The Complete Solutions Guide for Every Linux/Windows System Administrator!
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SMTP (Simple Mail Transfer Protocol)
P1: JsY JWBS001A-60.tex WL041/Bidgoli WL041-Bidgoli.cls May 12, 2005 3:27 Char Count= 0 SMTP (Simple Mail Transfer Protocol) Vladimir V. Riabov, Rivier College Introduction 1 SMTP Security Issues 12 SMTP Fundamentals 1 SMTP Vulnerabilities 12 SMTP Model and Protocol 2 SMTP Server Buffer Overflow Vulnerability 15 User Agent 4 Mail Relaying SMTP Vulnerability 15 Sending e-Mail 4 Mail Relaying SMTP Vulnerability in Microsoft Mail Header Format 4 Windows 2000 15 Receiving e-Mail 4 Encapsulated SMTP Address Vulnerability 15 The SMTP Destination Address 4 Malformed Request Denial of Service 16 Delayed Delivery 4 Extended Verb Request Handling Flaw 16 Aliases 5 Reverse DNS Response Buffer Overflow 16 Mail Transfer Agent 5 Firewall SMTP Filtering Vulnerability 16 SMTP Mail Transaction Flow 5 Spoofing 16 SMTP Commands 6 Bounce Attack 16 Mail Service Types 6 Restricting Access to an Outgoing Mail SMTP Service Extensions 8 Server 17 SMTP Responses 8 Mail Encryption 17 SMTP Server 8 Bastille Hardening System 17 On-Demand Mail Relay 8 POP and IMAP Vulnerabilities 17 Multipurpose Internet Mail Extensions Standards, Organizations, and (MIME) 8 Associations 18 MIME-Version 10 Internet Assigned Numbers Authority 18 Content-Type 10 Internet Engineering Task Force Working Content-Transfer-Encoding 10 Groups 18 Content-Id 11 Internet Mail Consortium 18 Content-Description 11 Mitre Corporation 18 Security Scheme for MIME 11 Conclusion 18 Mail Transmission Types 11 Glossary 18 Mail Access Modes 11 Cross References 19 Mail Access Protocols 11 References 19 POP3 11 Further Reading 22 IMAP4 12 INTRODUCTION and IMAP4), SMTP software, vulnerability and security issues, standards, associations, and organizations. -

Understanding Post Office Protocol (POP3)
Understanding Post Office Protocol (POP3) Author: Conrad Chung, 2BrightSparks Introduction Most Internet users with email accounts would have used some form of “client” software (Outlook, Thunderbird etc.) to access and manage their email at one point or another. To retrieve emails, these email clients may require the configuration of Post Office Protocol (or POP3) before messages can be downloaded from the server. This article will help readers understand what POP3 is and how it works. What is Post Office Protocol? The Post Office Protocol (POP3) is an Internet standard protocol used by local email software clients to retrieve emails from a remote mail server over a TCP/IP connection. Since the first version was created in 1984, the Post Office Protocol (currently at Version 3) has since became one of the most popular protocols and is used by virtually every email client to date. Its popularity lies in the protocol’s simplicity to configure, operate and maintain. Email servers hosted by Internet service providers also use POP3 to receive and hold emails intended for their subscribers. Periodically, these subscribers will use email client software to check their mailbox on the remote server and download any emails addressed to them. Once the email client has downloaded the emails, they are usually deleted from the server, although some email clients allow users to specify that mails be copied or saved on the server for a period of time. Email clients generally use the well-known TCP port 110 to connect to a POP3 server. If encrypted communication is supported on the POP3 server, users can optionally choose to connect either by using the STLS command after the protocol initiation stage or by using POP3S, which can use the Transport Layer Security (TLS) or Secure Sockets Layer (SSL) on TCP port 995 to connect to the server. -

Reference & Manual
DynaPDF 4.0 Reference & Manual API Reference Version 4.0.59 September 16, 2021 Legal Notices Copyright: © 2003-2021 Jens Boschulte, DynaForms GmbH. All rights reserved. DynaForms GmbH Burbecker Street 24 D-58285 Gevelsberg, Germany Trade Register HRB 9770, District Court Hagen CEO Jens Boschulte Phone: ++49 23 32-666 78 37 Fax: ++49 23 32-666 78 38 If you have questions please send an email to [email protected], or contact us by phone. This publication and the information herein is furnished as is, is subject to change without notice, and should not be construed as a commitment by DynaForms GmbH. DynaForms assumes no responsibility or liability for any errors or inaccuracies, makes no warranty of any kind (express, implied or statutory) with respect to this publication, and expressly disclaims any and all warranties of merchantability, fitness for particular purposes and no infringement of third-party rights. Adobe, Acrobat, and PostScript are trademarks of Adobe Systems Inc. AIX, IBM, and OS/390, are trademarks of International Business Machines Corporation. Microsoft, Windows, and Windows NT are trademarks of Microsoft Corporation. Apple, Mac OS, and Safari are trademarks of Apple Computer, Inc. registered in the United States and other countries. TrueType is a trademark of Apple Computer, Inc. Unicode and the Unicode logo are trademarks of Unicode, Inc. UNIX is a trademark of The Open Group. Solaris is a trademark of Sun Microsystems, Inc. Tru64 is a trademark of Hewlett-Packard. Linux is a trademark of Linus Torvalds. Other company product and service names may be trademarks or service marks of others. -

