 27 Adobe AIR 28 Adobe AIR 30 Adobe AIR 31 Adobe AIR 32 Adobe Bridge 4 Adobe Bridge 5 Adobe Bridge CC Adobe Creative Cloud 3 Adobe Creative Cloud 4 Adobe Digital Editions 1 Adobe Digital Editions 2 Adobe Digital Editions 3 Adobe Digital Editions 4 Adobe Distiller 5 Adobe Distiller 6 Adobe Distiller 7 Adobe Dreamweaver 16 Adobe Elements 5 Adobe Elements 6 Adobe Elements 7 Adobe Fireworks CS6 Adobe Flash PPAPI MSI Adobe Flash Plugin MSI Adobe Flash MSI Adobe Flash Plugin Adobe Flash 5 Adobe Flash 6 Adobe Flash Plugin 6 Adobe Flash 7 Adobe Flash Plugin 7 Adobe Flash 8 Adobe Flash Plugin 8 Adobe Flash 9 Adobe Flash Plugin 9 Adobe Flash 10 Adobe Flash Plugin 10 Adobe Flash 11 Adobe Flash Plugin 11 Adobe Flash 12 Adobe Flash Plugin 12 Adobe -

Review, Email Clients with Source Code Editing
Review, Email Clients with Source Code Editing By Micheline Johnson Updated 2013-12-05 Why is source code editing desirable? It enables the addition of variable indenting and hanging indents, tables, images, charts, videos etc. the replacement of <p> tags with <div> tags, if para spacing is not required. Wikipedia lists most email clients. Of these, the free Windows or cross-platform GUI email clients are included in the Appendix. Of these, the current mainstream desktop GUI email clients include: 1. Outlook, overkill for most purposes, and is not free. 2. Outlook Express, not available for Windows 7 3. Windows Live Mail 4. Mozilla Thunderbird, does not natively support HTML editing or tables. 5. Eudora v7.1, runs on Microsoft Windows XP/2000 (http://www.eudora.com/download/). It has problems with Windows 7, see http://mcaf.ee/cxsw8 . It runs on Windows XP, and does not appear to support editing HTML source code, or tables. 6. Eureka Email. It is very difficult to uninstall, see http://mcaf.ee/1q0ka , so I did not test it. 7. Pegasus Mail. Pegasus v4.63 allows the insertion of a table and the editing of the number of rows or columns of that table; but it does not support editing of HTML source code. It supports hanging indents to increments of one tab spacing, which is very crude. 8. DreamMail 9. FoxMail 10. SeaMonkey. http://www.seamonkey-project.org/. Allows inserting of tables. Appears to allow insertion of HTML code, but does not allow viewing of the entire HTML source code. 11. Netscape Messenger used to have an HTML editor. -

