Final Report
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Downloadable Email Program for My Pc 32 Best Free Email Clients
downloadable email program for my pc 32 Best Free Email Clients. Here are 32 best free email client software . These let you manage and access all of your email accounts in one single place easily. All these email client software are completely free and can be downloaded to Windows PC. These free software offer various features, like: can be used with IMAP, SMTP, POP3 and Gmail, keeps your emails safe and secure, lets you open various emails simultaneously, provide protection from spam, lets you view your emails offline, manage and access all of your email accounts in one single place, supports PH, LDAP, IMAP4, POP3 and SMPT mail protocols etc. So, go through this list of free email client software and see which ones you like the most. Thunderbird. Thunderbird is a free and handy email client software for your computer. It can be used with IMAP, SMTP, POP3 and Gmail. It will also work with email accounts provided by MS Exchange Server. The user interface of Thunderbird is tabbed. It lets you open various emails simultaneously. Thunderbird keeps your emails safe and secure. It also has special filters for filtering the mail. Windows Live Mail. Windows Live Mail is a free email client for your computer. It works with various email accounts. It lets you access Yahoo, Gmail, Hotmail and emails from different servers which supports POP3 and SMTP. Its security features are excellent it will also provide protection from spam. You can also view your emails offline in this freeware. Zimbra Desktop. Zimbra Desktop is a free email client. -

Web Browser a C-Class Article from Wikipedia, the Free Encyclopedia
Web browser A C-class article from Wikipedia, the free encyclopedia A web browser or Internet browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web. An information resource is identified by a Uniform Resource Identifier (URI) and may be a web page, image, video, or other piece of content.[1] Hyperlinks present in resources enable users to easily navigate their browsers to related resources. Although browsers are primarily intended to access the World Wide Web, they can also be used to access information provided by Web servers in private networks or files in file systems. Some browsers can also be used to save information resources to file systems. Contents 1 History 2 Function 3 Features 3.1 User interface 3.2 Privacy and security 3.3 Standards support 4 See also 5 References 6 External links History Main article: History of the web browser The history of the Web browser dates back in to the late 1980s, when a variety of technologies laid the foundation for the first Web browser, WorldWideWeb, by Tim Berners-Lee in 1991. That browser brought together a variety of existing and new software and hardware technologies. Ted Nelson and Douglas Engelbart developed the concept of hypertext long before Berners-Lee and CERN. It became the core of the World Wide Web. Berners-Lee does acknowledge Engelbart's contribution. The introduction of the NCSA Mosaic Web browser in 1993 – one of the first graphical Web browsers – led to an explosion in Web use. Marc Andreessen, the leader of the Mosaic team at NCSA, soon started his own company, named Netscape, and released the Mosaic-influenced Netscape Navigator in 1994, which quickly became the world's most popular browser, accounting for 90% of all Web use at its peak (see usage share of web browsers). -