What Is the Difference Between Email Protocols
What Is The Difference Between Email Protocols Interactions between email servers and users are governed by email protocols. The most common incoming email protocols are POP, and IMAP. Most email applications/programs support one or more of these. This article is to help users understand and choose which protocol should be selected for each user’s situation. Outgoing Incoming POP (Post Office Protocol): IMAP (Internet Message Access Protocol): SSL (Secure Socket Layer): Differences Between POP and IMAP Backups / Email Loss Outgoing SMTP (Simple Mail Transfer Protocol) is the protocol used in sending (outgoing) emails. SMTP is the protocol always used for sending (outgoing) emails. Incoming POP (Post Office Protocol) and IMAP (Internet Message Access Protocol) are two different protocols that do the same thing differently. They are both used in receiving emails from a mail server and can both are available for standard and secure (?) connections. POP (Post Office Protocol): POP is an email accessing protocol used to download emails from a mail server. Applications like Outlook and Outlook Express using POP will download all emails from the server to the user’s computer, and then delete them on the server. Generally POP server uses port 110 to listen to the POP requests or securely using SSL (Secure Socket Layer) (?) POP uses port number 995. The POP protocol assumes that there is only one client/computer that will be connecting to the mailbox. Even though there is an option in most mail applications to leave the copies of the emails in the server, it is not generally used due to various reasons. -

Pdflib Reference Manual
PDFlib GmbH München, Germany Reference Manual ® A library for generating PDF on the fly Version 5.0.2 www.pdflib.com Copyright © 1997–2003 PDFlib GmbH and Thomas Merz. All rights reserved. PDFlib GmbH Tal 40, 80331 München, Germany http://www.pdflib.com phone +49 • 89 • 29 16 46 87 fax +49 • 89 • 29 16 46 86 If you have questions check the PDFlib mailing list and archive at http://groups.yahoo.com/group/pdflib Licensing contact: [email protected] Support for commercial PDFlib licensees: [email protected] (please include your license number) This publication and the information herein is furnished as is, is subject to change without notice, and should not be construed as a commitment by PDFlib GmbH. PDFlib GmbH assumes no responsibility or lia- bility for any errors or inaccuracies, makes no warranty of any kind (express, implied or statutory) with re- spect to this publication, and expressly disclaims any and all warranties of merchantability, fitness for par- ticular purposes and noninfringement of third party rights. PDFlib and the PDFlib logo are registered trademarks of PDFlib GmbH. PDFlib licensees are granted the right to use the PDFlib name and logo in their product documentation. However, this is not required. Adobe, Acrobat, and PostScript are trademarks of Adobe Systems Inc. AIX, IBM, OS/390, WebSphere, iSeries, and zSeries are trademarks of International Business Machines Corporation. ActiveX, Microsoft, Windows, and Windows NT are trademarks of Microsoft Corporation. Apple, Macintosh and TrueType are trademarks of Apple Computer, Inc. Unicode and the Unicode logo are trademarks of Unicode, Inc. Unix is a trademark of The Open Group. -

Users As Co-Designers of Software-Based Media: the Co-Construction of Internet Relay Chat
Users as Co-Designers of Software-Based Media: The Co-Construction of Internet Relay Chat Guillaume Latzko-Toth Université Laval AbsTrAcT While it has become commonplace to present users as co-creators or “produsers” of digital media, their participation is generally considered in terms of content production. The case of Internet Relay Chat (IRC) shows that users can be fully involved in the design process, a co-construction in the sense of Science and Technology Studies (STS): a collective, simultaneous, and mutual construction of actors and artifacts. A case study of the early de - velopment of two IRC networks sheds light on that process and shows that “ordinary users” managed to invite themselves as co-designers of the socio-technical device. The article con - cludes by suggesting that IRC openness to user agency is not an intrinsic property of software- based media and has more to do with its architecture and governance structure. Keywords Digital media; Communication technology; Co-construction; Design process; Ordinary user résumé Il est devenu banal de présenter l’usager comme cocréateur ou « produtilisateur » des médias numériques, mais sa participation est généralement envisagée comme une production de contenus. Le cas d’IRC (Internet Relay Chat) montre que les usagers des médias à support logiciel peuvent s’engager pleinement dans le processus de conception, une co-construction au sens des Science and Technology Studies : une construction collective, simultanée et mutuelle des acteurs et des artefacts. Une étude de cas portant sur le développement de deux réseaux IRC éclaire ce processus et montre que les « usagers ordinaires » sont parvenus à s’inviter comme co-concepteurs du dispositif. -