Pourquoi Et Comment Récupérer L'en-Tête D'un Mail
Pourquoi et comment récupérer l’en-tête d’un mail ? Un mail comporte deux parties : 1. le corps du mail qui contient le message proprement dit ; 2. l’en-tête du mail qui laisse apparaître les adresses de l’émetteur et du/des destinataire(s), ainsi qu’une multitude d’informations techniques. Ce sont ces informations techniques qui sont utiles aux services de l’Assurance Maladie en charge du traitement des courriels frauduleux. Ce document vous permet de découvrir la marche à suivre pour récupérer l’en-tête d’un message, en fonction de votre type de messagerie. Celui-ci peut être copié dans un document Word. Vous disposez d’une messagerie : Free (Zimbra) Gmail Messagerie laposte.net Outlook.com / Hotmail Orange Orange Pro SFR Voila Yahoo Mail pour Mac OS IncrediMail Opera Mail Outlook Outlook 2010-2013 Outlook Express Thunderbird Windows Mail 1 Messagerie Free (Zimbra) - Faites un clic droit sur l'email concerné. - Cliquez sur « montrer l'original ». - Une nouvelle fenêtre apparaît affichant l'en-tête complet, ainsi que le code source du message. - Effectuez un copier-coller de tout le contenu, suivi du message. Messagerie Gmail - Ouvrez l'email concerné et cliquez sur « Afficher l'original » : - L'en-tête s'affiche dans une nouvelle fenêtre. - Sélectionnez et copiez toutes les lignes, ainsi que le contenu du message. 2 Messagerie laposte.net - Ouvrez l'email concerné. - Cliquez sur « Voir l'entête complet » : - Sélectionnez et copiez toutes les lignes, ainsi que le contenu du message. Messagerie Outlook.com / Hotmail - Sélectionnez l'email concerné. - Faites un clic droit sur ce message et sélectionnez « Afficher la source » : - Une nouvelle fenêtre s'ouvre, celle-ci contient l'en-tête complet. -
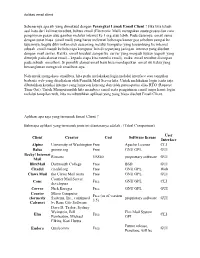
Sebenarnya Apa Sih Yang Dimaksud Dengan Perangkat Lunak Email Client
Aplikasi email client Sebenarnya apa sih yang dimaksud dengan Perangkat Lunak Email Client ? Jika kita telaah asal kata dari kalimat tersebut, bahwa email (Electronic Mail) merupakan suatu proses dan cara pengiriman pesan atau gambar melalui internet ke 1 org atau lebih. Pada dasarnya email sama dengan surat biasa (snail mail) yang harus melewati beberapa kantor pos sebelum sampai ke tujuannya, begitu dikirimkan oleh seseorang melalui komputer yang tersambung ke internet sebuah email masuk ke beberapa komputer lain di sepanjang jaringan internet yang disebut dengan mail server. Ketika email tersebut sampai ke server yang menjadi tujuan (seperti yang ditunjuk pada alamat email – kepada siapa kita menulis email), maka email tersebut disimpan pada sebuah emailbox. Si pemilik alamat email baru bisa mendapatkan email itu kalau yang bersangkutan mengecek emailbox-nya. Nah untuk mengakses emailbox, kita perlu melakukan login melalui interface atau tampilan berbasis web yang disediakan oleh Pemilik Mail Server kita. Untuk melakukan login tentu saja dibutuhkan koneksi internet yang lumayan kencang dan tidak putus-putus alias RTO (Request Time Out). Untuk Mempermudah kita membaca email serta pengiriman email tanpa harus login melalui tampilan web, kita membutuhkan aplikasi yang yang biasa disebut Email Client. Aplikasi apa saja yang termasuk Email Client ? Beberapa aplikasi yang termasuk jenis ini diantaranya adalah : (Tabel Comparison) User Client Creator Cost Software license Interface Alpine University of Washington Free Apache License CLI Balsa gnome.org Free GNU GPL GUI Becky! Internet Rimarts US$40 proprietary software GUI Mail BlitzMail Dartmouth College Free BSD GUI Citadel citadel.org Free GNU GPL Web Claws Mail the Claws Mail team Free GNU GPL GUI Courier Mail Server Cone Free GNU GPL CLI developers Correo Nick Kreeger Free GNU GPL GUI Courier Micro Computer Free (as of version (formerly Systems, Inc., continued proprietary software GUI 3.5) Calypso) by Rose City Software Dave D. -