How to Add an Apple Email Address to Microsoft Outlook
How to add an Apple Email Address to Microsoft Outlook For those of us who use ‘Two Factor Authentication’ with Apple, where you must enter a 6-digit code to access anything Apple, THIS IS THE THING that leads to the problem of connecting your iCloud email address to Outlook!!! How to fix this? 1. Open Outlook and a web browser 2. In the web browser, go to your Apple login page using: https://appleid.apple.com 3. Log in with your usual Apple username and password that you use for your iTunes account 4. If Apple ID Two-Factor Verification required, get 6-number code from iPhone and input the value 5. Once in, scroll down to the Security area, and then look for ‘App Specific Passwords' 6. Click on the link “Generate Password” and then create a name for this specific password (like 'outlook iCloud') and press “Create”. 7. A 16-digit password will be generated for you. Copy that password into memory or write it down. It will look something like this: abcd-efgh-ijkl-mnop 8. In Outlook you will receive an email from Apple titled: “An app-specific password was generated for your Apple ID” This is good. 9. Now go to the Outlook Account Settings window (File/Account Settings/Account Settings) which takes you to “Email Accounts” 10. On the Email tab, choose “New” 11. Enter your Apple email address (either [email protected] or [email protected]) 12. On the same window, press “Advanced options and “Let me set up my account manually” 13. -
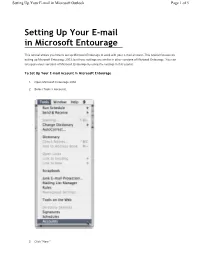
Setting up Your E-Mail in Microsoft Entourage
Setting Up Your E-mail in Microsoft Outlook Page 1 of 5 Setting Up Your E-mail in Microsoft Entourage This tutorial shows you how to set up Microsoft Entourage to work with your e-mail account. This tutorial focuses on setting up Microsoft Entourage 2003, but these settings are similar in other versions of Microsoft Entourage. You can set up previous versions of Microsoft Entourage by using the settings in this tutorial. To Set Up Your E-mail Account in Microsoft Entourage 1. Open Microsoft Entourage 2004. 2. Select Tools > Accounts. 3. Click "New." Setting Up Your E-mail in Microsoft Outlook Page 2 of 5 4. If the "Account Setup Assistant" window displays, click "Configure account manually." Setting Up Your E-mail in Microsoft Outlook Page 3 of 5 5. Select POP for the account type and click OK. 6. On the Edit Account window, enter your information as follows: Account name Enter a name for your account, for example: My Mail, Work, or Home. Name Enter your first and last name. E-mail address Enter your e-mail address. Account ID Enter your e-mail address, again. POP server Enter pop.secureserver.net as your incoming server Password Enter the password for your e-mail account. SMTP server Enter smtpout.secureserver.net for your outgoing mail server. Click "Click here for more advanced sending options." NOTE: "smtpout.secureserver.net" is an SMTP relay server. In order to use this server to send e-mails, you must first activate SMTP relay on your e-mail account. Log on to your Manage Email Accounts page to set up SMTP relay. -

Souhrada Awaits Trial, Maintains Innocence
The Volume V, Issue 21 March 19, 1996 Steal this issue. Profile: SOUHRADA AWAITS TRIAL, Gordon Bauer MAINTAINS INNOCENCE by Aaron Olk by Michelle Wolper Souhrada was released from the Gordon Bauer, psychology professor Ernest Souhrada is awaiting arraign Sarasota County Jail on March 8, the and Social Science Chair, was in Hawaii ment. The New College community is same day of his arrest. J. Alder, correc doing research on humpback whales and waiting for a complete story. While most tions officer at the jail, said that Afford working for the Veterans details cannot be disclosed at this time able Bail Bonds posted his bail amount of ~ u: Administration until he due to legal complications, Souhrada is $3508. Souhrada now awaits his arraign 0 came to New College five defending his innocence, while his ac ment, scheduled for April 19. a: a.. years ago. cuser has come forward. Alford has also made a statement re Bauer was working with Stephenie Alford and another uniden garding Harry's theft and her confession veterans plagued by post-traumatic stress tified source told University Police on to the police. disorder (JYTSD), an illness similar to March 7 that Souhrada, Alford's es "The students need to have the shell shock and battle fatigue, in an at tranged husband, stole Harry, the computer which was taken from them tempt to better understand the disease. computer that served as a student server Bauer said that the opinion most people in Hanson Lab. She also told police under SEE "SOUHRADA" ON PAGE 2 had at the time was that "there must be oath that Souhrada had changed the exte something wrong with the JYTSD victim rior container of Harry at the residence to begin with." that they shared at the time. -