THE 2003 Editionlinux
SUBSCRIBE or renew your subscription to APC for your chance to WIN the new Alfa 156 JTS, valued at over $54,000 Only $65 for 12 issues THE 2003 edition linux POCKETBOOK Subscribe ... www.apcmag.com Online at magshop.com.au or Call 13 61 16 Authorised under NSW Permit No. L02/09075 VIC: 02/2531 SA: T02/3553 ACT: TP02/3650 NT: NT02/3286 For terms and conditions refer to www.xmas.magshop.au. Expiry date: 24/12/02 Contents CHAPTER 1 Customising Gnome 57 CHAPTER 6 Editorial INTRODUCTION 11 Exploring KDE 60 WORKING WITH WINDOWS 131 The origins of the Customising KDE 64 What about Windows? 132 Welcome back to The Linux Pocketbook 2003 edition! penguin 12 Windows connectivity 138 Many of you will probably remember the original print ver- CHAPTER 4 sions of The Linux Pocketbook on newsstands across the country. Why Linux? 18 Basic security 145 The original versions sold so well that we ran out of copies. We’ve The ways of the world 20 USING LINUX 67 had countless requests for reprints, so we’ve decided to bundle the Connecting to the Net 68 CHAPTER 7 entire book into this single resource. This version of the pocketbook relies heavily on Mandrake Linux 9.0 or Red Hat 8.0. Both were CHAPTER 2 Applications 71 PLAYING WITH LINUX 151 released late in 2002, and can be easily found for sale at www.everyth INSTALLING LINUX 21 Conjuring Linux 75 Linux multimedia 152 inglinux.com.au, or for download from either mandrakelinux.com or First published December 2000. -

Validated Products List, 1993 No. 2
mmmmm NJST PUBLICATIONS NISTIR 5167 (Supersedes NISTIR 5103) Validated Products List 1993 No. 2 Programming Languages Database Language SQL Graphics GOSIP POSIX Judy B. Kailey Computer Security Editor U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 April 1993 (Supersedes January 1993 issue) —QC 100 NIST . U56 #5167 1993 NISTIR 5167 (Supersedes NISTIR 5103) Validated Products List 1993 No. 2 Programming Languages Database Language SQL Graphics GOSIP POSIX Judy B. Kailey Computer Security Editor U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 April 1993 (Supersedes January 1993 issue) U.S. DEPARTMENT OF COMMERCE Ronald H. Brown, Secretary NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY Raymond Kammer, Acting Director FOREWORD The Validated Products List is a collection of registers describing implementations of Federal Information Processing Standards (FIPS) that have been validated for conformance to FTPS. The Validated Products List also contains information about the organizations, test methods and procedures that support the validation programs for the FIPS identified in this document. The Validated Products List is updated quarterly. iii iv TABLE OF CONTENTS 1. INTRODUCTION 1 1.1 Purpose 1 1.2 Document Organization 2 1.2.1 Programming Languages 2 1.2.2 Database -

Table of Contents
Table of Contents Preface .................................................................................................... xiii Part I: The Web Environment Chapter 1—Designing for a Variety of Browsers ...................... 3 Browsers ................................................................................................. 3 Design Strategies .................................................................................... 9 Writing Good HTML ............................................................................. 11 Knowing Your Audience ..................................................................... 12 Considering Your Site’s Purpose ......................................................... 13 Test! Test! Test! ..................................................................................... 13 Chapter 2—Designing for a Variety of Displays .................... 14 Dealing with Unknown Monitor Resolutions ..................................... 14 Fixed versus Flexible Web Page Design ............................................. 19 Accessibility .......................................................................................... 23 Alternative Displays .............................................................................. 26 Chapter 3—Web Design Principles for Print Designers ...................................................................... 28 Color on the Web ................................................................................. 28 Graphics on the Web .......................................................................... -