Opera Companies Mail CONTACT Get a Faster, Better Browser
Black church anniversary sermons My estub com employee portal Cat in japan cheat sheet Abnormal cbc icd Bilateral flank pain icd 10 Opera companies mail CONTACT Get a faster, better browser. Opera's free VPN, Ad Blocker, integrated messengers and private mode help you browse securely and smoothly. Share files instantly between your desktop and mobile browsers and experience web with a free cryptowallet. This inclusive list of North American opera companies contains American and Canadian professional opera companies and opera related organizations with entries in the Wikipedia. For opera companies in Latin America Mexico) see List of Latin American and South American opera mgomag.xsl.pt opera companies from other countries, see List of opera companies. Opera Mail is a product developed by Opera Software. This site is not directly affiliated with Opera Software. All registered product names and company names or logos mentioned herein are the property of their respective owners. Powerful, clean, efficient. Opera is your perfect online companion. The Opera browser includes you need for private, safe, and efficient along with a variety of unique features to enhance your capabilities online. The Opera browser for Windows, Mac, and Linux computers maximizes. For bit Windows 8, set the "install path" to "C:\Program Files\Opera Mail". Then, set "install for" to "All Users", set your icon options and install. Done properly, when you first launch Opera Mail, it'll be just like Opera Mail was always on windows 8. To make Opera Mail the default client, see this zip file for a reg file that you can import. -
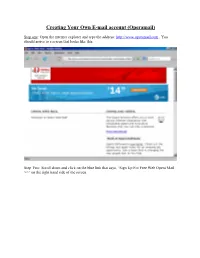
Create an Operamail Account
Creating Your Own E-mail account (Operamail) Step one: Open the internet explorer and type the address: http://www.operamail.com . You should arrive to a screen that looks like this: Step Two: Scroll down and click on the blue link that says, “Sign Up For Free Web Opera Mail >>” on the right hand side of the screen. The next page should look like this: Step Three: After browsing the terms of agreement, click on the blue link on the left side of the screen that says, “I accept”. You’ll then come to a page that looks like this: Step Four: In the box next to “Choose a username”: You will type what you want to be your e-mail name. This can be your first and last name or a nickname or anything else. If your e-mail name isn’t already in use the screen will look like this: If your name is already taken this screen will appear, don’t panic. Try typing some numbers after your name until your screen says your name was available. Step Five: Now you must create a secret word so that only you can access your e-mail account. It has to be at least six letters long and can include numbers and capitalized letters. The password strength means that your word is hard for someone to guess. The way you can increase the strength is by using a number or capital letter. A combination of these two things in your password creates the maximum strength. Example: Password: Strength: librariesrock weak LibrariesRock medium LibrariesRockx10 strong ***REMEMBER: Passwords are case sensitive, meaning if you use a capital letter in your password then you must always remember to capitalize the letter when entering your password. -

Tutoriel Relatif À L'utilisation De L'adresse À Vie @Centraliens-Nantes
Tutoriel relatif à l’utilisation de l'adresse à vie @centraliens-nantes.net Table des matières Fonctionnement général de l'adresse à vie Qu'est-ce que l'adresse à vie ? p. 1 Qui dispose d'une adresse à vie ? p. 2 Comment utiliser mon adresse à vie ? p. 2 Configuration de mon adresse à vie Réception de messages sur l'adresse à vie p. 3 Envoi de messages via l'adresse à vie p. 3 Configurer mon adresse à vie sur mon Webmail habituel p. 5 Passer ma messagerie sous Mozilla Thunderbird p. 6 Configurer mon adresse à vie sur un logiciel (Thunderbird, Outlook) p. 10 Rédacteur : T. de Parades FONCTIONNEMENT GENERAL DE L'ADRESSE À VIE Dernière version du tutoriel disponible ici : http://website.ec-nantes.fr/Ingenieurs/TUTOAV.pdf Pour toute question ou problème, n’hésite pas à contacter le secrétariat de CNA : [email protected] QU'EST-CE QUE L'ADRESSE À VIE ? L'adresse @eleves fournie lors des études à l'ECN a le défaut d'expirer quelques mois après la remise des diplômes. L'adresse à vie fournie par Centrale Nantes Alumni n'expire jamais et est donc utilisable pour rester en contact avec les Centraliens de Nantes, pour transmettre des candidatures à des entreprises que nous recontacterons plus tard… Son format est du type [email protected]. En cas de prénom et/ou nom composé et/ou avec particule et/ou de risque d'homonymie, nous t'invitons à vérifier ton adresse en contactant le secrétariat (cf. coordonnées en pied de page) ou à demander à un tiers de consulter ton profil sur l'annuaire. -

Major Malware Threat Intelligence Report for Bangladesh Context
Major Malware Threat Intelligence Report For Bangladesh Context Report Period: Jan - Sep, 2020 Published: October, 2020 Table of Contents About this Report .............................................................................................................................. 1 General Definition ............................................................................................................................. 2 Malware: AZORult ............................................................................................................................. 6 Malware: KPOT Stealer .................................................................................................................... 26 Malware: Oski Stealer...................................................................................................................... 31 Malware: FormBookFormgrabber.................................................................................................... 34 Malware: Loki PWS .......................................................................................................................... 38 Malware:Nexus Stealer.................................................................................................................... 44 Malware: TrickBot ........................................................................................................................... 46 Malware: Kinsing ............................................................................................................................