Mailstore Server Vs. Office 365 Archiving
MailStore Server vs. Office 365 Archiving The goal of this document is to detail the advantages of using MailStore Server instead of Office 365 archiving for email archiving based on provable facts as opposed to mere assumptions or hearsay. To achieve this goal, only statements about Office 365 archiving that are based on publicly available material published by Microsoft are taken into account. These statements are compared to the capabilities of MailStore Server, based on equally publicly available material published by MailStore Software GmbH. To further enhance the quality of this analysis, all statements (with the exception of those related to pricing) have been extracted from technical specifications and implementation guides to ensure that they are based on current best practice and state of affairs. This document supersedes all previous versions and has been updated to the latest information available in April 2014. Overview No Feature MailStore Server Office 365 Archive 1. Supported versions of All editions of Outlook 2003, Specific editions of Outlook Outlook with access to the 2007, 2010, 2013 1 2007, 2010, 2013 2 archive 2. Supported Office 365 plans All plans that include email 3 Archiving options dependent on plan, with various limits. Additional features can be added to certain plans only 4,5,6 3. Search capabilities Full text search of all Search capabilities readable folders including dependent on the Outlook attachment contents 7 version and edition 8 4. Completeness of the archive Ensured through journaling ° Journaling not available support 9 in all plans 10 ° Office 365 needs external mailbox for journaling 10 The Experts in Email Archiving www.mailstore.com 2 | 7 No Feature MailStore Server Office 365 Archive 5. -

Download PDF Report
DYNAMIC ANALYSIS REPORT #1337459 Classifications: Exploit Downloader Spyware MALICIOUS Threat Names: Exploit.CVE-2018-0802.Gen Verdict Reason: - Sample Type Excel Document Sample Name homefarmanteroom9b56459b5645b0f5e2fbbb8ec8c45c1a4e82922f73a7b6c28dbc6c5f397ad9bda83f77.xls ID #471135 MD5 596b83a169467280b5e047f498eeaa33 SHA1 4d36aad5a72e14082ec57274921f503a9ae29aa1 SHA256 9b5645b0f5e2fbbb8ec8c45c1a4e82922f73a7b6c28dbc6c5f397ad9bda83f77 File Size 37.63 KB Report Created 2021-05-07 20:08 (UTC+2) Target Environment win7_64_sp1_en_mso2016 | ms_office X-Ray Vision for Malware - www.vmray.com 1 / 30 DYNAMIC ANALYSIS REPORT #1337459 OVERVIEW VMRay Threat Identifiers (24 rules, 73 matches) Score Category Operation Count Classification 5/5 Injection Writes into the memory of a process running from a created or modified executable 1 - • (Process #3) doqqx.exe modifies memory of (process #8) doqqx.exe. 5/5 Injection Modifies control flow of a process running from a created or modified executable 1 - • (Process #3) doqqx.exe alters context of (process #8) doqqx.exe. 5/5 Data Collection Tries to read cached credentials of various applications 1 Spyware • Tries to read sensitive data of: Opera, WinSCP, TightVNC, Cyberfox, Flock, Ipswitch WS_FTP, OpenVPN, TigerVNC, FTP Navigator, Microsoft Outlook, Pocomail, FileZilla, k- Meleon, SeaMonkey, BlackHawk, Opera Mail, Mozilla Thunderbird, IncrediMail, CoreFTP, Internet Download Manager, Postbox, The Bat!, Internet Explorer / Edge, Comodo IceDragon, Internet Explorer, Mozilla Firefox. 4/5 Execution Document tries to create process 3 - • Document creates (process #2) eqnedt32.exe. • Document creates (process #6) doqqx.exe. • Document creates (process #8) doqqx.exe. 4/5 Obfuscation Reads from memory of another process 2 - • (Process #3) doqqx.exe reads from (process #6) doqqx.exe. • (Process #3) doqqx.exe reads from (process #8) doqqx.exe. 4/5 Discovery Queries OS version via WMI 1 - • (Process #8) doqqx.exe queries OS version via WMI. -