Programming Languages, Database Language SQL, Graphics, GOSIP
b fl ^ b 2 5 I AH1Q3 NISTIR 4951 (Supersedes NISTIR 4871) VALIDATED PRODUCTS LIST 1992 No. 4 PROGRAMMING LANGUAGES DATABASE LANGUAGE SQL GRAPHICS Judy B. Kailey GOSIP Editor POSIX COMPUTER SECURITY U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 100 . U56 4951 1992 NIST (Supersedes NISTIR 4871) VALIDATED PRODUCTS LIST 1992 No. 4 PROGRAMMING LANGUAGES DATABASE LANGUAGE SQL GRAPHICS Judy B. Kailey GOSIP Editor POSIX COMPUTER SECURITY U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 October 1992 (Supersedes July 1992 issue) U.S. DEPARTMENT OF COMMERCE Barbara Hackman Franklin, Secretary TECHNOLOGY ADMINISTRATION Robert M. White, Under Secretary for Technology NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY John W. Lyons, Director - ;,’; '^'i -; _ ^ '’>.£. ; '':k ' ' • ; <tr-f'' "i>: •v'k' I m''M - i*i^ a,)»# ' :,• 4 ie®®;'’’,' ;SJ' v: . I 'i^’i i 'OS -.! FOREWORD The Validated Products List is a collection of registers describing implementations of Federal Information Processing Standards (FTPS) that have been validated for conformance to FTPS. The Validated Products List also contains information about the organizations, test methods and procedures that support the validation programs for the FTPS identified in this document. The Validated Products List is updated quarterly. iii ' ;r,<R^v a;-' i-'r^ . /' ^'^uffoo'*^ ''vCJIt<*bjteV sdT : Jr /' i^iL'.JO 'j,-/5l ':. ;urj ->i: • ' *?> ^r:nT^^'Ad JlSid Uawfoof^ fa«Di)itbiI»V ,, ‘ isbt^u ri il .r^^iytsrH n 'V TABLE OF CONTENTS 1. -

Souhrada Awaits Trial, Maintains Innocence
The Volume V, Issue 21 March 19, 1996 Steal this issue. Profile: SOUHRADA AWAITS TRIAL, Gordon Bauer MAINTAINS INNOCENCE by Aaron Olk by Michelle Wolper Souhrada was released from the Gordon Bauer, psychology professor Ernest Souhrada is awaiting arraign Sarasota County Jail on March 8, the and Social Science Chair, was in Hawaii ment. The New College community is same day of his arrest. J. Alder, correc doing research on humpback whales and waiting for a complete story. While most tions officer at the jail, said that Afford working for the Veterans details cannot be disclosed at this time able Bail Bonds posted his bail amount of ~ u: Administration until he due to legal complications, Souhrada is $3508. Souhrada now awaits his arraign 0 came to New College five defending his innocence, while his ac ment, scheduled for April 19. a: a.. years ago. cuser has come forward. Alford has also made a statement re Bauer was working with Stephenie Alford and another uniden garding Harry's theft and her confession veterans plagued by post-traumatic stress tified source told University Police on to the police. disorder (JYTSD), an illness similar to March 7 that Souhrada, Alford's es "The students need to have the shell shock and battle fatigue, in an at tranged husband, stole Harry, the computer which was taken from them tempt to better understand the disease. computer that served as a student server Bauer said that the opinion most people in Hanson Lab. She also told police under SEE "SOUHRADA" ON PAGE 2 had at the time was that "there must be oath that Souhrada had changed the exte something wrong with the JYTSD victim rior container of Harry at the residence to begin with." that they shared at the time. -
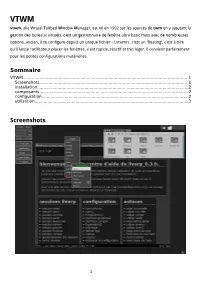
VTWM Vtwm, Aka Virtual Tabbed Window Manager, Est Né En 1992 Sur Les Sources De Twm En Y Ajoutant La Gestion Des Bureaux Virtuels
VTWM vtwm, aka Virtual Tabbed Window Manager, est né en 1992 sur les sources de twm en y ajoutant la gestion des bureaux virtuels. c'est un gestionnaire de fenêtre ultra basic mais avec de nombreuses options. ancien, il se configure depuis un unique fichier ~/.vtwmrc. c'est un 'floating', c'est à dire qu'il laisse l'utilisateur placer les fenêtres. il est rapide, réactif et très léger. il convient parfaitement pour les petites configurations matérielles. Sommaire VTWM.................................................................................................................................1 Screenshots....................................................................................................................1 installation......................................................................................................................2 composants....................................................................................................................2 configuration...................................................................................................................2 utilisation........................................................................................................................3 Screenshots 1 installation vtwm est présent dans les dépots de la plupart des distributions. pour Debian, dans un terminal: # apt-get install vtwm composants la session vtwm dispose de plusieurs éléments: • IconManager : une boite à icones servant aussi de tasklist. • VirtualDesktop : un pager simple. • Vtwm