Activid® Activclient®
ActivID® ActivClient® Advanced security client protects workstations and networks with smart cards and smart USB keys HID Global’s ActivID® ActivClient® ensures strong authentication of employees, contractors and suppliers when they access enterprise resources, helping IT managers, security professionals and auditors to manage the risk of unauthorized access to workstations and networks by enabling the deployment of Zero Trust security framework. AT-A-GLANCE ACTIVCLIENT BENEFITS: • Increases security with proven As a market-leading middleware for Microsoft® Outlook®, Adobe technology that is widely adopted smart cards and smart USB keys, Acrobat® and popular web because of its user-friendly, familiar, ATM-like authentication experience ActivID ActivClient consolidates browsers), smart cards, smart card identity credentials (private keys readers and smart USB keys • Optimizes productivity with a single, versatile strong authentication for public key infrastructure [PKI] • Compatibility with major certificate tool for both Windows Login and certificates and symmetric keys for authorities and encryption utilities Remote Access (e.g., PIN-protected one-time password [OTP] generation) PKI certificates or OTPs for VPN) • Simple automated deployment, on a single, secure, portable updates and diagnostics • Improves compliance with device. This capability, combined government and industry with support for a wide range of • An open, standards-based regulations desktop and network applications, architecture, which is easily • Reduces costs with easy -

Visualization of Client-Side Web Browsing and Email Activity
Calhoun: The NPS Institutional Archive Theses and Dissertations Thesis Collection 2009-06 Visualization of client-side web browsing and email activity Roussas, Gregory. Monterey, California. Naval Postgraduate School http://hdl.handle.net/10945/4738 NAVAL POSTGRADUATE SCHOOL MONTEREY, CALIFORNIA THESIS VISUALIZATION OF CLIENT-SIDE WEB BROWSING AND EMAIL ACTIVITY by Gregory Roussas June 2009 Thesis Advisor: Cynthia E. Irvine Second Reader: Chris S. Eagle Approved for public release; distribution is unlimited THIS PAGE INTENTIONALLY LEFT BLANK ii Form Approved REPORT DOCUMENTATION PAGE OMB No. 0704–0188 The public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instructions, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing this burden to Department of Defense, Washington Headquarters Services, Directorate for Information Operations and Reports (0704–0188), 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202–4302. Respondents should be aware that notwithstanding any other provision of law, no person shall be subject to any penalty for failing to comply with a collection of information if it does not display a currently valid OMB control number. PLEASE DO NOT RETURN YOUR FORM TO THE ABOVE ADDRESS. 1. REPORT DATE (DD–MM–YYYY) 2. REPORT TYPE 3. DATES COVERED (From — To) 22–6–2009 Master’s Thesis 2007-09-21—2009-06-19 4. TITLE AND SUBTITLE 5a. CONTRACT NUMBER 5b. GRANT NUMBER Visualization of Client-Side Web Browsing and Email Activity DUE 0414102 5c. -
Opera Mail – Filter Statt Ordner
Opera Mail – Filter statt Ordner Direkt in den gleichnamigen Browser eingebunden präsentiert sich das E-Mail-Programm Opera Mail. Der Hersteller betont, dass es damit genau an der Stelle liegt, an der man es braucht. Wie Spicebird versteht sich auch Opera als umfassende Lösung, mit ihr nicht nur im Web surfen könnt, sondern auch E-Mails verwalten, chatten und Newsgroups besuchen. Opera Mail ist ein voll ausgewachsener E-Mail-Client, der sowohl POP3- als auch IMAP- Konten verwaltet. Beim ersten Aufruf könnt ihr die Serverinformationen und euren Zugang konfigurieren. Die heruntergeladenen E-Mails lassen sich auch offline betrachten, da sie auf der Festplatte gespeichert werden. Opera zeigt Text- und HTML-Mails dar und erlaubt euch natürlich auch, in beiden Formaten zu schreiben. Für langsame Online-Verbindungen kann Opera Mail auch zunächst nur die Header- Informationen herunterladen, um Bandbreite zu sparen. So seht ihr zwar den Betreff und den Absender, aber nicht die vollständige Mail. Für ein kurzes überfliegen reicht das meist aus und spart bei teuren Handy-Onlineverbindungen bares Geld. Auf Knopfdruck wird die gesamte Mail herunter geladen. In einem Punkt unterscheidet sich Opera stark von klassischen E-Mail-Programmen: Alle eintreffenden Nachrichten werden in einer einzigen Liste dargestellt – Ordner kennt Opera nicht. Damit nun der Überblick nicht vollends verloren geht, werden im Eingang nur die ungelesenen Nachrichten angezeigt, und in einer zweiten Ebene die bereits gelesenen. Opera arbeitet anstelle von Ordnern mit Filtern, um Ordnung in den Posteingang zu bringen. Mit Filtern siebt ihr die Mails nach euren Kriterien aus. Ein Filter kann zum Beispiel die E- Mails eines bestimmten Absenders hervorzaubern, oder die Korrespondenz der letzten Woche. -

The Complete Solutions Guide for Every Linux/Windows System Administrator!
Integrating Linux and Windows Integrating Linux and Windows By Mike McCune Publisher : Prentice Hall PTR Pub Date : December 19, 2000 ISBN : 0-13-030670-3 • Pages : 416 The complete solutions guide for every Linux/Windows system administrator! This complete Linux/Windows integration guide offers detailed coverage of dual- boot issues, data compatibility, and networking. It also handles topics such as implementing Samba file/print services for Windows workstations and providing cross-platform database access. Running Linux and Windows in the same environment? Here's the comprehensive, up-to-the-minute solutions guide you've been searching for! In Integrating Linux and Windows, top consultant Mike McCune brings together hundreds of solutions for the problems that Linux/Windows system administrators encounter most often. McCune focuses on the critical interoperability issues real businesses face: networking, program/data compatibility, dual-boot systems, and more. You'll discover exactly how to: Use Samba and Linux to deliver high-performance, low-cost file and print services to Windows workstations Compare and implement the best Linux/Windows connectivity techniques: NFS, FTP, remote commands, secure shell, telnet, and more Provide reliable data exchange between Microsoft Office and StarOffice for Linux Provide high-performance cross-platform database access via ODBC Make the most of platform-independent, browser-based applications Manage Linux and Windows on the same workstation: boot managers, partitioning, compressed drives, file systems, and more. For anyone running both Linux and Windows, McCune delivers honest and objective explanations of all your integration options, plus realistic, proven solutions you won't find anywhere else. Integrating Linux and Windows will help you keep your users happy, your costs under control, and your sanity intact! 1 Integrating Linux and Windows 2 Integrating Linux and Windows Library of Congress Cataloging-in-Publication Data McCune, Mike. -

Introducción a Linux Equivalencias Windows En Linux Ivalencias
No has iniciado sesión Discusión Contribuciones Crear una cuenta Acceder Página discusión Leer Editar Ver historial Buscar Introducción a Linux Equivalencias Windows en Linux Portada < Introducción a Linux Categorías de libros Equivalencias Windows en GNU/Linux es una lista de equivalencias, reemplazos y software Cam bios recientes Libro aleatorio análogo a Windows en GNU/Linux y viceversa. Ayuda Contenido [ocultar] Donaciones 1 Algunas diferencias entre los programas para Windows y GNU/Linux Comunidad 2 Redes y Conectividad Café 3 Trabajando con archivos Portal de la comunidad 4 Software de escritorio Subproyectos 5 Multimedia Recetario 5.1 Audio y reproductores de CD Wikichicos 5.2 Gráficos 5.3 Video y otros Imprimir/exportar 6 Ofimática/negocios Crear un libro 7 Juegos Descargar como PDF Versión para im primir 8 Programación y Desarrollo 9 Software para Servidores Herramientas 10 Científicos y Prog s Especiales 11 Otros Cambios relacionados 12 Enlaces externos Subir archivo 12.1 Notas Páginas especiales Enlace permanente Información de la Algunas diferencias entre los programas para Windows y y página Enlace corto GNU/Linux [ editar ] Citar esta página La mayoría de los programas de Windows son hechos con el principio de "Todo en uno" (cada Idiomas desarrollador agrega todo a su producto). De la misma forma, a este principio le llaman el Añadir enlaces "Estilo-Windows". Redes y Conectividad [ editar ] Descripción del programa, Windows GNU/Linux tareas ejecutadas Firefox (Iceweasel) Opera [NL] Internet Explorer Konqueror Netscape /